Enumeration Ethical Hacking | What is Enumeration | Enumeration Ethical Hacking
What is Enumeration
Enumeration is a very essential phase of hacking, because when a hacker established an active connection with the target, then he tries to retrieve as much as possible information from the Target machine. There are a bunch of definitions of online enumeration.
Enumeration Ethical Hacking | What is Enumeration | Enumeration Ethical Hacking
Enumeration is also a process of the best tool which is to get access and more details about target computer attacker user this process to get more information about the victim using network scanning and system footprinting and enumeration of the system.
Enumeration Ethical Hacking | What is Enumeration | Enumeration Ethical Hacking
- Cross Site Scripting xss attack
- System Hacking Kali Linux
- Enumeration Ethical Hacking
- Network Scanning Tool
- What is Ethical Hacking
Enumeration Ethical Hacking Steps
- Network details
- Domain information
- Open ports and services
- Server Enumeration
- Web Server Version Detection
- Misconfiguration Detection
- Gather Windows Permissions
- Kernal Version Enumeration
- User Information
- Group information
- Weak File Permission
- Background Running Process
- Website URL Crawling
Common Ports and Services
- 21 FTP Enumeration
- 22 SHH Enumeration ( Secure Shell )
- 23 Telnet
- 25 SMTP Enumeration ( Simple Mail Transfer Protocol )
- 80 HTTP Service and version
- 53 DNS Enumeration ( Domain Name System )
- 137/138/139 SMB Enumeration ( NetBIOS )
- 443 SSL HTTPS ( Hypertext Transfer Protocol over )
- 8080 Tomcat HTTP Server
Enumeration Ethical Hacking Tools
- Dirb Scanner
- Dirbuster
- Wpscan
- Dnsenum
- Enum4linux
- Nikto
- Burp Suite
- SQL Map
- SMBclient
- Netcat
Enumeration with Dirb
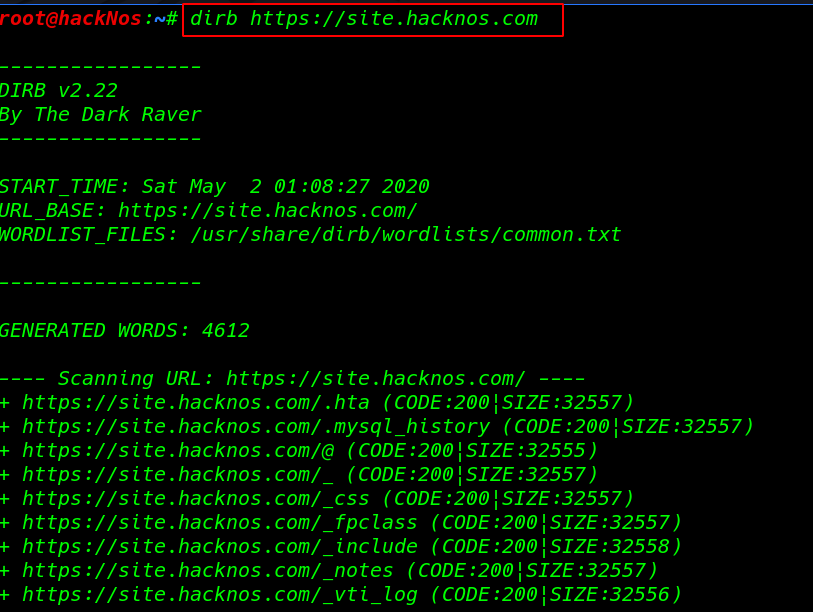
DIRB Is a Web Content Scanner and page and directory dictionary-based URL brute-forcing tool. a hacker uses to dirb tool to scan and crawls all websites. It basically works by launching a dictionary-based attack against a web server and analyzing the response.
Let’s try with an example
|
1 |
dirb https://site.hackno.com |
Enumeration through Dirbuster
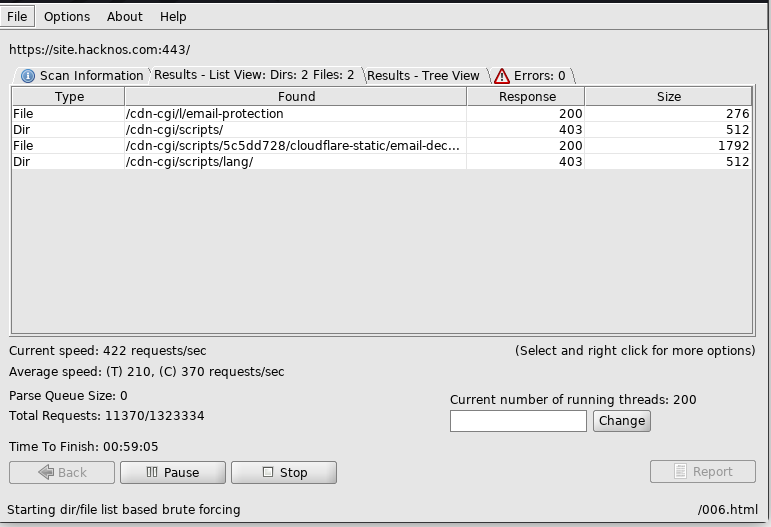
Dirbuser is a GUI version of dirb Scanner. dirt buster is a multi-threaded Program Language java tool it is designed for brute-forcing directories and files to web/application servers.
we can scan fast websites using the threads and we can apply a file extension filter. here an example
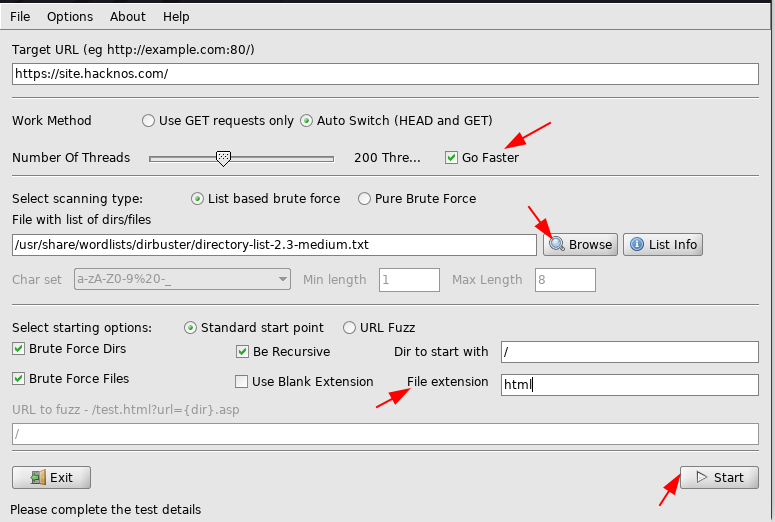
After Scanning
WordPress Enumeration Wpscan
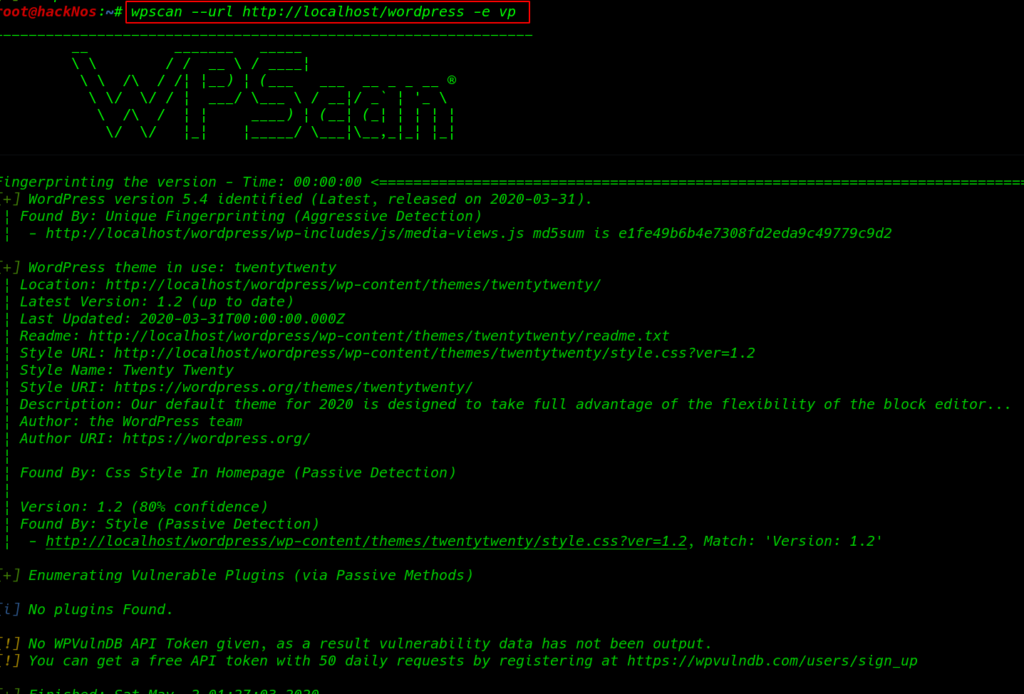
Wpscan ( WordPress Security Scanner ) is a powerful tool for scanning the WordPress website. using the wpscan we can find more than information about the website changing -e parameter like
- Enumerating Themes and Version
- Plugin Name and Version
- Author user name
- WAF Enable
- Password Brute-Forcing
- display the banner
- Timthumbs
- Config Backup Files
|
1 |
wpscan --url http://localhost/wordpress -e vp |
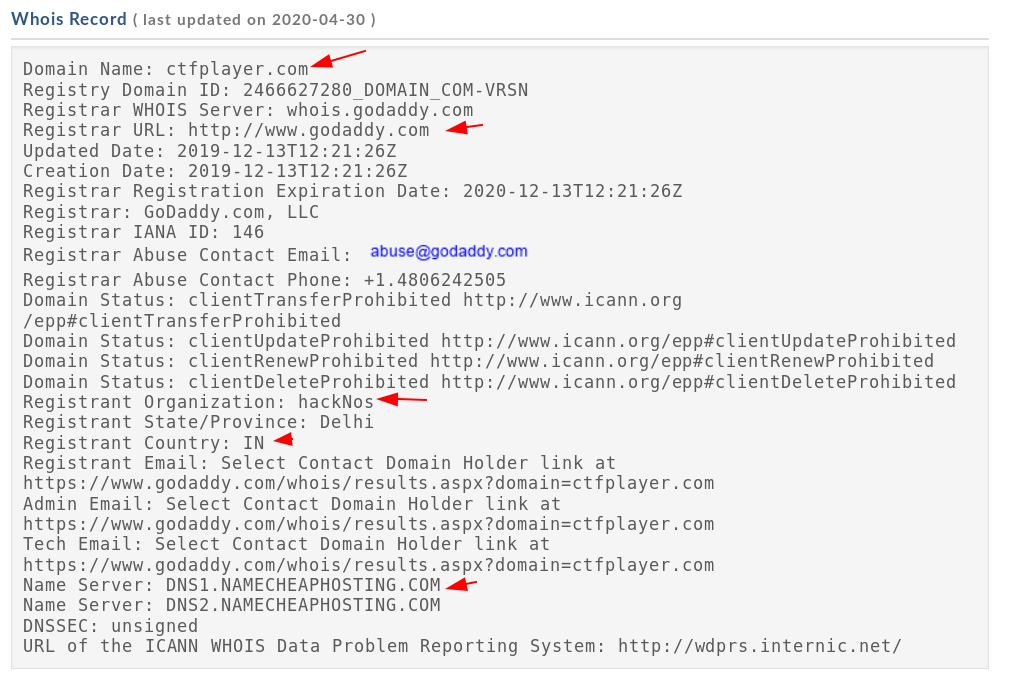
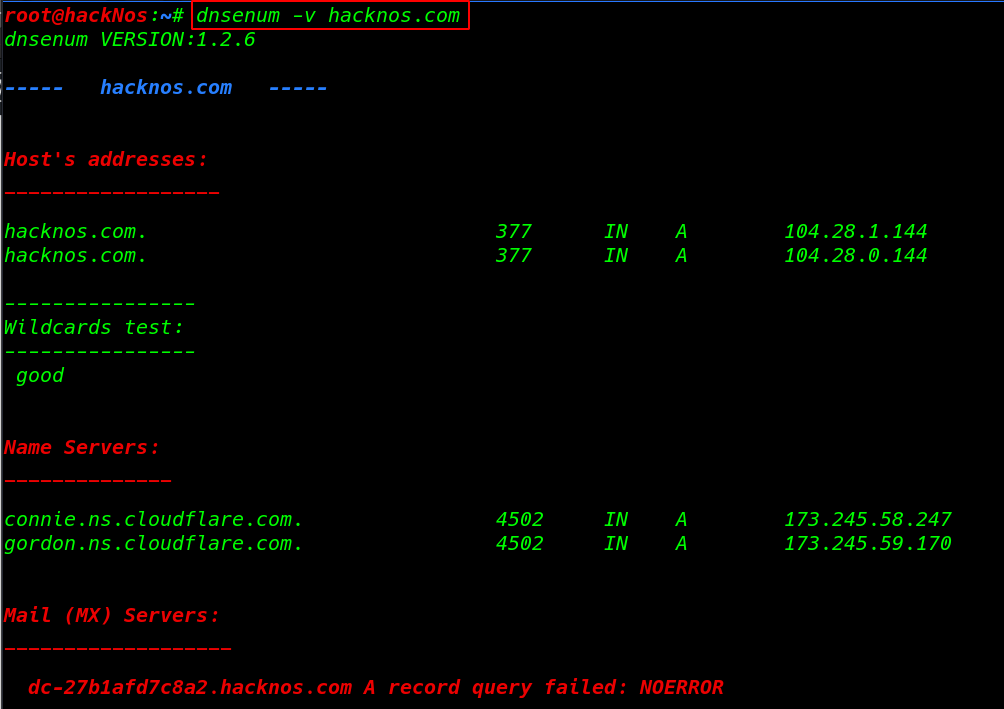
Dnsenum – DNS Enumeration Tool
dnsenum is a DNS ( Domain Name System ) enumeration Tool. it will allow us to gather critical information about the domain such as ( MX record ) mail server record, IP addresses, zone transfer details, Subdomains, and TXT record, etc.
|
1 |
dnsenum -v hacknos.com |
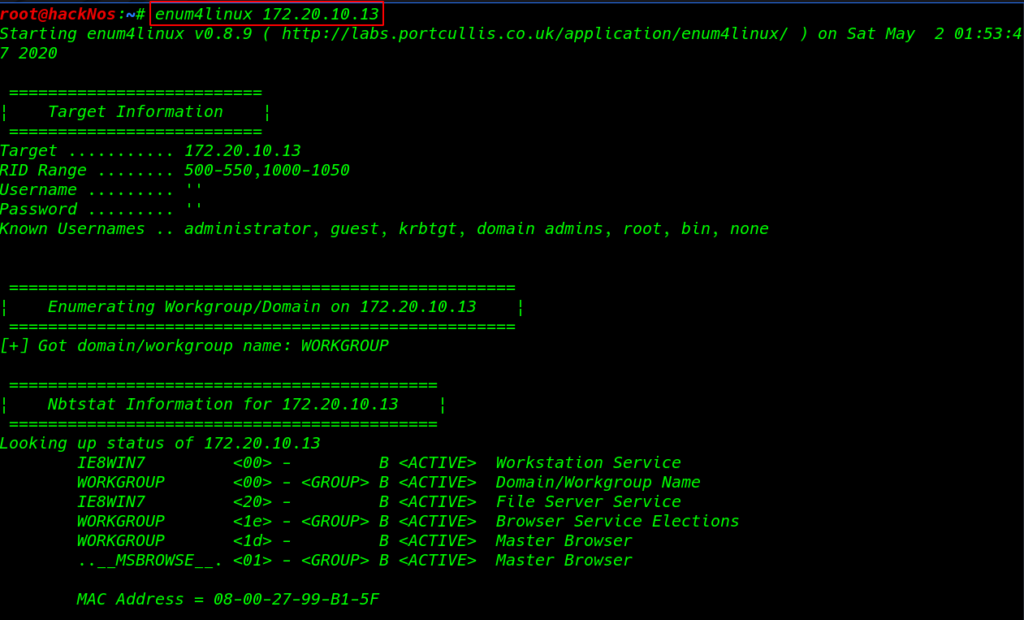
Enum4Linux – SMB Enumeration
Enum4linux is a tool for SMB enumerating information from Windows/Linux SMB Samba Server. This tool provides much information about the Samba Share Drives and Work-group domain name target mac address and shares driver username.
|
1 |
enum4linux 172.20.10.13 |
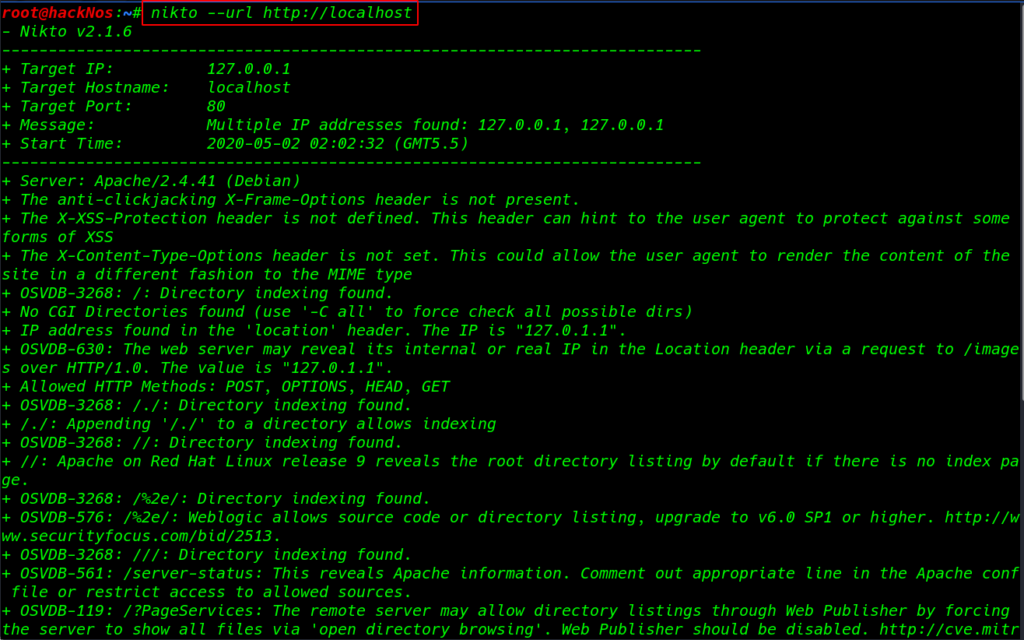
Enumaration with Nikto
Nikto scan for vulnerabilities and discover the weakness link URL how this powerful and versatile tool works It supports SSL, proxies, host authentication, IDS evasion, and more.
types of information provide website IP address, server name and version, web directory
indexing, target port, HTTP Methods, SSL information, and host vulnerabilities CVE number.
|
1 |
nikto --url http://localhost |