IOT
IoT Security Cheat Sheet
Introduction While doing IoT security testing of a system a robust and foolproof assessment…
IoT Threat Modelling
Introduction Although there are multiple definitions widely for ‘Internet of Things(IoT)’, but for purposes…
Top IoT Security Threats
Introduction: Top IoT Security Threats Internet of Things (IoT) is the most vast, versatile…
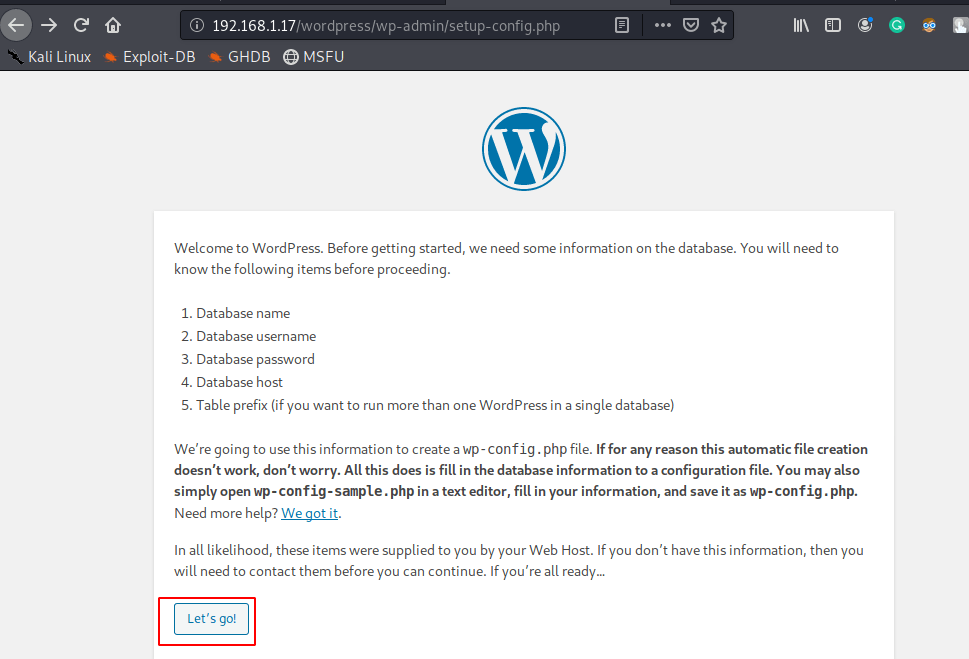
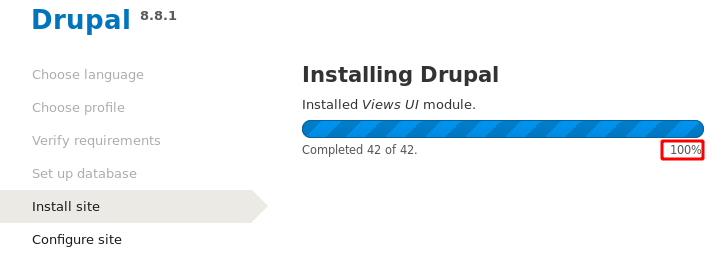
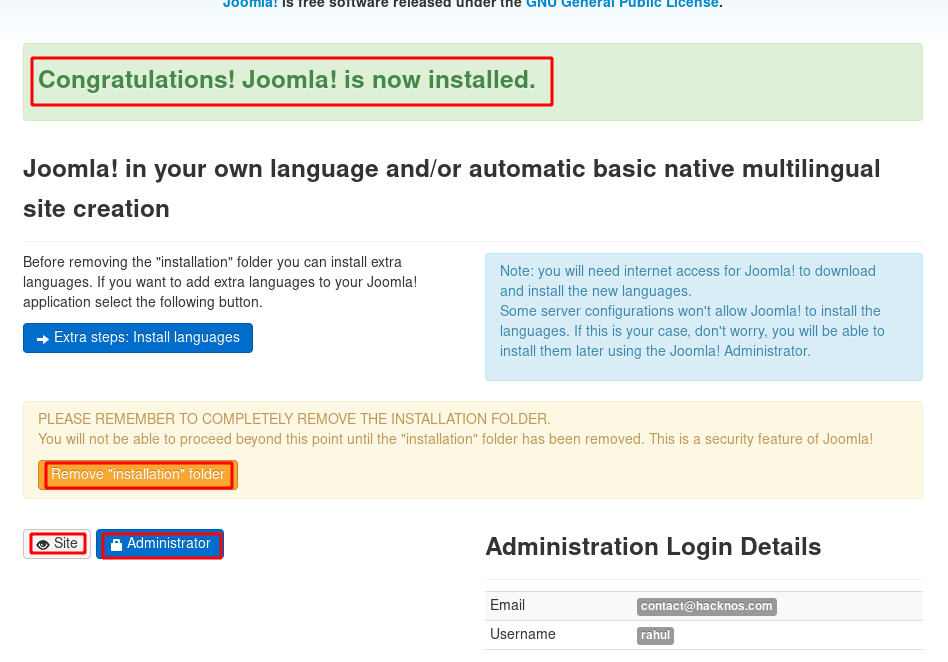
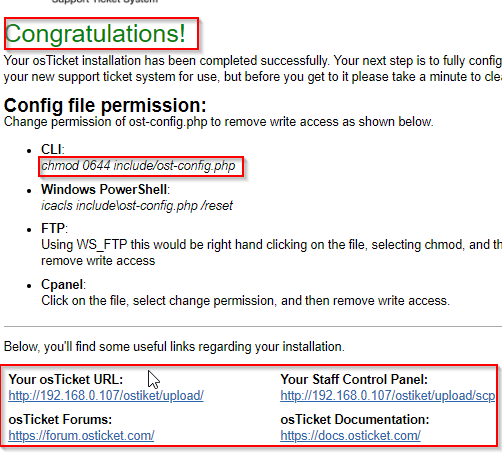
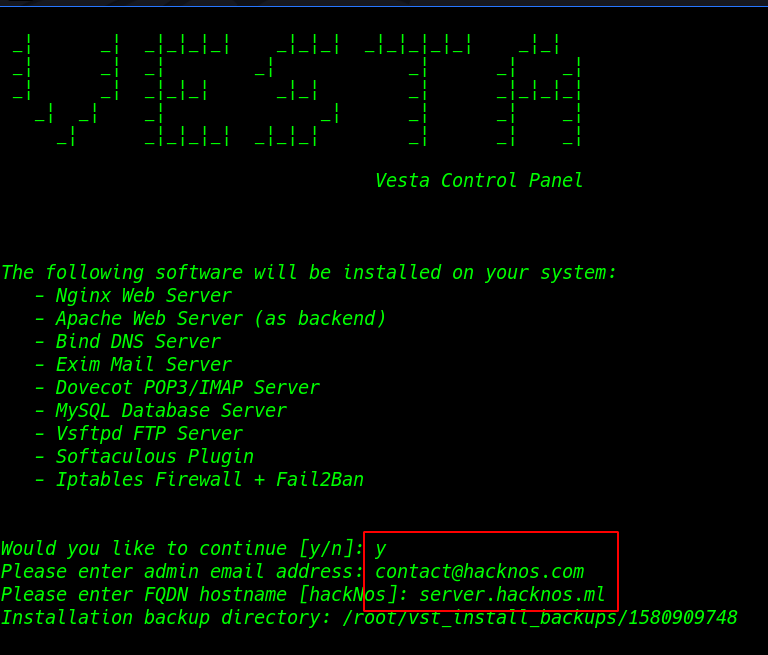
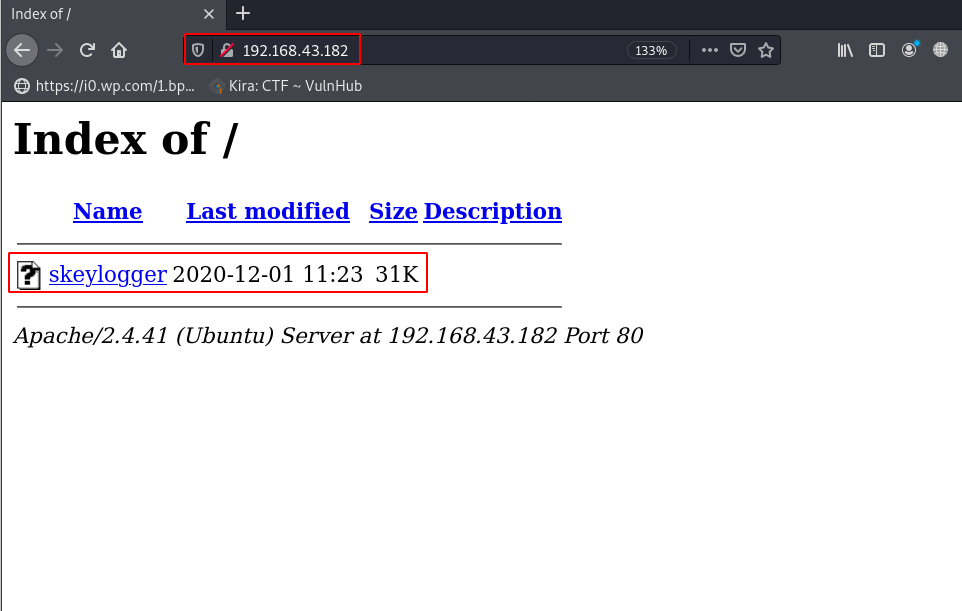
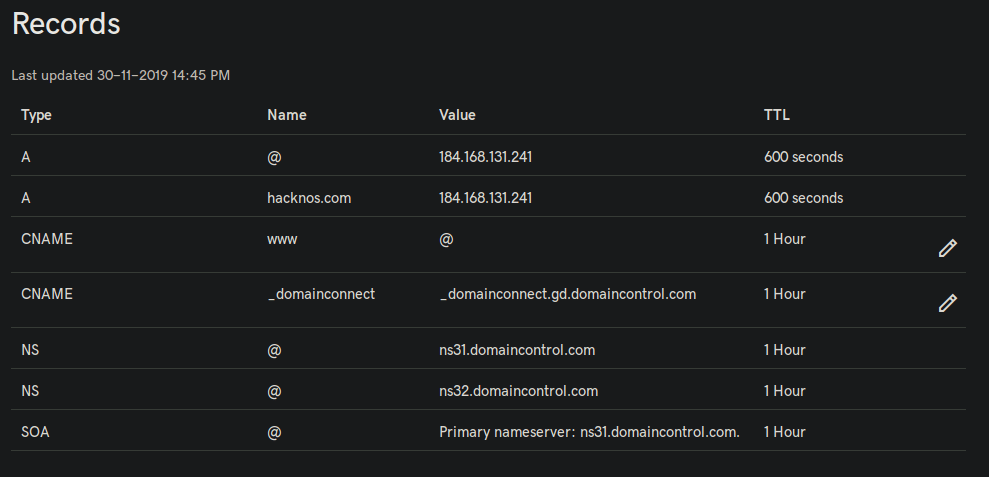
CMS Installation

Latest
Even though technology continues to advance at a break-neck pace, some forms of it remain…
In today’s interconnected and digital world, cybersecurity has become a paramount concern for organizations and…
Are you sick and tired of defending your CI/CD pipeline from the continuously changing cyber…
It is undeniable that macOS, the operating system (OS) made by Apple, does offer better…
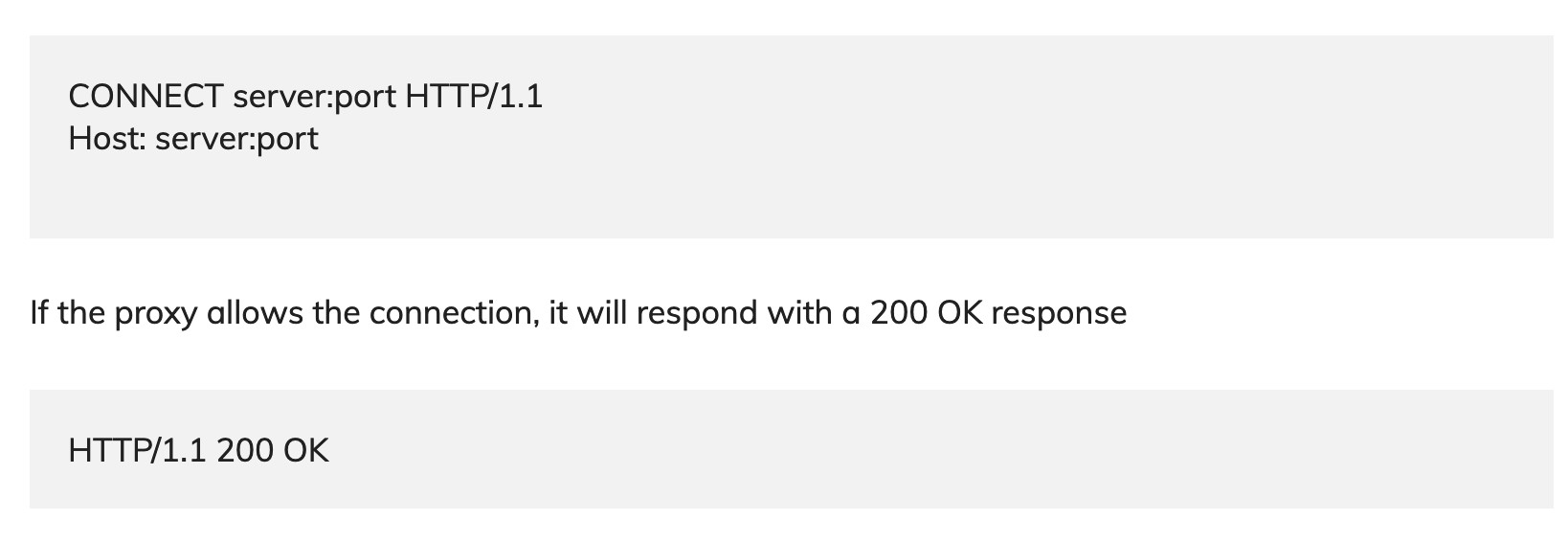
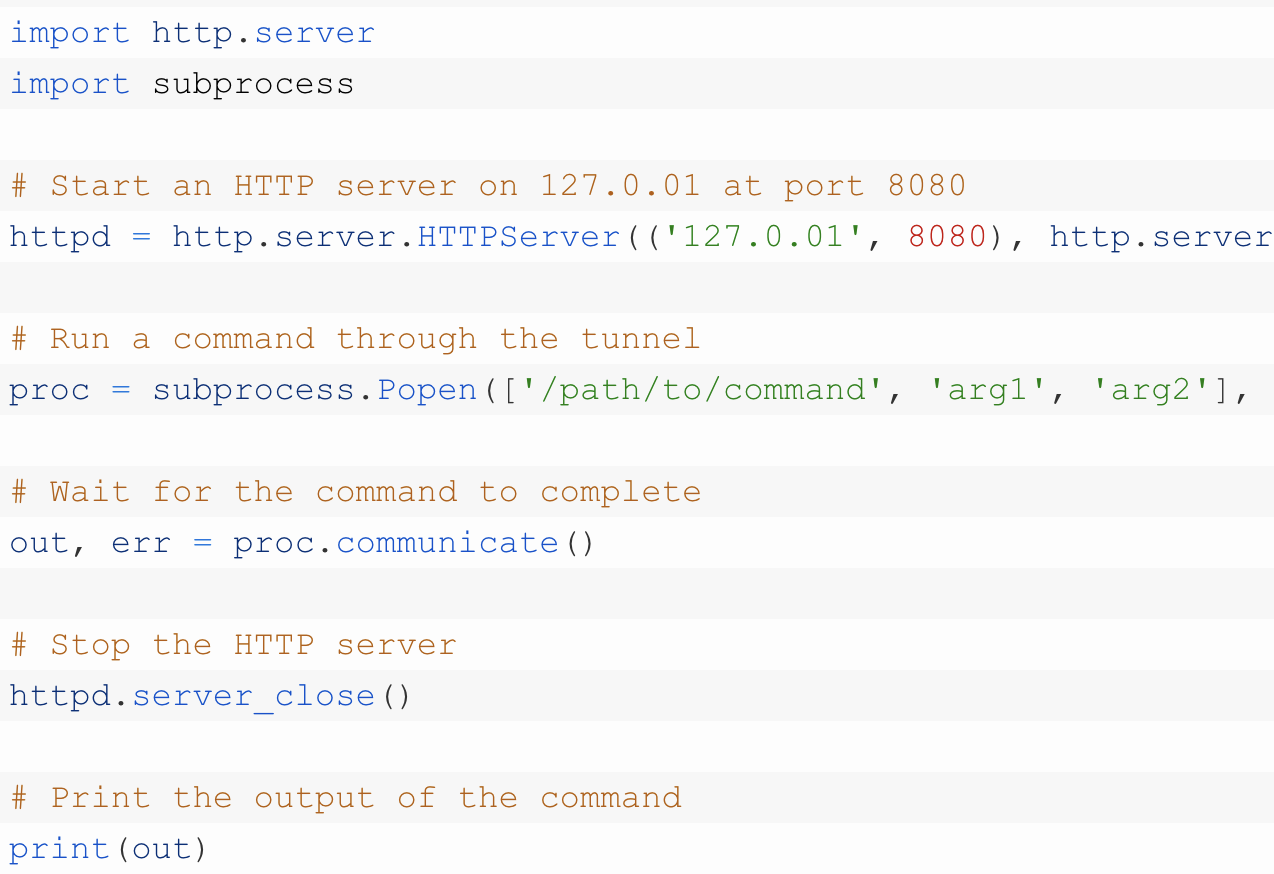
What is HTTP Tunnel HTTP tunneling is used to create a network link between two…
Process of making http tunnel in python, to create an HTTP tunnel with Python, we…