haclabs: Deception walkthrough vulnhub ctf
Today We are solving another Vulnhub CTF hacklabs: deception is created by HacLabs This machine is designed by keeping in mind about all the beginners.
you can download here
Network Scanning
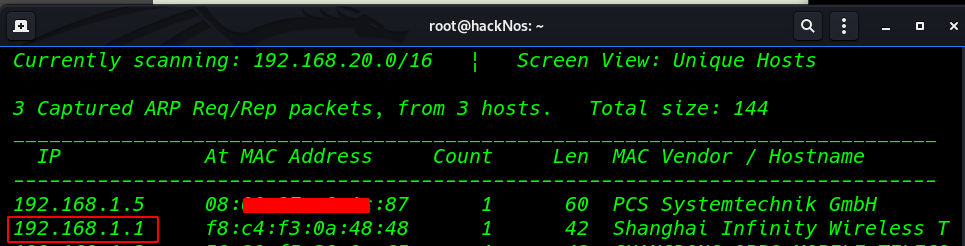
we found our target IP address through netdiscover, a simple ARP reconnaissance tool to find live hosts in a network.
|
1 |
netdiscover |
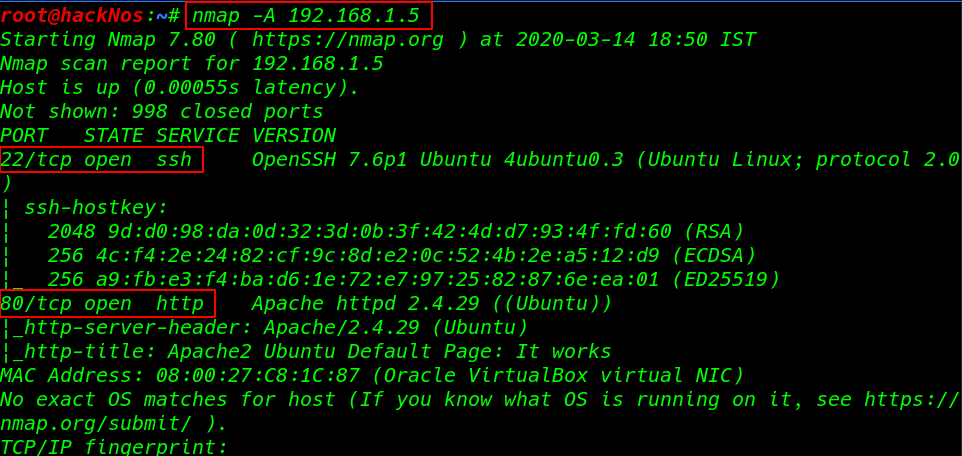
Aggressive scanning with Nmap finding the open port and running services.
|
1 |
nmap -A 192.168.1.5 |
Enumeration
I open the victim IP address the browser we see the apache2 default web page
|
1 |
https://192.168.1.5 |
dirb is a web content scanner that was also used to brute force for any available files and directory on the website.
|
1 |
dirb https://192.168.1.5 |
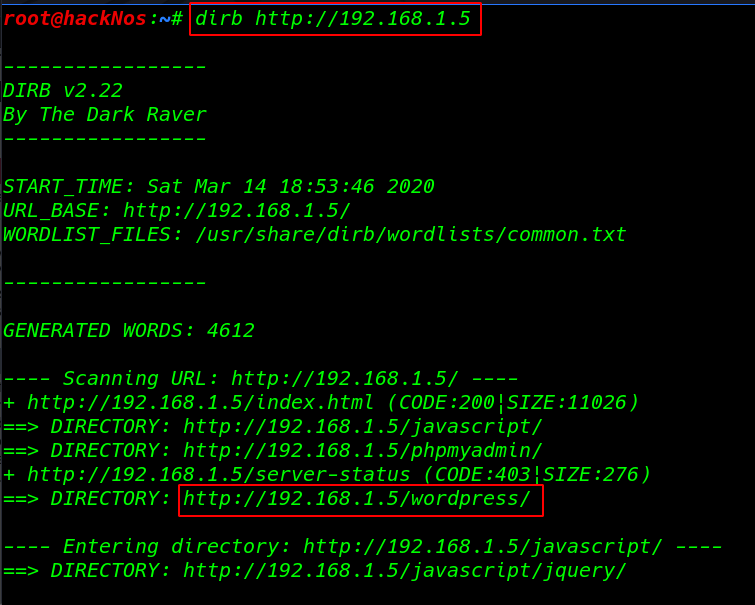
we see dirb result WordPress I open the URL browser and we see the WordPress default themes is installed
|
1 |
https://192.168.1.5/wordpress |
Since the website was made using WordPress wpscan, a WordPress Security Scanner was then used to try to find existing vulnerabilities on the website, ( -e u parameter find all user account )
|
1 |
wpscan --url https://192.168.1.5 -e u |
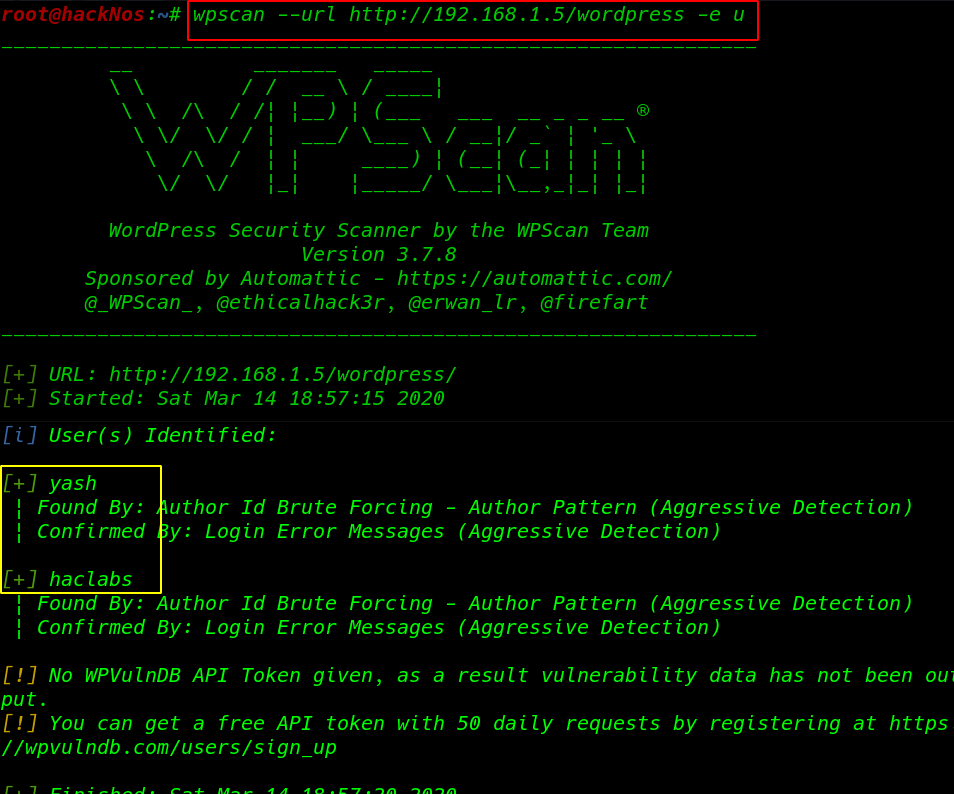
our scanning is complete and I found two users yash and hacklabs
we see the target robots.txt allow URLs
|
1 |
https://192.168.1.5/wordpress/robots.txt |
So we open this robots.html then we get a simple form with an input box and a submit button I Enter random text and we see new popup windows our text is reflected
|
1 |
https://192.168.1.5/wordpress/robots.html |
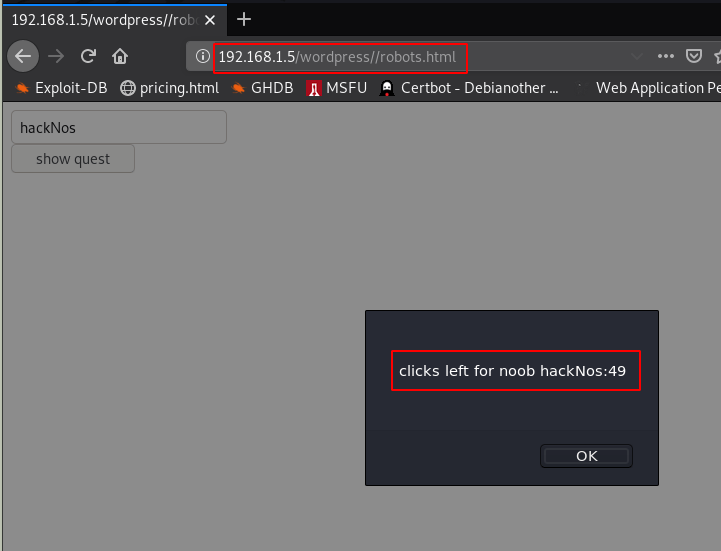
I check the source code of the webpage then we see that after 15 clicks it redirect the user to a new webpage admindelete.html here we see a text message LOL, A Noob is looking for a hint
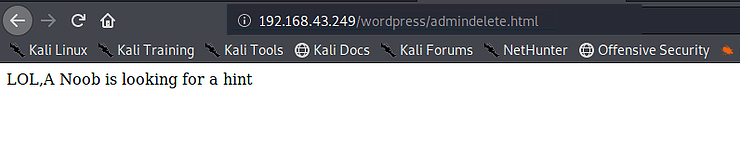
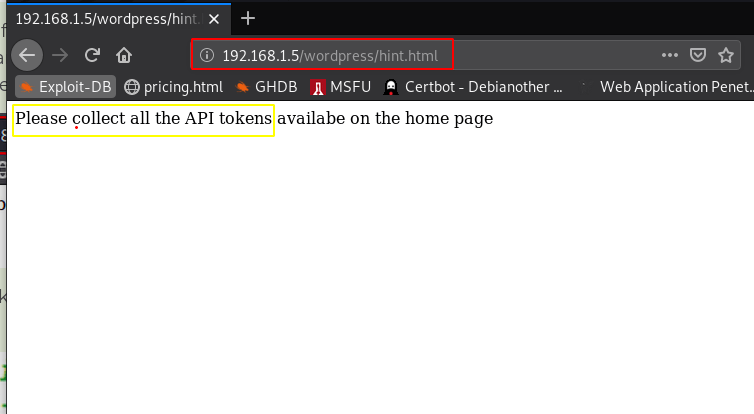
so, this means hint can be a webpage so I tried top open hint.html and we successfully I found one another page hint.html this hint file says that pleases collect all API tokens available on the home page
|
1 |
https://192.168.1.5/wordpress/hint.html |
I move on the home page URL and I check the source code of the webpage and I found many API tokens
|
1 |
view-source:https://192.168.1.5 |
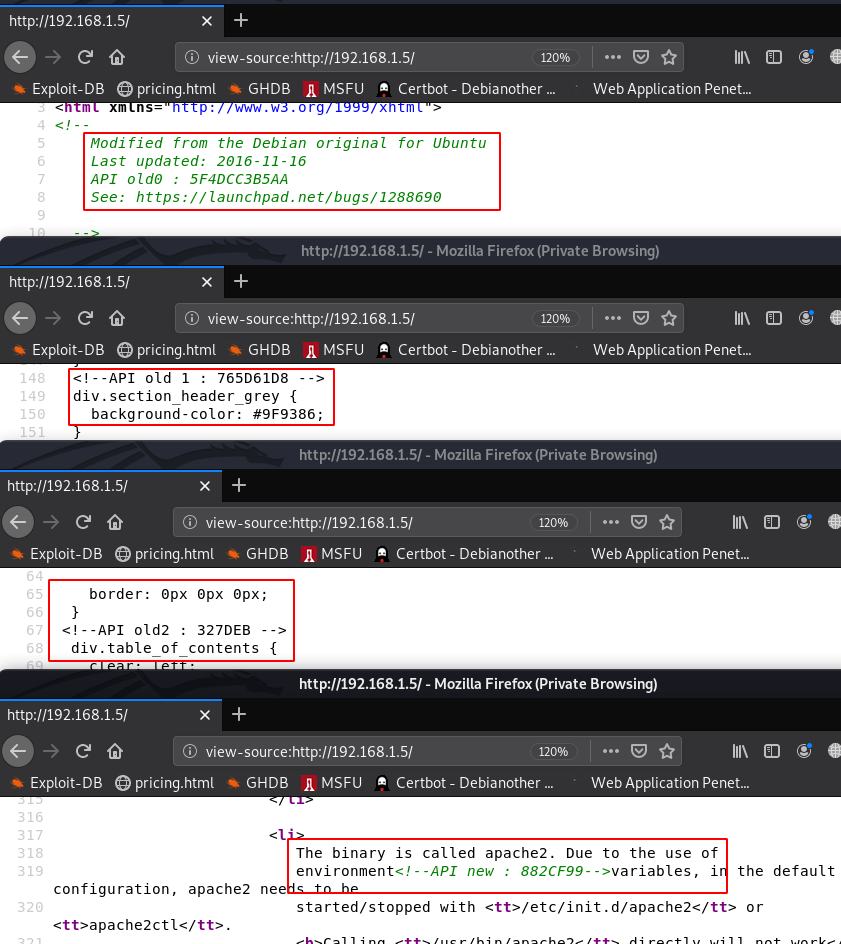
after collecting all the API and arranging them one line and all API token is look like this 5F4DCC3B5AA765D61D8327DEB882CF99
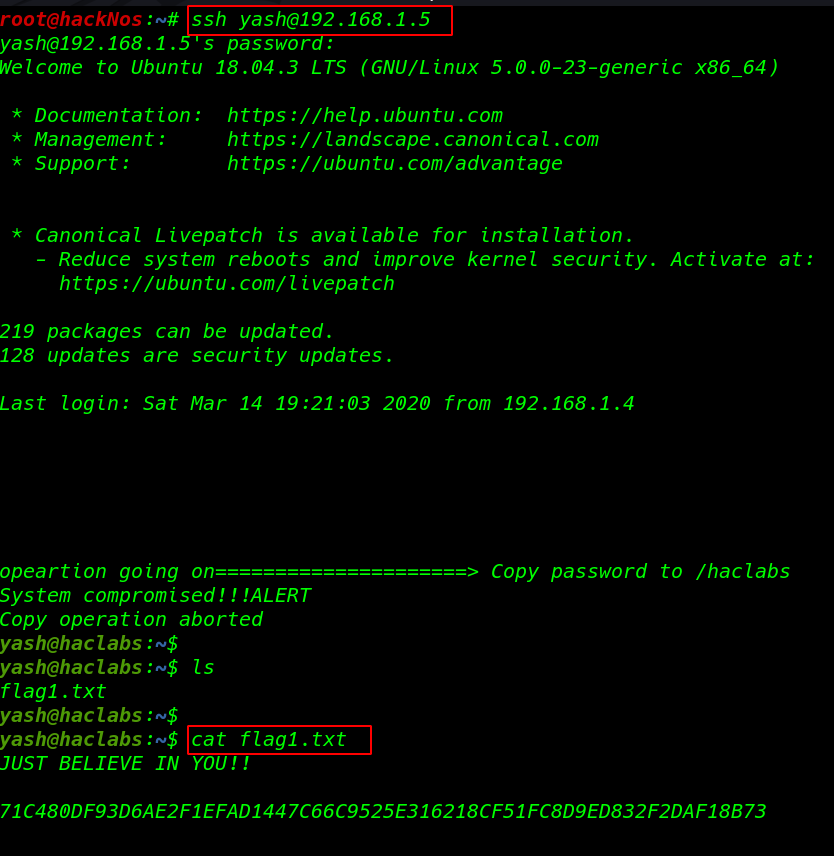
I tried all API token login username yash and password is founded all API key and I got yash user shell
|
1 |
ssh yash@192.168.1.5 |
First Flag
|
1 2 |
ls cat flag.txt |
after enumerating some directory I see a hidden file .systemlogs
|
1 |
ls -lsa |
we tried to read the content of this file using cat command. and I found something really helpful.
|
1 |
cat .systemlogs |
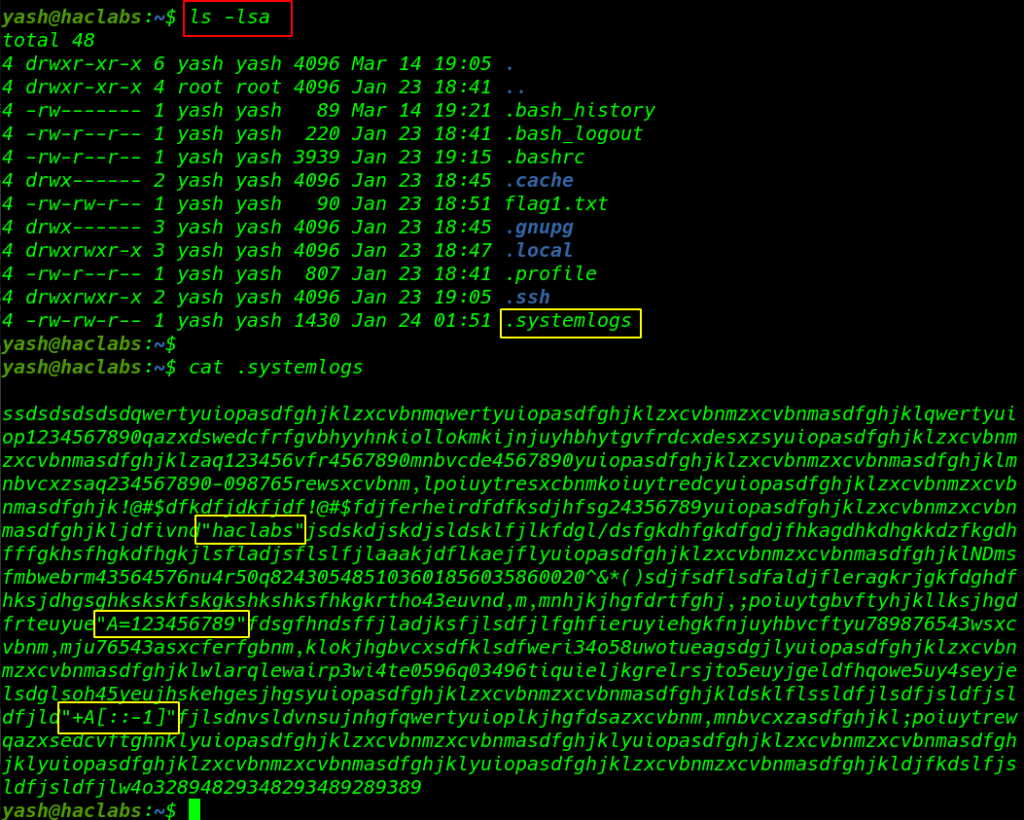
( first is hacklabs ) and (second is A=123456789 ) (third is +A[::-1] )
I treat the second value as a variable and third is look like String Slicing the variable A and we found a value like this ( hacklabs987654321 )
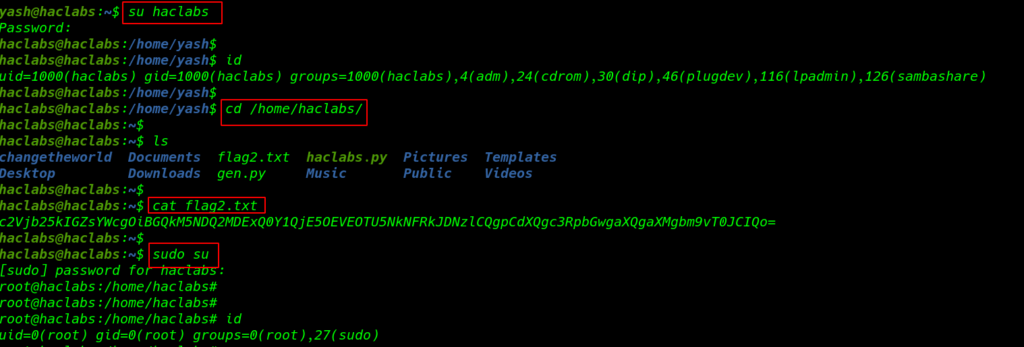
changing the current user yash to hacklabs with su ( switch user command ) and try password hacklabs987654321 and our shell is changed successfully
|
1 |
su hacklabs |
Second Flag
I move on haclabs home directory and we see our second flag
|
1 2 3 |
cd /home/hacklabs/ ls cat flag2.txt |
again upgrading our shell normal user to superuser root sudo su command with password hacklabs
|
1 |
sudo su |
|
1 |
cd /root/ && ls |
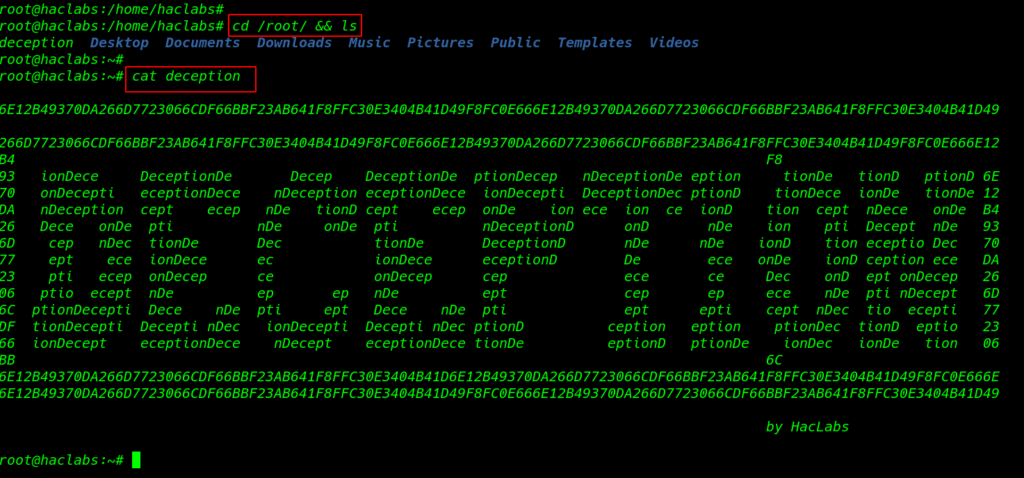
Final 3 Flag
|
1 |
cat deception |