Introduction: Top IoT Security Threats
Internet of Things (IoT) is the most vast, versatile technology in existence today. The diversity of devices connected with each other makes IoT more scalable and adaptable to situations and conditions in our lives.
However, as the Internet of Things(IoT) grows it also brings with it dire security risks and threats. You may come across a threat that may seem very minimal and innocuous but could have a very great impact on the security of an entire organization or infrastructure revolving around IoT.
- IoT Threat Modelling
- Use of FTK Imager Forensic Tool
- MacChanger in Kali Linux
- Genymotion For Linux
- Apache Stop Directory Listing
What are top IoT Security Threats?
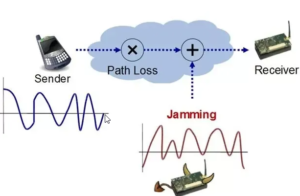
1. Signal Jamming Attacks
In this type of IoT Security Threat, an attacker interferes with the communication taking place between two systems. IoT system comprises of its own ecosystem that comprises of multiple nodes.
Jamming attacks are a form of DoS(Denial of Service) attack in which an adversary transmits a high-range signal to disrupt communication between nodes. A signal-jamming attack is a deliberate attempt by an attacker to interfere with the physical transmission of signals during a communication process.
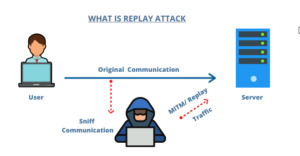
2. Replay Attacks
In this type of IoT Security Threat, an attacker repeats some operation or resends a transmitted packet again and again. In this type of IoT security attack, an unauthorized malicious attacker intercepts the traffic and sends it to the original destination multiple times. Taking an example in a hospital if a patient receives multiple doses of a medicine that was intended for a single dose may result in a very severe and fatal situation.
3. Setting Tampering Attacks
In this type of IoT Security Threat, an attacker exploits the very basic thing, a system’s lack of integrity to change its settings. Considering a scenario, If an unauthorized attacker gets his hands on an IoT system’s settings and changes the control server with a malicious control server controlled by an attacker, or he could change network settings for that particular system that result in a Denial of Service(DoS) attack.
4. Hardware Integrity Attacks
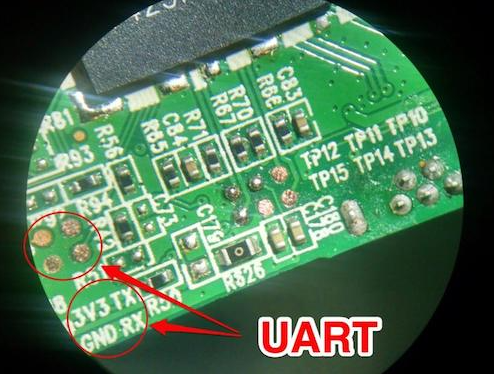
This type of IoT Security Threat occurs if an attacker is successful in compromising the integrity of the physical device. This is the most exploited IoT attack vector and all IoT systems face this threat because there is no device with perfect device integrity. For example, if an attacker manages to bypass insecure locks or gets his hands on the easily accessible debug ports on the hardware.
5. Node Cloning Attacks
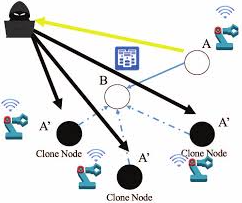
This type of IoT Security Threat occurs when an attacker creates fake nodes in a network to compromise its reliability and integrity. This attack is very common in IoT Systems and fairly simple to exploit in some weak configured systems.
Conclusion: Top IoT Security Threats
In this blog post, we discussed the Top IoT Security Threats and what risks they could pose. However, IoT is an evolving field and new attack vectors threats are being discovered every day.