Understanding /etc/passwd File.
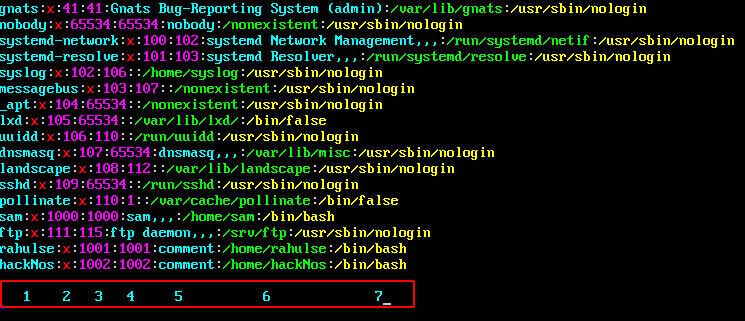
Overview of passwd file Understanding /etc/passwd The /etc/passwd File. /etc/passwd is a text file that contains the attributes of (i.e., […]
Overview of passwd file Understanding /etc/passwd The /etc/passwd File. /etc/passwd is a text file that contains the attributes of (i.e., […]
The VI editor modes is the most popular and classic text editor in Linux. VI editor has three modes of […]
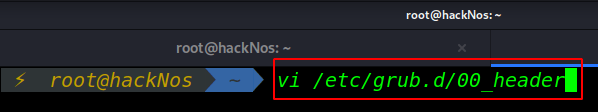
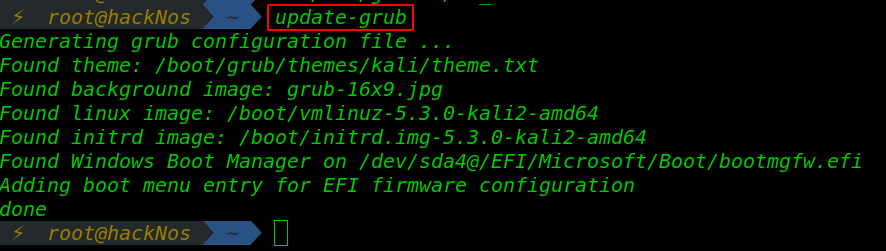
Today i will tell you how you can Protect Youe Kali Linux Grub. How to Protect Grub Boot Loader by […]
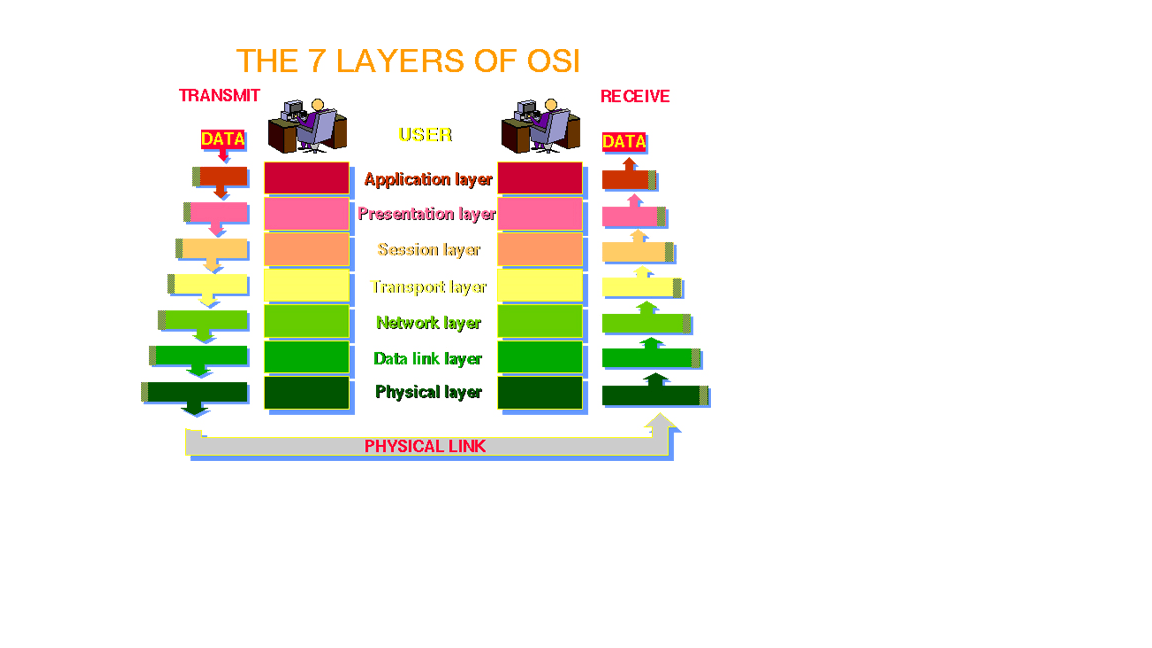
What is OSI 7 Layers Reference Model Here you will learn OSI Model Layer Introduction, an overview of the 7 […]