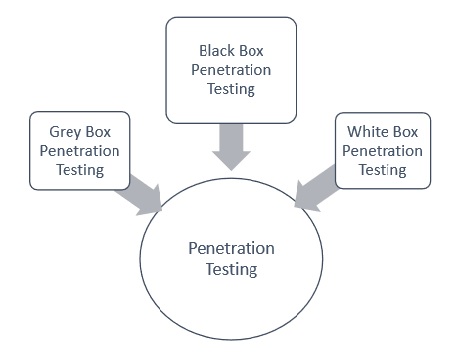
When the scope of the penetration test is defined, the categories & types of penetration test engagement are also defined along with it. The entire penetration test can be Black, Box white Box, or Gray Box Depending upon what the organization wants to test and how it wants the security paradigm to be tested.
How many types of penetration testing are there
- Black Box Penetration Testing
- White Box Penetration Testing
- Gray Box Penetration Testing
- Enumeration Ethical Hacking
- Network Scanning Tool
- System Hacking Kali Linux
- Shellphish Install in Termux
- Hiddeneye Install in Termux
What is a Black Box Penetration Test
In a black-box penetration test, no information is provided about the target. In the case of a network penetration test, this means that the target’s DMZ ( demilitarized zone ), the target operating system, and server version will not be provided by the client/origination. the only thing that will be provided is the target System IP ranges that you would test.
In the case of a Web Application Black Box Penetration testing, The source doe of the Website will not be provided. black-box penetration tester must be familiar with automated scanning tools and methodologies for manual penetration testing.
What is a White Box Penetration Test
In the Black Box penetration testing, almost all the information provided about the target. In the case of a White Box network penetration Test, which information is provided by the Client Like, IP address, Operating System Name, Operating system version, and architecture documentation.
In the case of the White Box Web Application Penetration testing the much information provided by the Client, the Web Application source code is provided, Unlike black-box and gray-box testing, white-box penetration testers are able to perform static/dynamic code analysis.
What is GREY box penetration testing
In a Gray Box Penetration Test, some information is provided, and some is hidden. In case of a network Penetration test, the organization provides the name of the application running behind the and IP address. It doesn’t disclose the exact version of the services running of the target machine.
In the case of the Gray Box Web Application Penetration Test, some information provides by the Client/ Organization. such as test accounts, back-end servers, and databases is provided to Penetration Tester.