Today we are solving enubox: mattermost walkthrough Vulnhub CTF is created by Avraham Cohen
Description: The Mattermost chatting system may or may not hold sensitive information. Can you find your way in? EnuBox Mattermost Walkthrough
EnuBox: Mattermost Download
First, step is finding our target IP address using Netdiscover Toll
|
1 |
netdiscover |
NMAP
( A network mapping tool that allows you to scan for open ports, services, and operating systems to list a few features. )
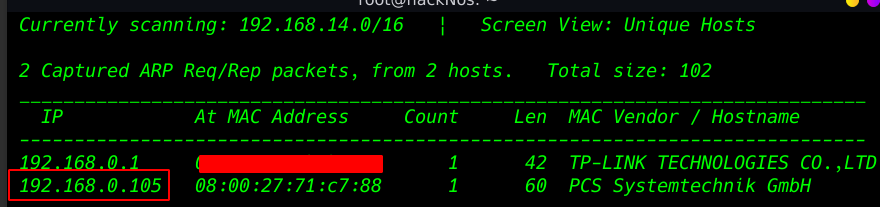
Now scanning our target Machine IP address with Nmap network mapping tool and using the parameter -A ( aggressive scan )
|
1 |
nmap -A 192.168.0.105 |
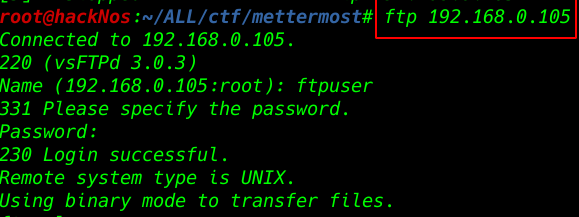
After scanning our target IP address we see many ports are open but port 21 FTP is allowing login with the default username and password
connecting FTP anonymous username password
|
1 |
ftp 192.168.0.105 |
- ftp
- ftp
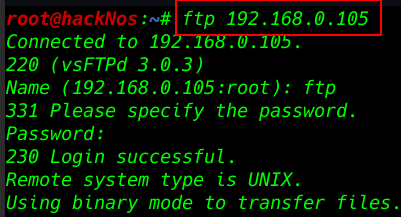
Enumerating port 80 HTTP service running I opening the IP address our firefox browser and this web site is showing 404 Access forbidden and information Details or Servername “mattermost”
|
1 |
http://192.168.0.105 |
Sometime later I am trying to FTP login with username ftpuser and password ftppassword and me successful login FTP connection
|
1 |
ftp 192.168.0.105 |
- ftpuser
- ftppassword
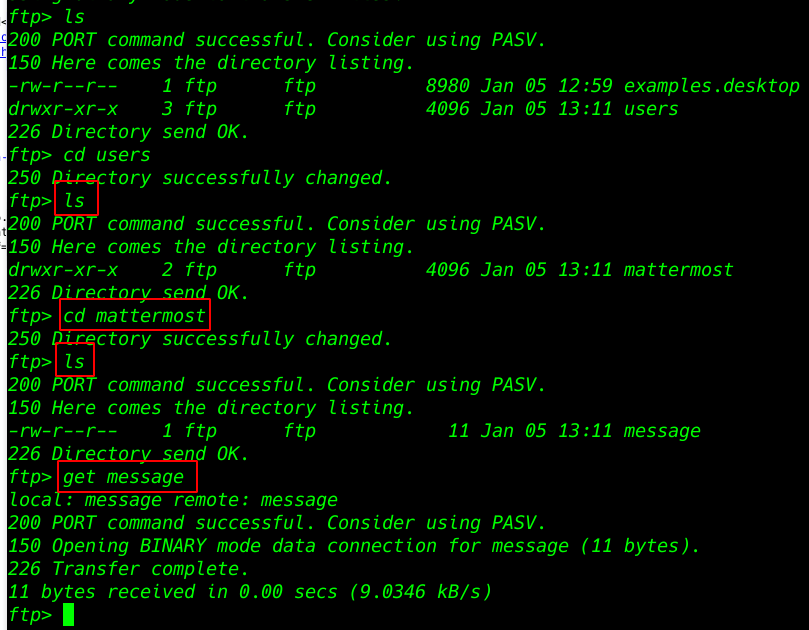
Enumerating Directory FTP
|
1 |
ls |
|
1 2 3 4 5 |
cd users ls cd mettermost ls get message |
After enumerating many directories we got a message txt file mattermost directory I download the file our local system and opening the txt file.
|
1 |
ls |
|
1 |
cat message |
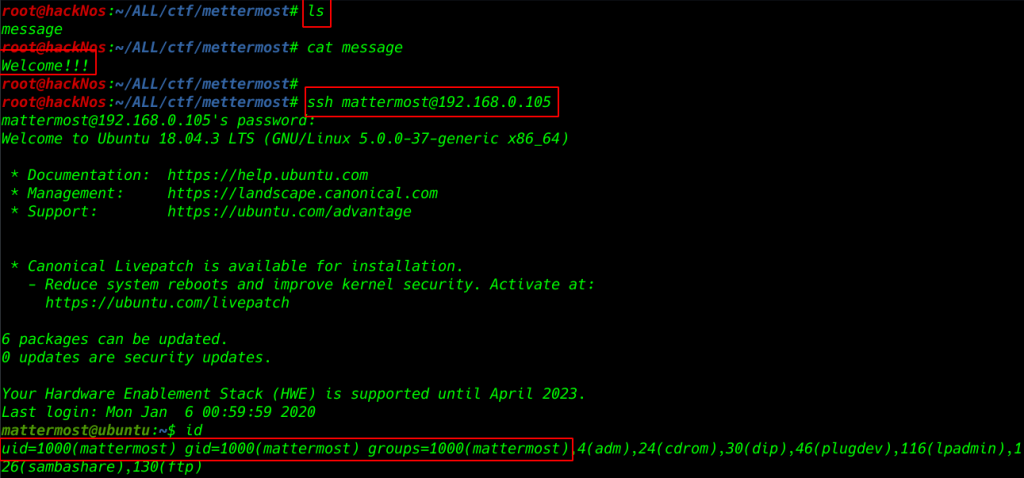
I am trying the message text for password login ssh connection and we already see the browser server name
|
1 |
ssh mattermost@192.168.0.105 |
I am trying to the login ssh connection
- username: mattermost
- password: Welcome!!!
logging Succesful ssh connection trying to enumerate the system directory and files
|
1 |
id |
|
1 |
cd Desktop |
|
1 |
ls |
|
1 |
cat README.md |
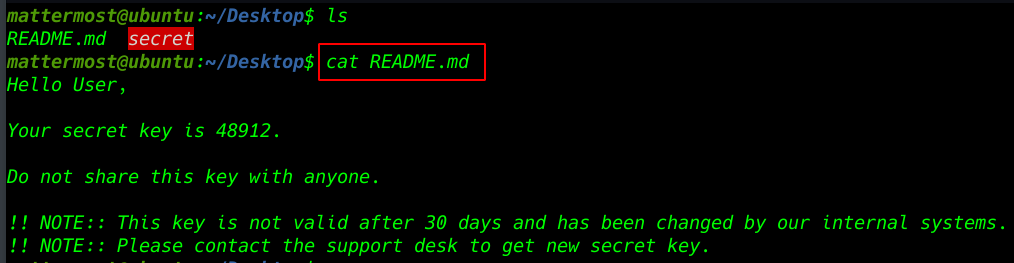
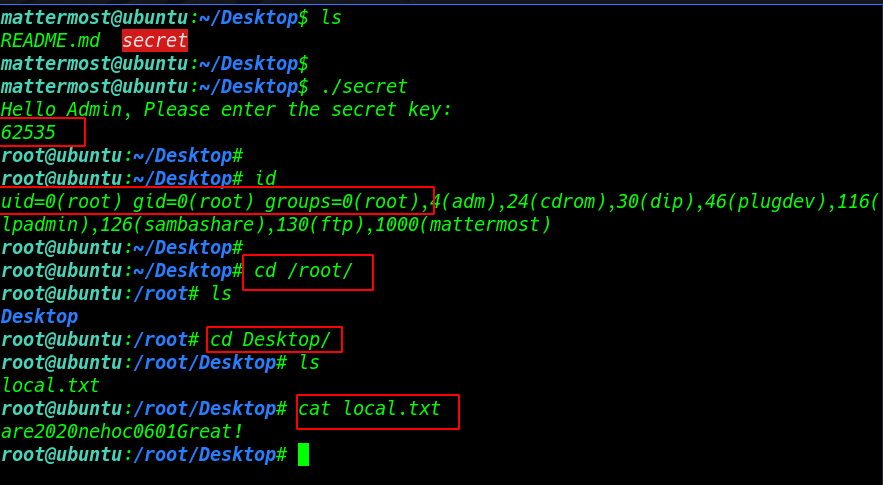
we see a secret file mattermost Desktop directory now run the file and we see a secret file key error
|
1 |
./secret |
Downloading the secret file our local system I am starting local PHP server port 4545 ( php -S targetvmip: any port number
|
1 |
php -S 192.168.0.105:4545 |
download the secret file with wget command our local system
wget http://192.168.0.105:4545/secret
After Download the secret file decompiling the c++ file using tool ghidra after analysis the code we found an if-else condition with a hax value 0xf447
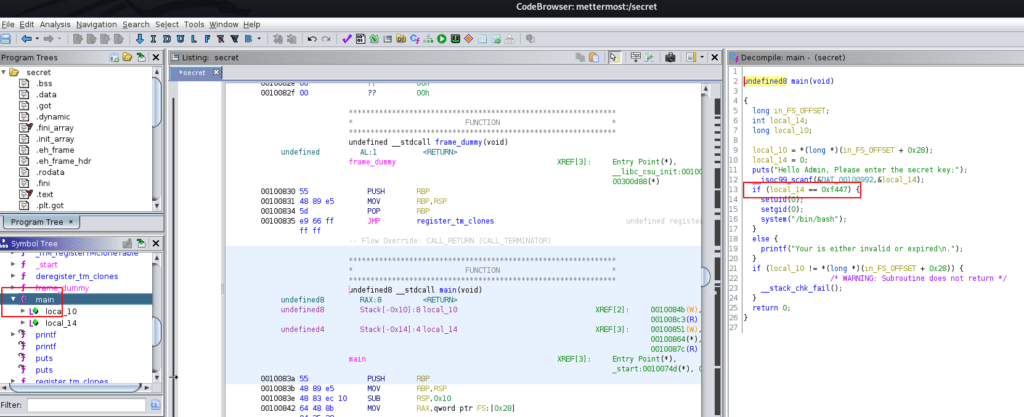
converting the hax value to a decimal using an online website
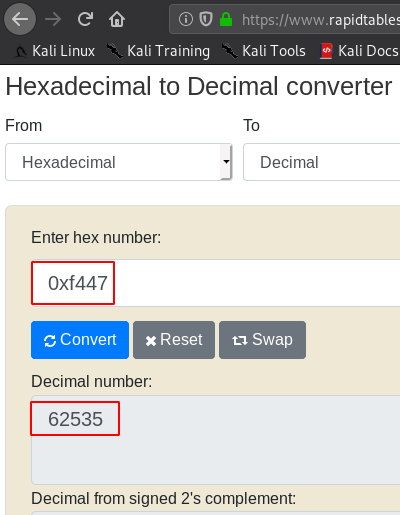
again run the script and type key our Decimal number value 62535 and we see our user is changed to root user
|
1 |
./secret |
|
1 2 3 4 |
id cd /root cd Desktop/ ls |
we found a text file named local.txt. Upon opening the file, we see the our last flag
|
1 |
cat local.txt |