Windows Post Exploitation Bypass UAC
Windows Post Exploitation Bypass User Account Control ( UAC ) Privilege escalation What is UAC User Account Control is a […]
Windows Post Exploitation Bypass User Account Control ( UAC ) Privilege escalation What is UAC User Account Control is a […]
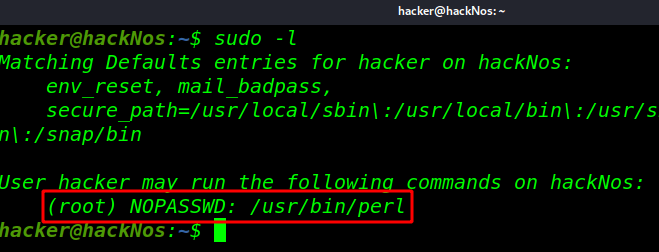
Perl Python Ruby Privilege Escalation Linux sudo <super user do> allows a system administrator to give certain users (or groups […]
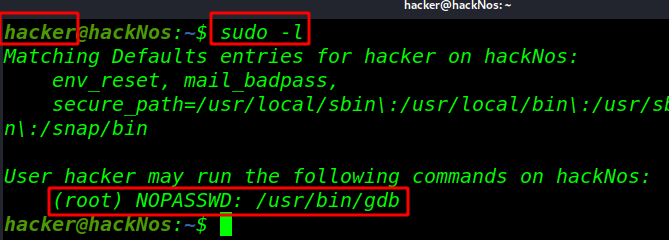
gdb Privilege Escalation Linux sudoers file entry GDB command in Linux with examples. gdb is the acronym for GNU Debugger. […]
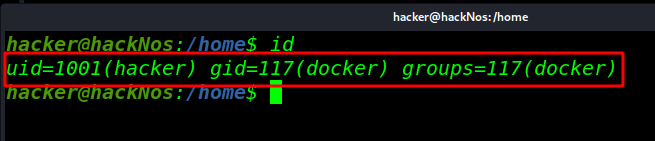
docker Privilege Escalation Linux Docker is a set of the platform as service products that use OS-level virtualization to deliver […]
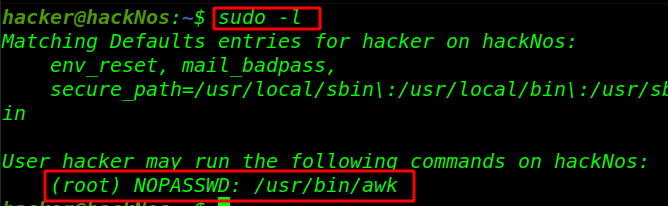
How to exploit sudoers entry awk editor command Sudo Privilege Escalation While solving CTF challenges, for privilege escalation we always […]